I scanned Ukraine
In February, Austrian Christian Haschek posted on his blog an interesting article entitled “I Crawled All of Austria . ” Of course, I wondered what would happen if this study was repeated, but with Ukraine. Several weeks of round-the-clock gathering of information, a couple of days to make out an article, and during this study, discussions with various representatives of our society, then clarify, then learn more. Please, under the cat ...
No special tools were used to collect the information (although several people advised using the same OpenVAS to make the study more thorough and informative). With IP security, which relate to Ukraine (below how it was defined), the situation, in my opinion, is pretty bad (and definitely worse than what is happening in Austria). No attempt was made or planned to use the discovered vulnerable servers.
It is actually very simple. IP addresses are not generated by the country itself, but allocated to it. Therefore, there is a list (and it is public) of all countries and all IPs that belong to them.
Everyone can download it and then filter it. Grep Ukraine IP2LOCATION-LITE-DB1.CSV> ukraine.csv
A simple script created by Christian allows you to bring the list into a more usable form.
Ukraine owns almost as many IPv4 addresses as Austria, more than 11 million 11 640 409, to be exact (for comparison in Austria - 11 170 487).
If you do not want to play with IP addresses yourself (and this is not worth doing!), Then you can use the Shodan.io service .
Of course, no conscious Ukrainian will open such access to their computers. Or will it be?
5669 Windows machines with direct access to the network were found (in Austria there are only 1273 of them, but this is a lot).
Oops Are there any among them that could be attacked with the exploits ETHERNALBLUE, which has been known since 2017? In Austria there was not a single such car, and I hoped that in Ukraine, too, would not be found. Unfortunately, it is useless. Found 198 IP addresses that did not block this "hole" at home.
Enough about Windows. Let's see what we have with DNS servers, which are open-resolvers and which can be used for DDoS attacks.
It works something like this. The attacker sends a small DNS query, and the vulnerable server responds with a packet that is 100 times larger. Boom! Corporate networks can quickly fall from this amount of data, and an attack requires the bandwidth that a modern smartphone can provide. And such attacks were not uncommon even on GitHub.
Let's see if there are such servers in Ukraine.
The first step is to find those that have an open 53 port. As a result, we have a list of 58,730 IP addresses, but this does not mean that they can all be used for DDoS attacks. It is necessary that the second requirement is fulfilled, namely they must be open-resolver.
To do this, you can use the simple dig command and see that we can dig up dig + short test.openresolver.com TXT @ ip.of.dns.server. If the server responded with open-resolver-detected, then it can be considered a potential target of attack. Open resolvers account for approximately 25%, which is comparable to Austria. In terms of total number, it is about 0.02% of all Ukrainian IPs.
Glad you asked. It’s easier (and the most interesting thing for me personally) to see IP with an open 80 port and what’s spinning on it.
260 849 Ukrainian IPs respond to port 80 (http). 125,444 addresses responded positively (200 status) to a simple GET request that your browser can send. The rest gave some errors. It is interesting that 853 servers issued 500 statuses, and the rarest statuses were 407 (request for proxy authorization) and absolutely non-standard 602 (IP is not in the “white list”) for one answer.
Apache absolutely dominates - 114 544 servers use it. The oldest version I found in Ukraine is 1.3.29, released on October 29, 2003 (!!!). nginx in the second place 61 659 servers.
11 servers use WinCE, which was released in 1996, and finished patching it in 2013 (in Austria there are only 4 of them).
The HTTP / 2 protocol uses 5,144 servers, HTTP / 1.1 - 256,836, HTTP / 1 - 13,491.
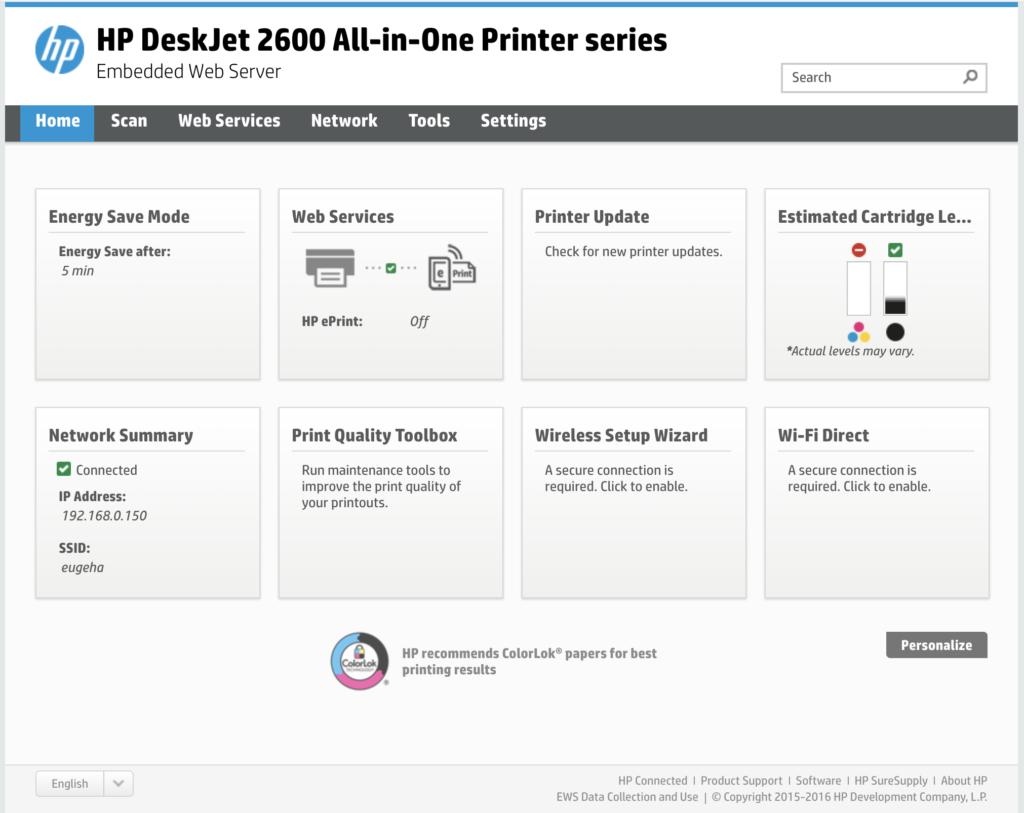
2 HP, 5 Epson and 4 Canon, which are accessible from the network, some of them without any authorization.
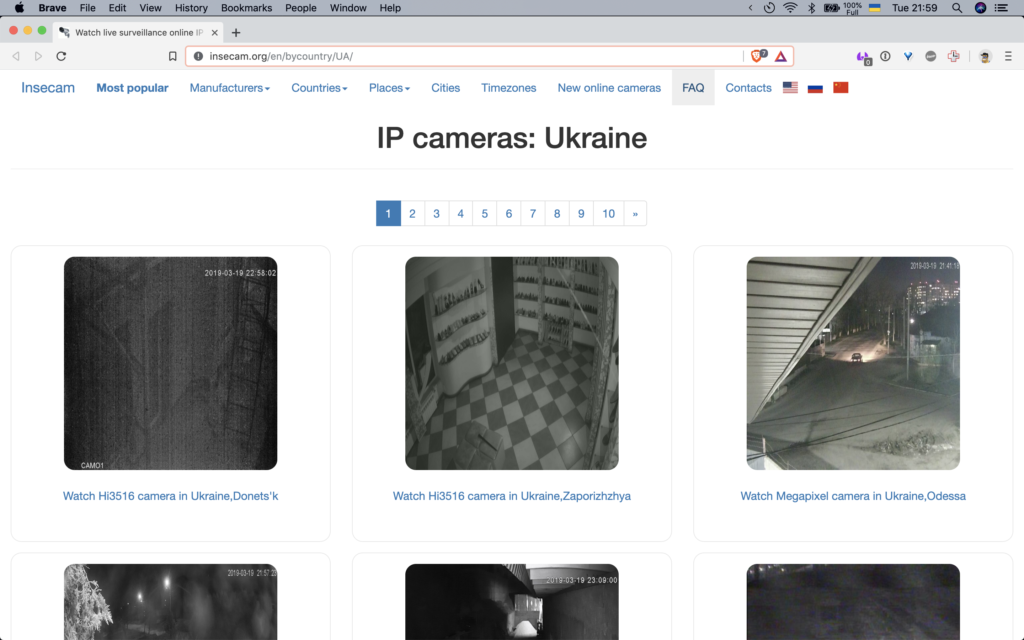
It is not news that in Ukraine there are VERY many webcams that broadcast themselves on the Internet, collected on different resources. At least 75 cameras broadcast themselves on the Internet without any protection. You can look at them here .
Ukraine is a small country, like Austria, but has the same problems as large countries in the field of IT. We need to develop a better understanding of what is safe and what is dangerous, and equipment manufacturers should provide a safe initial configuration of their equipment.
In addition, I am gathering partner companies ( to become a partner ) that can help you ensure the integrity of your own IT infrastructure. The next step I plan to do is review the security of Ukrainian sites. Do not switch!
TL; DR
No special tools were used to collect the information (although several people advised using the same OpenVAS to make the study more thorough and informative). With IP security, which relate to Ukraine (below how it was defined), the situation, in my opinion, is pretty bad (and definitely worse than what is happening in Austria). No attempt was made or planned to use the discovered vulnerable servers.
First of all: how can I get all the IP addresses that belong to a certain country?
It is actually very simple. IP addresses are not generated by the country itself, but allocated to it. Therefore, there is a list (and it is public) of all countries and all IPs that belong to them.
Everyone can download it and then filter it. Grep Ukraine IP2LOCATION-LITE-DB1.CSV> ukraine.csv
A simple script created by Christian allows you to bring the list into a more usable form.
Ukraine owns almost as many IPv4 addresses as Austria, more than 11 million 11 640 409, to be exact (for comparison in Austria - 11 170 487).
If you do not want to play with IP addresses yourself (and this is not worth doing!), Then you can use the Shodan.io service .
Are there any unpatched Windows machines in Ukraine that have direct access to the Internet?
Of course, no conscious Ukrainian will open such access to their computers. Or will it be?
masscan -p445 --rate 300 -iL ukraine.ips -oG ukraine.445.scan && cat ukraine.445.scan | wc -l5669 Windows machines with direct access to the network were found (in Austria there are only 1273 of them, but this is a lot).
Oops Are there any among them that could be attacked with the exploits ETHERNALBLUE, which has been known since 2017? In Austria there was not a single such car, and I hoped that in Ukraine, too, would not be found. Unfortunately, it is useless. Found 198 IP addresses that did not block this "hole" at home.
DNS, DDoS, and Rabbit Hole Depth
Enough about Windows. Let's see what we have with DNS servers, which are open-resolvers and which can be used for DDoS attacks.
It works something like this. The attacker sends a small DNS query, and the vulnerable server responds with a packet that is 100 times larger. Boom! Corporate networks can quickly fall from this amount of data, and an attack requires the bandwidth that a modern smartphone can provide. And such attacks were not uncommon even on GitHub.
Let's see if there are such servers in Ukraine.
masscan -pU 53 -iL ukraine.ips -oG ukraine.53.scan && cat ukraine.53.scan | wc -lThe first step is to find those that have an open 53 port. As a result, we have a list of 58,730 IP addresses, but this does not mean that they can all be used for DDoS attacks. It is necessary that the second requirement is fulfilled, namely they must be open-resolver.
To do this, you can use the simple dig command and see that we can dig up dig + short test.openresolver.com TXT @ ip.of.dns.server. If the server responded with open-resolver-detected, then it can be considered a potential target of attack. Open resolvers account for approximately 25%, which is comparable to Austria. In terms of total number, it is about 0.02% of all Ukrainian IPs.
What else can be found in Ukraine?
Glad you asked. It’s easier (and the most interesting thing for me personally) to see IP with an open 80 port and what’s spinning on it.
web server
260 849 Ukrainian IPs respond to port 80 (http). 125,444 addresses responded positively (200 status) to a simple GET request that your browser can send. The rest gave some errors. It is interesting that 853 servers issued 500 statuses, and the rarest statuses were 407 (request for proxy authorization) and absolutely non-standard 602 (IP is not in the “white list”) for one answer.
Apache absolutely dominates - 114 544 servers use it. The oldest version I found in Ukraine is 1.3.29, released on October 29, 2003 (!!!). nginx in the second place 61 659 servers.
11 servers use WinCE, which was released in 1996, and finished patching it in 2013 (in Austria there are only 4 of them).
The HTTP / 2 protocol uses 5,144 servers, HTTP / 1.1 - 256,836, HTTP / 1 - 13,491.
Printers ... because ... why not?
2 HP, 5 Epson and 4 Canon, which are accessible from the network, some of them without any authorization.

webcams
It is not news that in Ukraine there are VERY many webcams that broadcast themselves on the Internet, collected on different resources. At least 75 cameras broadcast themselves on the Internet without any protection. You can look at them here .

What's next?
Ukraine is a small country, like Austria, but has the same problems as large countries in the field of IT. We need to develop a better understanding of what is safe and what is dangerous, and equipment manufacturers should provide a safe initial configuration of their equipment.
In addition, I am gathering partner companies ( to become a partner ) that can help you ensure the integrity of your own IT infrastructure. The next step I plan to do is review the security of Ukrainian sites. Do not switch!
