Crystal Blockchain Analytics: Investigating the Hacks and Theft Cases
In this report, Bitfury shares analysis completed by its Crystal Blockchain Analytics engineering team on the movement of bitcoin from the Zaif exchange, Bithumb exchange and Electrum wallets.

On September 17, 2018, the Zaif exchange suspended deposits and withdrawals in BTC, BCH and MONA. On September 18, the exchange reported to the police that it had been hacked and funds had been stolen. In their announcement, they shared the following information:
Bitfury’s Blockchain Analytics engineering team investigated the hack, focusing specifically on the movement of stolen bitcoin. A summary of our investigation can be found below.
Step 1: Identify the hacker addresses. Because Zaif shared the exact time of unauthorized access, we were able to pinpoint which transactions belong to the hacker. We researched the largest transactions that happened between 7am and 11 am UTC. We shortly discovered a suspicious transaction. The transaction ID is c3b9a4a0831a65523c81e6a04f6ddf5a7a89f344d990e8a13e5278efe57f4280.
This transaction has 131 inputs. Using Crystal’s identification software, we were able to determine all of the input addresses were Zaif addresses. The output address is 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w. All bitcoin were sent to this address.
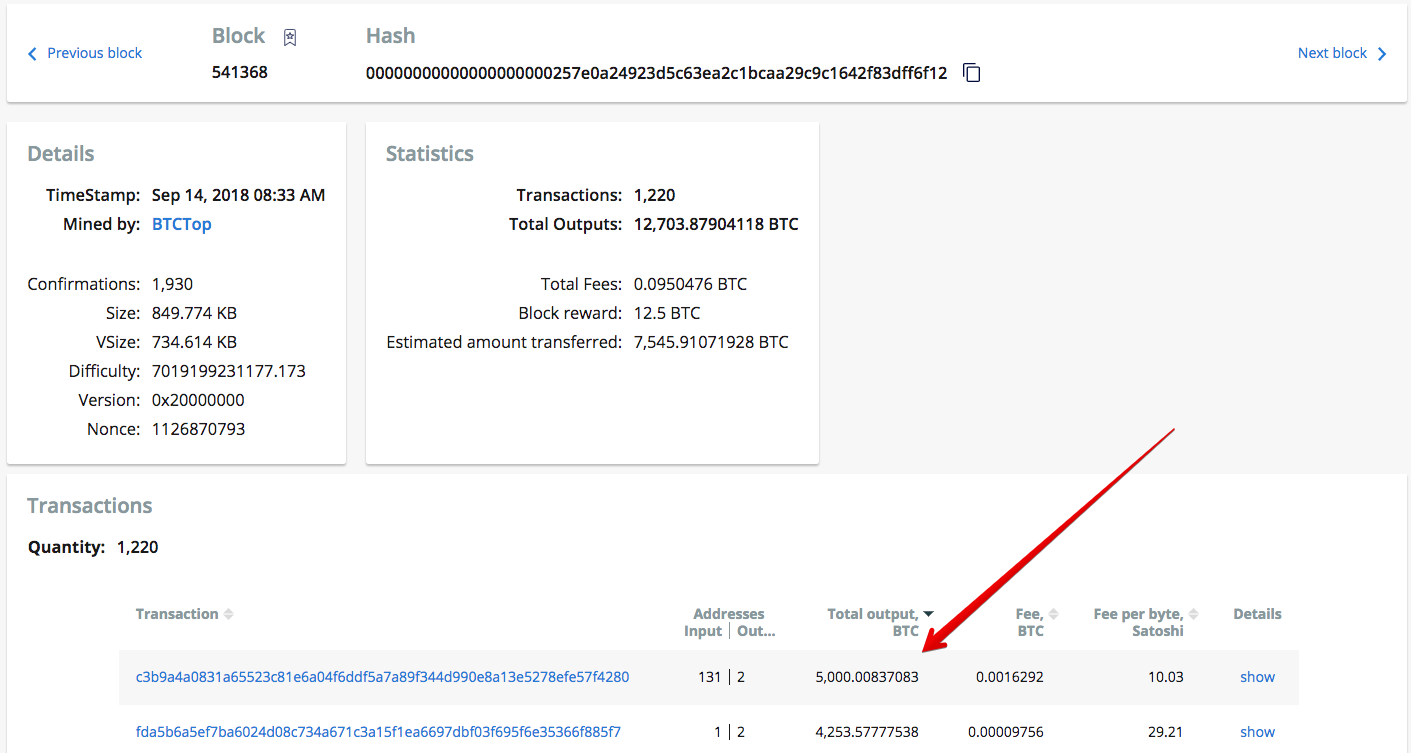
Identification of the suspicious transaction from Zaif to the hacker.
Step 2: Track the stolen funds. After identifying the bitcoin address the stolen bitcoin were sent to, we began monitoring that address. Our goal was to find addresses or known entities that received stolen bitcoin from this address. We did this by using Crystal’s Tracking tool.
Address 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w had 9 outgoing transactions and we tracked each one. After monitoring these transactions, we discovered that 5,109 addresses had received a portion of stolen funds.
Next, we sorted tracking results by the amount settled and found addresses in control of the most significant portion of funds. In some cases, we were able to attribute those addresses to real entities.

Transfer of funds from Zaif wallets to the hacker
Results: The tracking results indicated that significant part of the funds (30% of total amount) had settled on two bitcoin addresses:
These addresses received bitcoin within a very short chain of transactions (average length was 3 transactions). They had not appeared on the blockchain before, so the owner is unknown. It is probable that these addresses belong to the hacker, so we will monitor their activity going forward.
A significant portion of bitcoin (1,451.7 BTC or 24%) was sent to Binance within a set of small transactions, to Binance address 1NDyJtNTjmwk5xPNhjgAMu4HDHigtobu1s. Binance confirmed that they own this address in their official Twitter account. Binance allows users to withdraw up to 2 BTC without going through a strict KYC/AML process, so the average sum sent to each Binance deposit address was 1.99–2 BTC.

Pattern of Binance deposits

Visualization of money flow to a Binance address
Fractions of bitcoin were also sent to ChipMixer.com. The mixing service was reached within a rather short chain of transactions. Approximately 60 BTC have been sent to ChipMixer.com. You may see a transaction to ChipMixer.com on the figure below.

Visualization of money flow to ChipMixer.com
The remaining bitcoin were split into relatively small amounts. Nearly 13 BTC have been sent to various Huobi addresses. Some of bitcoin reached exchanges such as BTCBox.com, Bitstamp, and Livecoin. Some portions of bitcoin were sent to mixing/gambling services such as CoinGaming.io and Bitcoin Fog. However, these entities were reached within a rather long chain of transactions.
The rest of the funds have settled on addresses with unknown owners, and we will keep monitoring them in the future.
On Wednesday, June 20, Bithumb officials stated that about $31M was stolen by unknown hackers from the Korean crypto exchange Bithumb. Four days before the hack, the exchange announced that it was transferring all assets to a cold wallet for security reasons.
The withdrawal of funds by users was temporarily suspended starting June 15, 2018 at 6:20 PM UTC. We decided to trace the movement of funds in the period of the four days prior to the hack.
We started by examining the more than 1 million addresses that belong to Bithumb and compiled a list of all the addresses that received funds during those four days. Only transactions committed from June 15 to June 20 were reviewed.

Funds flow to Bithumb cold wallet
Until June 19, the movement of funds had two main patterns:
The 18x5 address is the exchange’s cold wallet. This is evidenced by its transaction history (rare transactions of large volumes from/to the Bithumb exchange addresses).

Balance history of address “18x5”
The pattern of fund movement changed on June 19, 2018 at 03:07 PM UTC. At this time, two transactions were initiated from the Bithumb wallets to the addresses:
...with abnormally high commissions of 0.1 BTC. After this moment, there was a period of half an hour in which about 1,050 BTC were withdrawn and deposited in addresses that had not previously appeared in the blockchain. The withdrawal of funds to these addresses (38 addresses) lasted more than a day.
After that, the exchange stop using the buffer address 1LhW. Also, after June 19, 2018 at 05:01 PM UTC, the fee amounts for incoming transactions for the address 18x5 changed dramatically — first to 0.1 BTC, and then to 0.2 BTC.
Soon after this change, a message appeared on the official Exchange account on Twitter, warning users to avoid depositing funds.
High transaction fees for the withdrawal of funds from the exchange addresses continued the entire day, sometimes reaching as high as 2 BTC, higher than the output volume.
 Transaction with abnormally high fee
Transaction with abnormally high fee
Such behavior provoked an increase of transaction fees and bitcoin network congestion on June 19–20.
All the funds withdrawn from the Bithumb wallets for the period from June 16 to June 20 were received by 39 wallets (we excluded several dozens of change addresses with small amounts from the results of the calculation).
One of these 39 addresses is the cold wallet of the exchange(18x5), which received most of the funds. The remaining 38 addresses have unidentified owners. These addresses received 2002.52 BTC within the day on June 19–20. (With transaction fees totaling to 48.126 BTC)
Based on the information given above, it is our professional opinion that there are two possible options:
These addresses were monitored further and the withdrawal of funds started on August 2. First, there was a large transaction of 1000 BTC. We launched tracking of this transaction and, according to its results, money was sent to two addresses belonging to Yobit exchange within transactions of approximately 30 BTC. The visualization of money flow can be seen in the figure below.

Funds flow to Yobit address
The address 1JwpFNKhBMHytJZtJCe7NhZ8CCZNs69NJ1 on top of the graph, which belongs to Yobit, received 603 BTC. Another Yobit address, 13jHABthiyHHtviHe9ZxjtK8KcEANzhjBT, received 396 BTC via the same chain of transactions.
The remaining funds were sent directly to Yobit addresses. Below you may see the list of its addresses and amounts received:
After the withdrawal to Yobit, there were 29 BTC left in 3 addresses, possibly belonging to the hacker. They started moving on August 31. The funds were divided into parts — approximately two BTC each — and were sent to CoinGaming.io. The visualization of money flow can be seen in the figure below:

Funds flow to CoinGaming.io
As a result, CoinGaming.io received 29 BTC from the stolen funds.
Considering the movement patterns of the funds, we assume that the 38 addresses we identified belong to the hacker. A majority of the stolen funds were sent to the Yobit exchange.
On Dec. 27, 2018, the bitcoin wallet Electrum notified users about a phishing attack that was targeting users through malicious servers. At that point, the alleged hacker(s) had already stolen more than 245 BTC.
Using Crystal analytics, we investigated the movement of funds from the hack, tracking them to two major exchanges. Below, we present those findings.
The phishing attack worked in the following way:
After a few hours, the alleged hacker had transferred all funds to the address 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj, where the funds have settled. As of Jan. 11, 2019, 245 BTC remained in 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj. However, it’s important to note that on Dec. 27, the alleged hacker sent 5 BTC to the address 1N1Q7fEF6yxnYsMjvH2jtDDzzW6ndLtfEE.
In the days since the original hack, the alleged hacker has moved those funds, withdrawing 0.2 BTC on Jan. 3 to a Bitfinex wallet (3Kk8aWoGexBo52bY8TJuMseoxKBnGD5QqH), and withdrawing 0.41 BTC on Jan. 11 to a Binance wallet (13cRSL82a9x2MMCedFQBCJJ2x5vCgLyCXC).

On January 18, the alleged hacker became active again by moving funds through chain of transactions. They have now withdrawn 3 BTC to a Bitfinex wallet (33d8Dm2hyJx6NHhHep7KM4QKbjTgWpAQQt).
Moreover, the alleged hacker transferred 49 BTC from 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj wallet and distributed them within 13 addresses.

On Jan. 25, 2019, the alleged hacker has withdrawn funds in bitcoin from all his wallets. Further investigation revealed that the alleged hacker had moved the significant part of bitcoin to the exchange service MorphToken. All the funds that reached Bitfinex were sent there by the MorphToken service.
MorphToken provides the ability to check the status of a transaction using its API. Having checked all the wallets in the hacker’s withdrawal chains in this way, we have managed to find out that at least 243 BTC were sent by the alleged hacker to this service. Almost all funds were exchanged for XMR. However, a small amount (0.07 BTC) was transferred to Ethereum.
Crystal is the all-in-one blockchain investigative tool. Designed for law enforcement and financial institutions, Crystal provides a comprehensive view of the public blockchain ecosystem and uses advanced analytics and data scraping to map suspicious transactions and related entities. Whether it is tracking a bitcoin transaction to a real-world entity, determining relationships between known criminal actors, or surveying suspicious online behavior, Crystal can help move your investigation forward.
To learn more, visit crystalblockchain.com.
Follow Crystal on Twitter to stay up to date on other investigations: @CrystalPlatform.

Investigation of the Zaif Exchange Hack
On September 17, 2018, the Zaif exchange suspended deposits and withdrawals in BTC, BCH and MONA. On September 18, the exchange reported to the police that it had been hacked and funds had been stolen. In their announcement, they shared the following information:
Someone gained unauthorized access to the exchange on September 14, 2018 between 5PM and 7 PM local time (8 AM and 10AM UTC). They successfully transferred away 5,966 bitcoin (BTC) and unknown amounts of BCH and MONA. Zaif was alerted to this unauthorized access when a server malfunction was detected on September 17.
Crystal Analytics Research
Bitfury’s Blockchain Analytics engineering team investigated the hack, focusing specifically on the movement of stolen bitcoin. A summary of our investigation can be found below.
Step 1: Identify the hacker addresses. Because Zaif shared the exact time of unauthorized access, we were able to pinpoint which transactions belong to the hacker. We researched the largest transactions that happened between 7am and 11 am UTC. We shortly discovered a suspicious transaction. The transaction ID is c3b9a4a0831a65523c81e6a04f6ddf5a7a89f344d990e8a13e5278efe57f4280.
This transaction has 131 inputs. Using Crystal’s identification software, we were able to determine all of the input addresses were Zaif addresses. The output address is 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w. All bitcoin were sent to this address.

Identification of the suspicious transaction from Zaif to the hacker.
Step 2: Track the stolen funds. After identifying the bitcoin address the stolen bitcoin were sent to, we began monitoring that address. Our goal was to find addresses or known entities that received stolen bitcoin from this address. We did this by using Crystal’s Tracking tool.
Address 1FmwHh6pgkf4meCMoqo8fHH3GNRF571f9w had 9 outgoing transactions and we tracked each one. After monitoring these transactions, we discovered that 5,109 addresses had received a portion of stolen funds.
Next, we sorted tracking results by the amount settled and found addresses in control of the most significant portion of funds. In some cases, we were able to attribute those addresses to real entities.

Transfer of funds from Zaif wallets to the hacker
Results: The tracking results indicated that significant part of the funds (30% of total amount) had settled on two bitcoin addresses:
- 3MyE8PRRitpLxy54chtf9pdpjf5NZgTfbZ —1,007.6 BTC settled on the address.
- 3EGDAa9rRNhxnhRzpyRmawYtcYg1jP8qb7—754.5 BTC settled on the address.
These addresses received bitcoin within a very short chain of transactions (average length was 3 transactions). They had not appeared on the blockchain before, so the owner is unknown. It is probable that these addresses belong to the hacker, so we will monitor their activity going forward.
A significant portion of bitcoin (1,451.7 BTC or 24%) was sent to Binance within a set of small transactions, to Binance address 1NDyJtNTjmwk5xPNhjgAMu4HDHigtobu1s. Binance confirmed that they own this address in their official Twitter account. Binance allows users to withdraw up to 2 BTC without going through a strict KYC/AML process, so the average sum sent to each Binance deposit address was 1.99–2 BTC.

Pattern of Binance deposits

Visualization of money flow to a Binance address
Fractions of bitcoin were also sent to ChipMixer.com. The mixing service was reached within a rather short chain of transactions. Approximately 60 BTC have been sent to ChipMixer.com. You may see a transaction to ChipMixer.com on the figure below.

Visualization of money flow to ChipMixer.com
The remaining bitcoin were split into relatively small amounts. Nearly 13 BTC have been sent to various Huobi addresses. Some of bitcoin reached exchanges such as BTCBox.com, Bitstamp, and Livecoin. Some portions of bitcoin were sent to mixing/gambling services such as CoinGaming.io and Bitcoin Fog. However, these entities were reached within a rather long chain of transactions.
The rest of the funds have settled on addresses with unknown owners, and we will keep monitoring them in the future.
Investigation of the Bithumb Exchange Hack
On Wednesday, June 20, Bithumb officials stated that about $31M was stolen by unknown hackers from the Korean crypto exchange Bithumb. Four days before the hack, the exchange announced that it was transferring all assets to a cold wallet for security reasons.
The withdrawal of funds by users was temporarily suspended starting June 15, 2018 at 6:20 PM UTC. We decided to trace the movement of funds in the period of the four days prior to the hack.
We started by examining the more than 1 million addresses that belong to Bithumb and compiled a list of all the addresses that received funds during those four days. Only transactions committed from June 15 to June 20 were reviewed.

Funds flow to Bithumb cold wallet
Until June 19, the movement of funds had two main patterns:
- Many of the funds moved were accumulated to this address: 1LhWMukxP6QGhW6TMEZRcqEUW2bFMA4Rwx (referred to after this as address “1LhW”)
- From the 1LhW address, transactions of large volume were sent to the address 18x5Wo3FLQN4t1DLZgV2MoAMWXmCYL9b7M (referred to after this as address “18x5”)
The 18x5 address is the exchange’s cold wallet. This is evidenced by its transaction history (rare transactions of large volumes from/to the Bithumb exchange addresses).

Balance history of address “18x5”
The pattern of fund movement changed on June 19, 2018 at 03:07 PM UTC. At this time, two transactions were initiated from the Bithumb wallets to the addresses:
- 34muFC1sWsvJ5dzWCotNH4rpKSNfkSCYvD
- and 3DjdVF83hhXKXV8nUFWCF5chrdSAkgE6Ny...
...with abnormally high commissions of 0.1 BTC. After this moment, there was a period of half an hour in which about 1,050 BTC were withdrawn and deposited in addresses that had not previously appeared in the blockchain. The withdrawal of funds to these addresses (38 addresses) lasted more than a day.
After that, the exchange stop using the buffer address 1LhW. Also, after June 19, 2018 at 05:01 PM UTC, the fee amounts for incoming transactions for the address 18x5 changed dramatically — first to 0.1 BTC, and then to 0.2 BTC.
Soon after this change, a message appeared on the official Exchange account on Twitter, warning users to avoid depositing funds.
High transaction fees for the withdrawal of funds from the exchange addresses continued the entire day, sometimes reaching as high as 2 BTC, higher than the output volume.

Such behavior provoked an increase of transaction fees and bitcoin network congestion on June 19–20.
All the funds withdrawn from the Bithumb wallets for the period from June 16 to June 20 were received by 39 wallets (we excluded several dozens of change addresses with small amounts from the results of the calculation).
One of these 39 addresses is the cold wallet of the exchange(18x5), which received most of the funds. The remaining 38 addresses have unidentified owners. These addresses received 2002.52 BTC within the day on June 19–20. (With transaction fees totaling to 48.126 BTC)
Based on the information given above, it is our professional opinion that there are two possible options:
- The set of 38 addresses to which funds were withdrawn belongs to the hackers. Criminals, having access to the system or the database with private keys, began to make transfers to their addresses starting on June 19, 2018 at 03:07PM UTC. High commissions (0.1 BTC) are logical in this case if you want to quickly withdraw as much as possible.
After a while, the exchange noticed the theft and started raising transaction fees when transferring to a cold wallet (sometimes much higher than the transactions of hackers had). By the end of the day on June 20, the exchange managed to solve security problems. The loss in bitcoins was, as stated by Bithumb, 2,016 BTC. This number is very close to the amount we calculated (obtained by a group of unknown addresses), 2,002.52 BTC, which also indicates that this option is likely. - All the addresses we considered belong to the exchange. Another possible option is that the theft could have occurred from wallets that are not in our database. Given that Bithumb is cooperating with law enforcement agencies in the investigation of this case, as well as the fact that they recently passed licensing procedure, the possibility that the exchange provided false information is unlikely.
Tracking the Funds
These addresses were monitored further and the withdrawal of funds started on August 2. First, there was a large transaction of 1000 BTC. We launched tracking of this transaction and, according to its results, money was sent to two addresses belonging to Yobit exchange within transactions of approximately 30 BTC. The visualization of money flow can be seen in the figure below.

Funds flow to Yobit address
The address 1JwpFNKhBMHytJZtJCe7NhZ8CCZNs69NJ1 on top of the graph, which belongs to Yobit, received 603 BTC. Another Yobit address, 13jHABthiyHHtviHe9ZxjtK8KcEANzhjBT, received 396 BTC via the same chain of transactions.
The remaining funds were sent directly to Yobit addresses. Below you may see the list of its addresses and amounts received:
- 1DBRZgDZYnmLWLUpLMgBo1P12v9TnCL8qr — 100 BTC
- 13rgFLyKYQduTwhJkkD83WDLVNMXs4fwPp — 100 BTC
- 1A6wuQGYPbEEb9cy76tdSQHmm5fi5wvzHK — 344 BTC
- 1JquU8Hp6nAhom5c3UDBa9QM5iv1W2Wf2b — 433 BTC
After the withdrawal to Yobit, there were 29 BTC left in 3 addresses, possibly belonging to the hacker. They started moving on August 31. The funds were divided into parts — approximately two BTC each — and were sent to CoinGaming.io. The visualization of money flow can be seen in the figure below:

Funds flow to CoinGaming.io
As a result, CoinGaming.io received 29 BTC from the stolen funds.
Considering the movement patterns of the funds, we assume that the 38 addresses we identified belong to the hacker. A majority of the stolen funds were sent to the Yobit exchange.
Investigation of the Electrum Theft Case
On Dec. 27, 2018, the bitcoin wallet Electrum notified users about a phishing attack that was targeting users through malicious servers. At that point, the alleged hacker(s) had already stolen more than 245 BTC.
Using Crystal analytics, we investigated the movement of funds from the hack, tracking them to two major exchanges. Below, we present those findings.
The phishing attack worked in the following way:
- First, the alleged hacker managed to add dozens of malicious servers to the Electrum network
- The user initiates a bitcoin transaction using their legitimate wallet;
- In response, the user receives a push error message — a phishing message that requires the user to immediately download the “update” from the malicious site (the GitHub repository);
- The user clicks on the link and downloads the malicious update;
- After the user installs a malware version of the wallet, the program asks the victim for a two-factor authentication code (which, under normal circumstances, is requested only for transferring funds);
- The fake Electrum wallet uses the code to send the user’s funds to a hacker’s wallets.
- Crystal’s findings showed that the majority of funds were sent to the address: 14MVEf1X4Qmrpxx6oASqzYzJQZUwwG7Fb5.
After a few hours, the alleged hacker had transferred all funds to the address 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj, where the funds have settled. As of Jan. 11, 2019, 245 BTC remained in 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj. However, it’s important to note that on Dec. 27, the alleged hacker sent 5 BTC to the address 1N1Q7fEF6yxnYsMjvH2jtDDzzW6ndLtfEE.
In the days since the original hack, the alleged hacker has moved those funds, withdrawing 0.2 BTC on Jan. 3 to a Bitfinex wallet (3Kk8aWoGexBo52bY8TJuMseoxKBnGD5QqH), and withdrawing 0.41 BTC on Jan. 11 to a Binance wallet (13cRSL82a9x2MMCedFQBCJJ2x5vCgLyCXC).

On January 18, the alleged hacker became active again by moving funds through chain of transactions. They have now withdrawn 3 BTC to a Bitfinex wallet (33d8Dm2hyJx6NHhHep7KM4QKbjTgWpAQQt).
Moreover, the alleged hacker transferred 49 BTC from 1MkM9Q6xo5AHZkLv2sTGLYb3zVreE6wBkj wallet and distributed them within 13 addresses.

On Jan. 25, 2019, the alleged hacker has withdrawn funds in bitcoin from all his wallets. Further investigation revealed that the alleged hacker had moved the significant part of bitcoin to the exchange service MorphToken. All the funds that reached Bitfinex were sent there by the MorphToken service.
MorphToken provides the ability to check the status of a transaction using its API. Having checked all the wallets in the hacker’s withdrawal chains in this way, we have managed to find out that at least 243 BTC were sent by the alleged hacker to this service. Almost all funds were exchanged for XMR. However, a small amount (0.07 BTC) was transferred to Ethereum.
About Crystal
Crystal is the all-in-one blockchain investigative tool. Designed for law enforcement and financial institutions, Crystal provides a comprehensive view of the public blockchain ecosystem and uses advanced analytics and data scraping to map suspicious transactions and related entities. Whether it is tracking a bitcoin transaction to a real-world entity, determining relationships between known criminal actors, or surveying suspicious online behavior, Crystal can help move your investigation forward.
To learn more, visit crystalblockchain.com.
Follow Crystal on Twitter to stay up to date on other investigations: @CrystalPlatform.
