Crypto miners infiltrated the Microsoft Store

It turns out that even in the Microsoft Store directory you can publish a malicious program, and no one will notice it. This is very convenient for attackers, because most users think of directories like the Microsoft Store, App Store and Google Play as a kind of safe haven where they are protected from viruses (of course, this is not so). Accordingly, thousands of users carefree download the application without suspecting anything bad. Unfortunately for scammers, now this shop has been partially covered.
January 17, 2019 Symantec foundThe Microsoft Store has eight apps with built-in cryptominers. All applications belong to the PWA (Progressive Web Applications) class, they are installed on Windows 10 and work in a separate window (WWAHost.exe), which does not look like a browser, but in fact they are browser-based applications.
Such programs do nothing wrong with the victim’s computer. They simply and quietly mine Monero on the CPU, without too much CPU load.
Symantec immediately reported the find to Microsoft, and they were soon removed from the catalog. February 15, the report was published in the public domain .
The list of applications covers several thematic categories: here are tutorials on optimizing your computer and battery (there is some irony here), an application for searching the Internet, web browsers, and also programs for downloading videos from YouTube.
Although the developers are three companies (DigiDream, 1clean and Findoo), but Symantec experts believe that they are actually created by one person or group.
On the one hand, if a developer wrote about mining in small letters in the user agreement, then with a probability of 99% no one would have noticed this phrase, but his actions would have been completely legal. On the other hand, in any case, mining probably violates the rules for Microsoft Store applications, so they simply would not be put into the catalog.
These applications were posted between April and December 2018, with most of them published at the end of the year.
It is not known how many users downloaded and installed programs. But they were easy to find in the tops of free applications in the tops of the Microsoft Store. Symantec says that as of mid-January, 1,900 ratings have been published for these applications, meaning the number of users is in the thousands, or perhaps tens of thousands. On the other hand, ratings can be wound up, so making an accurate assessment is not possible.
As soon as applications are downloaded and launched, they immediately download the JavaScript library for mining from the developer's server. How this is done: the official domains of each program are registered in the manifest file. For example, the domain Fast-search.tkfor the Fast-search Lite application in the screenshot below.
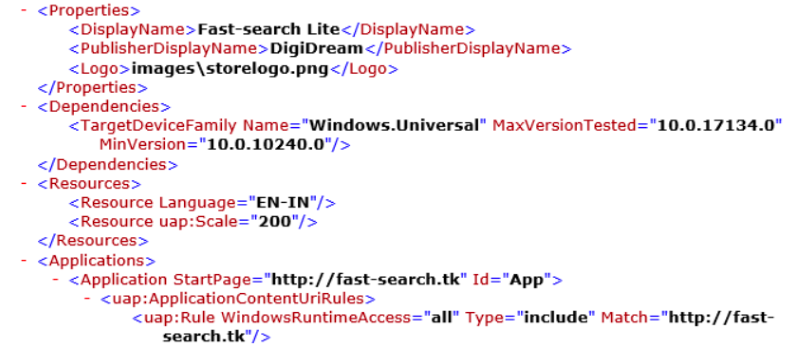
After installation, the application accesses this domain and activates the Google Tag Manager (GTM) script, and all eight applications do this with the same GTM-PRFLJPX key. Google Tag Manager is a common marketing tool. The link has the form
https://www.googletagmanager.com/gtm.js?id={GTM ID}, which theoretically allows you to refer to an arbitrary function, which is what the attackers took advantage of. Under the guise of GTM, the following script is launched:
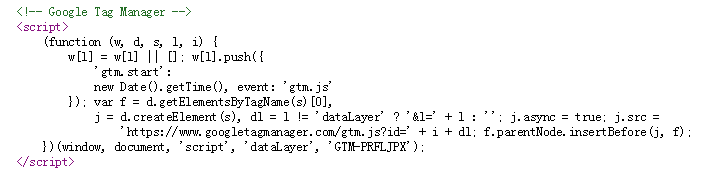
By listening to network traffic, Symantec specialists noticed that this script is accessing a remote server and trying to download the library
http://statdynamic.com/lib/crypta.js.Well, then it’s clear. Crypta.js is an encrypted library for mining that uses the CPU and miners the Monero coin, which is popular with cybercriminals. Why popular? Because it is specially optimized for mining on the central processor, so until now mining there is at least a little profitable.
In reality, Crypta.js is a version of the well-known Coinhive library, a legal service that opened in September 2017 and is still working, allowing users to monetize the user base for program developers and website owners.
Symantec decrypted Crypta.js and found a Coinhive account where money from mining is transferred : da8c1ffb984d0c24acc5f8b966d6f218fc3ca6bda661. Maybe someday in the future, in such situations, the attacker's account will be arrested, and the coins from him will be distributed among all the victims.
