The store opened 110,000 bank cards of its customers and for 6 months did not want to close the vulnerability

There has been so much news lately about company hacks and personal data leaks that website owners must have taken extra precautions to prevent this, you think. No matter how. Maybe in some large companies they thought about how not to lose their capitalization by tens of millions of dollars, like Yahoo before the sale (when the facts of major hacks surfaced). But many small businesses did not lift a finger.
In November 2016, security companies from the Kromtech Security Research Center discovered a database with complete customer information for one of the largest online pet stores in the United States — more than 110,000 bank card entries, some with CVV codes.
Kromtech Security Research Center employees immediately sent the store owners a notification about an incorrectly configured database on the server, due to which information from the database is available online to everyone. Data synchronization between store servers via Rsync protocol is carried out without a password, that is, anyone with an Rsync client and an Internet connection can download the entire database.
They hoped that the owners would immediately close the vulnerability, but did not receive any response. They sent notifications three times and once tried to contact the owners by phone, but to no avail. For six months the situation has not changed .
Specialists did not find any other way but to disclose the fact of vulnerability, although they did not give a specific company name or site name. However, you can’t hide the sewing in a bag, and colleagues quickly dug up that this was a Texas FuturePets.com store (note: at the time of writing, the server was turned off, it returned HTTP Error 404, and it resumed work several days later). The store was developed by Texas-based web studio DataWeb Inc. , which has developed many other related pet products sites. Portfolio presented on their home page. It is likely that these sites can look for similar vulnerabilities. The company owns DataWeb payment platform PegasusCart. This platform serves store sites developed by DataWeb.
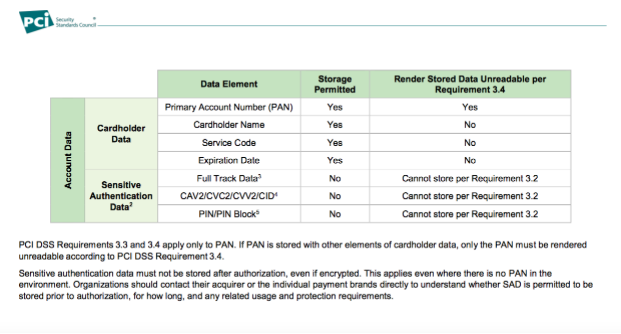
Representatives of MacKeeper warn that for such disorderly handling of financial data of customers, the company not only risks reputation, but also bears a specific legal responsibility. They violate the Payment Card Industry Data Security Standard (PCI DSS). For his violation punishment is provided. In addition to the fact that financial information is not properly protected, one more rule is violated: CVC, CVV and CVV2 numbers should not be stored in the system, even in encrypted form. This is clearly stated in clauses 3.2 and 3.4 of the PCI DSS standard.
The database has 193,337 entries containing names, addresses, mailing addresses and other identification data about customers, telephones, bank card numbers, card expiration dates, cardholder names, etc. Although the database does not have a CVV field as such, some fields contain this code, probably in error.
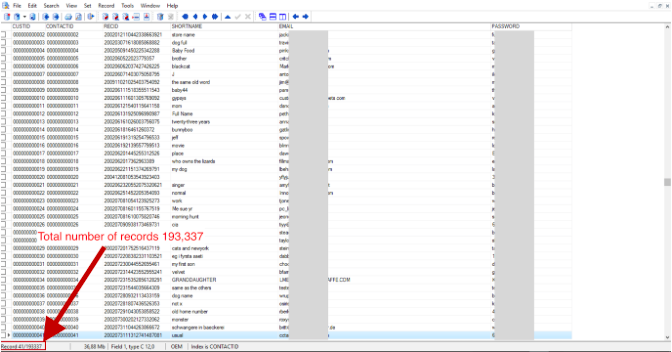
The total number of bank cards available is 110 429. The database contains records from 2002, so a large number of cards are already expired, but there are many cards added in 2015 and 2016, in some cases with CVV codes.
On the black market, information about bank cards is sold for a little more than a dollar apiece. Researchers say this pet store base is one of the largest payment card leaks in history.

Surprisingly, here, the hackers didn’t even need to crack anything - just configure the Rsync client to get broadcast from the company’s server during synchronization.
On the Internet, there are ways to cash money from someone else's card even without CVV knowledge, only by a 16-digit number, owner name and expiration date. For example, in this way you can pay for hotel rooms, buy goods on Amazon and in other stores (it is best to buy gift cards that are anonymous and then easily sold). So the leak is really serious
Security experts say that it’s the sites of small online stores that have now become the most attractive target for hacking by combining the benefits and ease of hacking. They simply have fewer resources and skills to defend themselves. According to a SecurityMagazine survey, only 31% of small businesses “took active steps to protect themselves from security hacks, and 41% were not aware of such risks at all .” It seems that for ignorance, some will have to pay.
