Overview of information security management architecture in Check Point R80.10. Part 1 (Translation)
- Tutorial

The exponential growth in the volume of data coming from various sources, such as network, cloud, mobile and virtual systems, leads to new threats. Organizations must adapt quickly and protect themselves by requiring more powerful and high-performance information security tools. Check Point Infinity , the first consolidated information security system operating on both conventional networks and cloud and mobile, provides the highest level of prevention of both known and unknown targeted attacks to protect you in the present and in the future. Check Point R80.10
control system as part of Check Point Infinityprovides information security management at a new level. With a single management console, providing a simple and effective tool for managing policies and viewing events. Next, we will take a closer look at the technical features of the new architecture.
R80.10 implements the possibility of competitive work of several administrators with editing policies and objects on the same management server. It is also possible to delegate a number of routine tasks to other administrators, which allows you to focus on security monitoring and incident handling.
Unified policy) allows organizations to translate their security regulations into a simple set of rules, which simplifies policy administration and enforcement throughout the organization. Policy levels ( the Policy the Layers ) allow you to split the policy into independent segments, which can be independently controlled and automated.
R80.10 improves overall management performance with advanced orchestration capabilities. API automation allows you to manage workflows, ensuring the consistency of information security services with IT processes and systems.
Key components of the R80.10 management server
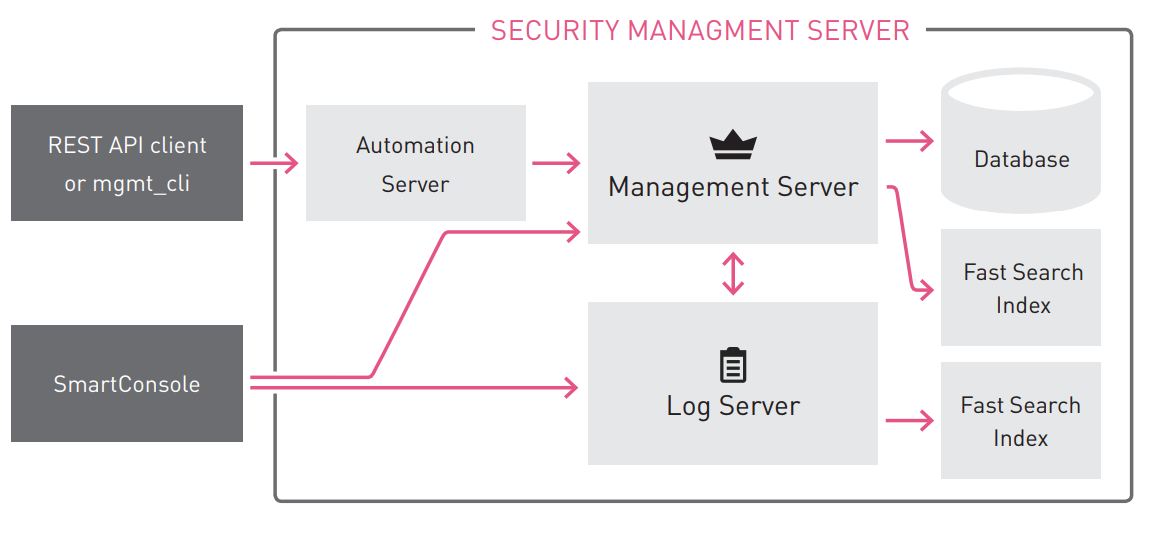
Smartconsole
Check Point R80.10 is managed using the new SmartConsole application. The new application allows, within the framework of one application, to perform tasks on:
- Policy management
- Log Analysis
- Health monitoring
- Office Multi Domain Management
The R80.10 SmartConsole provides a number of amenities that increase productivity. For example, you can easily switch between viewing the change log and a modifiable policy. The R80.10 SmartConsole communicates with the management server on port 19009 .
Part of Check Point blades uses old services to interact with the client part. They use the FWM and CPMI APIs on TCP port 18190 for this .
Check Point R80.10 Management Server Software Processes
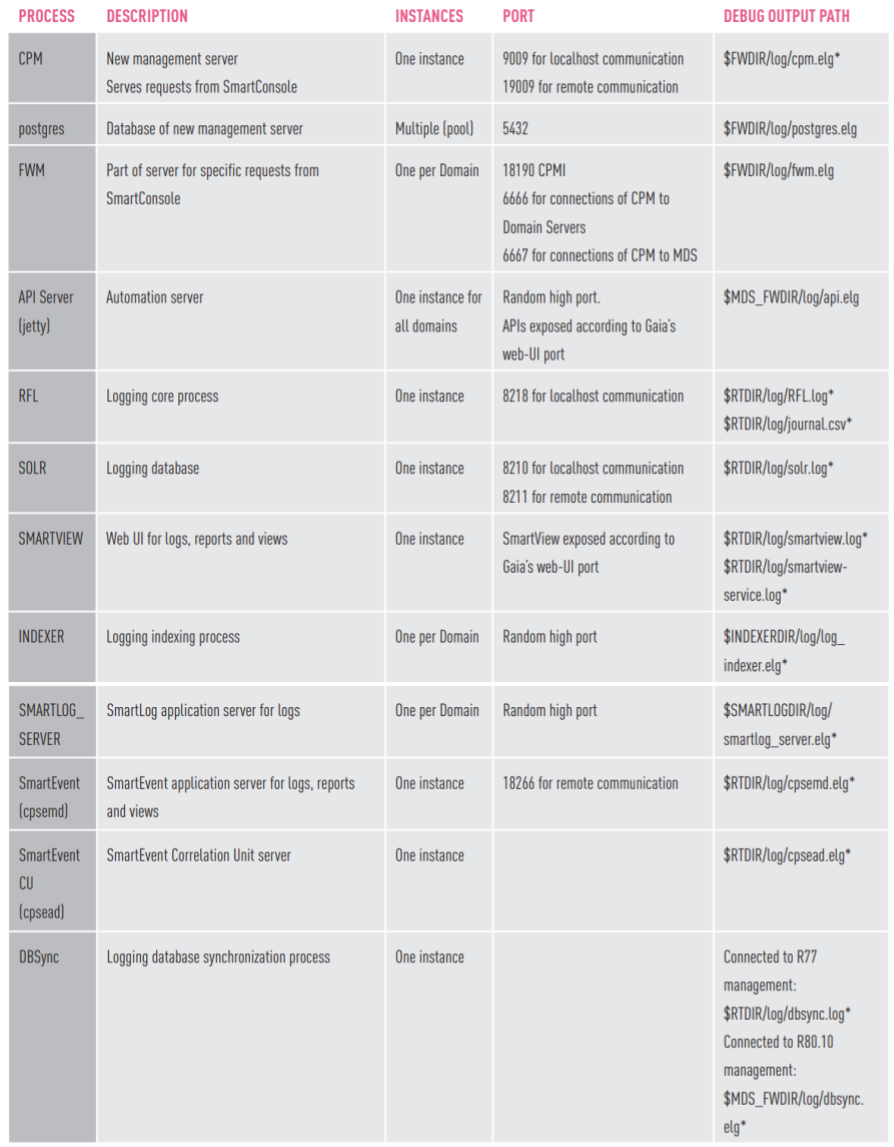
For more information on Check Point software processes, see sk52421 .
R80.10 Management Server Database
The new database architecture of the R80.10 management server allows you to implement new features when performing daily Check Point R80.10 administration tasks.
- Database sessions - allows multiple administrators without conflicts to compete in the same management domain.
- Database revisions - allows you to view the history of changes and improve the performance of many operations, such as setting policies and High Availability.
- Database domains is a solution used both in SMS management and in MDS management, which improves the performance of global policies, threat updates, and application management updates.
Database sessions
With R80.10, several administrators can work on SmartConsole in the same domain, with the same policies and at the same time. To avoid configuration conflicts, all work is performed in sessions, as shown in the diagram below.
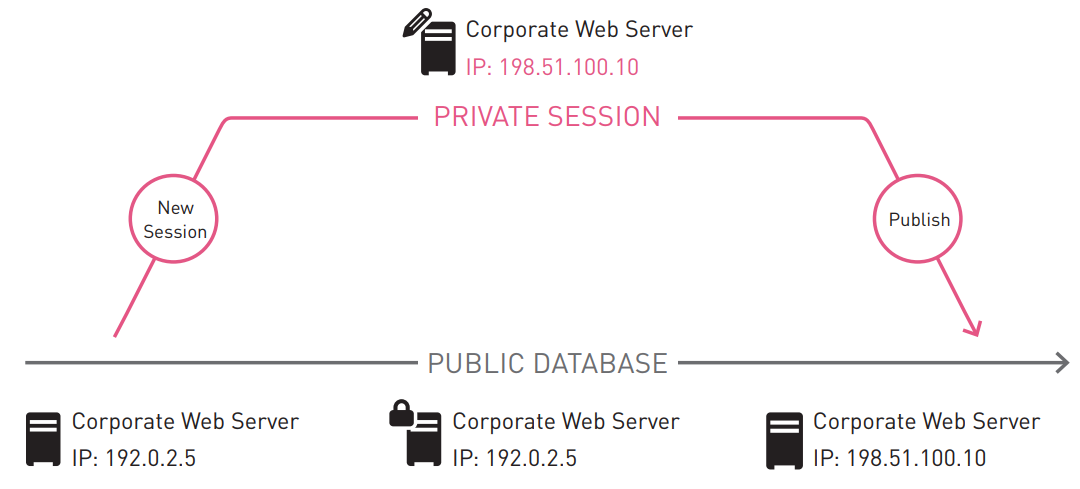
Each session is private and isolated. Changes cannot be seen by other administrators until they are posted. However, objects edited by one administrator are blocked by other administrators, and they can see who blocked the object. This helps administrators coordinate work with shared resources. After the publication of changes, they will be visible to all administrators. When installing the policy, only published data is uploaded to the gateways.
All changes are saved instantly in the management server database. If an accidental shutdown occurs, the work performed is not lost. Administrators can undo changes during a session, and they can open a new session. If necessary, administrators with the appropriate permissions can participate in sessions of other administrators.
Database Domains
In R80.10, the control configuration is stored in a PostgreSQL database. This data is divided into several database domains. Consider the difference between the following terms:
- Database Domains — Segments in a Postgres database that store data for both a simple management server (SMS) and multi-domain management server (MDS).
- Multi-domain domains (Multi Domain Domains) - logical domains created by administrators in the Multi-Domain Server (MDS) and used to manage various parts of the organization’s network.
Types of Database Domains
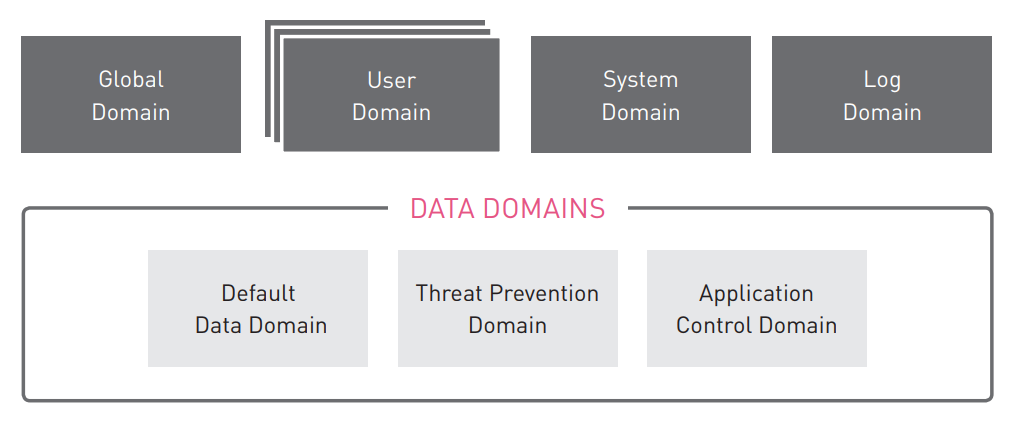
User Domain - store the configuration of objects modified by administrators, for example, network objects and security policies.
Data Domains - There are several Data Domains in R80.10:
- Default Data Domain - contains network objects and services created by default.
- Threat Prevention Domain - Keeps updates for Threat Prevention blades.
- Application Control Domain - Stores updates to the Application Control blade.
The content of Data Domains is changed only by updates downloaded from Check Point.
System Domain - contains information about administrators, rights profiles, and management settings.
Log Domain - stores the configuration for logs that are automatically generated and provided upon request by administrators.
Global Domain - stores the configuration of Global Policies and Global Objects. This domain is used only in a multi-domain management server configuration.
Peer Domains
Security policy configuration requires the use of data from multiple domains, and some domains need to recognize and share their data with other domains. These domains are peer-to-peer with respect to each other.
In a multi-domain environment, a global domain is equated to a user domain. Aligning the domain structure eliminates the need to copy all global objects to the user domain. This leads to increased performance and scalability.
Multi-Domain Domains
In a multi-domain environment, each domain (also known as Customer) is represented by a separate database domain such as User Domain. Each of the other types of database domains has its own domain both in a multi-domain environment and on a regular management server. This separation within a single database has several advantages:
- Separation of user domains . The use of different database domains for storing information of different management domains provides a complete separation of their data. User Domains are not peer domains, and therefore sharing their data is not possible.
- The expanded purpose of global politics . Prior to R80.10, the global policy assignment copied all global objects to the domain database (the $ FWDIR / conf directory of the domain). In R80.10, the global policy assignment operation assigns a new version of the global domain to the user domain.
- Enhanced Threat Prevention updates in multi-domain environments . When an administrator updates the Threat Prevention domain, it is updated only in the domain with which it is associated. The administrator has a choice in which domain the update revision should be applied. When a Threat Prevention rolls back, an administrator can roll back only this domain, not the entire database.
MDMS level data is stored in the System Domain. This data is administrators, rights profiles, trusted clients, server configuration, management domains, domain servers. This allows you to manage this data in parallel on all MDS servers.
Database Revisions
In versions earlier than R80.10, revisions were saved on the management server as backups in case of an accident. Each revision completely repeated the database. The new R80.10 architecture has a built-in revision engine. Each time when the changes made are published to the management server, a new database revision is automatically created and saved. Each new revision contains only changes that have occurred since the previous revision. This saves disk space and allows you to create revisions faster. This solution improves productivity, and many new management capabilities are based on it:
- Faster policy check using the difference between installed versions.
- More efficient Management High Availability based on changes made since the previous synchronization.
The following diagrams illustrate the process of creating database revisions over time:
Database revisions Database revisions

and peer domains
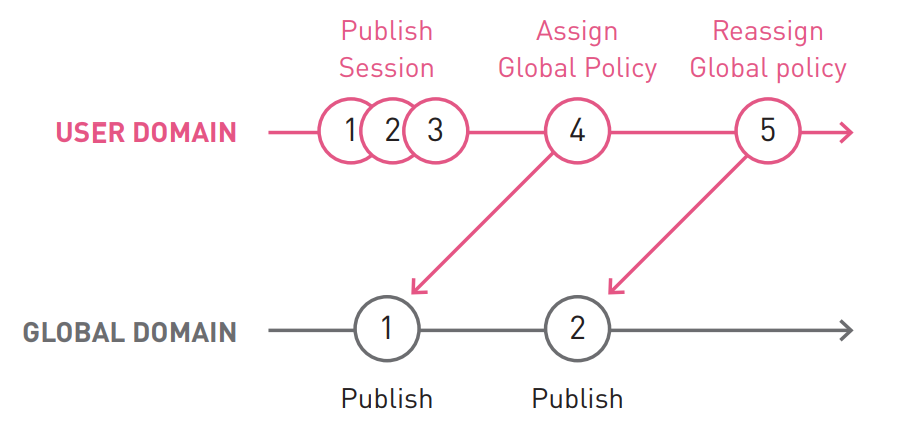
In this example:
The Assign Global Policy operation created revision 4 in the user domain and aligned it to version 1 of the global domain. The publication, which has created a global revision 2 domain is not displayed in the user's domain to the transaction reordering global politics ( reassign of Global policy ). The policy reassignment operation updated the user domain so that it points to the latest version (2) of the Global domain.
The same method is used to update Threat Prevention and Application Control blade data. Each update creates a new revision in the corresponding data domain. And the user domain is aligned with the corresponding revision of the data domain. In a multi-domain environment, each user domain can be aligned with its version of a global or data domain.
Revision Usage Examples
Case No. 1 : There was a problem after installing the policy (loss of connectivity or security error).
Decision:
- Open Security Policies > Installation History .
- In Installation History, select the latest hassle-free policy and select Install specific version
- After the gateway is safely reinstalled, request audit data and changes made to each of the management revisions.
Case 2 : Network problems after updating Threat Prevention data and installing them on gateways.
Solution: Select the hassle-free Threat Prevention update option in Threat Prevention> Updates .
Case No. 3 : It is necessary to perform a state recovery at a specified point in time. Typically, this operation is performed by restoring from the backup, but this will lead to the loss of all the results of the work after backup.
Solution : You can perform the Revert Policy operation . This will allow you to roll back the state of policies to a specified point in time, but will not lead to a rollback of object properties.
So, we familiarized ourselves with the changes that have occurred with the data storage architecture in the new version of R80.10 and with the features that opened up these changes.
To be continued ...
Original article .
If you are interested in courses or articles about Check Point, then you can subscribe to our VKontakte group , as well as our colleagues' group - TS Solution .
You can get authorized Check Point training here.
