Root access through TeamCity
GitHub came under the largest DDoS attack , discussed a bit in the general working chat in the evening. It turned out that few people know about the wonderful search engines shodan.io and censys.io .
Well, for the sake of interest, I’ve looked for TeamCity (hereinafter referred to as the hardware) for the wow effect I remember a cool bug with rega in old versions (it was fixed in version 9.0.2 from January 2015).
As it turned out, it didn’t even have to be used, because in many TS administrators did not close the registration, and on some there was an entrance under the guest.
* Pictures can be opened in the next tab, for better quality
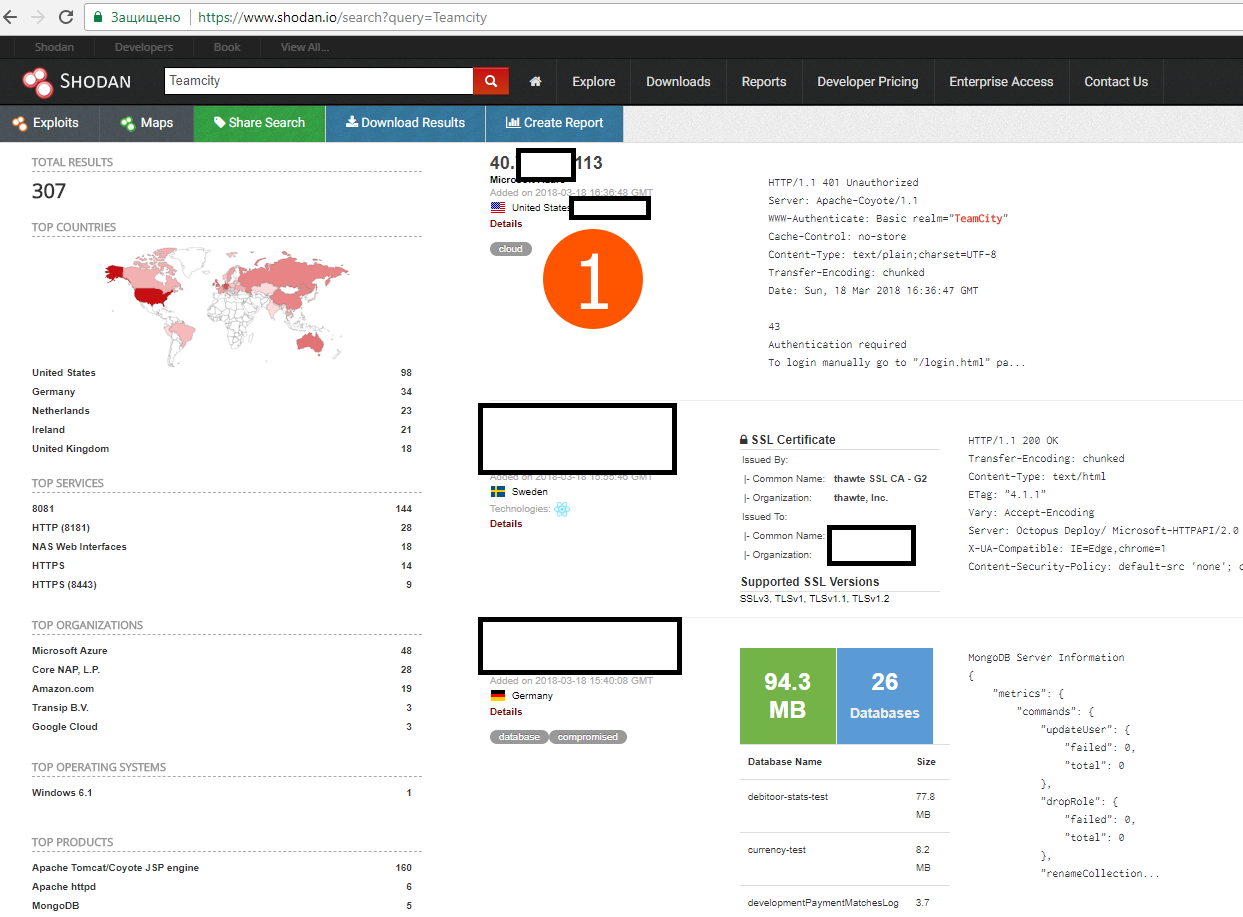
I took the very first IP that came across and moved to their hardware.
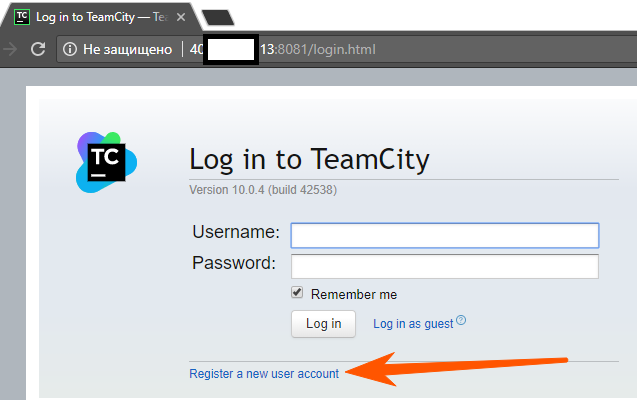
Hurray, there is an ordinary rega, and as a rule, it has more rights than a guest, see comparison below.
Guest
And so, under a new registered account,
some accesses were explicitly registered in the parameters.

But logins also have passwords elsewhere - in configs artifacts:
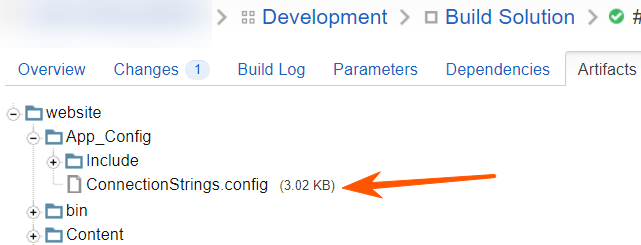
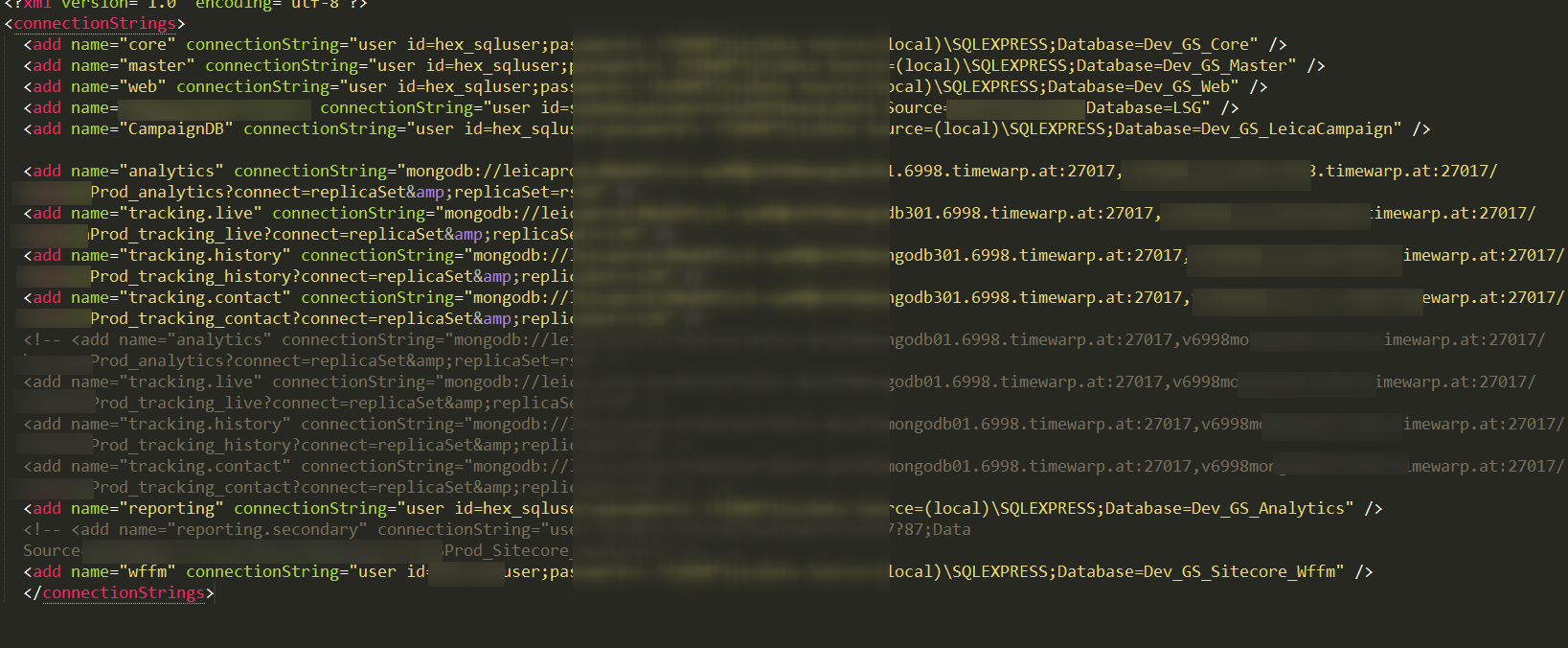
Judging by the names of the database, nothing interesting can be there, but still decided to try it.
Lightweight and fast client for monga under Windows - robomongo.org

I didn’t rummage around the database very much, because the word analytics makes you bored.
It was not possible to go to TFS, definitely the login is not web-based, smoking api is also boring, because it is not the most interesting project, but enough for demonstration).
The post of developers was obtained there - I unsubscribed, there is no answer.
If artifacts were not available, you can always see the change log:


Surprise projects where passwords are simple words, at least there is a prefix here.
I remember once I got a pass - look around , it's just funny.
Also, a certain category of people prefers to store all sorts of settings directly in the code:
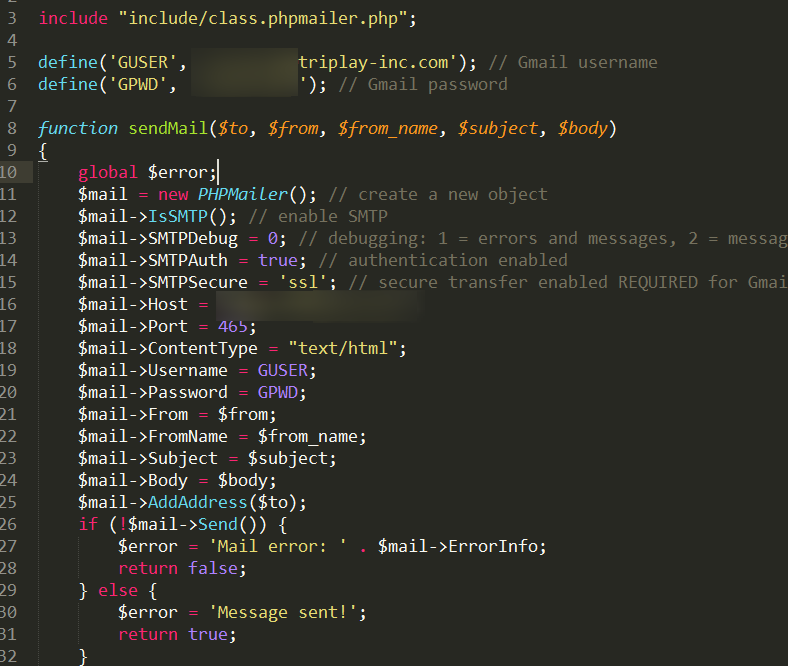
I turn to the most interesting thing - there is a triplay.com project .
Their products are emusic.com, estories.com, mydigipack.com, mymusiccloud.com and some others. Android application downloads 1,000,000+, eplovoe - did not understand where there is the number of downloads to watch.
And of course - their team building was open outside, + rega opened:
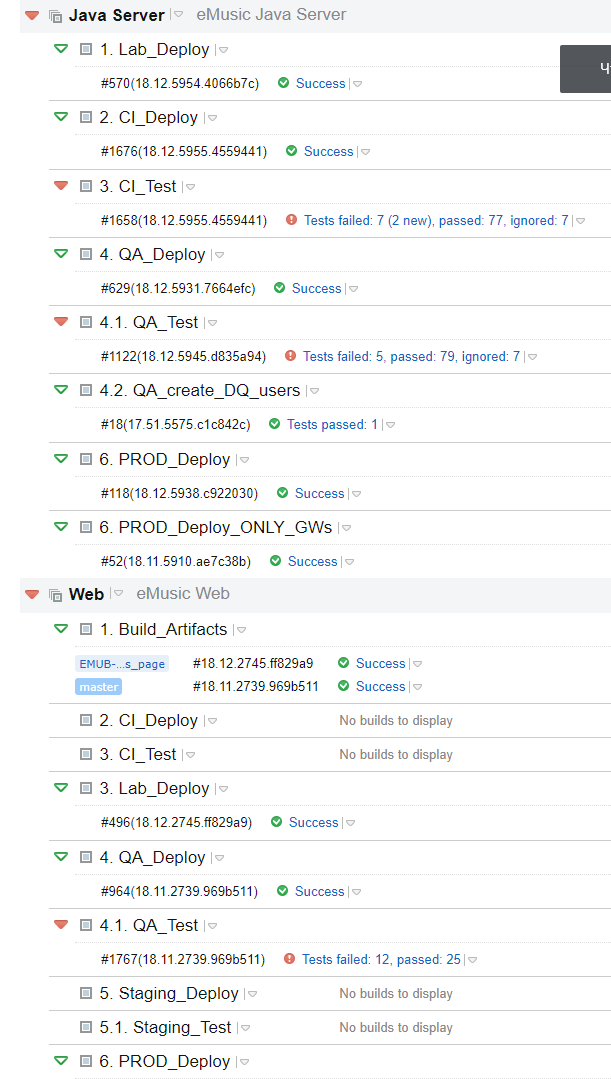
120 assemblies, but artifacts were far from everywhere, probably to save space. But there is a Common project, where all the artifacts come together, but the server ones were completely on their own and that was enough:
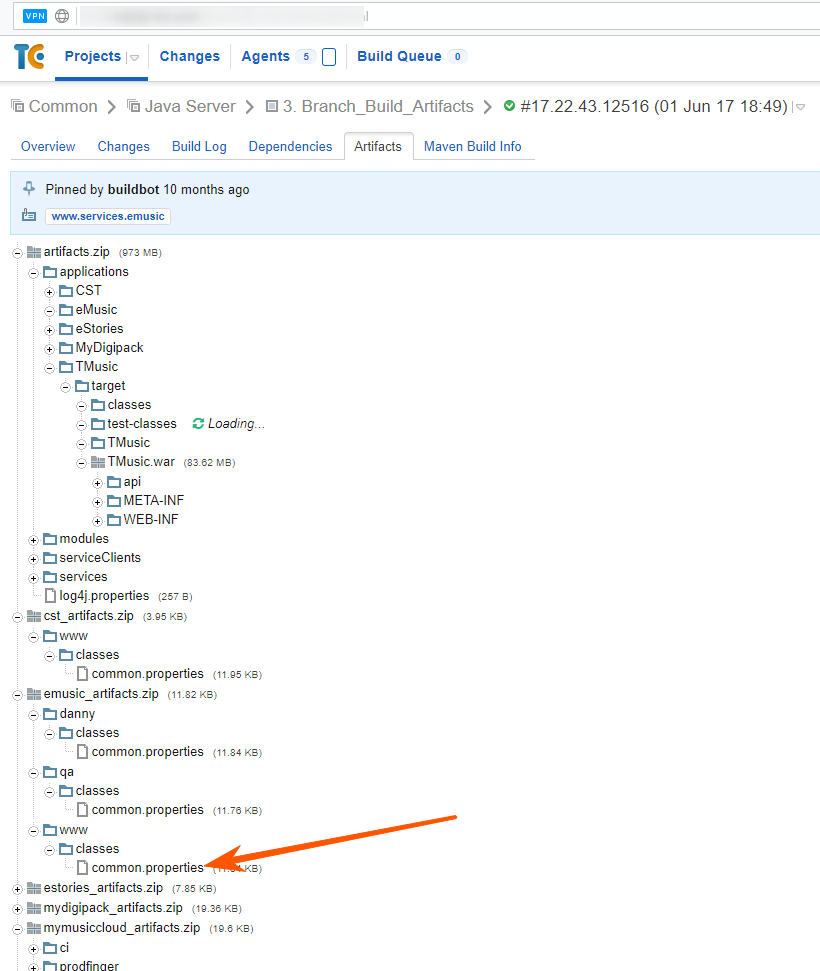
Great, download the file and ... I’m not directly surprised:

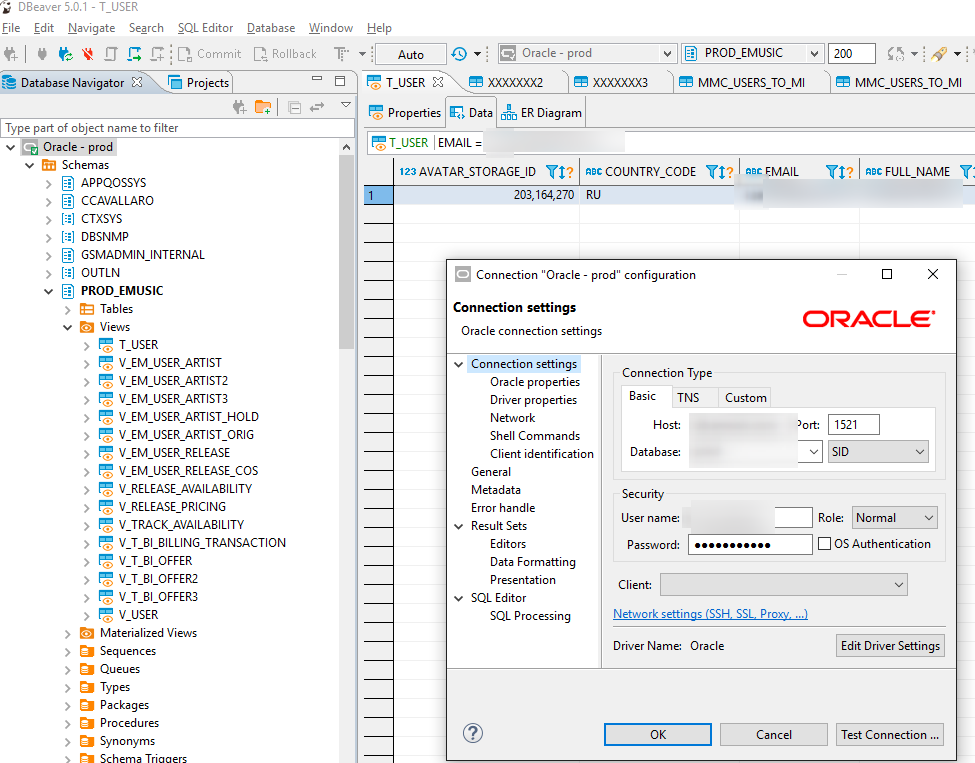
I had to put it in and check the connection to Oracle (Oracle for a simple site in prod, aah, damn, well, why not postgres):

Of course, despite the fact that the prod prefix was specified everywhere in the configs - you couldn't say for sure without an explicit check):
And of course, I myself registered mail with which I wrote to them about the problem (I just showed screenshots, not the script, because I didn’t want people from support to get access to the database, where 691k accounts, downloaded it all at home and ... I xs what I could do. The script is a bit contrived, but it is better to ask for the contact of the admin / developer).
In theory, full access to the database and you can safely replace someone else's hash / salt with your own and enter under it.
But I just read the data and settled down on this, unsubscribing to off. the support, to which they replied that they would consider everything, will be transferred to a specialist who will answer in turn and ... silence
A few days later they closed access to the database, but not to the vehicle, checked the mail - no questions, no thanks.
Well, ok, I’ve got to check further and ... in the artifacts I found a project that contains deploy scripts, as if it gets into the hardware from somewhere outside and then launches the build itself.

So it was, + more login / pass from the vehicle.
It was difficult to believe in this, well, ok, telnet 22 plows, I try sssh, but wait a minute, what login ...
A little surprised by the availability of access, approx. I looked around in the console, looked at the hosts (35 machines are registered) and some kind of keys (I'm not very good with nixes, access to the root is already clear that it would make it possible to do whatever you want).
I found a test domain + a specific machine (and ... it seems ssl certificate).

The screen above is, by the way, when I go from one server to another, because that one from outside via ssh was not available. And there were such machines, of course, dofiga, imagine yourself what kind of infrastructure there is.
And I put the file with special greetings (with errors, sorry, I already wanted to sleep).

After another letter, they covered the shop.
But it wasn’t there, the guys had a test account. I entered under it. It turned out you can get the track for free ... well, I'm just in F12 and ... what I see in the payload:
No, this is not an April Fool’s joke - to get a track for free or to buy - is decided on the frontend by the freeTrackPurchase flag:
And now the nuance - it works, apparently, not for all accounts, but for a specific test one)), but having access to it, you can “buy” all the tracks. Yes, and one figs, they are all available without authorization (there are special URLs, info from the database, checked).
What mistakes did the guys make:
Therefore - if you have any products that are available from outside - think about how you can use them for other purposes than others and prevent this.
And the main application should be designed, and assembled so that "the code base of the application can be freely available at any time without compromising any private data . "
And know the products you work with, such as:
Well, for the sake of interest, I’ve looked for TeamCity (hereinafter referred to as the hardware) for the wow effect I remember a cool bug with rega in old versions (it was fixed in version 9.0.2 from January 2015).
As it turned out, it didn’t even have to be used, because in many TS administrators did not close the registration, and on some there was an entrance under the guest.
* Pictures can be opened in the next tab, for better quality

I took the very first IP that came across and moved to their hardware.

Hurray, there is an ordinary rega, and as a rule, it has more rights than a guest, see comparison below.

Guest

And so, under a new registered account,
some accesses were explicitly registered in the parameters.

But logins also have passwords elsewhere - in configs artifacts:


Judging by the names of the database, nothing interesting can be there, but still decided to try it.
Lightweight and fast client for monga under Windows - robomongo.org

I didn’t rummage around the database very much, because the word analytics makes you bored.
It was not possible to go to TFS, definitely the login is not web-based, smoking api is also boring, because it is not the most interesting project, but enough for demonstration).
The post of developers was obtained there - I unsubscribed, there is no answer.
If artifacts were not available, you can always see the change log:


Surprise projects where passwords are simple words, at least there is a prefix here.
I remember once I got a pass - look around , it's just funny.
Also, a certain category of people prefers to store all sorts of settings directly in the code:

I turn to the most interesting thing - there is a triplay.com project .
Their products are emusic.com, estories.com, mydigipack.com, mymusiccloud.com and some others. Android application downloads 1,000,000+, eplovoe - did not understand where there is the number of downloads to watch.
And of course - their team building was open outside, + rega opened:

120 assemblies, but artifacts were far from everywhere, probably to save space. But there is a Common project, where all the artifacts come together, but the server ones were completely on their own and that was enough:

Great, download the file and ... I’m not directly surprised:


I had to put it in and check the connection to Oracle (Oracle for a simple site in prod, aah, damn, well, why not postgres):

Of course, despite the fact that the prod prefix was specified everywhere in the configs - you couldn't say for sure without an explicit check):

And of course, I myself registered mail with which I wrote to them about the problem (I just showed screenshots, not the script, because I didn’t want people from support to get access to the database, where 691k accounts, downloaded it all at home and ... I xs what I could do. The script is a bit contrived, but it is better to ask for the contact of the admin / developer).
In theory, full access to the database and you can safely replace someone else's hash / salt with your own and enter under it.
But I just read the data and settled down on this, unsubscribing to off. the support, to which they replied that they would consider everything, will be transferred to a specialist who will answer in turn and ... silence
A few days later they closed access to the database, but not to the vehicle, checked the mail - no questions, no thanks.
Well, ok, I’ve got to check further and ... in the artifacts I found a project that contains deploy scripts, as if it gets into the hardware from somewhere outside and then launches the build itself.


So it was, + more login / pass from the vehicle.
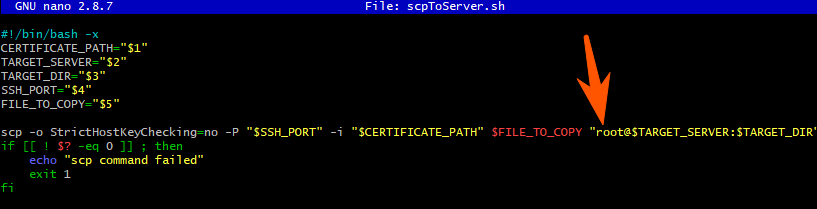
It was difficult to believe in this, well, ok, telnet 22 plows, I try sssh, but wait a minute, what login ...

wu la
ssh -p 22 -i triplay-deployer-priv root@build.triplay-inc.comA little surprised by the availability of access, approx. I looked around in the console, looked at the hosts (35 machines are registered) and some kind of keys (I'm not very good with nixes, access to the root is already clear that it would make it possible to do whatever you want).
I found a test domain + a specific machine (and ... it seems ssl certificate).

The screen above is, by the way, when I go from one server to another, because that one from outside via ssh was not available. And there were such machines, of course, dofiga, imagine yourself what kind of infrastructure there is.
And I put the file with special greetings (with errors, sorry, I already wanted to sleep).

After another letter, they covered the shop.
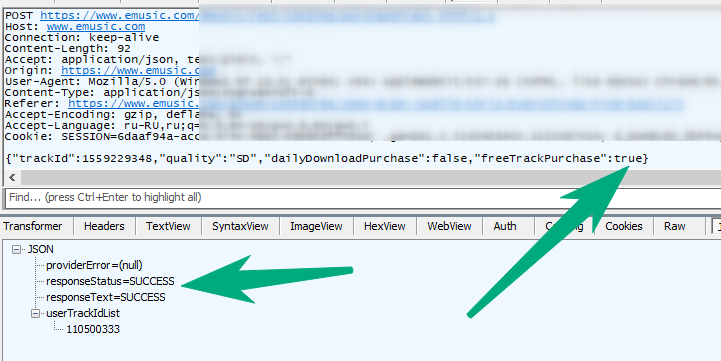
But it wasn’t there, the guys had a test account. I entered under it. It turned out you can get the track for free ... well, I'm just in F12 and ... what I see in the payload:
{
"trackId": 1559229346,
"quality": "SD",
"dailyDownloadPurchase": false,
"freeTrackPurchase": true
}
No, this is not an April Fool’s joke - to get a track for free or to buy - is decided on the frontend by the freeTrackPurchase flag:
Demo purchases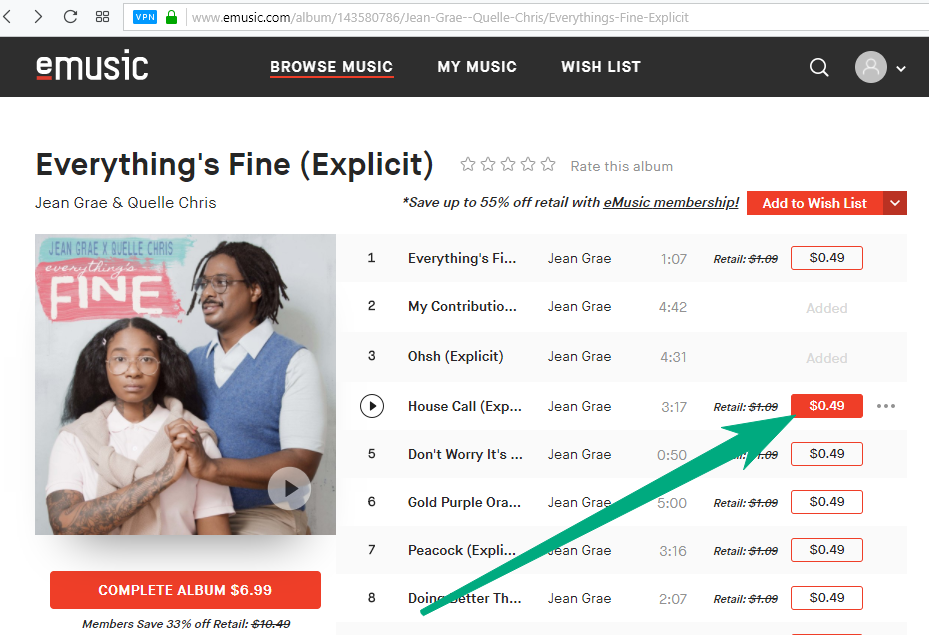




And now the nuance - it works, apparently, not for all accounts, but for a specific test one)), but having access to it, you can “buy” all the tracks. Yes, and one figs, they are all available without authorization (there are special URLs, info from the database, checked).
What mistakes did the guys make:
- Very internal resources were open to the whole world (DB, TeamCity, SSH)
- Even if there is such a need, they did not make a whitelist for connections
- Connect under the root from the outside ... even so-so idea
- Moreover, add a certificate for this from the root to the project!
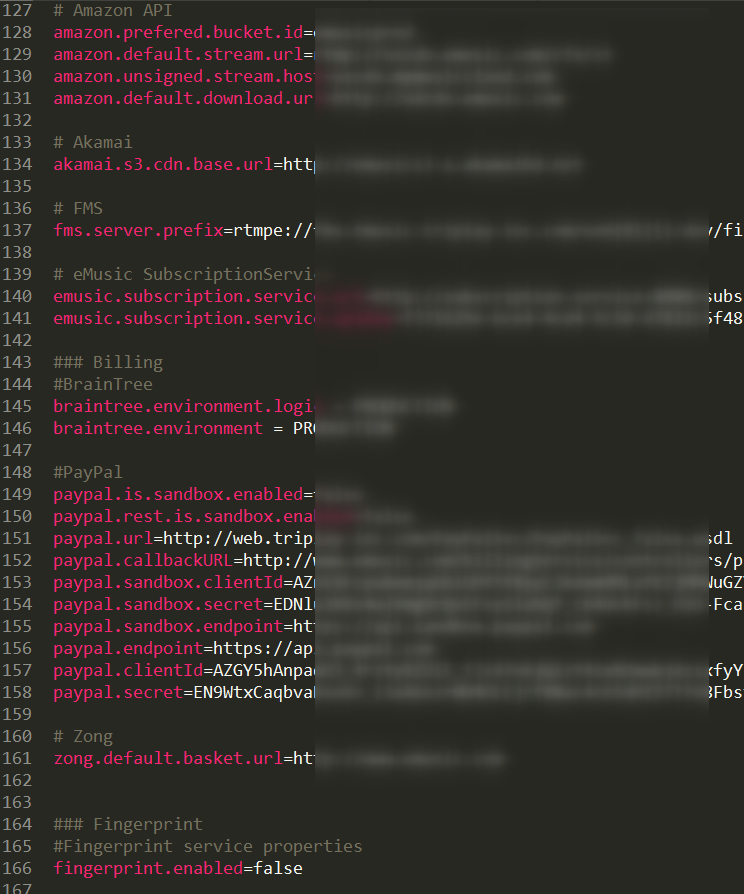
- All accesses and keys are stored in ... files and propagated by project (aws, paypal, etc., put the template here ), instead of storing one connection to the configuration service
- And most importantly - regga was allowed in TeamCity, in fact, how it all started
- Well, up to the heap - there were going to applications for google / apple store and the corresponding certificates and source codes were in place
Therefore - if you have any products that are available from outside - think about how you can use them for other purposes than others and prevent this.
And the main application should be designed, and assembled so that "the code base of the application can be freely available at any time without compromising any private data . "
And know the products you work with, such as:
- rabbit - default login pass guest / guest
- redis - without authorization by default and allows you to do this
- teamcity - default allowed rega
- and ... the list goes on, including the same memekesh that is accessible from outside and has failed github)
Что для тебя "счастье"?
Когда как:
0. Тишина, книга, сок
1. Жена, настолка, кот,
2. Кафе, сидр, друг
3. Код, работа, доступ root
