Hunt Dofoil with Windows Defender ATP
- Transfer
In March 2018, hundreds of thousands of computers were attacked by the Dofoil crypto miner . In previous blog posts, we looked at how we managed to protect users from this massive attack. We also managed to trace the origins of the attack until the infection of the software update service , which was used by cybercriminals to spread the malware.
In this publication, we will take a detailed look at the methods of counteracting the launch in debug mode and analysis, which the authors of Dofoil resorted to, and describe how the capabilities of Windows 10 to detect malware can be useful in investigating such attacks.

During the investigation, we found out that the Dofoil virus has built-in methods to counteract the analysis. It checks what environment it is in and stops working in virtual machines. He also scans the memory for the presence of analysis tools and immediately completes their processes. All this significantly complicates the analysis of malicious code.
The following figure shows the steps involved in introducing malware. Some of these include checking for an analysis environment.
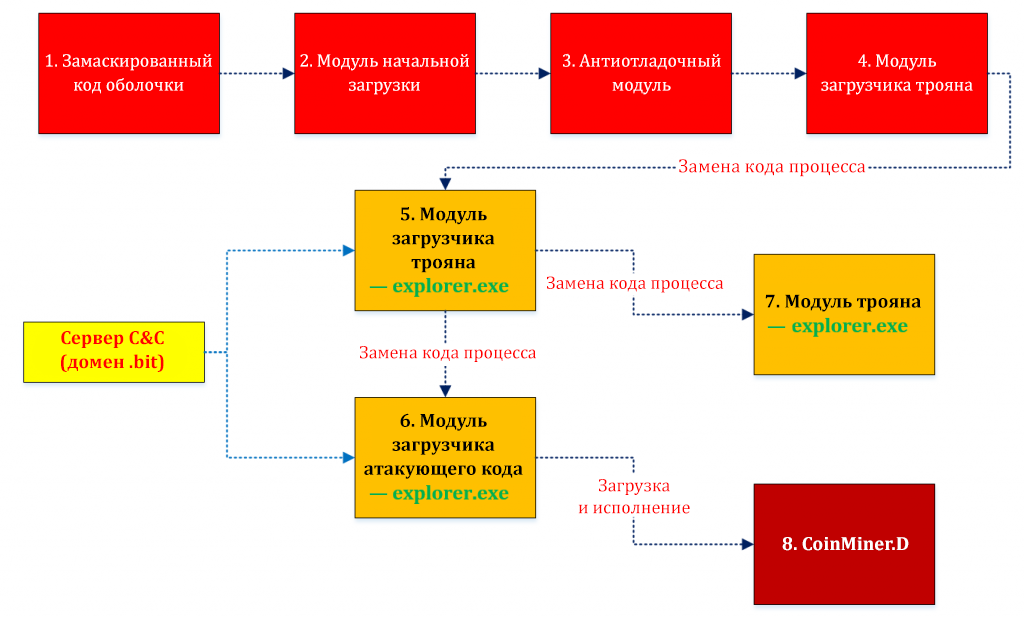
Figure 1. A step-by-step diagram of the execution of the shell code and the attack code Dofoil
The table below describes the purpose of each stage. Each of the first five stages includes means of counteracting dynamic or static analysis of malicious code.
Table 1. Modules implemented by Dofoil at different stages
The first three stages (that is, the disguised shell code, bootstrap module, and anti-debugging module) try to prevent analysis and recognition by the following methods.
Table 2. Methods of counteracting the analysis
The first stage contains a site with the appearance of clean code, followed by real malicious code. Because of this, executable files may seem safe. In addition, the presence of such code can complicate the emulation, since it is not easy to simulate API calls that are rarely found in malicious code.
The first step code also checks the registry key against the expected value. After passing all the checks, the code decrypts the shell code of the second stage and executes it in the labeled memory area. The shell code clears the memory layout of the source main module, decrypts the shell code of the third stage and puts it in the same memory location - this procedure is called replacing the code of the native process.
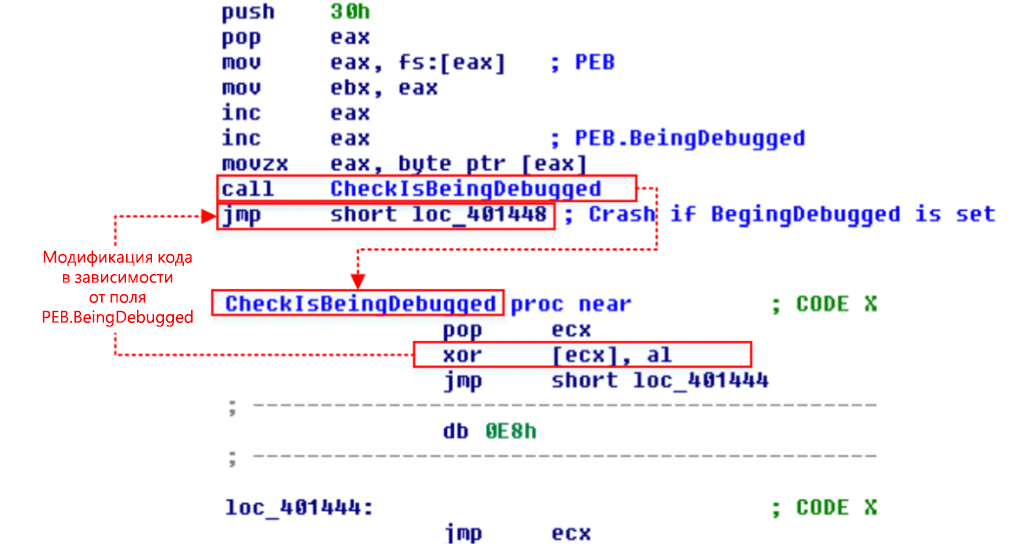
Figure 2. Code mutation depending on the value of PEB.BeingDebugged
The Windows Defender ATP process tree helps expose such anti-debugging mechanisms.
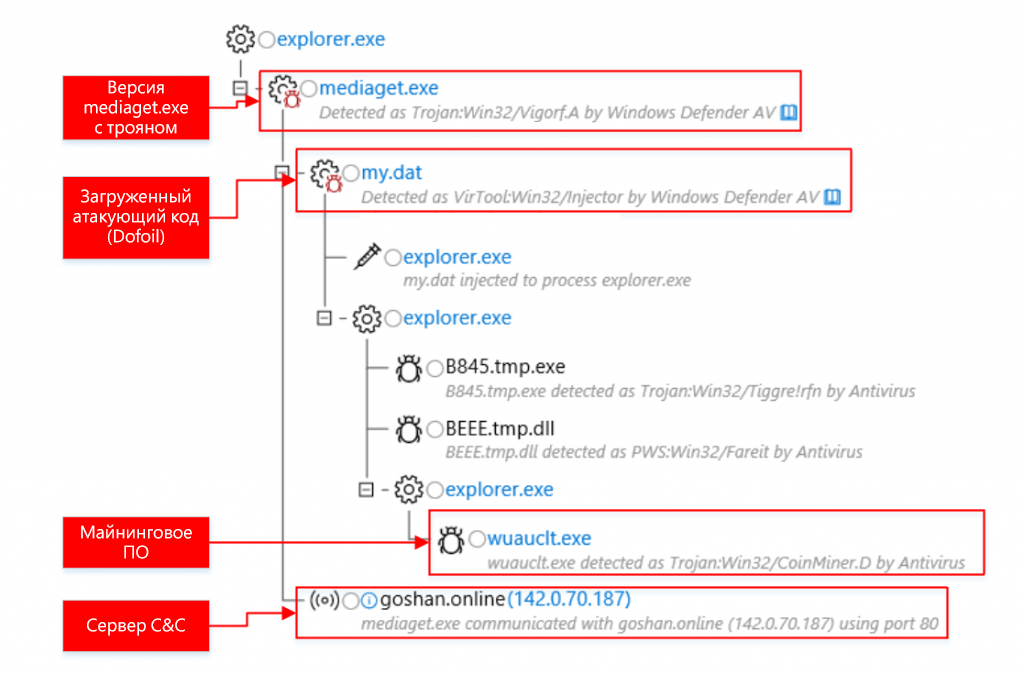
Figure 3. Anti-debugging mechanisms visible in the Windows Defender ATP process tree
Before loading the attacking code, the Trojan loader module checks the runtime in various ways, including virtuality and the availability of analysis tools.
Table 3. Methods of counteracting analysis in the Dofoil Trojan downloader module.
The names of the target processes and Windows classes are stored as a list of specially calculated checksums. The verification algorithm looks like this:
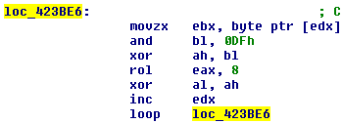
Figure 4. A special algorithm for checking checksums based on shear and exclusive OR operations
Using checksums was supposed to slow down the investigation and prevent researchers from quickly figuring out which analysis tools malware detects.
Table 4. Checksum table for Windows process names and classes
Dofoil’s performance is highly dependent on the process code replacement technique. The main target process is explorer.exe. Shell-code Dofoil launches a new instance of explorer.exe, places the shell-code in dynamic memory and modifies the code of the entry point to switch to the shell-code. Due to this, the malware injects the code without using the CreateRemoteThread API function .
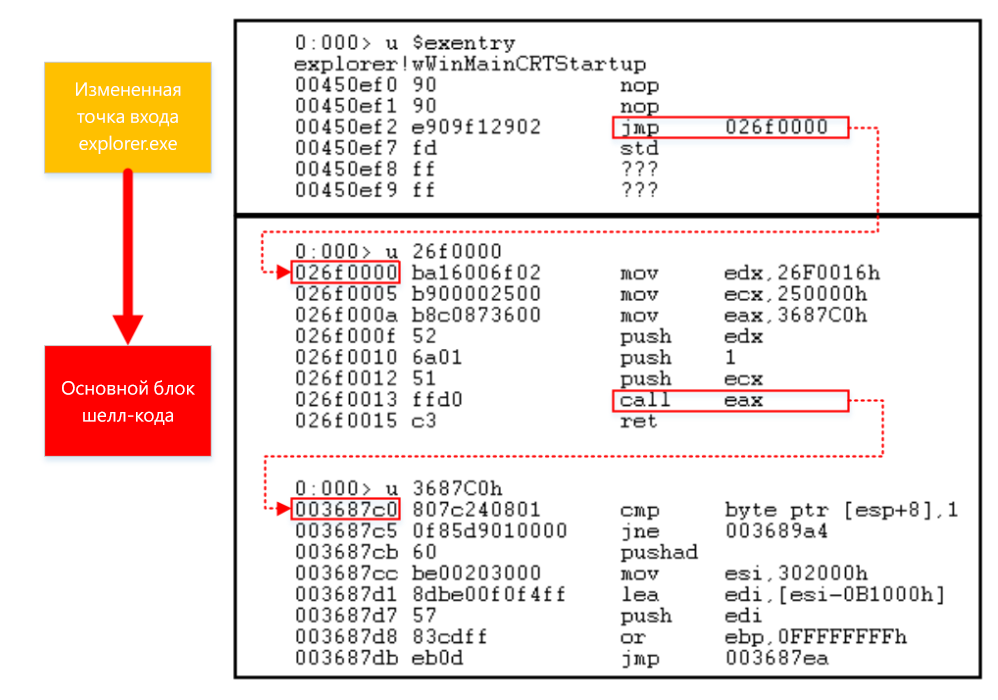
Figure 5. Changing the entry point code in explorer.exe
Windows Defender ATP can detect signs of process code replacement by analyzing operations in memory. The following process tree shows how a malicious program is embedded in explorer.exe by replacing the process code.
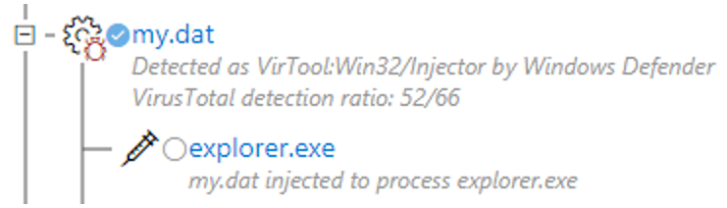
Figure 6. Windows Defender ATP warning process tree: the first process code replacement
When the shell code loads the next layer of attacking code, it spawns another explorer.exe process, into which it then embeds the attacking code by the replacement method. In such cases, Windows Defender ATP significantly accelerates the analysis, accurately identifying malicious operations and indicating the questionable actions of the newly created Windows system processes.
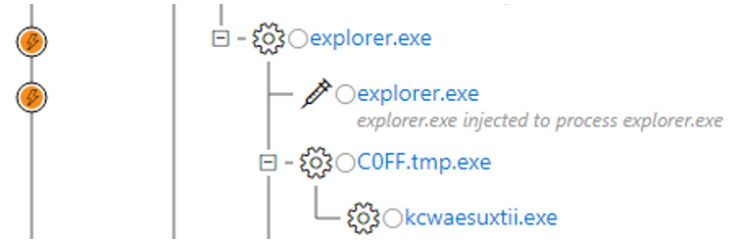
Figure 7: Wood Windows Defender ATP warning process: second replacement process ID
for the discovery process of replacement of code responsible component of protection against exploits in the Windows Defender the Exploit Guard . To do this, enable Export Address Filter (EAF) protection for the explorer.exe process. In this case, the component will detect a spoofing when the shellcode will look in the export address modules of the LoadLibraryA and GetProcAddress functions .
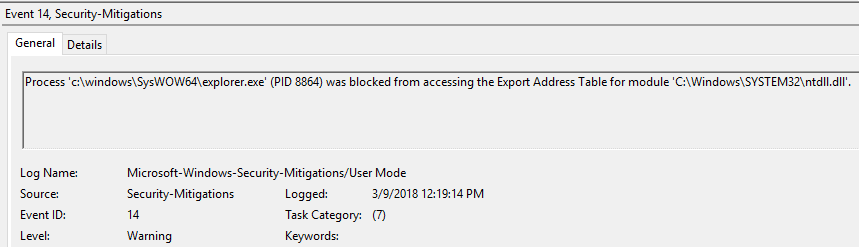
Figure 8. EAF event in the event log
Windows Defender Exploit Guard events are also available on the Windows Defender ATP portal:

Figure 9. Windows Defender Exploit Guard event in Windows Defender ATP
When the EAF audit or blocking policy in Windows Defender Exploit Guard covers popular system processes, such as explorer.exe, cmd.exe, or verclsid.exe, it greatly facilitates the detection and blocking of key methods to replace process code and inject code used by malware. A policy can affect the operation of third-party programs that act as shell code, so we recommend that you test it in the Windows Defender Exploit Guard audit mode before applying it continuously.
Dofoil is especially careful when connecting to C&C servers. The Trojan code first tries to connect to checked web pages to make sure that there is an Internet connection and that it is real, and not imitated in a testing environment. After confirming the authenticity of the Internet connection, the malicious program communicates with real C&C servers via HTTP.
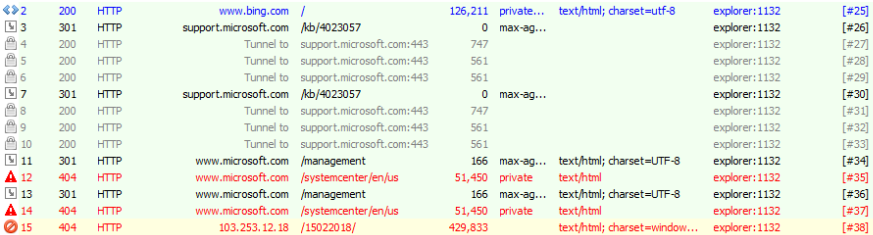
Figure 10. Connecting to known servers to test your Internet connection
Malicious software accesses NameCoin domain name servers. NameCoin is a decentralized DNS server system that provides a high degree of anonymity thanks to blockchain technology. In general, working with it is not particularly different from ordinary DNS queries, but the DNS client must access certain NameCoin DNS servers. Since NameCoin relies on the blockchain model, the history of changes in the domain name can be tracked by blocks.
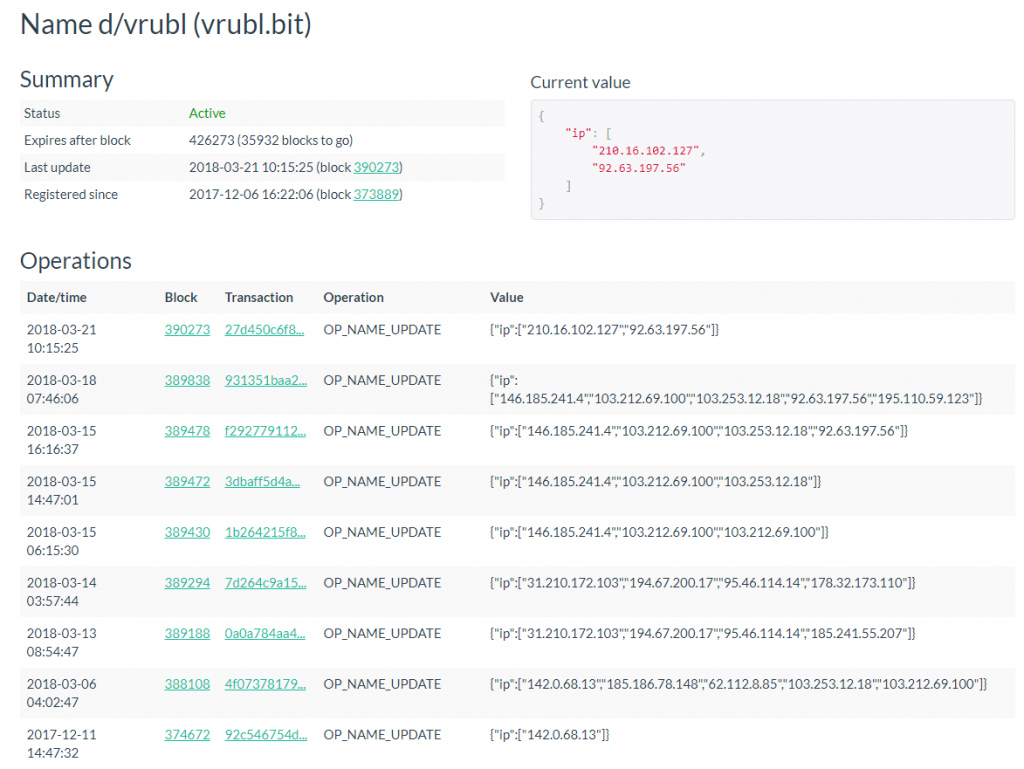
Figure 11. DNS change log for malicious hosts ( https://namecha.in/name/d/vrubl )
Windows Defender ATP allows you to track the network activity of malware. The following warning process tree shows how the malicious process resolves the .bit domain names corresponding to the C&C servers and establishes connections with them. Other actions of the executable file are also visible, for example, connecting to other servers via SMTP ports.
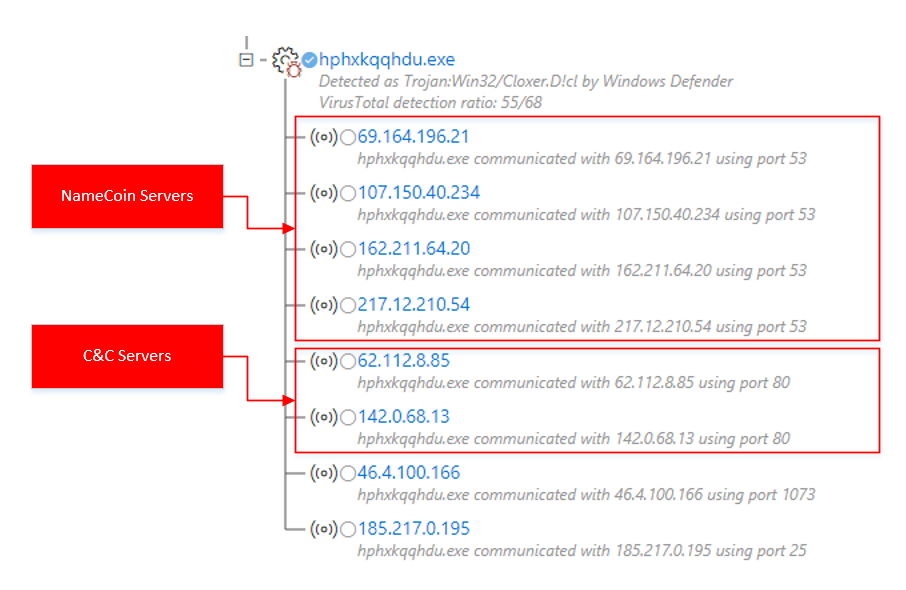
Figure 12. Windows Defender ATP warning process tree: connecting to C&C servers after resolving names through NameCoin servers
The advanced Windows Defender ATP threat search feature, which is still available as a trial version, is able to detect more malicious code samples using NameCoin servers. For example, the following query allows you to see recent connections to them. This can help you learn about other threats that are associated with the same NameCoin servers.
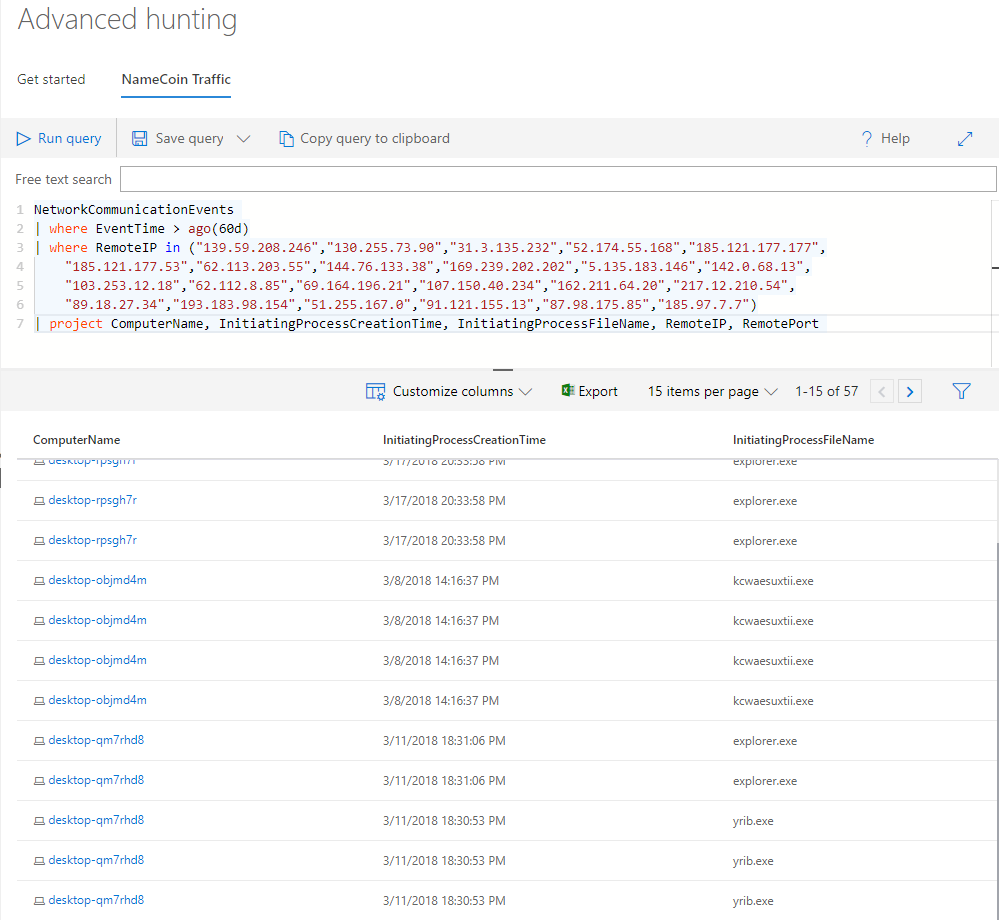
Figure 13. Advanced search for threats that use the same NameCoin servers.
NameCoin is designed to complicate domain management interception (the so-called syncholing). NameCoin domain name records are not managed by some central regulator, therefore such records cannot be changed at the request of law enforcement agencies. Moreover, malware relies on a host of NameCoin DNS servers and it is extremely difficult to stop them.
Dofoil is a very dodgy malware. Using various methods, she checks the nature of the system environment and the authenticity of the Internet connection in order to work only on real computers, and not in the analysis environment or virtual machines. All this slows down the analysis and confuses research systems.
In Dofoil Campaigns, Windows Defender Advanced Threat Protectioncan help security professionals analyze the order of events on the victim’s computer and get detailed information about the process steps, connections to C&C servers, and process code replacement operations. Windows Defender ATP can act as an analysis platform that allows you to configure detailed tracking of system operations in a test environment. Thus, you can save a lot of time and resources on the investigation of infection.
In addition, Windows Defender Exploit Guard can help detect malicious shell code that scans export address tables. This is a great tool to detect and block the actions of exploits and malware.
Windows Defender Exploit Guard events are also visible on the Windows Defender ATP portal, which integrates other Microsoft security solutions, including Windows Defender Antivirus and Windows Defender Application Guard .
In order to evaluate in practice how Windows Defender ATP helps to detect, analyze and repel attacks of increased complexity, get access to a free trial version .
Matt Oh, Stefan Sellmer, Jonathan Bar Or, Mark Wodrich
Windows Defender ATP Research Team
In this publication, we will take a detailed look at the methods of counteracting the launch in debug mode and analysis, which the authors of Dofoil resorted to, and describe how the capabilities of Windows 10 to detect malware can be useful in investigating such attacks.

During the investigation, we found out that the Dofoil virus has built-in methods to counteract the analysis. It checks what environment it is in and stops working in virtual machines. He also scans the memory for the presence of analysis tools and immediately completes their processes. All this significantly complicates the analysis of malicious code.
The following figure shows the steps involved in introducing malware. Some of these include checking for an analysis environment.

Figure 1. A step-by-step diagram of the execution of the shell code and the attack code Dofoil
The table below describes the purpose of each stage. Each of the first five stages includes means of counteracting dynamic or static analysis of malicious code.
| STAGES | DESCRIPTION |
| 1. Disguised shell code | Protects against heuristic analysis. Protects against emulation. |
| 2. Bootstrap Module | Replaces the code of the native process for loading the next module. |
| 3. Anti-debugging module | It stops attempts to start in debug mode. |
| 4. Trojan bootloader module | Checks the system environment. It stops attempts to start inside a virtual machine. Embeds in explorer.exe by replacing the process code. |
| 5. Trojan bootloader module in explorer.exe | It communicates with the management and control server to download the trojan and execute it using the process code replacement method. |
| 6. The bootloader module of the attacking code in explorer.exe | It communicates with the management and control server to download the main attacking code. |
| 7. Trojan module | It steals credentials from the configurations of different applications and transfers the collected data to the management and control server through an HTTP channel. |
| 8. CoinMiner.D | Performs cryptocurrency mining. |
Table 1. Modules implemented by Dofoil at different stages
Initial stages
The first three stages (that is, the disguised shell code, bootstrap module, and anti-debugging module) try to prevent analysis and recognition by the following methods.
| ANTI-ANALYSIS METHODS | DESCRIPTION |
| Built-in clean code | Embeds a huge chunk of clean code to confuse heuristic and manual analysis. |
| Emulation Test | It selects an arbitrary registry key (HKEY_CLASSES_ROOT \ Interface \ {3050F557-98B5-11CF-BB82-00AA00BDCE0B}) and compares the data with the expected value (DispHTMLCurrentStyle) to see if malware is running inside the emulator. |
| Replacing your own process code | Replaces the code of the current process, significantly complicating the analysis due to the changed address markup of the code. |
| Debug check | Checks for debugging tools. Finding them modifies the code, causing a crash. This mechanism complicates the work of researchers who can only find out the reason for such a conclusion. The program checks the PEB.BeingDebugged and PEB.NtGlobalFlag fields in the PEB structure. For example, when the process is running in the debugger, the PEB.BeingDebugged field is set to 1, and PEB.NtGlobalFlag is set to FLG_HEAP_ENABLE_TAIL_CHECK | FLG_HEAP_ENABLE_FREE_CHECK | FLG_HEAP_VALIDATE_PARAMETERS . |
Table 2. Methods of counteracting the analysis
The first stage contains a site with the appearance of clean code, followed by real malicious code. Because of this, executable files may seem safe. In addition, the presence of such code can complicate the emulation, since it is not easy to simulate API calls that are rarely found in malicious code.
The first step code also checks the registry key against the expected value. After passing all the checks, the code decrypts the shell code of the second stage and executes it in the labeled memory area. The shell code clears the memory layout of the source main module, decrypts the shell code of the third stage and puts it in the same memory location - this procedure is called replacing the code of the native process.

Figure 2. Code mutation depending on the value of PEB.BeingDebugged
The Windows Defender ATP process tree helps expose such anti-debugging mechanisms.

Figure 3. Anti-debugging mechanisms visible in the Windows Defender ATP process tree
Trojan downloader module
Before loading the attacking code, the Trojan loader module checks the runtime in various ways, including virtuality and the availability of analysis tools.
| ANTI-ANALYSIS METHODS | DESCRIPTION |
| Checking the name of the module | Checks if the name of the main executable file contains the string “sample”. |
| Checking Volume Serial Number | Checks if the current volume has serial number 0xCD1A40 or 0x70144646 . |
| Checking Modules | Checks for the presence of debugging DLLs. |
| Checking drives for registry keys | Checks the value of the registry key HKLM \ System \ CurrentControlSet \ Services \ Disk \ Enum with common disk name patterns in virtual machines ( qemu, virtual, vmware, xen, ffffcce24 ). |
| Process check | Checks running processes and terminates those related to analysis tools ( procexp.exe, procexp64.exe, procmon.exe, procmon64.exe, tcpview.exe, wireshark.exe, processhacker.exe, ollydbg.exe, idaq.exe, x32dbg .exe ). |
| Checking Windows Class Names | Checks the current Windows class names and exits when it finds common class names related to analysis and debugging ( Autoruns, PROCEXPL, PROCMON_WINDOW_CLASS, TCPViewClass, ProcessHacker, OllyDbg, WinDbgFrameClass ). |
Table 3. Methods of counteracting analysis in the Dofoil Trojan downloader module.
The names of the target processes and Windows classes are stored as a list of specially calculated checksums. The verification algorithm looks like this:

Figure 4. A special algorithm for checking checksums based on shear and exclusive OR operations
Using checksums was supposed to slow down the investigation and prevent researchers from quickly figuring out which analysis tools malware detects.
| LINE | CHECK SUM |
| Autoruns | 0x0E5C1C5D |
| PROCEXPL | 0x1D421B41 |
| PROCMON_WINDOW_CLASS | 0x4B0C105A |
| TCPViewClass | 0x1D4F5C43 |
| Processhacker | 0x571A415E |
| Ollydbg | 0x4108161D |
| WinDbgFrameClass | 0x054E1905 |
| procexp.exe | 0x19195C02 |
| procexp64.exe | 0x1C0E041D |
| procmon.exe | 0x06185D0B |
| procmon64.exe | 0x1D07120A |
| tcpview.exe | 0x060B5118 |
| wireshark.exe | 0x550E1E0D |
| processhacker.exe | 0x51565C47 |
| ollydbg.exe | 0x04114C14 |
| ollydbg.exe | 0x04114C14 |
| x32dbg.exe | 0x5F4E5C04 |
| idaq.exe | 0x14585A12 |
Table 4. Checksum table for Windows process names and classes
Process Code Replacement
Dofoil’s performance is highly dependent on the process code replacement technique. The main target process is explorer.exe. Shell-code Dofoil launches a new instance of explorer.exe, places the shell-code in dynamic memory and modifies the code of the entry point to switch to the shell-code. Due to this, the malware injects the code without using the CreateRemoteThread API function .

Figure 5. Changing the entry point code in explorer.exe
Windows Defender ATP can detect signs of process code replacement by analyzing operations in memory. The following process tree shows how a malicious program is embedded in explorer.exe by replacing the process code.

Figure 6. Windows Defender ATP warning process tree: the first process code replacement
When the shell code loads the next layer of attacking code, it spawns another explorer.exe process, into which it then embeds the attacking code by the replacement method. In such cases, Windows Defender ATP significantly accelerates the analysis, accurately identifying malicious operations and indicating the questionable actions of the newly created Windows system processes.

Figure 7: Wood Windows Defender ATP warning process: second replacement process ID
for the discovery process of replacement of code responsible component of protection against exploits in the Windows Defender the Exploit Guard . To do this, enable Export Address Filter (EAF) protection for the explorer.exe process. In this case, the component will detect a spoofing when the shellcode will look in the export address modules of the LoadLibraryA and GetProcAddress functions .

Figure 8. EAF event in the event log
Windows Defender Exploit Guard events are also available on the Windows Defender ATP portal:

Figure 9. Windows Defender Exploit Guard event in Windows Defender ATP
When the EAF audit or blocking policy in Windows Defender Exploit Guard covers popular system processes, such as explorer.exe, cmd.exe, or verclsid.exe, it greatly facilitates the detection and blocking of key methods to replace process code and inject code used by malware. A policy can affect the operation of third-party programs that act as shell code, so we recommend that you test it in the Windows Defender Exploit Guard audit mode before applying it continuously.
Management and Control Server (C&C) and NameCoin Domains
Dofoil is especially careful when connecting to C&C servers. The Trojan code first tries to connect to checked web pages to make sure that there is an Internet connection and that it is real, and not imitated in a testing environment. After confirming the authenticity of the Internet connection, the malicious program communicates with real C&C servers via HTTP.

Figure 10. Connecting to known servers to test your Internet connection
Malicious software accesses NameCoin domain name servers. NameCoin is a decentralized DNS server system that provides a high degree of anonymity thanks to blockchain technology. In general, working with it is not particularly different from ordinary DNS queries, but the DNS client must access certain NameCoin DNS servers. Since NameCoin relies on the blockchain model, the history of changes in the domain name can be tracked by blocks.

Figure 11. DNS change log for malicious hosts ( https://namecha.in/name/d/vrubl )
Windows Defender ATP allows you to track the network activity of malware. The following warning process tree shows how the malicious process resolves the .bit domain names corresponding to the C&C servers and establishes connections with them. Other actions of the executable file are also visible, for example, connecting to other servers via SMTP ports.

Figure 12. Windows Defender ATP warning process tree: connecting to C&C servers after resolving names through NameCoin servers
The advanced Windows Defender ATP threat search feature, which is still available as a trial version, is able to detect more malicious code samples using NameCoin servers. For example, the following query allows you to see recent connections to them. This can help you learn about other threats that are associated with the same NameCoin servers.

Figure 13. Advanced search for threats that use the same NameCoin servers.
NameCoin is designed to complicate domain management interception (the so-called syncholing). NameCoin domain name records are not managed by some central regulator, therefore such records cannot be changed at the request of law enforcement agencies. Moreover, malware relies on a host of NameCoin DNS servers and it is extremely difficult to stop them.
Conclusion
Dofoil is a very dodgy malware. Using various methods, she checks the nature of the system environment and the authenticity of the Internet connection in order to work only on real computers, and not in the analysis environment or virtual machines. All this slows down the analysis and confuses research systems.
In Dofoil Campaigns, Windows Defender Advanced Threat Protectioncan help security professionals analyze the order of events on the victim’s computer and get detailed information about the process steps, connections to C&C servers, and process code replacement operations. Windows Defender ATP can act as an analysis platform that allows you to configure detailed tracking of system operations in a test environment. Thus, you can save a lot of time and resources on the investigation of infection.
In addition, Windows Defender Exploit Guard can help detect malicious shell code that scans export address tables. This is a great tool to detect and block the actions of exploits and malware.
Windows Defender Exploit Guard events are also visible on the Windows Defender ATP portal, which integrates other Microsoft security solutions, including Windows Defender Antivirus and Windows Defender Application Guard .
In order to evaluate in practice how Windows Defender ATP helps to detect, analyze and repel attacks of increased complexity, get access to a free trial version .
Matt Oh, Stefan Sellmer, Jonathan Bar Or, Mark Wodrich
Windows Defender ATP Research Team
