The difference in approaches to information security between "us" and "them" (for example, DLP)
The modern DLP system is a huge combine that can be used in very different ways. Developers of DLP-systems a couple of years ago were in such a position that they all turned out to have approximately the same product, which needs to be developed somehow, but it’s not entirely clear where. Around then, two different approaches emerged, which can be conditionally divided into “western” and “eastern”. Most likely this is due to differences in business cultures and, in general, to differences in the principles of work of “security personnel”.
What are these differences?


On the left, the Western approach is “close everything, nothing is impossible”, on the right our “control everything and everything”
If you exaggerate, then the DLP system is a program that analyzes all traffic in the organization and blocks transmission if the transmitted information looks confidential.
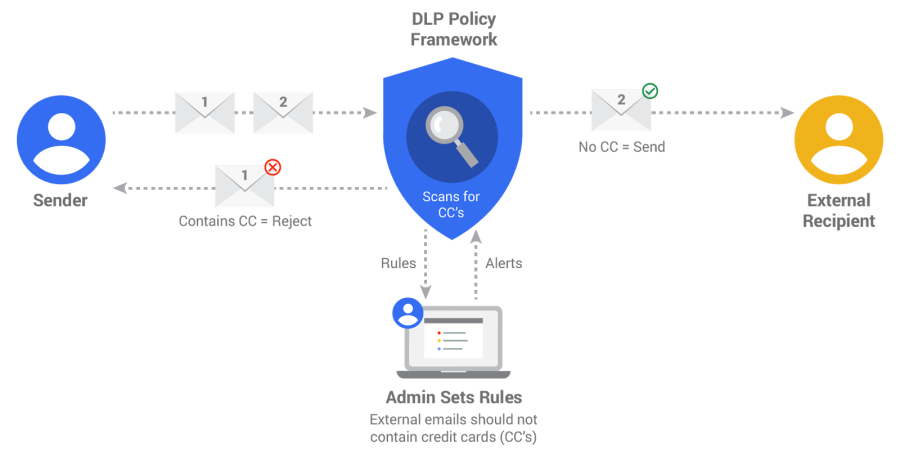
The diagram shows the principle of DLP operation using the example of the rule “prohibit the transfer of credit card data”. Two letters are sent, the letter No. 1 contains credit card details, and the letter No. 2 does not. After analysis on the mail server, letter No. 2 is sent to the addressee, and letter No. 1 is returned to the addressee, and the security guard / administrator receives a notification of an attempted violation
Security experts of the "western" direction use the program only to block "sensitive" information. In practice, it looks like this - they install the system, mark that they understand important information, set up security rules by setting the lock option for certain operations, and return to the system once a month to finalize the rules and check the operability. Everything that is not intended to work is blocked by other tools, and DLP monitors the allowed traffic (most often mail) for violations.
Accordingly, Western developers are primarily concerned with providing quick and reliable locks, an understandable algorithm for setting rules, leaving some kind of analytics to the mercy of other systems (for example, SIEM). Sometimes in “their” systems it’s not even possible to save intercepted data and, accordingly, conduct retrospective analysis and investigations — why, because the system is not designed for this and does not use this functionality?
At the same time, the “eastern” approach is characterized by a different way of managing the instrument received in the hands. While working, DLP collects a huge array of information - all employee negotiations, working hours in applications, visited sites, typed text, etc. During the collection process, the system can not only check for the transfer of sensitive information, but also analyze and process the information in accordance with the settings made - and this data can be made available in a visual form in the form of graphs, charts, tables, document transfer schemes and employee communications.
I specifically do not want to mention the ethical side of the issue, this is too vast a topic and deserves a separate discussion, but this functionality is in demand - therefore, domestic (and Asian, they have a similar approach) developers pay more attention to analytical capabilities, and modern DLP at some point all more like tools for tracking user behavior, UBA class products. With this approach, the economic security of organizations is ensured to a greater extent, security professionals are interested in such a product as a tool for full-fledged investigations, and blocking tools - the main functionality of the "classic" DLP - are paid much less attention.
The difference between the approaches is noticeable with the naked eye, but with what it is connected - the question remains open. Perhaps this is due to different laws and attitudes towards the notorious privacy, or the historical context may be important and “our” guys, along with the Chinese, more like the “manual” control mode than automation. It would also be interesting to find out if there are similar examples of the so different branches of the functionality of similar products during the evolution of “with us” and “with them”, whoever remembers - send it.
What are these differences?


On the left, the Western approach is “close everything, nothing is impossible”, on the right our “control everything and everything”
If you exaggerate, then the DLP system is a program that analyzes all traffic in the organization and blocks transmission if the transmitted information looks confidential.

The diagram shows the principle of DLP operation using the example of the rule “prohibit the transfer of credit card data”. Two letters are sent, the letter No. 1 contains credit card details, and the letter No. 2 does not. After analysis on the mail server, letter No. 2 is sent to the addressee, and letter No. 1 is returned to the addressee, and the security guard / administrator receives a notification of an attempted violation
Security experts of the "western" direction use the program only to block "sensitive" information. In practice, it looks like this - they install the system, mark that they understand important information, set up security rules by setting the lock option for certain operations, and return to the system once a month to finalize the rules and check the operability. Everything that is not intended to work is blocked by other tools, and DLP monitors the allowed traffic (most often mail) for violations.
Accordingly, Western developers are primarily concerned with providing quick and reliable locks, an understandable algorithm for setting rules, leaving some kind of analytics to the mercy of other systems (for example, SIEM). Sometimes in “their” systems it’s not even possible to save intercepted data and, accordingly, conduct retrospective analysis and investigations — why, because the system is not designed for this and does not use this functionality?
At the same time, the “eastern” approach is characterized by a different way of managing the instrument received in the hands. While working, DLP collects a huge array of information - all employee negotiations, working hours in applications, visited sites, typed text, etc. During the collection process, the system can not only check for the transfer of sensitive information, but also analyze and process the information in accordance with the settings made - and this data can be made available in a visual form in the form of graphs, charts, tables, document transfer schemes and employee communications.
I specifically do not want to mention the ethical side of the issue, this is too vast a topic and deserves a separate discussion, but this functionality is in demand - therefore, domestic (and Asian, they have a similar approach) developers pay more attention to analytical capabilities, and modern DLP at some point all more like tools for tracking user behavior, UBA class products. With this approach, the economic security of organizations is ensured to a greater extent, security professionals are interested in such a product as a tool for full-fledged investigations, and blocking tools - the main functionality of the "classic" DLP - are paid much less attention.
The difference between the approaches is noticeable with the naked eye, but with what it is connected - the question remains open. Perhaps this is due to different laws and attitudes towards the notorious privacy, or the historical context may be important and “our” guys, along with the Chinese, more like the “manual” control mode than automation. It would also be interesting to find out if there are similar examples of the so different branches of the functionality of similar products during the evolution of “with us” and “with them”, whoever remembers - send it.
