From anti-malware patches to a holistic strategy
It is not paradoxical, but I still regularly hear as advice on the fight against malware a recommendation on using a modern antivirus and updating it regularly. It seems that the latest stories with WannaCry and Petya / Nyetya occurred in some kind of world different from the one in which those who still believe that anti-virus are all that is needed to fight malware. Even a good antivirus. Even with heuristic mechanisms. Even if they are turned on and at the same time does not slow down the PC. Even if these mechanisms also work, and are not just marketing lure. It’s time for ourselves to formulate a simple conclusion - the fight against modern malware requires a holistic strategy and the balanced use of various technologies, aimed at detecting and preventing the use of malicious code of various methods of penetration and infection. And in order not to be limited to banal phrases, let's try to formulate what a holistic strategy for combating malware should include.
But before I start building a protective wall from individual technological bricks, let's recall what modern malware is like. This is very important, as it is not necessary to allow manufacturers to make marketing statements about 100% detection of unknown viruses, but to realize what modern malware can and what is not and, accordingly, how to resist it.
Yes, there are old viruses that are well detected by standard and commonly used antiviruses on the market. There are probably about 80% of the total number of bad programs. They can often be seen in various videos on corporate YouTube channels or their hashes are often featured in various presentations and materials. Then, by entering such hashes on VirusTotal, you can make sure that the product catches this infection in such a way and that means it is worth it to pay for it. Or not worth it?
And let's try to look at it from the point of view of the creator ... the creator of malicious code. He, or rather a whole group of qualified programmers and architects behind all modern “Non-Petites,” have the following picture as initial data:
What conclusions can be drawn from these three obvious points that any security guard knows, for some reason not using them to stand on the side of Evil and not think “like a hacker” who will try to circumvent all traditional protection systems? I would immediately draw the following conclusions:
That is why the malware creation industry is developed, having good budgets, copying the best practices of software development (yes, virus developers also have agile). But most importantly, malware developers have a high interest in having their creations have a high infection rate and low detection rate. Here is just one, quite old, beginning of 2016, an example showing that antiviruses are not able to detect even the simplest malicious programs.
A typical approach to protection against malware, which is often still called viruses in the old fashion, which creates a feeling of frivolity of the problem, is to use a pair of antivirus and firewall. However, as we saw above, modern malicious code is much more complicated. There are several infection channels - e-mail, Web, Wi-Fi, flash drives, software updates, laptops of contractors, personal mobile devices of management, etc. Moreover, the malware created can use both already known old vulnerabilities and unknown holes (0 -Day). Moreover, malicious code can be based on fragments of viruses already used by someone, as well as written code from scratch, including using various techniques to bypass protection tools at different levels.
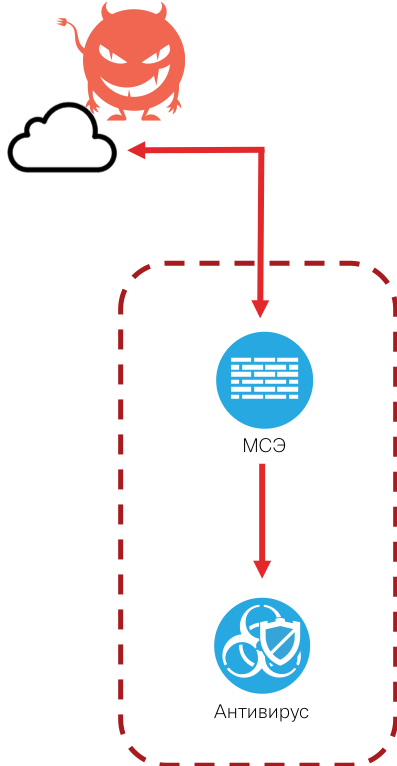
You can even have two or three different antiviruses (as is, for example, recommended or required in Bank of Russia regulations), but this does not help much. Even if they use different anti-virus engines (or they may not :-), they are still based on a method that failed many years ago - comparisons with attack signatures, that is, detection of something known. Although according to the statistics of many information security players today, previously unknown malware is predominantly unique to most customers. This means that most antivirus products are unable to deal with what they do not see and do not know.
A colleague recently sent me a file asking me to check it in our Cisco Threat Grid sandbox.. He had a suspicion regarding this file, and his antivirus did not respond to the file in any way. A few minutes after the start of the analysis, Cisco Threat Grid issued a verdict - the ZBot Trojan. But this is a fairly well-known and old malware. Why didn’t the antivirus catch it? The key word is “old”. It turns out that in order to reduce the size of the signature database that was poured onto each personal computer, the anti-virus vendor decided to disable the old signatures. And it can be understood. The number of signatures is constantly growing and is measured in hundreds of millions and even billions - no hard disk is enough to store all this information. We have to make a choice and it can lead to disastrous consequences.
Yes, you yourself probably remember the story with WannaCry, when many anti-virus vendors who boast of winning the “100% detection of unknown viruses” tests, on the next days (and not all that Friday night) began to send recommendations about the outbreak what needs to be done to overcome this infection. Do you remember? A strange situation is obtained. Information about the vulnerability used by WannaCry has been known for a month, but the malicious code has not yet used it, and therefore there are simply no signatures in anti-virus databases. Therefore, most of the traditional means of combating malicious code work post-factum, struggling with something known. When it came to mass epidemics, this approach worked, but in the conditions of mostly unique malware, it began to fail.
OK, but doesn't ITU help us cut off connections to C&C servers? In theory, yes. In practice, we encounter two difficulties. Firstly, according to Cisco statistics, about 92% of malicious programs use the DNS protocol, which few ordinary firewalls can filter (NGFW with DNS inspection, for example, Cisco Firepower NGFW, are already needed here ). And secondly, in order to block interaction with C&C nodes, you need to know the addresses of these nodes, and they change constantly and, accordingly, ITU must also promptly update its rules, which does not happen in practice.
What needs to be done to increase the company's security against malware? In addition to the regular installation of patches, backups and restrictions on the use of the rights of local administrators by users, let's recall the possible infection vectors. According to statistics, the lion's share of all infections is carried out through two main channels - Web and e-mail. This means that the protection solutions that will filter the traffic for malicious attachments should also protect these channels. At Cisco, this is the E-mail Security Appliance and the Web Security Appliance .
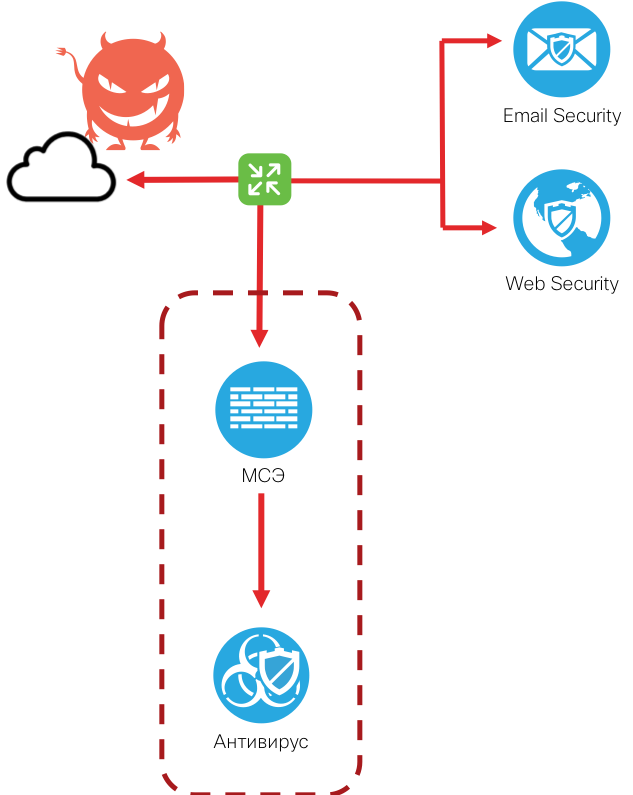
But the overlap of the two main channels for malicious code to get inside the organization does not remove the problems of antiviruses that catch only the known. Is there a technology that allows you to analyze files, regardless of the presence or absence of digital fingerprints (signatures) on them? Yes, it’s called a sandbox and allows it to perform static and dynamic analysis of a file with a view to performing any unauthorized actions - access to the registry, copying files, interacting with C&C servers, encapsulating in allowed traffic, etc. The same Cisco Threat Grid sandbox can analyze over 700 different parameters and behavior factors of files to determine their harmfulness. It is the sandbox that protects the tools that have built-in anti-virus engines, but cannot detect unknown viruses. Sandbox integration provides this opportunity. In the case of the Cisco security architecture, all security solutions are associated with the Threat Grid sandbox - Cisco E-mail Security Appliance, Web Security Appliance, Cisco Firepower NGFW / NGIPS, Cisco ASA with FirePOWER Services, Cisco AMP for Endpoints, Cisco Umbrella, etc.
Suppose we protected the network perimeter, but what to do with mobile users? Around them, we cannot build defensive walls from ITU, IPS, content gateways and sandboxes. MDM solutions do not greatly help us deal with malicious code, since they have a different purpose. Mobile antivirus? He has the same problem as previously described. And not all mobile platforms have anti-malware tools (for example, for the iPhone). How then to fight? Again, we must take the side of the attacker and see how he creates his creations. As a rule, they do not work autonomously, but use a client-server architecture, which implies communication with the management server, and most often the DNS protocol is used for this. If we can inspect it, then we will solve most of the problems with malicious code on mobile platforms.Cisco Umbrella ) and in addition to the DNS service, we also get full protection against interaction with C & C-servers. In fact, Cisco Umbrella also allows us to cut off phishing resources, DGA domains used to spread malware, track clone sites, kill switch domains, etc.

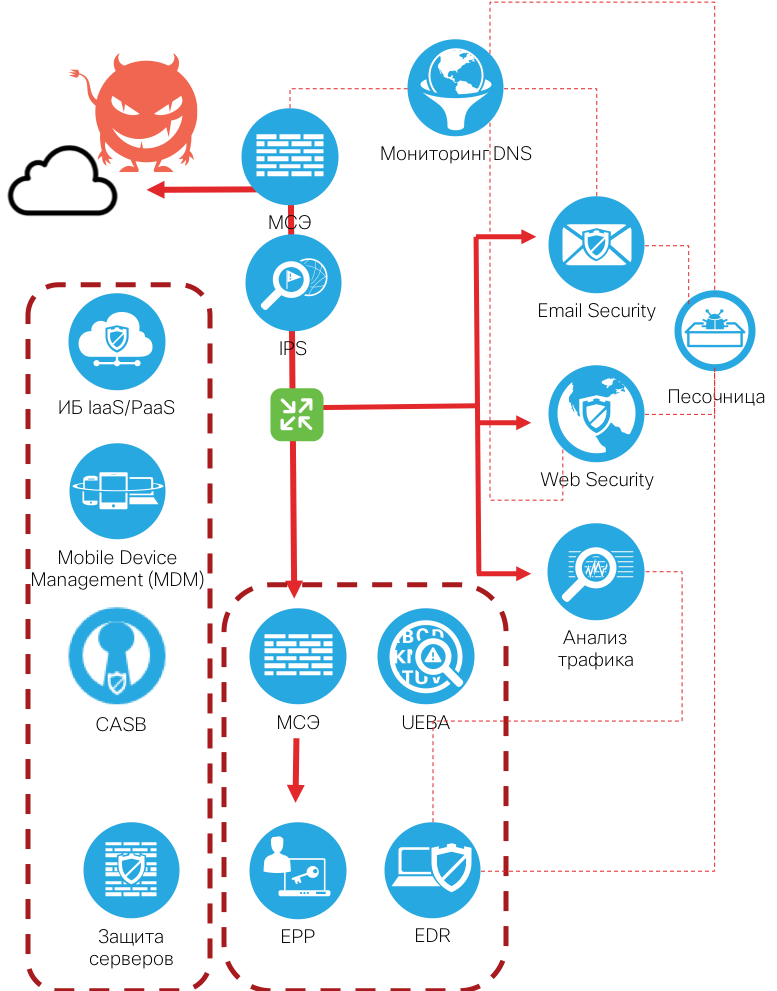
Let's go back to the story with WannaCry. The CEO of a large industrial company on Friday evening picked up WannaCry on his home computer. Without hesitation, on Saturday morning he brought the infected laptop to work, connected it to the corporate network, simultaneously causing his IT specialists to “figure it out”. While they were driving to work, WannaCry began to spread over the internal network, despite the rather good perimeter protection. But there are still flash drives with an unknown virus, hacking Wi-Fi, laptops of contractors, etc. What to do in this situation? The only answer is to monitor the internal infrastructure using NTA and EDR technologies. These are abbreviations that mean two classes of security features - Network Traffic Analysis and Endpoint Detection and Response.
An analysis of network traffic (for example, using Cisco Stealthwatch ) allows us to identify the manifestations of malicious code even when there are no protection tools on the terminal devices, even outdated antiviruses. Moreover, due to ETA technology, it is possible to detect signs of malicious activity even in encrypted traffic. In turn, it’s time to exchange antiviruses for solutions of the EDR class (for example, Cisco AMP for Endpoint ), which are built not on the principle of preventing all 100% threats, but be prepared for the fact that a compromise of the node can still occur and you need to be able to be able to timely detect this fact and react to it.
The firewall on the perimeter has its own analogy in the internal network - it is a network access control system (for example, Cisco ISE ), which provides segmentation of the internal network and localization of the spread of malicious code if it enters the internal network in one way or another. Ideally, a network traffic analysis solution, detecting the first attempts to spread malicious code, can give a command to a network access control system to block an infected computer by disconnecting the switch port or entering the quarantine subnet by changing the ACL on the router.
Of course, all the technologies described above should not work separately or offline, but in close cooperation with each other, exchanging alarms, security policies, teams, as well as indicators of compromise. By the way, regarding indicators (IoC). They also need to be regularly received from external sources ( Cisco Talos plays the role of such a source ) and equipped with knowledge of constantly changing threats, all security tools - perimeter, cloud, personal or internal.
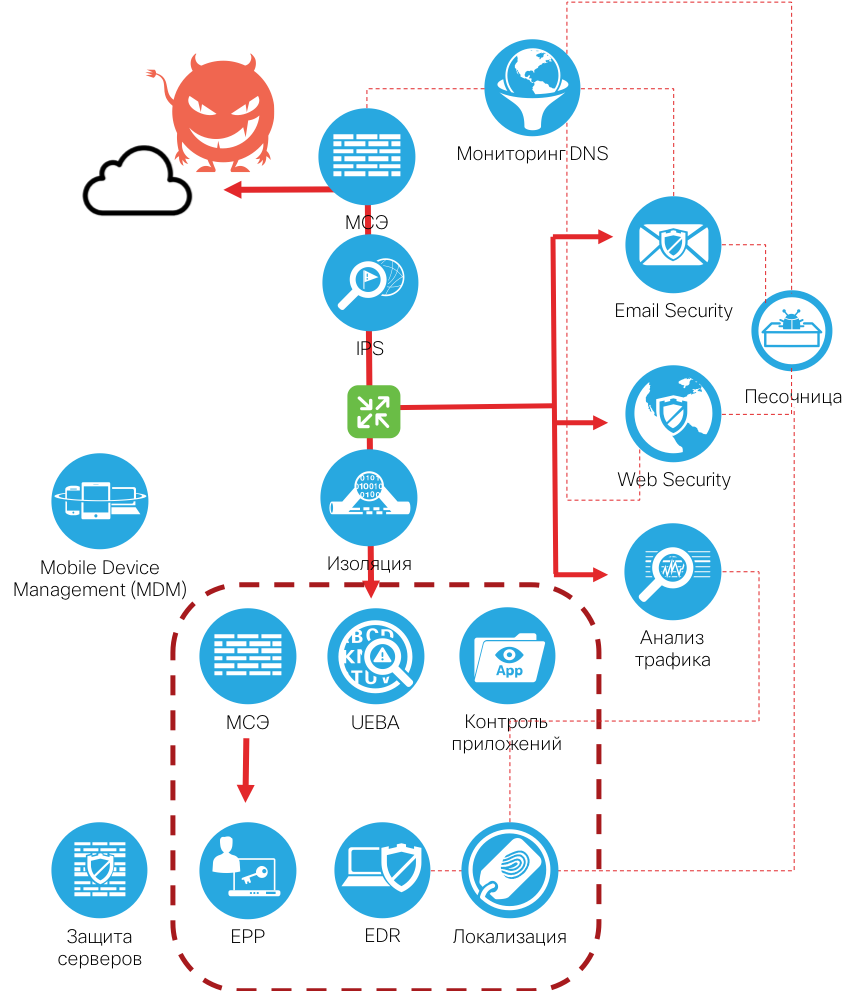
The strategy described above is optimal for protection against 98% of malicious code. Can we increase this value by approaching the cherished hundred? In fact, it is possible, but it must only be understood that in this case we will have to significantly degrade the operational characteristics of our network and reduce the usability of the users. This is achieved by abandoning the blacklist paradigm and moving to the rule "only what is known is allowed." Allowed applications, IP addresses, users, etc. As we understand it, this approach has significant limitations in real life, but it can significantly limit the operation of malicious code. An additional level of protection is achieved through isolation technologies, virtualization, remote browsers, TPM, OS integrity control, remote verification, electronic e-mail signature.
I described several strategies for protecting against malicious code - from minimalist to maximum. Does this mean that we can completely prevent the infection of our internal network and mobile users? Alas. No one can guarantee 100% protection. But the task of this note was different - to show that the point of view still existing that antivirus alone can save from modern malware has long been “rotten” and that only an integrated approach can solve the problem and you need to use it as a starting point that we already wrote about .
Description of the use of Cisco network Cisco StealthWatch
description technology for detecting malicious code in encrypted traffic
Description approach to finding kriptomaynerov network
construction system of protection based on the Use Case
Description combating programs, cryptographers strategy
description combat WannaCry strategy
Description of application in the ISE Cisco Cisco network
VPO development industry
But before I start building a protective wall from individual technological bricks, let's recall what modern malware is like. This is very important, as it is not necessary to allow manufacturers to make marketing statements about 100% detection of unknown viruses, but to realize what modern malware can and what is not and, accordingly, how to resist it.
Yes, there are old viruses that are well detected by standard and commonly used antiviruses on the market. There are probably about 80% of the total number of bad programs. They can often be seen in various videos on corporate YouTube channels or their hashes are often featured in various presentations and materials. Then, by entering such hashes on VirusTotal, you can make sure that the product catches this infection in such a way and that means it is worth it to pay for it. Or not worth it?
And let's try to look at it from the point of view of the creator ... the creator of malicious code. He, or rather a whole group of qualified programmers and architects behind all modern “Non-Petites,” have the following picture as initial data:
- they know that malware will be searched through various means of information protection
- they know that a sandbox can be used to analyze unknown malicious code
- they know that 99% of victims companies use widespread, purchased protection software.
What conclusions can be drawn from these three obvious points that any security guard knows, for some reason not using them to stand on the side of Evil and not think “like a hacker” who will try to circumvent all traditional protection systems? I would immediately draw the following conclusions:
- Malicious code must be unique and must not be repeated
- Malicious code must use multiple distribution vectors
- Malicious code must be modular
- Malicious code should bypass the methods of its detection and analysis.
That is why the malware creation industry is developed, having good budgets, copying the best practices of software development (yes, virus developers also have agile). But most importantly, malware developers have a high interest in having their creations have a high infection rate and low detection rate. Here is just one, quite old, beginning of 2016, an example showing that antiviruses are not able to detect even the simplest malicious programs.
A typical approach to protection against malware, which is often still called viruses in the old fashion, which creates a feeling of frivolity of the problem, is to use a pair of antivirus and firewall. However, as we saw above, modern malicious code is much more complicated. There are several infection channels - e-mail, Web, Wi-Fi, flash drives, software updates, laptops of contractors, personal mobile devices of management, etc. Moreover, the malware created can use both already known old vulnerabilities and unknown holes (0 -Day). Moreover, malicious code can be based on fragments of viruses already used by someone, as well as written code from scratch, including using various techniques to bypass protection tools at different levels.

What is bad antivirus with ITU?
You can even have two or three different antiviruses (as is, for example, recommended or required in Bank of Russia regulations), but this does not help much. Even if they use different anti-virus engines (or they may not :-), they are still based on a method that failed many years ago - comparisons with attack signatures, that is, detection of something known. Although according to the statistics of many information security players today, previously unknown malware is predominantly unique to most customers. This means that most antivirus products are unable to deal with what they do not see and do not know.
A colleague recently sent me a file asking me to check it in our Cisco Threat Grid sandbox.. He had a suspicion regarding this file, and his antivirus did not respond to the file in any way. A few minutes after the start of the analysis, Cisco Threat Grid issued a verdict - the ZBot Trojan. But this is a fairly well-known and old malware. Why didn’t the antivirus catch it? The key word is “old”. It turns out that in order to reduce the size of the signature database that was poured onto each personal computer, the anti-virus vendor decided to disable the old signatures. And it can be understood. The number of signatures is constantly growing and is measured in hundreds of millions and even billions - no hard disk is enough to store all this information. We have to make a choice and it can lead to disastrous consequences.
Yes, you yourself probably remember the story with WannaCry, when many anti-virus vendors who boast of winning the “100% detection of unknown viruses” tests, on the next days (and not all that Friday night) began to send recommendations about the outbreak what needs to be done to overcome this infection. Do you remember? A strange situation is obtained. Information about the vulnerability used by WannaCry has been known for a month, but the malicious code has not yet used it, and therefore there are simply no signatures in anti-virus databases. Therefore, most of the traditional means of combating malicious code work post-factum, struggling with something known. When it came to mass epidemics, this approach worked, but in the conditions of mostly unique malware, it began to fail.
OK, but doesn't ITU help us cut off connections to C&C servers? In theory, yes. In practice, we encounter two difficulties. Firstly, according to Cisco statistics, about 92% of malicious programs use the DNS protocol, which few ordinary firewalls can filter (NGFW with DNS inspection, for example, Cisco Firepower NGFW, are already needed here ). And secondly, in order to block interaction with C&C nodes, you need to know the addresses of these nodes, and they change constantly and, accordingly, ITU must also promptly update its rules, which does not happen in practice.
And if you add security Web and E-mail gateways?
What needs to be done to increase the company's security against malware? In addition to the regular installation of patches, backups and restrictions on the use of the rights of local administrators by users, let's recall the possible infection vectors. According to statistics, the lion's share of all infections is carried out through two main channels - Web and e-mail. This means that the protection solutions that will filter the traffic for malicious attachments should also protect these channels. At Cisco, this is the E-mail Security Appliance and the Web Security Appliance .

But the overlap of the two main channels for malicious code to get inside the organization does not remove the problems of antiviruses that catch only the known. Is there a technology that allows you to analyze files, regardless of the presence or absence of digital fingerprints (signatures) on them? Yes, it’s called a sandbox and allows it to perform static and dynamic analysis of a file with a view to performing any unauthorized actions - access to the registry, copying files, interacting with C&C servers, encapsulating in allowed traffic, etc. The same Cisco Threat Grid sandbox can analyze over 700 different parameters and behavior factors of files to determine their harmfulness. It is the sandbox that protects the tools that have built-in anti-virus engines, but cannot detect unknown viruses. Sandbox integration provides this opportunity. In the case of the Cisco security architecture, all security solutions are associated with the Threat Grid sandbox - Cisco E-mail Security Appliance, Web Security Appliance, Cisco Firepower NGFW / NGIPS, Cisco ASA with FirePOWER Services, Cisco AMP for Endpoints, Cisco Umbrella, etc.
How to protect mobile users?
Suppose we protected the network perimeter, but what to do with mobile users? Around them, we cannot build defensive walls from ITU, IPS, content gateways and sandboxes. MDM solutions do not greatly help us deal with malicious code, since they have a different purpose. Mobile antivirus? He has the same problem as previously described. And not all mobile platforms have anti-malware tools (for example, for the iPhone). How then to fight? Again, we must take the side of the attacker and see how he creates his creations. As a rule, they do not work autonomously, but use a client-server architecture, which implies communication with the management server, and most often the DNS protocol is used for this. If we can inspect it, then we will solve most of the problems with malicious code on mobile platforms.Cisco Umbrella ) and in addition to the DNS service, we also get full protection against interaction with C & C-servers. In fact, Cisco Umbrella also allows us to cut off phishing resources, DGA domains used to spread malware, track clone sites, kill switch domains, etc.

Let's look towards NTA and EDR
Let's go back to the story with WannaCry. The CEO of a large industrial company on Friday evening picked up WannaCry on his home computer. Without hesitation, on Saturday morning he brought the infected laptop to work, connected it to the corporate network, simultaneously causing his IT specialists to “figure it out”. While they were driving to work, WannaCry began to spread over the internal network, despite the rather good perimeter protection. But there are still flash drives with an unknown virus, hacking Wi-Fi, laptops of contractors, etc. What to do in this situation? The only answer is to monitor the internal infrastructure using NTA and EDR technologies. These are abbreviations that mean two classes of security features - Network Traffic Analysis and Endpoint Detection and Response.
An analysis of network traffic (for example, using Cisco Stealthwatch ) allows us to identify the manifestations of malicious code even when there are no protection tools on the terminal devices, even outdated antiviruses. Moreover, due to ETA technology, it is possible to detect signs of malicious activity even in encrypted traffic. In turn, it’s time to exchange antiviruses for solutions of the EDR class (for example, Cisco AMP for Endpoint ), which are built not on the principle of preventing all 100% threats, but be prepared for the fact that a compromise of the node can still occur and you need to be able to be able to timely detect this fact and react to it.
The firewall on the perimeter has its own analogy in the internal network - it is a network access control system (for example, Cisco ISE ), which provides segmentation of the internal network and localization of the spread of malicious code if it enters the internal network in one way or another. Ideally, a network traffic analysis solution, detecting the first attempts to spread malicious code, can give a command to a network access control system to block an infected computer by disconnecting the switch port or entering the quarantine subnet by changing the ACL on the router.
Of course, all the technologies described above should not work separately or offline, but in close cooperation with each other, exchanging alarms, security policies, teams, as well as indicators of compromise. By the way, regarding indicators (IoC). They also need to be regularly received from external sources ( Cisco Talos plays the role of such a source ) and equipped with knowledge of constantly changing threats, all security tools - perimeter, cloud, personal or internal.

Returning to a closed software environment and isolation from the outside world
The strategy described above is optimal for protection against 98% of malicious code. Can we increase this value by approaching the cherished hundred? In fact, it is possible, but it must only be understood that in this case we will have to significantly degrade the operational characteristics of our network and reduce the usability of the users. This is achieved by abandoning the blacklist paradigm and moving to the rule "only what is known is allowed." Allowed applications, IP addresses, users, etc. As we understand it, this approach has significant limitations in real life, but it can significantly limit the operation of malicious code. An additional level of protection is achieved through isolation technologies, virtualization, remote browsers, TPM, OS integrity control, remote verification, electronic e-mail signature.

As a summary
I described several strategies for protecting against malicious code - from minimalist to maximum. Does this mean that we can completely prevent the infection of our internal network and mobile users? Alas. No one can guarantee 100% protection. But the task of this note was different - to show that the point of view still existing that antivirus alone can save from modern malware has long been “rotten” and that only an integrated approach can solve the problem and you need to use it as a starting point that we already wrote about .
Additional Information:
Description of the use of Cisco network Cisco StealthWatch
description technology for detecting malicious code in encrypted traffic
Description approach to finding kriptomaynerov network
construction system of protection based on the Use Case
Description combating programs, cryptographers strategy
description combat WannaCry strategy
Description of application in the ISE Cisco Cisco network
