FastTrack Training. "Network Basics." "Fundamentals of telephony." Part 2. Eddie Martin. December 2012
- Tutorial
About a year ago, I noticed an interesting and fascinating series of lectures by Eddie Martin, which is incredibly intelligible, thanks to its history and real life examples, as well as colossal experience in teaching, which allows us to gain an understanding of rather complex technologies.

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Product Software”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the twentieth of them.
We broadcast voice using applications and we are committed to ensuring the operation of customer applications. Cisco did not know anything about PBX, therefore, when we explained the advantage of our telephony, we first of all pointed to the highest reliability. Our equipment had a phenomenal fault tolerance of 99.999%. This means that Cisco downtime did not exceed 5 minutes per year! But what is considered a downtime in telephony?
By creating VoIP, we opened the whole world to users. If you return to the issues of reliability, then there are several interesting features.
Let 24 telephones be connected to one of the cards of our station (lower left segment). My PBX has 600 such stations. If one such 24-card card fails, will this be considered a system downtime?

Where is the starting point after which you can tell whether the system is working or not, how fault tolerant it is, what percentage of its reliability? So, classical telephony was considered inoperative if 30% of its infrastructure became unavailable. Suppose your day started unsuccessfully, a policeman stopped you and fined you on the way to work, then your wife called and announced that she was getting divorced. You are in a disgusting mood, you pulled out a phone card in your hearts and disabled 24 phones. Is this a system crash? Of course not. If you have 600 such stations, then in order for the system to be considered inoperative, you must get rid of 30% - this is 180 stations. This is what a system failure means.
But an ordinary Cisco employee did not know about all this, and we made many mistakes trying to overcome our competitors until we found the best way. You know, people still do not see the difference between IP telephony and VoIP technology. They do not understand that the difference lies in the fact that we do not just transmit the voice, but turn it into an application! We just had to do something about it. In 2001, customers became interested in our technology, and 2002 was a really good year for us. There was an economic downturn in the country, but we managed to sell a lot of our products. Let me remind you that in 2000 Nortel was the leader in the field of networks, and Avaya was the leader in production on the market. But already in 2009, No. 1 became Cisco. This is a very short period for the market, and during this time we were able to change the world.
We did not specialize in the production of equipment specifically for offices, but we have a series of switches 6000 Business Edition, designed for small companies. I will digress from the topic a bit and give one example. Customers often told me that they did not need voicemail. Do you think my daughter Emily uses voicemail? No, she never answers voice messages. This suggests that the rules of the game are changing. We must strengthen the development of those changes in technology that really interest people today. We must make sure that new customers come to us.
Regarding my drawing, we need to know and explain to our customers the role of Cisco in this area. We introduced our technology and thereby stimulated the entire telephony market. We switched to IP-technology and all this hardware has sunk into the past. A little later we will talk about HCS, a hierarchical honeycomb structure.
Now let's talk about how Cisco solutions look. I already told you that since I'm not very smart, I like to simplify everything. Therefore, we consider solutions from three sides - services, customers, and infrastructure.
Services are a combination of network software and applications with which one or another type of client interacts, and the infrastructure will depend on what these clients require for their work.
A typical solution is a switch with which an IP phone is connected using PoE. The last word “telephone” as a physical device should disappear. It is not needed in this technology, but people continue to use telephones. So in reality, an IP phone is not a phone at all, but a client. After all, we have a personal computer PC, where you can put this client. This is the Jabber client.
Next - what service does our switch need, what software does it need? He needs a CM communications manager.

Our phone has an IP address 10.10.10.6 and a MAC address A. How do we associate a phone with a CM manager? We need to put the MAC address of our phone there. That is, CM is a database with tables of all components. This table has MAC addresses, EXT extensions for mobility, that is, passwords and logins, and telephone features. And by the way, when the phone contacts SM, it sends it its IP address. Thanks to this, you can transfer your phone anywhere and connect to the network wherever you want.

Our computer has a MAC address B and an IP address 11.11.11.9. We also enter these data into the CM table.
I pick up the phone, or press a button, and my IP phone sends CM one packet. This starts recording call details, or CDR (Call Detail Record). It allows you to track this call, see that the call is taking place. The SM manager sends another packet to the phone - this is a beep that informs the client that the phone is working. Suppose our phone has an extension of 3000, and the computer, or rather, its Jabber client, is 3200. The call from the phone goes to the CM, which determines the extension of the device with the number 3200 from the table and finds its IP address, and then sends the call to the computer. And the computer starts ringing like a regular phone, showing that someone is calling its owner. Both the "iron" and the "softphone" react equally to an incoming call - they both produce a ringing noise. The communication manager organizes a direct conversation between network clients, two RTP-poktoka, in both directions. They do not go through him; he only organizes it. When one of the subscribers hangs up, the signal enters the CM and it stops recording CDR, and the customer phones go into normal mode. Here's how it works - it's not rocket science.
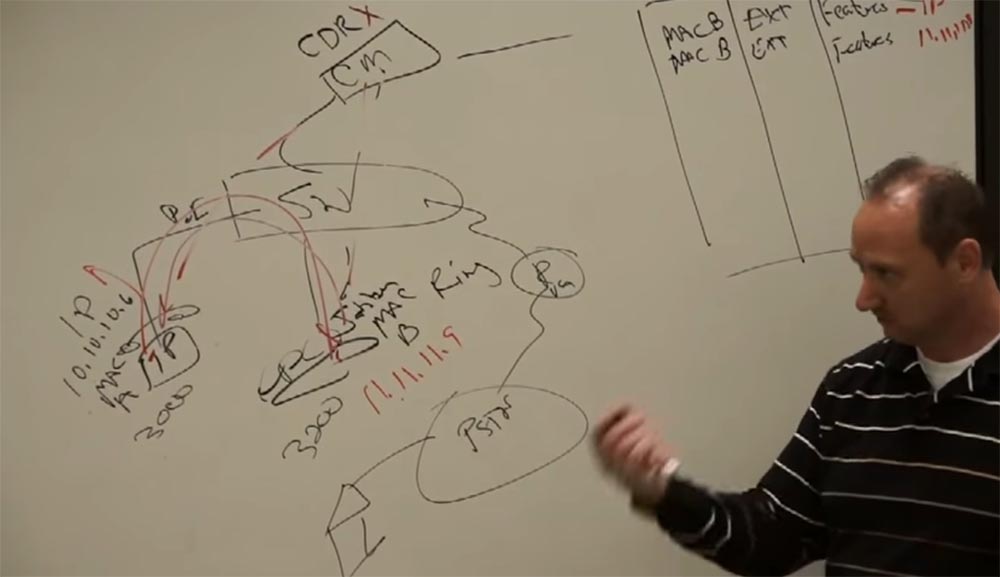
What happens if I want to call someone who is outside our network? I will draw here a router with a “voice gateway” VG, which is connected to the PSTN, and that one with the subscriber’s home phone.
Suppose I want to call my wife to find out if her dog has eaten anything else. Two days ago, when I put my things downstairs, she was worrying about my hat, my favorite hat. Never before had a wife's dog been so close to death. I pick up the phone, the signal is received by CM, then I dial my home number, SM checks it according to the table - oh, this is an external call! And turns to the switch. He contacts the router, which has its own IP address, and the router sends the called number to the PSTN, and then the city network calls my wife to the phone. Similarly, calls are made via Wi-Fi, because it is the same network.
I will tell you an important thing that I always say to my clients. Classic telephone exchanges did all these things, but the problem was that PBX was literally stuffed with different equipment, a bunch of cards with different functions. Therefore, it was very difficult to achieve fault-tolerant joint work of all this “iron”, it was too much.
We proposed a solution whereby a call takes 17 steps before connecting two subscribers, but thanks to protocols and applications this happens on a minimum amount of hardware. We proceeded from the principle of “do not make complicated what can be simplified”. Our result was not a server for selected clients, but a server for absolutely everyone.
The table located in the CM is a phone book. We all used them once. The last time I used the phone book was when I needed a target for an air rifle. It was convenient to shoot at her, and she was the cheapest target.
They ask me if Microsoft played a role in the development of IP telephony. This refers to software for making phone calls through a computer. Undoubtedly, since Microsoft is developing software, they took part in this, created a client-server emulator. As they say, it's hard not to notice an elephant in the room. However, in 2001, when we were engaged in IP-telephony, Microsoft had nothing to do with it. They picked up the technology and were forced to create software for computers with call features already upon the existence of IP-telephony.
Here, our representative from Australia is present in the hall, and I will notice that more IP telephony systems are being sold in Australia than anywhere else in the world. In North America, about 60% of telephone systems sold are based on IP solutions, of which 40% are Cisco products. But I want to ask you to be careful with these numbers - the number of IP phones does not match the number of phone numbers. For example, a client has 25 IP phones and 560 regular telephone sets, these are different numbers. So be careful when telling customers about these numbers.
We will expand our scheme. I’ll add a WAN to our router, then another 1 router, also connected to the PSTN, then I will put the switch and attach the IP phone to it.
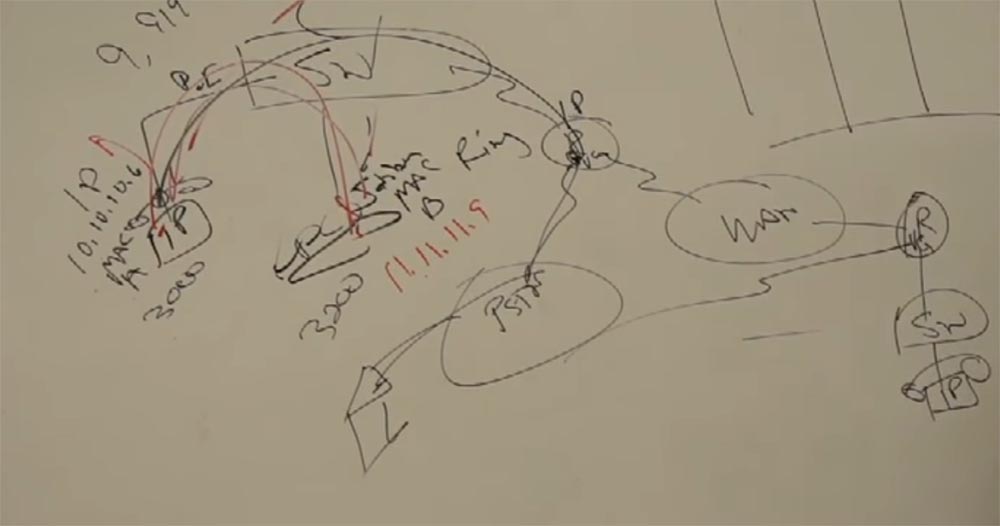
This phone does not need a separate PBX. His data is entered in the table SM and he becomes a full member of our network. Suppose it has a code of 4000. I pick up the phone of my phone with code 3000 and call my friend, that is, I call the number 4000. And the SM ensures that my IP phone “talks” to my friend’s IP phone, that is, it connects two IP together. At the same time, we have a choice - I can contact this number via PSTN or send a call via WAN. I have two different networks and I can choose the one that suits me best.
In the case of WAN, we have bandwidth limitations. Remember how I drew pipes of different diameters: a wide pipe, a narrow tube, again a wide pipe. My IP phone encapsulates voice, turns it into data, and uses a 64 Kbps channel. More service information is added to the outgoing packet, and I get a 100 Kbit packet for 1 second of the call. For LAN equipment, this is negligible. But for a WAN with a throughput of 2 Mbps, this value does not seem too small. Therefore, we use codecs that pack a voice call of only 8 Kbit, and we get a packet size 4 times smaller - only 25 Kbit for 1 second of a call. This reduces the load on the WAN.
Our CM communications manager should ask the router if the router can pass the call through the WAN. Why is this done? Because the router controls this bridge between the system and the WAN. And administrative call control is becoming more and more important. After all, we want to transmit not only voice, but also video and other data.
So, if the router allows you to skip the call, then the SMS informs our phone at the system input that the call needs to be transcoded to a lower bitrate of 8 Kbit, because it will go through the WAN, which has limited bandwidth. This is how the system that connects the phone with code 3000 and the phone with code 4000 works.

This technology is provided by the routing protocol over which the router works. SM allows you to simultaneously send 6 calls over the network. In total, the system uses 4 different protocols for transferring calls.
How many telephones or video devices can be connected to one SM communication manager? 40 thousand devices! In this case, we have a restriction determined by the capabilities of the server. Cisco, as a very good engineering company, has documentation that tells the user about the capabilities of the cluster solution and how to combine hundreds of such servers into one IP solution. That is, you have the potential to connect 4 million phones to the same network, which is provided by Cisco technical support. We have several such clusters in India, Europe, North America, and so on.
Now let's talk about clusters. The first SM you set up, let's call it Publisher - Publisher. He owns a database. I want to have redundancy here for fault tolerance, right? And so we have a second CM, Subscriber - Subscriber, and this manager receives data from Publisher. When you download this system, CM asks Publisher or Subscriber it. The first can do anything, read, write. But Subscriber immediately asks the question, where is my Publisher? These devices are separated so that our database remains complete and provides fault tolerance. The database can be located both on an independent server and on a virtual one, and the CM is a device that can request this database and use it for its needs. Let me remind you that all these servers are software, application.
So, Publisher owns the information, and Subscriber uses it. At what distance from the Publisher can a Subscriber be placed? Are they in the same common building?
The requirements stipulate a time of 80 milliseconds for the mutual exchange of data between the two devices.
I will give you an example. North America is a big enough continent, big enough for me, especially when you fly across the continent often. I worked in Telus, Canada, and we talked about the possibilities of technology. And I was told that they are able to provide information from Halifax, Nova Scotia, and this is on the other side of the continent, to Calgary in 80 ms and the claimed bandwidth. So I can place my Publisher in Calgary, and the Subscriber in Halifax, at a distance of ¾ the length of the continent, and such a speed of communication between them will be guaranteed.
So, Publisher and Subscriber form a cluster. A cluster may consist of two or more SM communication managers using a common database.

In one cluster, you can combine 20 servers. What should you buy by downloading CM communication manager software? Only user license! You do not need to buy any additional physical devices.
If you use UCS, the Cisco server platform, then install the new server software from existing equipment under license. You can buy 20 or 50 licenses and connect the corresponding number of user phones to the network. You simply upload the new CM to an existing server and run it. This solution is based on VMware technology. Based on Linux, a virtual machine is created that organizes a virtual network. The guide for the deployment of such a network consists of 1200 pages, and absolutely all the principles of work and steps are described there. Cisco C Series equipment is used to create these networks, but you can use IBM servers and other products with which our equipment is compatible.
The license enters the CM, which performs all the actions provided for by this license. Users can even choose their phone numbers, if required by the license.
We do not need telephonists in their classical understanding, but in the companies of clients there are external technical specialists who are involved in IP-telephony.
I want to return again in 2000-2001, when we just entered the market with our technology. Then we used the SCCP protocol, and now SIP - perhaps this is the whole difference with the 2001 configuration.
Consider what happens if the WAN fails - here I cross it out.

We will have a client that does not see its server. It will not have a way to transfer data to the server.
Suppose your mail server has disappeared at home. The Internet has disconnected, and when you open Outlook or another email client, you cannot send an email. So, the communication manager, as soon as he sees that the connection with any client IP has disappeared, will immediately inform that the WAN is out of order. However, we cannot risk the business of our customers. Therefore, Cisco in less than 3.5 months created special software for the router called SRST - “invulnerable remote telephone communications” - which shows that our equipment has much greater capabilities than you might imagine.
We have been using this system since 2001 - look at how it looks in the picture.

You can call from the branch (upper left telephone) to headquarters (lower right telephone), talk with a friend (lower left telephone) or order pizza in the city. In the first case, the call will go through the IP WAN, in the second - directly through the local network of the branch connecting the upper and lower phones, and in the third case through the public telephone network PSTN. Assume that the connection to the IP WAN is interrupted.

Having discovered this, the branch server will make 3 attempts to contact the subscriber at headquarters. If this does not succeed, he will forward the call to bypass the WAN via PSTN and then to the headquarters router. We have been using this method of providing reliable communications since 2001. This is made possible because in our IP telephony system, PSTN and IP WAN are separate and can operate independently. This is not in the classical telephone network, so it is less reliable.
Keep in mind that our customers are not alike. For example, some need voicemail, others do not, and this must be taken into account. Your business phone uses the open JMPber XMPP protocol to use voicemail. Customer needs change over time.
So, we have a server called SM, a communication manager that manages the connected devices, in this case your phones. It is connected to the network using a switch. Further we have infrastructure, for example a router with VG function. Inside the router is a DSP card, a resource that provides the ability to convert traditional telephony into packetized voice data.
Clients are connected to the switch: IP phones, PC or MAC personal computers with Jabber installed, iPad tablets, iPhone and Android smartphones. All mobile devices contain a Jabber client.
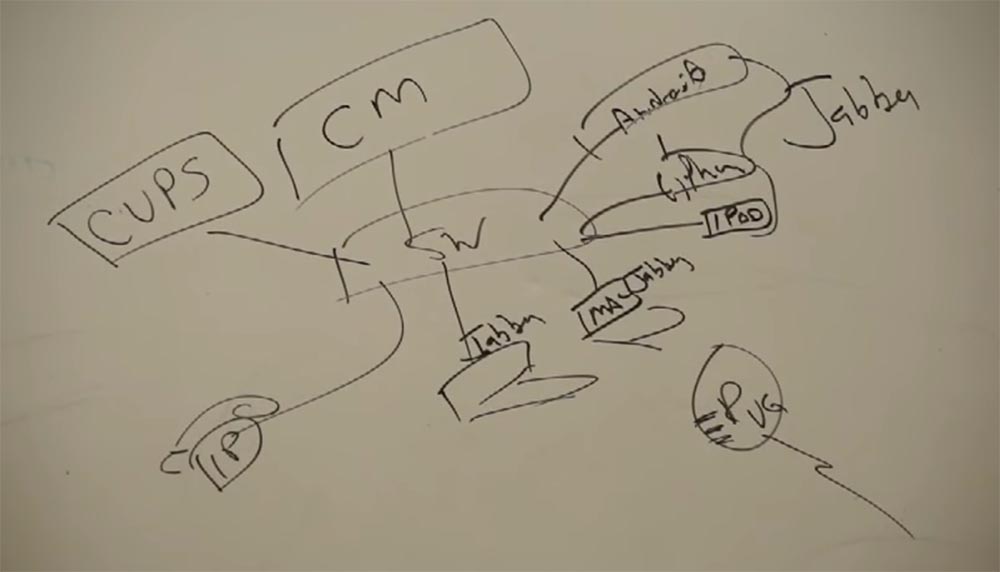
A communications manager manages all of this infrastructure under license. You simply download the CM software to the server of your choice.
In addition, we have another application that runs on the server - this is CUPS - Cisco Unified Presence Server. This server provides customers with additional services to traditional telephony, in this case, the possibility of chat.
Both of these services, CUPS and CM, can be downloaded to any server you select. They give you the opportunity to organize a chat and transmit voice.
For voicemail, Cisco has another server — CUC, or Cisco Unity Connection. It is an application server that provides the ability to messaging voicemail on a corporate network.
If someone calls my phone and he doesn’t answer, the communication manager switches this call to CUC, in my voicemail box, and the caller leaves his message there.
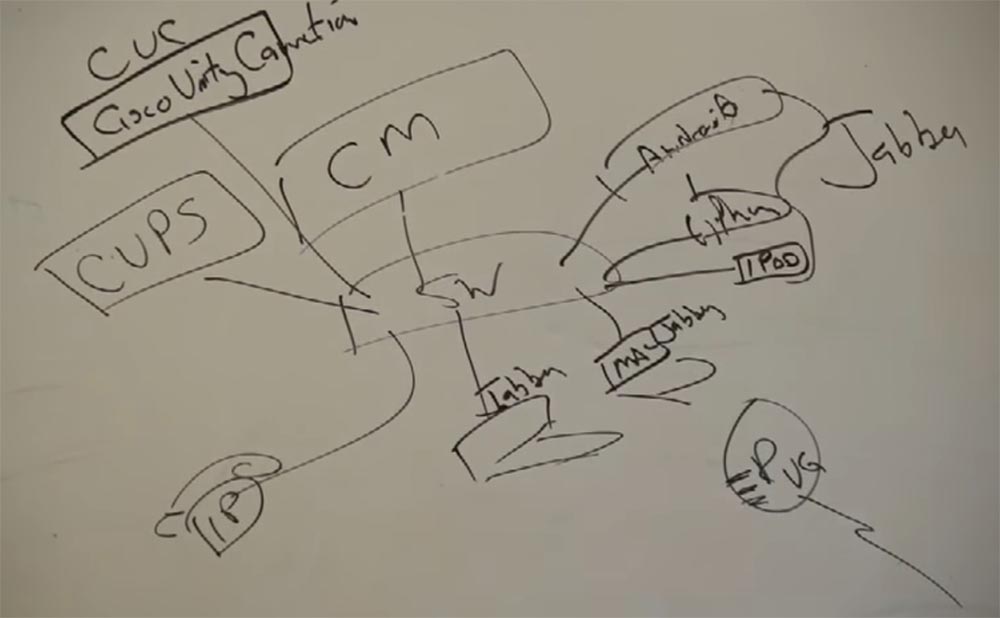
Let me remind you again - all this can be virtualized based on the UCS platform. We can say that these servers are virtual applications that can be virtualized on another server.
These solutions apply to all infrastructure elements. That is, you can use voice mail from your iPhone, tablet or any other smartphone connected to the network, regardless of your location.
As for security, at work you connect your smartphone to the corporate network, and at home use Wi-Fi connection to the provider's network, so access to the work network from home does not provide sufficient security. But even in this case, you can use Jabber through an Internet connection, and for security you need to create a secure channel using software called AnyConnect. It is built on the basis of a VPN client.
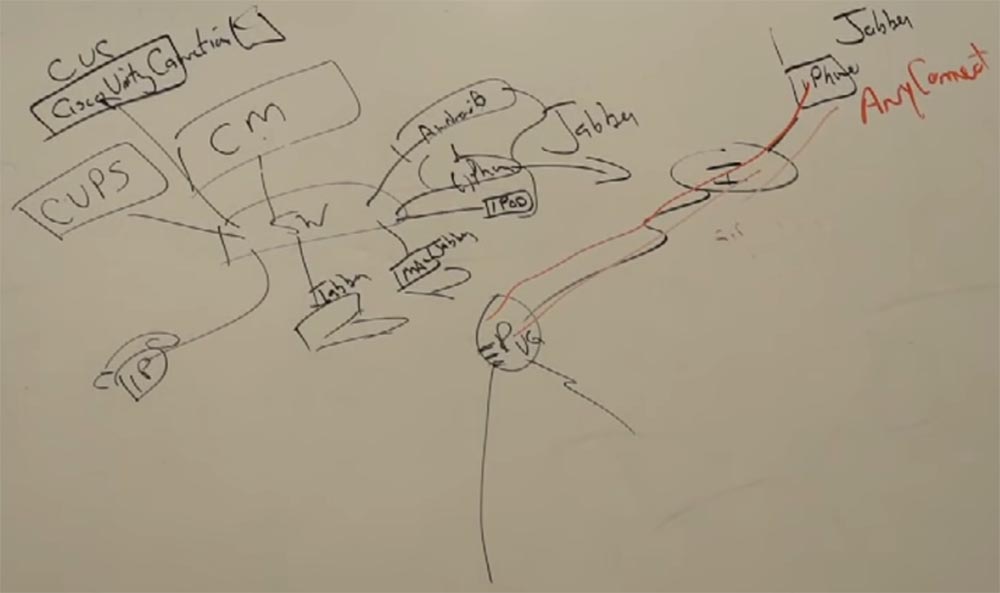
It runs on any equipment: PC, MacBook, smartphone. If you are outside the corporate network of Cisco, then after authorization on the network, a VPN starts, which creates a secure secure connection to the production server.
A basic license provides the client with CUPS and CM servers, and an extended license adds CUC voicemail. In addition, there is a universal license of the highest level, which gives the client full access to the system. At the same time, the same user can use both the IP phone and other stationary and mobile devices to communicate with other network users with the same phone number.
To familiarize with the capabilities of the license, the user is presented with a 30-day free period, and from 31 days you will have to pay for the services by purchasing a license.
SM unites everything.
To be continued, the link will appear here after the work on the translation is completed.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build the infrastructure of the building. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the field of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Product Software”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the twentieth of them.
FastTrack Training. "Network Basics." "Fundamentals of telephony." Part 2. Eddie Martin. December 2012
We broadcast voice using applications and we are committed to ensuring the operation of customer applications. Cisco did not know anything about PBX, therefore, when we explained the advantage of our telephony, we first of all pointed to the highest reliability. Our equipment had a phenomenal fault tolerance of 99.999%. This means that Cisco downtime did not exceed 5 minutes per year! But what is considered a downtime in telephony?
By creating VoIP, we opened the whole world to users. If you return to the issues of reliability, then there are several interesting features.
Let 24 telephones be connected to one of the cards of our station (lower left segment). My PBX has 600 such stations. If one such 24-card card fails, will this be considered a system downtime?

Where is the starting point after which you can tell whether the system is working or not, how fault tolerant it is, what percentage of its reliability? So, classical telephony was considered inoperative if 30% of its infrastructure became unavailable. Suppose your day started unsuccessfully, a policeman stopped you and fined you on the way to work, then your wife called and announced that she was getting divorced. You are in a disgusting mood, you pulled out a phone card in your hearts and disabled 24 phones. Is this a system crash? Of course not. If you have 600 such stations, then in order for the system to be considered inoperative, you must get rid of 30% - this is 180 stations. This is what a system failure means.
But an ordinary Cisco employee did not know about all this, and we made many mistakes trying to overcome our competitors until we found the best way. You know, people still do not see the difference between IP telephony and VoIP technology. They do not understand that the difference lies in the fact that we do not just transmit the voice, but turn it into an application! We just had to do something about it. In 2001, customers became interested in our technology, and 2002 was a really good year for us. There was an economic downturn in the country, but we managed to sell a lot of our products. Let me remind you that in 2000 Nortel was the leader in the field of networks, and Avaya was the leader in production on the market. But already in 2009, No. 1 became Cisco. This is a very short period for the market, and during this time we were able to change the world.
We did not specialize in the production of equipment specifically for offices, but we have a series of switches 6000 Business Edition, designed for small companies. I will digress from the topic a bit and give one example. Customers often told me that they did not need voicemail. Do you think my daughter Emily uses voicemail? No, she never answers voice messages. This suggests that the rules of the game are changing. We must strengthen the development of those changes in technology that really interest people today. We must make sure that new customers come to us.
Regarding my drawing, we need to know and explain to our customers the role of Cisco in this area. We introduced our technology and thereby stimulated the entire telephony market. We switched to IP-technology and all this hardware has sunk into the past. A little later we will talk about HCS, a hierarchical honeycomb structure.
Now let's talk about how Cisco solutions look. I already told you that since I'm not very smart, I like to simplify everything. Therefore, we consider solutions from three sides - services, customers, and infrastructure.
Services are a combination of network software and applications with which one or another type of client interacts, and the infrastructure will depend on what these clients require for their work.
A typical solution is a switch with which an IP phone is connected using PoE. The last word “telephone” as a physical device should disappear. It is not needed in this technology, but people continue to use telephones. So in reality, an IP phone is not a phone at all, but a client. After all, we have a personal computer PC, where you can put this client. This is the Jabber client.
Next - what service does our switch need, what software does it need? He needs a CM communications manager.

Our phone has an IP address 10.10.10.6 and a MAC address A. How do we associate a phone with a CM manager? We need to put the MAC address of our phone there. That is, CM is a database with tables of all components. This table has MAC addresses, EXT extensions for mobility, that is, passwords and logins, and telephone features. And by the way, when the phone contacts SM, it sends it its IP address. Thanks to this, you can transfer your phone anywhere and connect to the network wherever you want.

Our computer has a MAC address B and an IP address 11.11.11.9. We also enter these data into the CM table.
I pick up the phone, or press a button, and my IP phone sends CM one packet. This starts recording call details, or CDR (Call Detail Record). It allows you to track this call, see that the call is taking place. The SM manager sends another packet to the phone - this is a beep that informs the client that the phone is working. Suppose our phone has an extension of 3000, and the computer, or rather, its Jabber client, is 3200. The call from the phone goes to the CM, which determines the extension of the device with the number 3200 from the table and finds its IP address, and then sends the call to the computer. And the computer starts ringing like a regular phone, showing that someone is calling its owner. Both the "iron" and the "softphone" react equally to an incoming call - they both produce a ringing noise. The communication manager organizes a direct conversation between network clients, two RTP-poktoka, in both directions. They do not go through him; he only organizes it. When one of the subscribers hangs up, the signal enters the CM and it stops recording CDR, and the customer phones go into normal mode. Here's how it works - it's not rocket science.

What happens if I want to call someone who is outside our network? I will draw here a router with a “voice gateway” VG, which is connected to the PSTN, and that one with the subscriber’s home phone.
Suppose I want to call my wife to find out if her dog has eaten anything else. Two days ago, when I put my things downstairs, she was worrying about my hat, my favorite hat. Never before had a wife's dog been so close to death. I pick up the phone, the signal is received by CM, then I dial my home number, SM checks it according to the table - oh, this is an external call! And turns to the switch. He contacts the router, which has its own IP address, and the router sends the called number to the PSTN, and then the city network calls my wife to the phone. Similarly, calls are made via Wi-Fi, because it is the same network.
I will tell you an important thing that I always say to my clients. Classic telephone exchanges did all these things, but the problem was that PBX was literally stuffed with different equipment, a bunch of cards with different functions. Therefore, it was very difficult to achieve fault-tolerant joint work of all this “iron”, it was too much.
We proposed a solution whereby a call takes 17 steps before connecting two subscribers, but thanks to protocols and applications this happens on a minimum amount of hardware. We proceeded from the principle of “do not make complicated what can be simplified”. Our result was not a server for selected clients, but a server for absolutely everyone.
The table located in the CM is a phone book. We all used them once. The last time I used the phone book was when I needed a target for an air rifle. It was convenient to shoot at her, and she was the cheapest target.
They ask me if Microsoft played a role in the development of IP telephony. This refers to software for making phone calls through a computer. Undoubtedly, since Microsoft is developing software, they took part in this, created a client-server emulator. As they say, it's hard not to notice an elephant in the room. However, in 2001, when we were engaged in IP-telephony, Microsoft had nothing to do with it. They picked up the technology and were forced to create software for computers with call features already upon the existence of IP-telephony.
Here, our representative from Australia is present in the hall, and I will notice that more IP telephony systems are being sold in Australia than anywhere else in the world. In North America, about 60% of telephone systems sold are based on IP solutions, of which 40% are Cisco products. But I want to ask you to be careful with these numbers - the number of IP phones does not match the number of phone numbers. For example, a client has 25 IP phones and 560 regular telephone sets, these are different numbers. So be careful when telling customers about these numbers.
We will expand our scheme. I’ll add a WAN to our router, then another 1 router, also connected to the PSTN, then I will put the switch and attach the IP phone to it.

This phone does not need a separate PBX. His data is entered in the table SM and he becomes a full member of our network. Suppose it has a code of 4000. I pick up the phone of my phone with code 3000 and call my friend, that is, I call the number 4000. And the SM ensures that my IP phone “talks” to my friend’s IP phone, that is, it connects two IP together. At the same time, we have a choice - I can contact this number via PSTN or send a call via WAN. I have two different networks and I can choose the one that suits me best.
In the case of WAN, we have bandwidth limitations. Remember how I drew pipes of different diameters: a wide pipe, a narrow tube, again a wide pipe. My IP phone encapsulates voice, turns it into data, and uses a 64 Kbps channel. More service information is added to the outgoing packet, and I get a 100 Kbit packet for 1 second of the call. For LAN equipment, this is negligible. But for a WAN with a throughput of 2 Mbps, this value does not seem too small. Therefore, we use codecs that pack a voice call of only 8 Kbit, and we get a packet size 4 times smaller - only 25 Kbit for 1 second of a call. This reduces the load on the WAN.
Our CM communications manager should ask the router if the router can pass the call through the WAN. Why is this done? Because the router controls this bridge between the system and the WAN. And administrative call control is becoming more and more important. After all, we want to transmit not only voice, but also video and other data.
So, if the router allows you to skip the call, then the SMS informs our phone at the system input that the call needs to be transcoded to a lower bitrate of 8 Kbit, because it will go through the WAN, which has limited bandwidth. This is how the system that connects the phone with code 3000 and the phone with code 4000 works.

This technology is provided by the routing protocol over which the router works. SM allows you to simultaneously send 6 calls over the network. In total, the system uses 4 different protocols for transferring calls.
How many telephones or video devices can be connected to one SM communication manager? 40 thousand devices! In this case, we have a restriction determined by the capabilities of the server. Cisco, as a very good engineering company, has documentation that tells the user about the capabilities of the cluster solution and how to combine hundreds of such servers into one IP solution. That is, you have the potential to connect 4 million phones to the same network, which is provided by Cisco technical support. We have several such clusters in India, Europe, North America, and so on.
Now let's talk about clusters. The first SM you set up, let's call it Publisher - Publisher. He owns a database. I want to have redundancy here for fault tolerance, right? And so we have a second CM, Subscriber - Subscriber, and this manager receives data from Publisher. When you download this system, CM asks Publisher or Subscriber it. The first can do anything, read, write. But Subscriber immediately asks the question, where is my Publisher? These devices are separated so that our database remains complete and provides fault tolerance. The database can be located both on an independent server and on a virtual one, and the CM is a device that can request this database and use it for its needs. Let me remind you that all these servers are software, application.
So, Publisher owns the information, and Subscriber uses it. At what distance from the Publisher can a Subscriber be placed? Are they in the same common building?
The requirements stipulate a time of 80 milliseconds for the mutual exchange of data between the two devices.
I will give you an example. North America is a big enough continent, big enough for me, especially when you fly across the continent often. I worked in Telus, Canada, and we talked about the possibilities of technology. And I was told that they are able to provide information from Halifax, Nova Scotia, and this is on the other side of the continent, to Calgary in 80 ms and the claimed bandwidth. So I can place my Publisher in Calgary, and the Subscriber in Halifax, at a distance of ¾ the length of the continent, and such a speed of communication between them will be guaranteed.
So, Publisher and Subscriber form a cluster. A cluster may consist of two or more SM communication managers using a common database.

In one cluster, you can combine 20 servers. What should you buy by downloading CM communication manager software? Only user license! You do not need to buy any additional physical devices.
If you use UCS, the Cisco server platform, then install the new server software from existing equipment under license. You can buy 20 or 50 licenses and connect the corresponding number of user phones to the network. You simply upload the new CM to an existing server and run it. This solution is based on VMware technology. Based on Linux, a virtual machine is created that organizes a virtual network. The guide for the deployment of such a network consists of 1200 pages, and absolutely all the principles of work and steps are described there. Cisco C Series equipment is used to create these networks, but you can use IBM servers and other products with which our equipment is compatible.
The license enters the CM, which performs all the actions provided for by this license. Users can even choose their phone numbers, if required by the license.
We do not need telephonists in their classical understanding, but in the companies of clients there are external technical specialists who are involved in IP-telephony.
I want to return again in 2000-2001, when we just entered the market with our technology. Then we used the SCCP protocol, and now SIP - perhaps this is the whole difference with the 2001 configuration.
Consider what happens if the WAN fails - here I cross it out.

We will have a client that does not see its server. It will not have a way to transfer data to the server.
Suppose your mail server has disappeared at home. The Internet has disconnected, and when you open Outlook or another email client, you cannot send an email. So, the communication manager, as soon as he sees that the connection with any client IP has disappeared, will immediately inform that the WAN is out of order. However, we cannot risk the business of our customers. Therefore, Cisco in less than 3.5 months created special software for the router called SRST - “invulnerable remote telephone communications” - which shows that our equipment has much greater capabilities than you might imagine.
We have been using this system since 2001 - look at how it looks in the picture.

You can call from the branch (upper left telephone) to headquarters (lower right telephone), talk with a friend (lower left telephone) or order pizza in the city. In the first case, the call will go through the IP WAN, in the second - directly through the local network of the branch connecting the upper and lower phones, and in the third case through the public telephone network PSTN. Assume that the connection to the IP WAN is interrupted.

Having discovered this, the branch server will make 3 attempts to contact the subscriber at headquarters. If this does not succeed, he will forward the call to bypass the WAN via PSTN and then to the headquarters router. We have been using this method of providing reliable communications since 2001. This is made possible because in our IP telephony system, PSTN and IP WAN are separate and can operate independently. This is not in the classical telephone network, so it is less reliable.
Keep in mind that our customers are not alike. For example, some need voicemail, others do not, and this must be taken into account. Your business phone uses the open JMPber XMPP protocol to use voicemail. Customer needs change over time.
So, we have a server called SM, a communication manager that manages the connected devices, in this case your phones. It is connected to the network using a switch. Further we have infrastructure, for example a router with VG function. Inside the router is a DSP card, a resource that provides the ability to convert traditional telephony into packetized voice data.
Clients are connected to the switch: IP phones, PC or MAC personal computers with Jabber installed, iPad tablets, iPhone and Android smartphones. All mobile devices contain a Jabber client.

A communications manager manages all of this infrastructure under license. You simply download the CM software to the server of your choice.
In addition, we have another application that runs on the server - this is CUPS - Cisco Unified Presence Server. This server provides customers with additional services to traditional telephony, in this case, the possibility of chat.
Both of these services, CUPS and CM, can be downloaded to any server you select. They give you the opportunity to organize a chat and transmit voice.
For voicemail, Cisco has another server — CUC, or Cisco Unity Connection. It is an application server that provides the ability to messaging voicemail on a corporate network.
If someone calls my phone and he doesn’t answer, the communication manager switches this call to CUC, in my voicemail box, and the caller leaves his message there.

Let me remind you again - all this can be virtualized based on the UCS platform. We can say that these servers are virtual applications that can be virtualized on another server.
These solutions apply to all infrastructure elements. That is, you can use voice mail from your iPhone, tablet or any other smartphone connected to the network, regardless of your location.
As for security, at work you connect your smartphone to the corporate network, and at home use Wi-Fi connection to the provider's network, so access to the work network from home does not provide sufficient security. But even in this case, you can use Jabber through an Internet connection, and for security you need to create a secure channel using software called AnyConnect. It is built on the basis of a VPN client.

It runs on any equipment: PC, MacBook, smartphone. If you are outside the corporate network of Cisco, then after authorization on the network, a VPN starts, which creates a secure secure connection to the production server.
A basic license provides the client with CUPS and CM servers, and an extended license adds CUC voicemail. In addition, there is a universal license of the highest level, which gives the client full access to the system. At the same time, the same user can use both the IP phone and other stationary and mobile devices to communicate with other network users with the same phone number.
To familiarize with the capabilities of the license, the user is presented with a 30-day free period, and from 31 days you will have to pay for the services by purchasing a license.
SM unites everything.
To be continued, the link will appear here after the work on the translation is completed.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read aboutHow to build the infrastructure of the building. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
