OWASP Automated Threat: Automated Web Application Threats
The OWASP Automated Threat Handbook provides information on protecting web applications from automated threats. These threats are associated with the use of automated tools, denial of service, violation of the application logic, abandoned baskets, incomplete transactions, etc.
In addition to the classic risks of web vulnerabilities introduced in OWASP TOP 10, there are numerous opportunities for attackers to destabilize the web application , or to manipulate the functionality of the application to disrupt its operation. An example of such manipulation can be the creation of multiple "unfinished" orders, which can exhaust the reserved positions of goods in the online store, which will not make it possible to make an order to legitimate users.
Also, these threats include the so-called bot or automated attacks aimed at:
- user identification;
- aggregation;
- click fraud;
- Spam comments
- parsing content.
Overuse of functionality can be interpreted as denial of service applications (DoS), although in fact DoS is a side effect.
Automated Threats
Threats are distributed in several types and uses in alphabetical order. For understanding, I will use the native OAT name and the adapted description of the threat.
| Oat | Description |
|---|---|
| OAT-020 Account Aggregation | Using multiple accounts and interacting on their behalf in an intermediate application. |
| OAT-019 Account Creation | Creating multi-accounts for future use. |
| OAT-003 Ad Fraud | Advertising fraud. Create fraudulent ad impressions and click aggregation. |
| OAT-009 CAPTCHA Defeat | Bypass captcha tests. |
| OAT-001 Carding | Validation of stolen payment card data by shopping. |
| OAT-010 Card Cracking | Checking the validity of the validity of the stolen payment card, as well as its CVV code by exhaustive search. |
| OAT-012 Cashing Out | Purchase of goods or cash out using confirmed data of stolen payment cards. |
| OAT-007 Credential Cracking | Identification of valid user accounts of the system using the tools for selecting logins / passwords. |
| OAT-008 Credential Stuffing | Mass login attempts used to verify the authenticity of stolen pairs in the form of a username and password. |
| OAT-021 Denial of Inventory | Exhaustion of stocks by multiple “abandoned” or forged orders. |
| OAT-015 Denial of Service | Exhaustion of server / DBMS resources - for example, when generating a lot of reports or "heavy" queries to the DBMS. |
| OAT-006 Expediting | Speeding up usually slow, tedious, or time-consuming activities. |
| OAT-004 Fingerprinting | Identify information about web server components. |
| OAT-018 Footprinting | Identify information about web application components. |
| OAT-005 Scalping | Gaining access to limited goods / services by manipulating the logic of the web application. |
| OAT-011 Scraping | Web application parsing / data collection for use in third-party applications. |
| OAT-016 Skewing | Repeated form requests, clicks, etc. to change indicators. |
| OAT-013 Sniping | Manipulating application logic to create the "last winning bet." |
| OAT-017 Spamming | Malicious or spam information in open or closed (DBMS) access, messages. |
| OAT-002 Token Cracking | Identification of predictive values of tokens, coupons, discount codes by exhaustive search. |
| OAT-014 Vulnerability Scanning | Automated scanning and fuzzing of a web application to identify potential vulnerabilities. |
This type of threat is superimposed on the WASC Threat Classification matrix and Miter CAPEC :
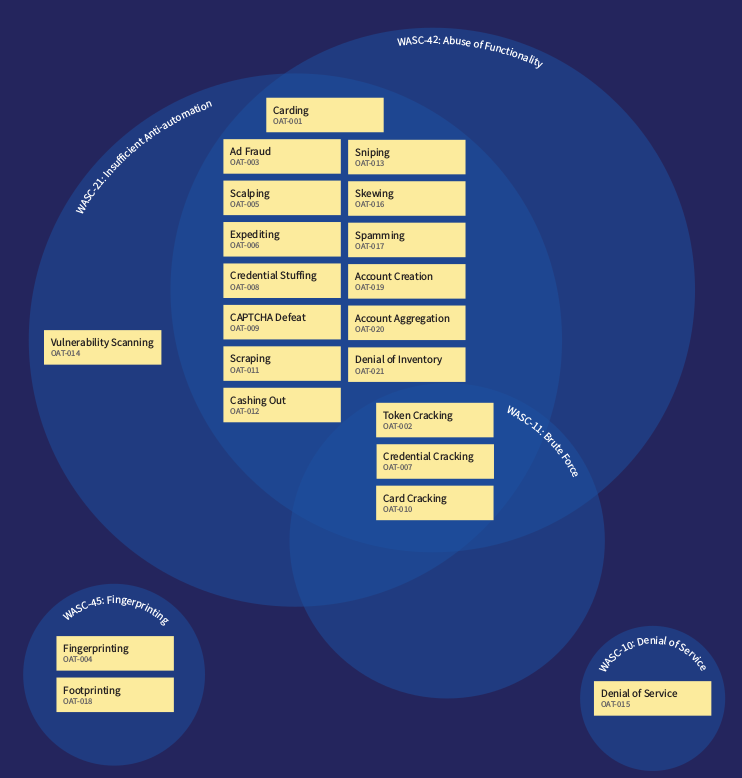

The area of focus on threat events included in this list should include both individual events and multi-stage and iterative interaction with a web application.
Most of these threats are similar to the actions of legitimate users and only a comprehensive in-depth analysis can help to identify those or other abuses and manipulations that depend on both the iteration time of certain actions and the scale of events. Events related to automatic threats can affect not only the web application, but can also be associated with third-party services.
Some of these threats can be identified and eliminated using tools for analyzing anomalies, machine learning and artificial intelligence, drawing up legitimate user behavior patterns, etc.
Project Page: OWASP Automated Threats
