FastTrack Training. "Network Basics." "Understanding the OSI Model." Part one. Eddie Martin December 2012
- Tutorial
About a year ago, I noticed an interesting and fascinating series of lectures by Eddie Martin, which is incredibly intelligible, thanks to its history and real life examples, as well as colossal experience in teaching, which allows us to gain an understanding of rather complex technologies.

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the area of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the first of them.
When I met Cisco, I was just a customer. Now I have been in the field of network technologies for 30 years. I began my career working with the military, with the US Air Force. I actually traveled with President Reagan, so you can imagine how long it was. But not yet about that.
I was a client of the company, a buyer of their services and a user of their technology. In fact, I was their client longer than an employee, because the career in Cisco for me began in 1999. Then the era of IP telephony began.
I was that PBX guy who connected switches and routers and could carry out functions not only the telecommunication manager, but also did a lot of things. They needed a professional and they found me in South Carolina. If you work as an account manager or in a team of accountants, then your team will have a whole link of so-called product sales specialists. They will explain to you how to work with this or that technology. The fact is that when I was just starting out, we were selling voice communication services. In my time, accountants could only write bills for calls, now we have greatly complicated this process due to the development of networks. And these networks have never been so complex. What became a problem, a big problem, as customers hoped that the implementation of their tasks would be simple. And it became more complicated not from the point of view of network engineers, and in terms of technology, but what's great - when we turn on our computers - they work. This is what customers are waiting for. They expect a miracle from us. The incredibly fast development of technologies, namely their transformation, is something amazing.
That is why one of the tasks that was entrusted to me was training new account managers in my own team, since we hired a lot of people from outside, not from Cisco, and they had no experience in the field of network routing. They did not understand switches and routers, but they could sell well. Usually I say this - give me someone who can sell, I don’t worry about whether he knows technology, I can teach, but I can never learn to sell. I myself am not a seller. So the thing went in that direction.
The class was built and for the first three to six months I just kept telling them something, we had lunch, dinner and breakfast together. So the training went on and we realized that this should be done for the entire staff of the company, even the most insignificant, because everyone influences our business and only in this way they can fully understand its essence. Today we will focus more on choosing an approach to selling a product. In fairness, I note that service providers often sell these same services better than sellers.
I left Cisco at will in 2004 and opened my own consulting company. You can see the inscription KEM consulting here. Now I am sitting on the other side of the table. I was hired to go to clients and provoke them to talk about technology. You often have to talk with customers about technology, but I'm one of those they ask, what was that seller talking about? How will this affect my business? Will it help me or not? Or am I just wasting my resources? It's funny to be in my current position, because now I can hear what they said about me, in a way, when I represented the interests of the vendor.
So, we will begin with a discussion about the OSI model. This model has been around for some time, actually longer than I am in this business. It appeared at the beginning of network technology. Before that, we essentially had a large computer and a private network through which everyone connected to this mainframe, everything was centralized, we used ancient terminals, or rather 3270 terminal emulators, because there were no terminals as such. So then there was a network, very private and very close. And then all of a sudden people started building “personal computers” and began to wonder how to make connections between them.

I find it extremely funny, but after I finished working with the military, I started working with American Airlines, which at that time had the largest private data network in the world with a mainframe located in Tulsa, Oklahoma. And it launched the Saber computer reservation system used by the four airlines. And once, in the mid-80s, we had a load of 140 thousand people who connected to this mainframe from IBM. Then everyone used these fucking Raytheon terminals, summit terminals, someone’s stupid term, be they wrong:

And then personal computers appear. The terminal at that time cost 75-85 dollars and it had two color options - green and black or orange and black. And here we replace the terminal with a personal computer worth 4 thousand dollars. We connect them to a separate network, which we had to create. And then the first thing we do is upload a terminal emulator to it so that it looks like a terminal. But we did it for the sake of productivity. Suddenly, we no longer needed typewriters, since we no longer needed to type anything manually. Printers have become network devices and now there is no need to know a person who could print. All these processes began to occur simultaneously. And at that moment when the evolution of what we now call the network took place, there were a lot of competing technologies offered by different companies, with their own vision of how the network should function. Some of them could not function together. Here is a living example. IBM released the first personal computers and American Airlines bought a whole bunch of such computers. We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186: We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186: We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186:

And they change the type of connectors to Ethernet. Now computers can not communicate with each other, they can not even communicate when connected to the same Ethernet network. Token Ring does not work with Ethernet, Ethernet works completely differently. In the end, they had to make it all work together, and at that moment, by and large, the OSI model appears.
Today we should not worry about that. Ethernet is used everywhere and lovers of Token Ring, like me, were left out of work, licking their wounds. Like all these people who have contributed to ATM and other similar technologies that are a thing of the past today, since we only have Ethernet. Usually I say this joke later, but I’d better say it now. How do you pronounce Ethernet from a Cisco perspective? Cisco This is Ethernet. You know that I worked at CISCO, it was we who started to offer these technologies to people and we gave the client options to choose from - ATM switches, Token Ring or Ethernet. Clients themselves chose the technology they need. And what happened in the end? We almost did not sell ATM or Token Ring switches and now we do not sell them at all. We can adapt them if necessary, but we do not sell them ourselves. There are no more core network products besides Ethernet,
But the OSI model for vendors and organizations is, above all, a great way to explain why network technologies even exist. There are many industry representatives among us today and I will ask you a traditional question. Why do people even buy routers and switches? Why do they need all these wireless technologies and stuff? Why do they invest their money in this? They need software applications, right? All of these applications are the most important thing in the world for our customers.
I will show you the entire OSI model and all its seven layers. And I will need to tell you why customers need it and why you and I are generally sitting here right now. We must show them that they need these technologies to run their business. They need these routers and switches for the business to flourish. The only reason a customer buys a router and switch is access to applications.
So, we begin to disassemble the model and meet the seventh level. An application layer is the final set of protocols required to access network resources.

What is a protocol? This is the set of rules that we set. That is, to connect to a printer or server, we need this set of protocols. In fact, customers buy all these routers and switches in order to use applications, to have access to the web, which also works via the protocol. This is the only reason they buy them. You will say that I am not seven spans in my forehead and not a local genius, but it took me a long time to get to this conclusion.
And in order to explain this, I would like to talk about the case with my best friend, who decided to open his own business. He trained at Virginia Tech as a chemical engineer and went to work at a naval shipyard in Charleston, South Carolina, as a chemical engineer, a notch lower. He worked on nuclear submarines, conducted a variety of studies, and suddenly for no reason decided to completely change the direction of his activities. He decided to go back to where we had grown up, to the southwest of Virginia. And he wanted to open his own home health care firm. He liked living where he grew up. There are forests, mountains, beauties. In general, he opened his own business and provided people with home services. There are many mining enterprises in our region and people often have lung problems for this reason. And he decided to help people get treatment at home. This is easier for insurance and for hospitals and for the clients themselves. He began selling, for example, air compressors, so that a person could breathe pure oxygen in cases of lung problems. And later he had to build an insurance company. Why did he have to use mail, regular mail, which we called a turtle for fun. That is, he filled out the form, wrote the doctor’s recommendations and sent these forms to the insurance. Then 90 or 95 days later, he received his check for payment. And this is only if the insurance has confirmed everything the first time. It took him 95 days to get his money. Not the best option. And then someone knocked on his door and said - we have the application you need, a server that will solve your problems. You will have a terminal or a personal computer, which will connect to this server and you will enter data and transfer it using new technologies. This technology was called a modem in those days. You will dial the server and transfer data to the insurance company. So, if you invest in this server, in the terminal and the application - this will reduce your expectation from 95 to 70 days.
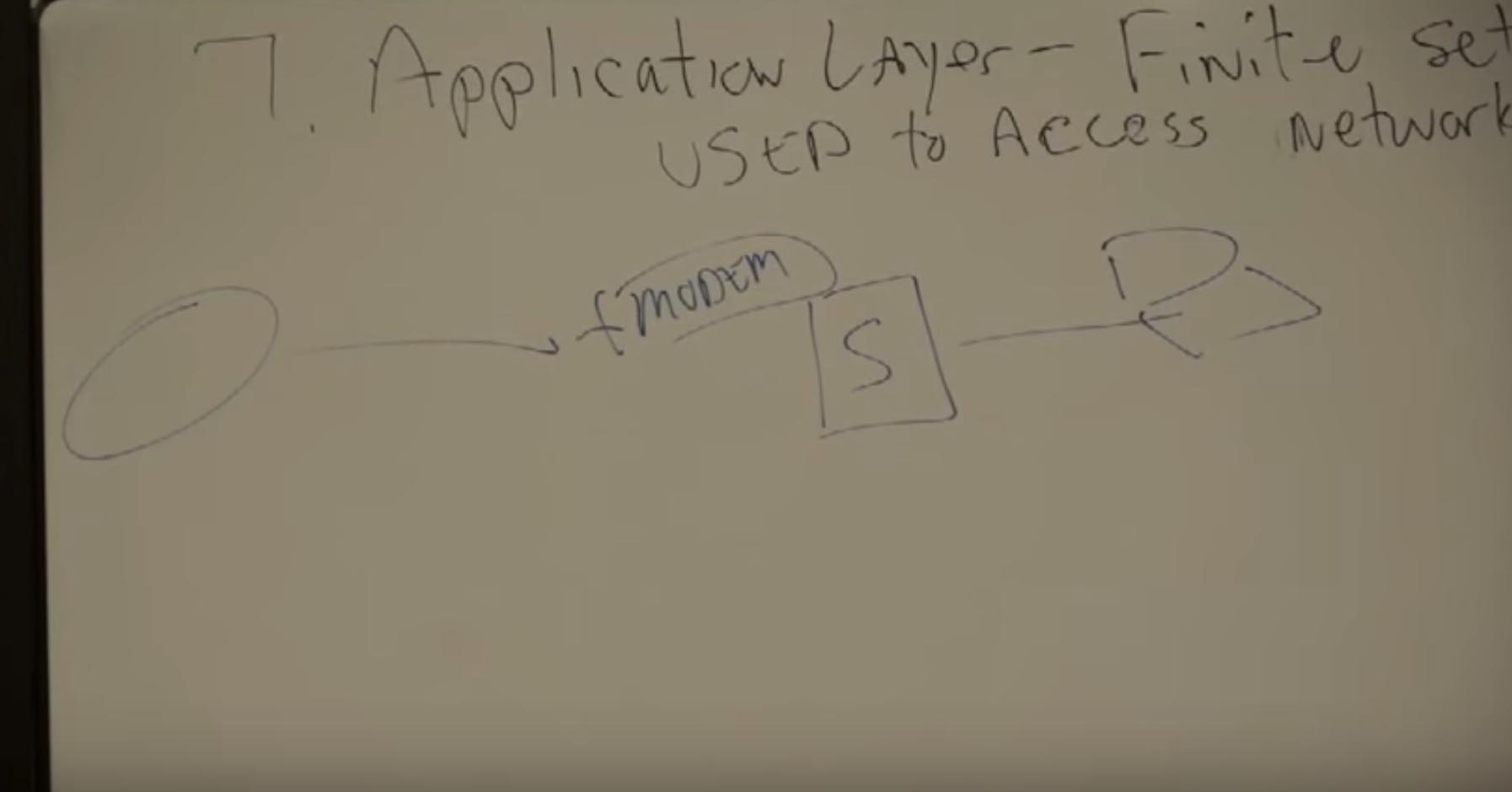
Are you curious, they asked? And what do you think Mack answered? Of course! Of course! He began to buy equipment that, among other things, needed to be serviced. But time passed and he thought that he needed more employees so that they could work and bring even more profit. And for this, he needs network equipment that will make it possible to connect several computers to the server, not just one. So the first network appeared. This is basically. Primarily. And then other people came and suggested that we should have another server on the network, since we have a lot of equipment and we don’t even know how much, where and when it should be serviced. We have an inventory database, an application that must be connected to a network that allows you to know everything about your equipment. Is it interesting for you? Of course! Spare me the need to do all this. We connected it to the network. After that, he got a service of nurses who worked in the homes of clients and he sent them to different parts of the city. He needed to know who and where and when is located and he created an application with a schedule of their work. Now imagine that you meet my friend Mack in a bar, and this is the most likely place where you can meet him outside the house, and ask him a question - what do you consider the most important thing for your business? He will answer that this is what gives him access to applications. With the development of technology, he got routers and more, but the main thing is that they give him access to applications. How much money do Cisco switches and routers bring? 52 percent profit. About 35-37 percent of them are switches and the rest are routers. These are fundamental products. But they are needed only in order to provide access to applications. That is why we need to make sure that we effectively interact with customers and understand what they need, and they need to use applications.

Now the term of the decision on its payments has decreased from 95 to 45 days. If you have a newer technology that will reduce the waiting time to 40 days, the Mac will be happy. Show her to him. Only geeks like you and me are interested in such technologies, but we have no money. We do not scatter them. I have a wife and two children and I will tell you honestly, I have no money. We need to understand what is important for the client and give it to him, or rather, what he sees as valuable for himself, and these are applications. He doesn’t just need cool switches and routers, and we made really amazing products, but he needs to understand why they can come in handy for him, for which applications they can be used. The network exists solely to use applications! Take another example.
Mac has a router, to which more routers are connected in various places, his network is now wide. What if a young employee here and another employee from another segment of the network decide to install on their computers the latest version of some new game, like Doom or something else? They will want to play on the network, fight with each other. They will phone and agree to download the game and play during lunch. They will need an intermediary who will transmit this high-resolution video and the game and the network can become very busy. We need the network to be smarter, it must prioritize the so-called QoS. She should put paramount tasks above such gaming. Mac will say that for him, working servers are much more important, they are in the first place, and everything else is in third. Should the network somehow understand its priorities? Yes,
This is what we did in the 90s. We have invested millions and even billions of dollars in order to make our decisions smarter and determine what is more important in a particular network. An ordinary packet or a packet containing a frame, which packet can be delayed and which not. What was determined by QoS. We started broadcasting voice over the data network and then we really started using priorities, so IP-telephony appeared. The network must meet our business challenges. And she can, if she is smart enough. Cisco does just that and offers people not only switches and routers, but also applications that can make them smart, otherwise the network will not work and customers will not receive what they paid for. In the future, I will tell you about the servers that we use to work. But the main thing is the applications that our users need. It’s interesting for us to talk about technologies and protocols, but our customers only think about their business. They wake up in the morning and don’t think that they need a new switch or router. They think that the economy is in poor condition and they need a successful business, they want to survive. They want their business to flourish and to bring as much profit as possible. We must balance our efforts with their requirements. We must follow our strategy. And it's simple when you are a local manager, but if you are a regional manager and you have 1200 clients, then it becomes difficult to act in accordance with the strategy. But if you try to ask at least a couple of questions to clients, then the strategy will be easier to build. You will be able to think outside the templates and expand the capabilities of customers. Understand that we need to constantly find out how we can strategically help the business of our customers. This is what I do as a consultant. Implementation sometimes changes the picture completely. Thus, we discussed the seventh level - the application level, which truth is the most important level for me.
We go down a level below. This is a presentation layer that acts as a kind of adapter. He makes a picture from a JPG image so that we can send it. The application sees the image as an object and turns it into a JPG file. We are adapting this facility. The text gets its own format, its own picture, this makes it possible to turn all zeros and ones into the objects we need. Adapt them to your needs. But that is not all, we have added here some more functions and settings. I will explain this with an example of an Internet browser. How many browsers do we know? Chrome, Internet Explorer, Firefox and many others. They all use the same protocol. Which one? HTTP For example, I want to send a PowerPoint presentation to your computer. We call this file sales.ppt. But how the network will understand What format is this document? When the creators of PowerPoint thought about this task, the task of transferring files, they knew what to face with it.

And they came up with a file transfer protocol called File Transfer Protocol or FTP protocol. If I want to send a letter from one mail server to another, then I use the simple mail protocol or SMTP (Simple Mail Transfer Protocol). If I need network management, then I use the Simple Network Management Protocol (SNMP). And all these are standard applications that you can use for your own purposes.
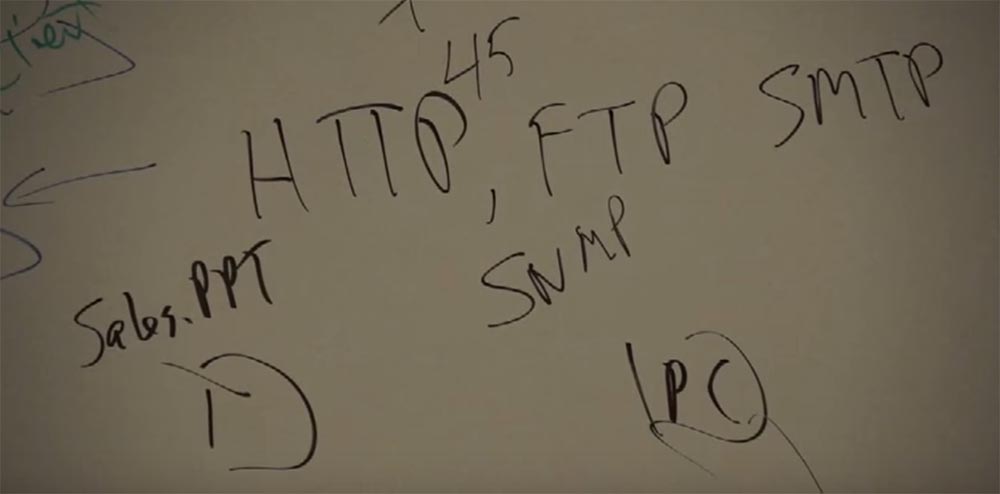
My wife believes that the Internet was created for only three things - shopping, email and information. No, not for facebook. Do not guess. She does not have a facebook, she uses mine, I don’t even close it, because she communicates with friends. She loves to write letters to relatives, as she comes from a large Italian family from the northern part of New York and now her relatives live all over the country, and not as before in one big house. And she very often uses E-mail, keeps in touch, finds out what is happening: “Oh God, you know, Joey’s girl is just awful for him,” and that's it. It also reads news on the Internet. She really likes these gossip columns, she always reads how things are with the Kardashian family, the whole Kardashian family and more. She is crazy about local newspapers, and always loves to know who is arrested - “they drove intoxicated, the whole family, for years,” In general, you understand me. She also loves shopping. And when we started dating, I still did not know about the company that produces women's clothing. The company is called Talbot. They produce expensive clothes. When we walked around the mall, I often noticed their signboard and red door, but I never came in until it dragged me there. You know this:
- I look like?
- You look amazing.
But when you look at the price, you understand that it’s not so amazing, in your mind, not by ear, but the essence of what. Now, in the era of the Internet, Talbot write letters herself to her and offer new collections of clothes and she does not need to go anywhere. She can buy a spring collection, which also has not appeared in stores. But why is the company doing this? Why do they do such mailings? So that a person can enjoy shopping at home, sitting on a comfortable sofa.
I remember how we were going to a friends wedding last summer and she bought three or four dresses for this and I thought if we were going to a wedding or a fashion show? For dresses, she needed shoes, bags and other trifles and she could choose all this while sitting at home. What did she need for this? Personal computer, Internet, Talbot servers. There should be two of them. Why two? They are like bulbs, they can burn out. You turn on the light at home and in 99.99% of cases the light comes on, but there comes a time when the light bulb burns out. Also, the server, electronics, which can fail and therefore at least two are needed to increase fault tolerance and scaling. We now have the most powerful multi-core processors, and then it was necessary to use many servers for scaling. So, my wife sits on the couch and adds things to the basket, and then she needs to press this magic button "Payment". And what will she do? She needs to enter my credit card details into their system so that they charge me. My card ... She knows all my credit card numbers. And all this, including my personal information, will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes. will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes. will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes.
A little help:
If you pay attention, at the moment of transition to the payment page, the protocol changes from HTTP to HTTPS. Why? Because now it is a secure network. This creates a secure tunnel for the transfer of personal data of the client. It is at the presentation level that this encryption is performed. We now not only convert files and data to zeros and ones, but also encrypt them, creating an additional layer - a secure socket. Our personal computer starts encoding by adding a certain code to the information, which only he and the server to which we send the information can decrypt. Nobody else.
This happened in the late 90s, then there was still no opportunity to buy so much on the Internet. There were no sites like Amazon and others. People did not know how to transfer money and the protocol was just invented. I will say again that at that time we did not have such powerful multi-core processors. At the same time, as many as 5 thousand people could make purchases. And they all begin to send letters and they want to order their product, because the stock, you know, today is a 30% discount, and tomorrow 40% and everyone is running to buy - sale! You will not have problems with sending letters, but let's look at this process from the point of view of Talbot servers. At that time, and with those technologies of the 90s, they could process requests, despite the fact that 30 percent of the server capacity went to coding, 30%!
And what should be done in this case? Of course, if we are successful, add more servers.
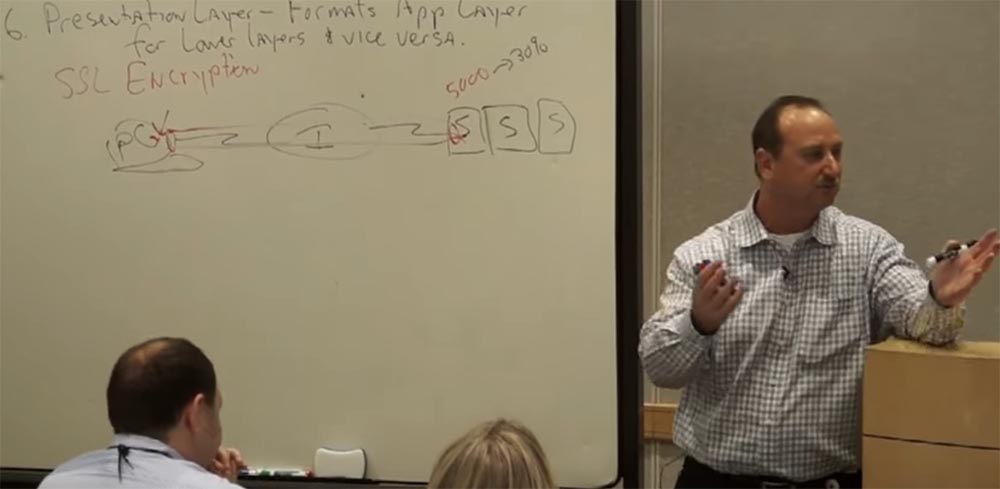
Servers are like children. I did not know what return on investment (ROI) could be expected, but I did two. My son is 13 now and his daughter is 15. I remember how Emily was born. She weighed only 4 pounds and 11 ounces, was so tiny, and I promised her that I would become the best father in the world and give her everything she needed. Now she has grown up and is choosing an expensive college and is testing my nerves by driving. But servers are like children too. They need to invest a lot of money. How much does the server cost? These are not only computers. You need to pay for electricity, but the servers will be very hot and you need to cool them, and here you need air conditioners. But not only them. You will still need such cheap applications like Oracle, right? :) Also, you will need people who know how to keep an eye on these servers and databases, who will put things in order there and monitor their work. You buy servers and pay a bunch of additional costs, which you simply can’t do without. Just like with children, that's why I compare them with children.
At that moment, Cisco came up with a proposal. Why would you buy another server and pay crazy money for its contents? What if we sell you a device that itself will encrypt all this data, live inside your network and give you the finished code at the output? In addition, the device will also be able to evenly distribute tasks between servers, depending on their load, act as a balancer. Cisco combined with a presentation layer offers customers more than just the transfer of data and packets over the network, they offer an additional level of intelligence. To implement what, at one time, a whole company was acquired, which allowed the manufacture of a device that allowed the hardware to balance the load that the program could not do so effectively. In this way, Cisco helped a lot of companies save a lot in the early 90s and early 2000s, as they didn't need to increase the number of servers anymore. That is what our company continues to do so far. We reduce the costs of our customers. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video.
Emily loves video calling. She is ready for hours to chat face-to-face with her friends, but sometimes she invites girlfriends to chat with her friends. That is, she invites Mary Kay, Lexie, and they are their friends and a small fight is arranged because of the guys at school, which they really love. But this requires a bridge that allows them to communicate via video. A service that will allow this to materialize. That's what we sell, we sell the ability to enable and use this technology, to make it the most effective. Yes, this is a combination of software and hardware, all Cicso solutions are always software, we call it in Cisco iOS, and certain uniquely designed devices, always a combination of the first and second, second and first. We produce a complete product. Of course, companies like Amazon don't need this right now, they have their own software and powerful processors. But we did this in the late 90s, when there were no powerful processors, we saw the needs of customers and offered them a solution. In this case, the customers wanted to save money and we helped them. We saw this trend in the industry, we saw evolution, we realized what customers would need at this stage. We gave them the opportunity to reduce the number of servers and save money by meeting the needs of their applications, that's all, this is not rocket science.
The fifth level is the session level. This is like the first handshake of a client and its server. At the application level, you click on the icon of a browser or other program, the connection to the Internet begins and the transition to the site. This is the first handshake. The client seems to get acquainted with the server and says to him:
- Hello! Here are the rules by which we will work with you. Today we will transfer the file and use FTP, so you must understand the rules for the transfer.
This is essentially the first level at which the client, that is, the computer, communicates with the server through the network. The computer tells the server:
- Hello!
And he answers him:
- Let's work together!
You may even notice how “Session Start” appears on the page.

Imagine that it is a mail server and you are using Outlook. You click on the icon of this program and it, when opened, gives a signal via the POP3 or IMAP protocol that you need to go to the server and pick up the mail. And it all starts with the installation of the session, from the beginning of this session. But every time we create or use some kind of application, we should think about those people who want to harm us. About those who write viruses or try to steal our data with you. I know that no one carries desktops with us, we often use mobile devices - laptops or phones, at Starbucks or at a hotel, connect to many different networks and don’t think about the local connection being unsafe.
What if one of these bugs, called a virus, clings to your mail? What if the task of this bug is to drive your server crazy by loading it to the limit? You connect to the server and the virus begins to plague it. We use antiviruses, but what happens next? The appearance and functions of viruses change very quickly. And antiviruses stop detecting them. We have to update antiviruses again and again and again. But what if the network is smart and knows all the protocol rules? Can she then protect your server in the best way? Of course! You don’t have to worry so much about the server.
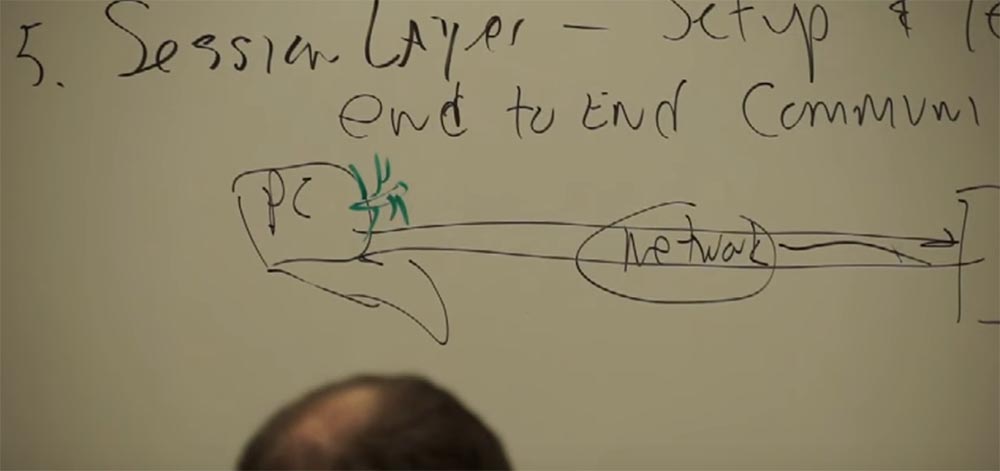
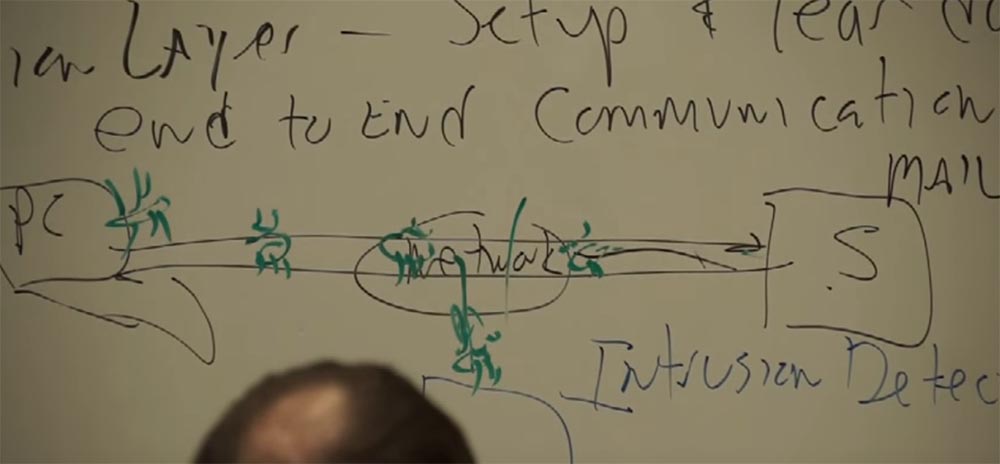
We have created a whole line of products for detecting violations and intrusions, which works at the level of POP3, IMAP, etc. protocols. This means that in the case of mail, we added to the network a device through which all mail going to the server passes. The device monitors the correctness of the sessions. It tracks traffic.
And when your server is attacked by a virus, you will find out about it, since at first the virus will go through the device upon its detection. We will discover it and will be able to end the session simply by breaking the connection. Is there something wrong with this client and it is attacking the server? Turn it off. For the client, this is an incredibly useful feature. But I never liked this, to be honest, since the analysis of the traffic takes place after it has passed, not in real time, it looks like a ghost chase. The virus is already on the other side, we did not stop it, we just found out about it. Then we had to think further and decide how to stop the virus. And we came up with a program not to detect, but to prevent intrusions and violations. We decided to filter them in the network, in real time, to pass all traffic through ourselves.
Imagine that we have a track. We indicate the direction of movement in the lanes. A program to identify violations will be presented as a policeman standing on the sidelines. He stands with a weapon, a walkie-talkie and a baton and listens to the radio, eating a donut, and then some nut from North Carolina rushes at a frantic speed through the oncoming traffic. The policeman transmits information about him on the radio:
- There’s some kind of crazy man rushing along the oncoming road at a speed of 60 miles per hour, there may be an accident down the road.
But he cannot stop him, and in the end something terrible can happen. But the program to prevent violations and intrusions will stand in the form of a policeman in the middle of the road, and the policeman will not eat a donut, but will be ready to block the path. The psycho will have to stop and surrender to the policeman, who will take his keys from him and remove him from the road. And which option would you prefer? Of course, the second.
No questions. Since your business is based on the work of applications. And when you want to have such a device in the structure of your network, and even on the same device that you use to access this network, we will help you. We will simply add the rules for all of these cases to our devices. Now such anti-virus and anti-virus programs are installed on all our products. We protect the servers and networks of our customers, we have a big business in IPS. We make many products, individual products, solutions for routers and many other devices. Since it is not enough to ensure the security of the server, the network is like onion layers, it consists of many layers and we must ensure the security of the client at each level and the security of the network as a whole. Many companies offered such programs, but on a separate device, we decided that the program can be placed in an existing one. It’s convenient. You already have a router and it’s much easier to install it on a router. Cisco occupies a unique place, since we supply switches and routers and we can supply them with the right set of protection software so that the problem can be solved at the entrance, and not on 3/4 of the way. We are not the only ones who offer such protection, but it is our programs that stop the virus earlier and work much more conveniently. Our company risks the most in the world. If something goes wrong with the networks, then we will suffer the biggest losses and therefore we are working on maximum convenience and customer protection, we are investing billions of dollars. For in the event of failure, we simply lose 52 percent of our profits, which simply cannot be allowed. And because Cisco routers are the cheapest in the world! : ) You can buy a cheaper switch and then add the desired function to it. But at the moment we produce routers that are equipped with a protection program. This applies to all routers of our production. But not all switches have a similar option. The client can save if he has a switch and then connects to the router of the head office, which already has our protection. We need to stop viruses to prevent attacks on servers. And we do it. But our customers choose for fault tolerance not only Cisco, but also Juniper. Firewalls and other network equipment from two manufacturers at once. To have a great guarantee. It is safe. Nevertheless, Cisco invests the most in security. The network is monotonous and if something goes wrong, we stop it and check. We use the principle of levels to verify and each level has a protective function. We need to protect ourselves, because for each of our good technology there are 30 people who want to hack it and we must be able to do it.

At the beginning of my career, I myself did not understand how to talk with clients and how to conduct presentations in general, but I was told that this was a necessary skill. I was afraid that I would start to tell abstruse things and people would simply fall asleep from boredom. I suggest you use my abstract examples in working with clients. No need to go into technical details, the main thing is to talk about the principle of operation.
Let's move on ...
FastTrack Training. "Network Basics." "Understanding the OSI Model." Part two. Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?

We continue the cycle of 27 articles based on his lectures:
01/02: “Understanding the OSI Model” Part 1 / Part 2
03: “Understanding the Cisco Architecture”
04/05: “The Basics of Switching or Switches” Part 1 / Part 2
06: “ Switches from Cisco ”
07: “ The area of use of network switches, the value of Cisco switches ”
08/09:“ Basics of a wireless LAN ” Part 1/ Part 2
10: “Products in the area of wireless LANs”
11: “The value of Cisco wireless LANs”
12: “The basics of routing”
13: “The structure of routers, routing platforms from Cisco”
14: “The value of Cisco routers”
15/16: “Basics of data centers” Part 1 / Part 2
17: “Equipment for data centers”
18: “The value of Cisco in data centers”
19/20/21: “Fundamentals of telephony” Part 1 / Part 2 / Part 3
22: Cisco Collaboration Products
23:“Cisco Collaboration Product Value”
24: “Security Essentials”
25: “Cisco Security Software Products”
26: “Cisco Security Product Value”
27: “Understanding Cisco Architectural Games (Overview)”
And here is the first of them.
FastTrack Training. "Network Basics." "Understanding the OSI Model." Part one. Eddie Martin December 2012
When I met Cisco, I was just a customer. Now I have been in the field of network technologies for 30 years. I began my career working with the military, with the US Air Force. I actually traveled with President Reagan, so you can imagine how long it was. But not yet about that.
I was a client of the company, a buyer of their services and a user of their technology. In fact, I was their client longer than an employee, because the career in Cisco for me began in 1999. Then the era of IP telephony began.
I was that PBX guy who connected switches and routers and could carry out functions not only the telecommunication manager, but also did a lot of things. They needed a professional and they found me in South Carolina. If you work as an account manager or in a team of accountants, then your team will have a whole link of so-called product sales specialists. They will explain to you how to work with this or that technology. The fact is that when I was just starting out, we were selling voice communication services. In my time, accountants could only write bills for calls, now we have greatly complicated this process due to the development of networks. And these networks have never been so complex. What became a problem, a big problem, as customers hoped that the implementation of their tasks would be simple. And it became more complicated not from the point of view of network engineers, and in terms of technology, but what's great - when we turn on our computers - they work. This is what customers are waiting for. They expect a miracle from us. The incredibly fast development of technologies, namely their transformation, is something amazing.
That is why one of the tasks that was entrusted to me was training new account managers in my own team, since we hired a lot of people from outside, not from Cisco, and they had no experience in the field of network routing. They did not understand switches and routers, but they could sell well. Usually I say this - give me someone who can sell, I don’t worry about whether he knows technology, I can teach, but I can never learn to sell. I myself am not a seller. So the thing went in that direction.
The class was built and for the first three to six months I just kept telling them something, we had lunch, dinner and breakfast together. So the training went on and we realized that this should be done for the entire staff of the company, even the most insignificant, because everyone influences our business and only in this way they can fully understand its essence. Today we will focus more on choosing an approach to selling a product. In fairness, I note that service providers often sell these same services better than sellers.
I left Cisco at will in 2004 and opened my own consulting company. You can see the inscription KEM consulting here. Now I am sitting on the other side of the table. I was hired to go to clients and provoke them to talk about technology. You often have to talk with customers about technology, but I'm one of those they ask, what was that seller talking about? How will this affect my business? Will it help me or not? Or am I just wasting my resources? It's funny to be in my current position, because now I can hear what they said about me, in a way, when I represented the interests of the vendor.
So, we will begin with a discussion about the OSI model. This model has been around for some time, actually longer than I am in this business. It appeared at the beginning of network technology. Before that, we essentially had a large computer and a private network through which everyone connected to this mainframe, everything was centralized, we used ancient terminals, or rather 3270 terminal emulators, because there were no terminals as such. So then there was a network, very private and very close. And then all of a sudden people started building “personal computers” and began to wonder how to make connections between them.

I find it extremely funny, but after I finished working with the military, I started working with American Airlines, which at that time had the largest private data network in the world with a mainframe located in Tulsa, Oklahoma. And it launched the Saber computer reservation system used by the four airlines. And once, in the mid-80s, we had a load of 140 thousand people who connected to this mainframe from IBM. Then everyone used these fucking Raytheon terminals, summit terminals, someone’s stupid term, be they wrong:

And then personal computers appear. The terminal at that time cost 75-85 dollars and it had two color options - green and black or orange and black. And here we replace the terminal with a personal computer worth 4 thousand dollars. We connect them to a separate network, which we had to create. And then the first thing we do is upload a terminal emulator to it so that it looks like a terminal. But we did it for the sake of productivity. Suddenly, we no longer needed typewriters, since we no longer needed to type anything manually. Printers have become network devices and now there is no need to know a person who could print. All these processes began to occur simultaneously. And at that moment when the evolution of what we now call the network took place, there were a lot of competing technologies offered by different companies, with their own vision of how the network should function. Some of them could not function together. Here is a living example. IBM released the first personal computers and American Airlines bought a whole bunch of such computers. We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186: We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186: We installed them and connected them to the network using the Token Ring protocol. God, I loved this system. And here IBM release new computers, with a more efficient 8088 processor, instead of the old 8086, the model was called RM Nimbus PC-186:

And they change the type of connectors to Ethernet. Now computers can not communicate with each other, they can not even communicate when connected to the same Ethernet network. Token Ring does not work with Ethernet, Ethernet works completely differently. In the end, they had to make it all work together, and at that moment, by and large, the OSI model appears.
Today we should not worry about that. Ethernet is used everywhere and lovers of Token Ring, like me, were left out of work, licking their wounds. Like all these people who have contributed to ATM and other similar technologies that are a thing of the past today, since we only have Ethernet. Usually I say this joke later, but I’d better say it now. How do you pronounce Ethernet from a Cisco perspective? Cisco This is Ethernet. You know that I worked at CISCO, it was we who started to offer these technologies to people and we gave the client options to choose from - ATM switches, Token Ring or Ethernet. Clients themselves chose the technology they need. And what happened in the end? We almost did not sell ATM or Token Ring switches and now we do not sell them at all. We can adapt them if necessary, but we do not sell them ourselves. There are no more core network products besides Ethernet,
But the OSI model for vendors and organizations is, above all, a great way to explain why network technologies even exist. There are many industry representatives among us today and I will ask you a traditional question. Why do people even buy routers and switches? Why do they need all these wireless technologies and stuff? Why do they invest their money in this? They need software applications, right? All of these applications are the most important thing in the world for our customers.
I will show you the entire OSI model and all its seven layers. And I will need to tell you why customers need it and why you and I are generally sitting here right now. We must show them that they need these technologies to run their business. They need these routers and switches for the business to flourish. The only reason a customer buys a router and switch is access to applications.
So, we begin to disassemble the model and meet the seventh level. An application layer is the final set of protocols required to access network resources.

What is a protocol? This is the set of rules that we set. That is, to connect to a printer or server, we need this set of protocols. In fact, customers buy all these routers and switches in order to use applications, to have access to the web, which also works via the protocol. This is the only reason they buy them. You will say that I am not seven spans in my forehead and not a local genius, but it took me a long time to get to this conclusion.
And in order to explain this, I would like to talk about the case with my best friend, who decided to open his own business. He trained at Virginia Tech as a chemical engineer and went to work at a naval shipyard in Charleston, South Carolina, as a chemical engineer, a notch lower. He worked on nuclear submarines, conducted a variety of studies, and suddenly for no reason decided to completely change the direction of his activities. He decided to go back to where we had grown up, to the southwest of Virginia. And he wanted to open his own home health care firm. He liked living where he grew up. There are forests, mountains, beauties. In general, he opened his own business and provided people with home services. There are many mining enterprises in our region and people often have lung problems for this reason. And he decided to help people get treatment at home. This is easier for insurance and for hospitals and for the clients themselves. He began selling, for example, air compressors, so that a person could breathe pure oxygen in cases of lung problems. And later he had to build an insurance company. Why did he have to use mail, regular mail, which we called a turtle for fun. That is, he filled out the form, wrote the doctor’s recommendations and sent these forms to the insurance. Then 90 or 95 days later, he received his check for payment. And this is only if the insurance has confirmed everything the first time. It took him 95 days to get his money. Not the best option. And then someone knocked on his door and said - we have the application you need, a server that will solve your problems. You will have a terminal or a personal computer, which will connect to this server and you will enter data and transfer it using new technologies. This technology was called a modem in those days. You will dial the server and transfer data to the insurance company. So, if you invest in this server, in the terminal and the application - this will reduce your expectation from 95 to 70 days.

Are you curious, they asked? And what do you think Mack answered? Of course! Of course! He began to buy equipment that, among other things, needed to be serviced. But time passed and he thought that he needed more employees so that they could work and bring even more profit. And for this, he needs network equipment that will make it possible to connect several computers to the server, not just one. So the first network appeared. This is basically. Primarily. And then other people came and suggested that we should have another server on the network, since we have a lot of equipment and we don’t even know how much, where and when it should be serviced. We have an inventory database, an application that must be connected to a network that allows you to know everything about your equipment. Is it interesting for you? Of course! Spare me the need to do all this. We connected it to the network. After that, he got a service of nurses who worked in the homes of clients and he sent them to different parts of the city. He needed to know who and where and when is located and he created an application with a schedule of their work. Now imagine that you meet my friend Mack in a bar, and this is the most likely place where you can meet him outside the house, and ask him a question - what do you consider the most important thing for your business? He will answer that this is what gives him access to applications. With the development of technology, he got routers and more, but the main thing is that they give him access to applications. How much money do Cisco switches and routers bring? 52 percent profit. About 35-37 percent of them are switches and the rest are routers. These are fundamental products. But they are needed only in order to provide access to applications. That is why we need to make sure that we effectively interact with customers and understand what they need, and they need to use applications.

Now the term of the decision on its payments has decreased from 95 to 45 days. If you have a newer technology that will reduce the waiting time to 40 days, the Mac will be happy. Show her to him. Only geeks like you and me are interested in such technologies, but we have no money. We do not scatter them. I have a wife and two children and I will tell you honestly, I have no money. We need to understand what is important for the client and give it to him, or rather, what he sees as valuable for himself, and these are applications. He doesn’t just need cool switches and routers, and we made really amazing products, but he needs to understand why they can come in handy for him, for which applications they can be used. The network exists solely to use applications! Take another example.
Mac has a router, to which more routers are connected in various places, his network is now wide. What if a young employee here and another employee from another segment of the network decide to install on their computers the latest version of some new game, like Doom or something else? They will want to play on the network, fight with each other. They will phone and agree to download the game and play during lunch. They will need an intermediary who will transmit this high-resolution video and the game and the network can become very busy. We need the network to be smarter, it must prioritize the so-called QoS. She should put paramount tasks above such gaming. Mac will say that for him, working servers are much more important, they are in the first place, and everything else is in third. Should the network somehow understand its priorities? Yes,
This is what we did in the 90s. We have invested millions and even billions of dollars in order to make our decisions smarter and determine what is more important in a particular network. An ordinary packet or a packet containing a frame, which packet can be delayed and which not. What was determined by QoS. We started broadcasting voice over the data network and then we really started using priorities, so IP-telephony appeared. The network must meet our business challenges. And she can, if she is smart enough. Cisco does just that and offers people not only switches and routers, but also applications that can make them smart, otherwise the network will not work and customers will not receive what they paid for. In the future, I will tell you about the servers that we use to work. But the main thing is the applications that our users need. It’s interesting for us to talk about technologies and protocols, but our customers only think about their business. They wake up in the morning and don’t think that they need a new switch or router. They think that the economy is in poor condition and they need a successful business, they want to survive. They want their business to flourish and to bring as much profit as possible. We must balance our efforts with their requirements. We must follow our strategy. And it's simple when you are a local manager, but if you are a regional manager and you have 1200 clients, then it becomes difficult to act in accordance with the strategy. But if you try to ask at least a couple of questions to clients, then the strategy will be easier to build. You will be able to think outside the templates and expand the capabilities of customers. Understand that we need to constantly find out how we can strategically help the business of our customers. This is what I do as a consultant. Implementation sometimes changes the picture completely. Thus, we discussed the seventh level - the application level, which truth is the most important level for me.
We go down a level below. This is a presentation layer that acts as a kind of adapter. He makes a picture from a JPG image so that we can send it. The application sees the image as an object and turns it into a JPG file. We are adapting this facility. The text gets its own format, its own picture, this makes it possible to turn all zeros and ones into the objects we need. Adapt them to your needs. But that is not all, we have added here some more functions and settings. I will explain this with an example of an Internet browser. How many browsers do we know? Chrome, Internet Explorer, Firefox and many others. They all use the same protocol. Which one? HTTP For example, I want to send a PowerPoint presentation to your computer. We call this file sales.ppt. But how the network will understand What format is this document? When the creators of PowerPoint thought about this task, the task of transferring files, they knew what to face with it.

And they came up with a file transfer protocol called File Transfer Protocol or FTP protocol. If I want to send a letter from one mail server to another, then I use the simple mail protocol or SMTP (Simple Mail Transfer Protocol). If I need network management, then I use the Simple Network Management Protocol (SNMP). And all these are standard applications that you can use for your own purposes.
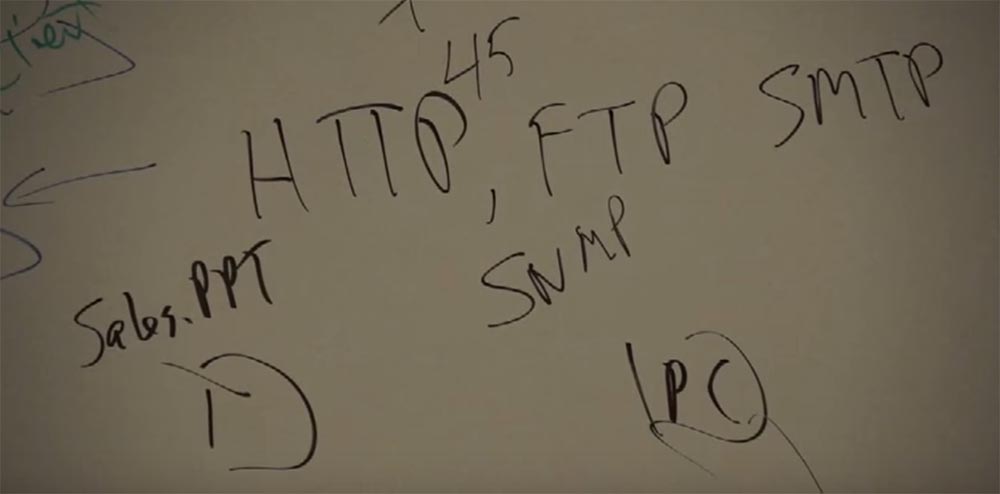
My wife believes that the Internet was created for only three things - shopping, email and information. No, not for facebook. Do not guess. She does not have a facebook, she uses mine, I don’t even close it, because she communicates with friends. She loves to write letters to relatives, as she comes from a large Italian family from the northern part of New York and now her relatives live all over the country, and not as before in one big house. And she very often uses E-mail, keeps in touch, finds out what is happening: “Oh God, you know, Joey’s girl is just awful for him,” and that's it. It also reads news on the Internet. She really likes these gossip columns, she always reads how things are with the Kardashian family, the whole Kardashian family and more. She is crazy about local newspapers, and always loves to know who is arrested - “they drove intoxicated, the whole family, for years,” In general, you understand me. She also loves shopping. And when we started dating, I still did not know about the company that produces women's clothing. The company is called Talbot. They produce expensive clothes. When we walked around the mall, I often noticed their signboard and red door, but I never came in until it dragged me there. You know this:
- I look like?
- You look amazing.
But when you look at the price, you understand that it’s not so amazing, in your mind, not by ear, but the essence of what. Now, in the era of the Internet, Talbot write letters herself to her and offer new collections of clothes and she does not need to go anywhere. She can buy a spring collection, which also has not appeared in stores. But why is the company doing this? Why do they do such mailings? So that a person can enjoy shopping at home, sitting on a comfortable sofa.
I remember how we were going to a friends wedding last summer and she bought three or four dresses for this and I thought if we were going to a wedding or a fashion show? For dresses, she needed shoes, bags and other trifles and she could choose all this while sitting at home. What did she need for this? Personal computer, Internet, Talbot servers. There should be two of them. Why two? They are like bulbs, they can burn out. You turn on the light at home and in 99.99% of cases the light comes on, but there comes a time when the light bulb burns out. Also, the server, electronics, which can fail and therefore at least two are needed to increase fault tolerance and scaling. We now have the most powerful multi-core processors, and then it was necessary to use many servers for scaling. So, my wife sits on the couch and adds things to the basket, and then she needs to press this magic button "Payment". And what will she do? She needs to enter my credit card details into their system so that they charge me. My card ... She knows all my credit card numbers. And all this, including my personal information, will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes. will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes. will go through the most insecure network ever created in the world - the Internet. What then should Talbot representatives provide? The security of my data. And then in a small company like Netscape, they created a completely new protocol for these purposes.
A little help:
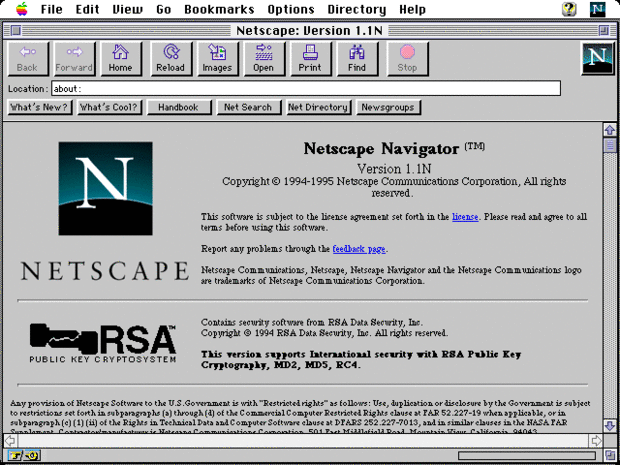
Netscape Communications created HTTPS in 1994 for its Netscape Navigator web browser. HTTPS was originally used with SSL. As SSL evolved into Transport Layer Security (TLS), HTTPS was officially identified by RFC 2818 in May 2000.

If you pay attention, at the moment of transition to the payment page, the protocol changes from HTTP to HTTPS. Why? Because now it is a secure network. This creates a secure tunnel for the transfer of personal data of the client. It is at the presentation level that this encryption is performed. We now not only convert files and data to zeros and ones, but also encrypt them, creating an additional layer - a secure socket. Our personal computer starts encoding by adding a certain code to the information, which only he and the server to which we send the information can decrypt. Nobody else.
This happened in the late 90s, then there was still no opportunity to buy so much on the Internet. There were no sites like Amazon and others. People did not know how to transfer money and the protocol was just invented. I will say again that at that time we did not have such powerful multi-core processors. At the same time, as many as 5 thousand people could make purchases. And they all begin to send letters and they want to order their product, because the stock, you know, today is a 30% discount, and tomorrow 40% and everyone is running to buy - sale! You will not have problems with sending letters, but let's look at this process from the point of view of Talbot servers. At that time, and with those technologies of the 90s, they could process requests, despite the fact that 30 percent of the server capacity went to coding, 30%!
And what should be done in this case? Of course, if we are successful, add more servers.
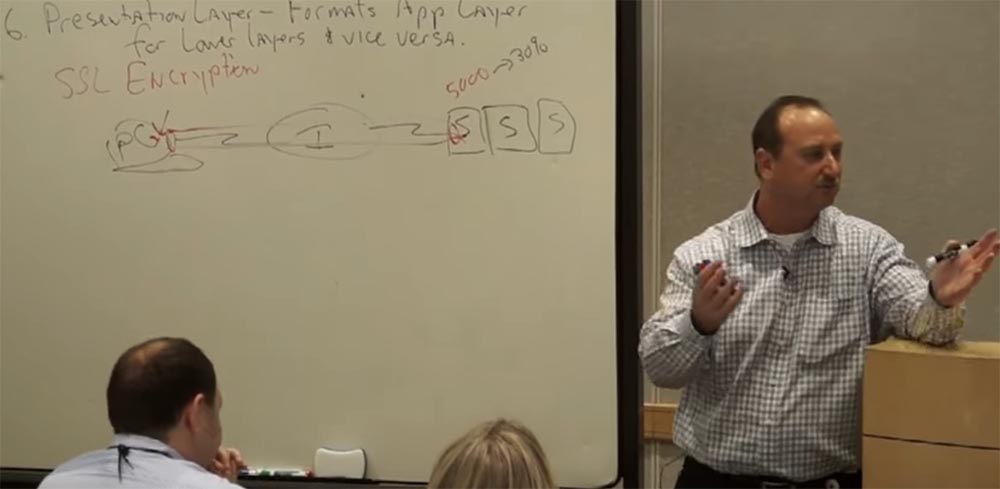
Servers are like children. I did not know what return on investment (ROI) could be expected, but I did two. My son is 13 now and his daughter is 15. I remember how Emily was born. She weighed only 4 pounds and 11 ounces, was so tiny, and I promised her that I would become the best father in the world and give her everything she needed. Now she has grown up and is choosing an expensive college and is testing my nerves by driving. But servers are like children too. They need to invest a lot of money. How much does the server cost? These are not only computers. You need to pay for electricity, but the servers will be very hot and you need to cool them, and here you need air conditioners. But not only them. You will still need such cheap applications like Oracle, right? :) Also, you will need people who know how to keep an eye on these servers and databases, who will put things in order there and monitor their work. You buy servers and pay a bunch of additional costs, which you simply can’t do without. Just like with children, that's why I compare them with children.
At that moment, Cisco came up with a proposal. Why would you buy another server and pay crazy money for its contents? What if we sell you a device that itself will encrypt all this data, live inside your network and give you the finished code at the output? In addition, the device will also be able to evenly distribute tasks between servers, depending on their load, act as a balancer. Cisco combined with a presentation layer offers customers more than just the transfer of data and packets over the network, they offer an additional level of intelligence. To implement what, at one time, a whole company was acquired, which allowed the manufacture of a device that allowed the hardware to balance the load that the program could not do so effectively. In this way, Cisco helped a lot of companies save a lot in the early 90s and early 2000s, as they didn't need to increase the number of servers anymore. That is what our company continues to do so far. We reduce the costs of our customers. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video. They would have to add and add these servers, increase their number constantly. Now it did not have to be done so quickly. The network itself provides you with the necessary services. QoS (quality of service, priority) increases if you offload SSL, but there are still many different services on the network that need to be provided. One of them is a video.
Emily loves video calling. She is ready for hours to chat face-to-face with her friends, but sometimes she invites girlfriends to chat with her friends. That is, she invites Mary Kay, Lexie, and they are their friends and a small fight is arranged because of the guys at school, which they really love. But this requires a bridge that allows them to communicate via video. A service that will allow this to materialize. That's what we sell, we sell the ability to enable and use this technology, to make it the most effective. Yes, this is a combination of software and hardware, all Cicso solutions are always software, we call it in Cisco iOS, and certain uniquely designed devices, always a combination of the first and second, second and first. We produce a complete product. Of course, companies like Amazon don't need this right now, they have their own software and powerful processors. But we did this in the late 90s, when there were no powerful processors, we saw the needs of customers and offered them a solution. In this case, the customers wanted to save money and we helped them. We saw this trend in the industry, we saw evolution, we realized what customers would need at this stage. We gave them the opportunity to reduce the number of servers and save money by meeting the needs of their applications, that's all, this is not rocket science.
The fifth level is the session level. This is like the first handshake of a client and its server. At the application level, you click on the icon of a browser or other program, the connection to the Internet begins and the transition to the site. This is the first handshake. The client seems to get acquainted with the server and says to him:
- Hello! Here are the rules by which we will work with you. Today we will transfer the file and use FTP, so you must understand the rules for the transfer.
This is essentially the first level at which the client, that is, the computer, communicates with the server through the network. The computer tells the server:
- Hello!
And he answers him:
- Let's work together!
You may even notice how “Session Start” appears on the page.

Imagine that it is a mail server and you are using Outlook. You click on the icon of this program and it, when opened, gives a signal via the POP3 or IMAP protocol that you need to go to the server and pick up the mail. And it all starts with the installation of the session, from the beginning of this session. But every time we create or use some kind of application, we should think about those people who want to harm us. About those who write viruses or try to steal our data with you. I know that no one carries desktops with us, we often use mobile devices - laptops or phones, at Starbucks or at a hotel, connect to many different networks and don’t think about the local connection being unsafe.
What if one of these bugs, called a virus, clings to your mail? What if the task of this bug is to drive your server crazy by loading it to the limit? You connect to the server and the virus begins to plague it. We use antiviruses, but what happens next? The appearance and functions of viruses change very quickly. And antiviruses stop detecting them. We have to update antiviruses again and again and again. But what if the network is smart and knows all the protocol rules? Can she then protect your server in the best way? Of course! You don’t have to worry so much about the server.
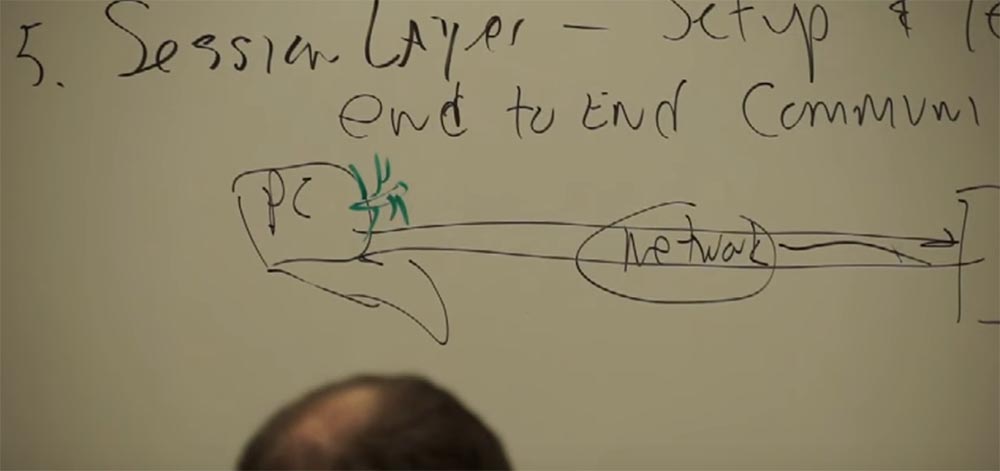
We have created a whole line of products for detecting violations and intrusions, which works at the level of POP3, IMAP, etc. protocols. This means that in the case of mail, we added to the network a device through which all mail going to the server passes. The device monitors the correctness of the sessions. It tracks traffic.
And when your server is attacked by a virus, you will find out about it, since at first the virus will go through the device upon its detection. We will discover it and will be able to end the session simply by breaking the connection. Is there something wrong with this client and it is attacking the server? Turn it off. For the client, this is an incredibly useful feature. But I never liked this, to be honest, since the analysis of the traffic takes place after it has passed, not in real time, it looks like a ghost chase. The virus is already on the other side, we did not stop it, we just found out about it. Then we had to think further and decide how to stop the virus. And we came up with a program not to detect, but to prevent intrusions and violations. We decided to filter them in the network, in real time, to pass all traffic through ourselves.

Imagine that we have a track. We indicate the direction of movement in the lanes. A program to identify violations will be presented as a policeman standing on the sidelines. He stands with a weapon, a walkie-talkie and a baton and listens to the radio, eating a donut, and then some nut from North Carolina rushes at a frantic speed through the oncoming traffic. The policeman transmits information about him on the radio:
- There’s some kind of crazy man rushing along the oncoming road at a speed of 60 miles per hour, there may be an accident down the road.
But he cannot stop him, and in the end something terrible can happen. But the program to prevent violations and intrusions will stand in the form of a policeman in the middle of the road, and the policeman will not eat a donut, but will be ready to block the path. The psycho will have to stop and surrender to the policeman, who will take his keys from him and remove him from the road. And which option would you prefer? Of course, the second.
No questions. Since your business is based on the work of applications. And when you want to have such a device in the structure of your network, and even on the same device that you use to access this network, we will help you. We will simply add the rules for all of these cases to our devices. Now such anti-virus and anti-virus programs are installed on all our products. We protect the servers and networks of our customers, we have a big business in IPS. We make many products, individual products, solutions for routers and many other devices. Since it is not enough to ensure the security of the server, the network is like onion layers, it consists of many layers and we must ensure the security of the client at each level and the security of the network as a whole. Many companies offered such programs, but on a separate device, we decided that the program can be placed in an existing one. It’s convenient. You already have a router and it’s much easier to install it on a router. Cisco occupies a unique place, since we supply switches and routers and we can supply them with the right set of protection software so that the problem can be solved at the entrance, and not on 3/4 of the way. We are not the only ones who offer such protection, but it is our programs that stop the virus earlier and work much more conveniently. Our company risks the most in the world. If something goes wrong with the networks, then we will suffer the biggest losses and therefore we are working on maximum convenience and customer protection, we are investing billions of dollars. For in the event of failure, we simply lose 52 percent of our profits, which simply cannot be allowed. And because Cisco routers are the cheapest in the world! : ) You can buy a cheaper switch and then add the desired function to it. But at the moment we produce routers that are equipped with a protection program. This applies to all routers of our production. But not all switches have a similar option. The client can save if he has a switch and then connects to the router of the head office, which already has our protection. We need to stop viruses to prevent attacks on servers. And we do it. But our customers choose for fault tolerance not only Cisco, but also Juniper. Firewalls and other network equipment from two manufacturers at once. To have a great guarantee. It is safe. Nevertheless, Cisco invests the most in security. The network is monotonous and if something goes wrong, we stop it and check. We use the principle of levels to verify and each level has a protective function. We need to protect ourselves, because for each of our good technology there are 30 people who want to hack it and we must be able to do it.

At the beginning of my career, I myself did not understand how to talk with clients and how to conduct presentations in general, but I was told that this was a necessary skill. I was afraid that I would start to tell abstruse things and people would simply fall asleep from boredom. I suggest you use my abstract examples in working with clients. No need to go into technical details, the main thing is to talk about the principle of operation.
Let's move on ...
FastTrack Training. "Network Basics." "Understanding the OSI Model." Part two. Eddie Martin December, 2012
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending it to your friends, a 30% discount for Habr users on a unique analogue of entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to divide the server? (options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA!Read about How to Build Infrastructure Bldg. class using Dell R730xd E5-2650 v4 servers costing 9,000 euros for a penny?
