As I asked students to write phishing emails
- Teacher, I picked up a good password, which can not be in the dictionaries.
Yin Fu Wo nodded.
“I introduced it to Google,” the Sysadmin went on, “and made sure that there wasn’t such a combination on the Web.”
- Now it is.
I am a graduate student and teach virology at the university.
Six months ago, before the start of the fall semester, I was given a whole stream of fifth-year students - 45 people with different backgrounds, interests and attitudes. Even then, I thought it was a good base for some kind of scientific experiment. Two months later, I came up with everything and asked students to write phishing emails.

Under the cut, what came of it, what they were for, and a little analytics about the work of popular mail services. And the letters themselves, of course.
Caution, a lot of screenshots.
Do not engage in phishing. Formally, this is fraud, it is prosecuted under article 159.6 of the Criminal Code of the Russian Federation. Laboratory work was carried out under controlled conditions, letters were sent to pre-prepared boxes, access to which is available only to the author of the post.
All characters are fictitious, all coincidences with real people and organizations are random. All logos, trademarks and names belong to their respective owners.
I immediately realized that nothing interesting would come of sending letters to my personal mail - there would be boring spam, which would be of no use and educational value. Students should understand why they are doing this (spoiler: to know how to defend themselves) and what an approach to any person can be.
Therefore, before giving the assignment, I gave a lecture on targeted attacks, social engineering and phishing, showed examples and explained that any person is vulnerable.
And again, he recalled the criminal liability for fraud.
I came up with three characters. Each of them works somewhere, is interested in some things and experiences weaknesses. All three are from different cities, of different ages and with different life values (at least I thought about it when I prescribed them).

Of course, for various reasons, these three use different mail services - from Google, Yandex and mail.ru. They have different spam filters, and it was interesting to understand where it is better.
It's time to introduce the characters.
Mazaeva Olga Venediktovna, 53 years old, accountant, LLC Vector, Voronezh. Mail to mail.ru, mazaeva1964@inbox.ru.
Vladislava Olegovna Petrichenko, 21, office manager at Astek, Tomsk. Mail - zlatovladka@yandex.ru.
Andrey Pimanov, 26 years old, tester at Alphabetic Issues, St. Petersburg. Mail - ultradoter9000@gmail.com.
Naturally, simply giving descriptions of people and their electric mail would not be enough for a full-fledged laboratory work, so I formulated the conditions. I bring them unchanged.
In the report, I asked to attach the text of the letters, received logins and passwords and analytics hares about why the letters turned out to be so. For the rest, students had complete creative freedom.
I also gave students some links with useful info and began to wait.
To begin with, it is worth saying that links in almost all letters work and lead to sites of varying degrees of roasting.
The first packet of letters arrived a week later. We give the floor to the authors.

I scolded the authors on the subject of sending screenshots, but counted the letters.
The authors received the standings first from the entire stream.
For obvious reasons, 135 letters and their detailed description will not be able to enter the article. Also, I do not attach links to phishing sites - mainly for ethical reasons.
So, there were a lot of letters, but some intermediate result needs to be summed up. Further, in what direction the students thought and what letters came most often.
The most notable ones are under the spoilers.
Accountant Olga Mazaeva received 11 letters from her favorite game in Odnoklassniki and another 5 letters about free or almost free arrangement of fives on pictures of school friends.
They also tried to warn her of various things by the Federal Tax Service, 1C, Sberbank and Odnoklassniki security service.
As expected, the most difficult letters were given to students by the paranoid tester Andrei. Basically, of course, the difficulties were due to the Google Mail spam filter, but the students themselves came up with fewer attack vectors here than in other cases.
Andrei received an uncountable number of letters from Steam, about ten from Aliexpress and other Chinese stores and a couple more from Google. The most delicious, all of a sudden, from the Sam Susam airsoft club, see under the spoiler.
All students loved Vladislav. She carefully sent links to dating sites suitable for the type of partners, and even a promotional code for Photoshop to edit photos was even more pleasant.
In general, they probably should, but no.
Gmail did the best job - out of 38 emails, 13 ended up in the Spam folder. Google Mail filtered emails “similar to the ones that we have already blocked” and those that “contain things specific to phishing emails”.
In second place out of three Yandex - he filtered out the disappointing three letters. Unfortunately, Yandex does not indicate the reason for the block in the mail interface.
On mail.ru the only letter got to spam.
If you recall how successful letters looked, I would not call the work of all three services good. And even no percentage of filtered emails from gmail solves the problems with phishing and targeted attacks. Attackers can pretend to be anyone and, knowing very little about you, will gain access to your accounts.
I believe that the laboratory work was a success. After the conversation, students understand (or pretend they understand) how to protect themselves from phishing and why you do not need to do this in real life - fraudsters face a real prison term under article 159.6 of the Criminal Code of the Russian Federation. I have warned students about this many times in lectures and workshops. Do not do that either.
How to defend yourself?
Many thanks to the students who participated in this experiment. I'll meet you at the exam :)
And thanks to everyone else for reading to the end. Do not be fooled.
Yin Fu Wo nodded.
“I introduced it to Google,” the Sysadmin went on, “and made sure that there wasn’t such a combination on the Web.”
- Now it is.
I am a graduate student and teach virology at the university.
Six months ago, before the start of the fall semester, I was given a whole stream of fifth-year students - 45 people with different backgrounds, interests and attitudes. Even then, I thought it was a good base for some kind of scientific experiment. Two months later, I came up with everything and asked students to write phishing emails.

Under the cut, what came of it, what they were for, and a little analytics about the work of popular mail services. And the letters themselves, of course.
Caution, a lot of screenshots.
A warning
Do not engage in phishing. Formally, this is fraud, it is prosecuted under article 159.6 of the Criminal Code of the Russian Federation. Laboratory work was carried out under controlled conditions, letters were sent to pre-prepared boxes, access to which is available only to the author of the post.
All characters are fictitious, all coincidences with real people and organizations are random. All logos, trademarks and names belong to their respective owners.
I immediately realized that nothing interesting would come of sending letters to my personal mail - there would be boring spam, which would be of no use and educational value. Students should understand why they are doing this (spoiler: to know how to defend themselves) and what an approach to any person can be.

Therefore, before giving the assignment, I gave a lecture on targeted attacks, social engineering and phishing, showed examples and explained that any person is vulnerable.
And again, he recalled the criminal liability for fraud.
Dramaturgy
I came up with three characters. Each of them works somewhere, is interested in some things and experiences weaknesses. All three are from different cities, of different ages and with different life values (at least I thought about it when I prescribed them).

Of course, for various reasons, these three use different mail services - from Google, Yandex and mail.ru. They have different spam filters, and it was interesting to understand where it is better.
It's time to introduce the characters.
Mazaeva Olga Venediktovna, 53 years old, accountant, LLC Vector, Voronezh. Mail to mail.ru, mazaeva1964@inbox.ru.
He does not like modern technology. Sometimes she plays in Pirates Treasures on her son’s donated phone. Able to press buttons in 1C, but, in general, with you computer.
In the past she worked as a financier in the NGO JOUL. In the 90s, a western investor bought the plant, and staff was reduced. He has an account in Odnoklassniki, sometimes he puts five friends with a plus for money for childhood friends.
Vladislava Olegovna Petrichenko, 21, office manager at Astek, Tomsk. Mail - zlatovladka@yandex.ru.
After a semester of computer science in the second year, I am now sure that the work of system administrators is much simpler than her. Of course, playing tanks all day and sometimes plugging cables pulled out by stupid accountants. Masterfully handles his selfies in Photoshop - replaces flowers with flowers in Malta. This is her first job, so she only learns to copy documents using the COPY button on the MFP, and not by scanning and printing. Vladislav is registered on thirteen dating sites, because he is waiting for the man of his dreams, and not a spineless rag.
Andrey Pimanov, 26 years old, tester at Alphabetic Issues, St. Petersburg. Mail - ultradoter9000@gmail.com.
Paranoid and liberal. Recently he transferred all his data to Google Drive, and passwords to Google Smart Lock, because the old mail.ru account, according to him, “was hacked by a bloody gebe.” He is obsessed with airsoft, a regular participant in the Sam Susam club tournaments. I bought 458 games in "Steam", played only 6. Every week she goes to the post office for packages from Chinese online stores. I ordered a laptop on Girbest and is terribly proud of it.
Naturally, simply giving descriptions of people and their electric mail would not be enough for a full-fledged laboratory work, so I formulated the conditions. I bring them unchanged.
Laboratory conditions
Conditions
- Letters really need to be sent to the indicated mailboxes. If you use specially created mailboxes, then after sending, send a list of addresses indicating your last name and group number.
- It is believed that characters open letters on work computers during working hours.
- When writing, you need to use the individual characteristics of the characters. By default, it is believed that a letter written to anyone without details does not count.
- The purpose of the attack is access to the internal network or to the data (mail, calendars, archives, financial information) of the organization in which each of the characters works. Lower priority in obtaining personal data of characters.
- From whom, under what pretext and how the attack will be made, remains at your discretion. Use of add. funds (scripts, documents with macros, software) counts if there is a suitable legend.
- Spam emails do not count.
In the report, I asked to attach the text of the letters, received logins and passwords and analytics hares about why the letters turned out to be so. For the rest, students had complete creative freedom.
I also gave students some links with useful info and began to wait.
Read letters
To begin with, it is worth saying that links in almost all letters work and lead to sites of varying degrees of roasting.
The first packet of letters arrived a week later. We give the floor to the authors.
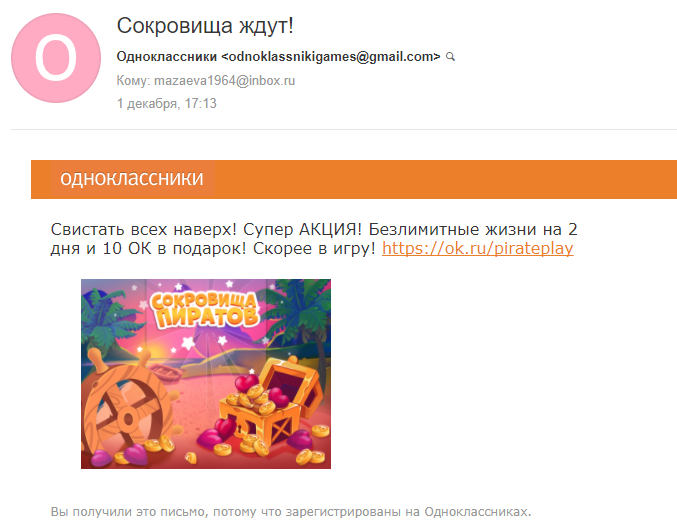
Letter to Olga Mazaeva
Creating this letter, we emphasized the interest of our addressee in the game “Pirate Treasures” and in obtaining the so-called “OKs” in the Odnoklassniki network. In addition, we took into account the well-known fact that people like to participate in various promotions, while receiving something completely free.

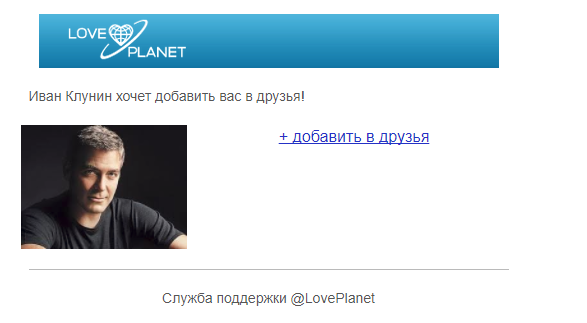
Letter to Vladislav Petrichenko
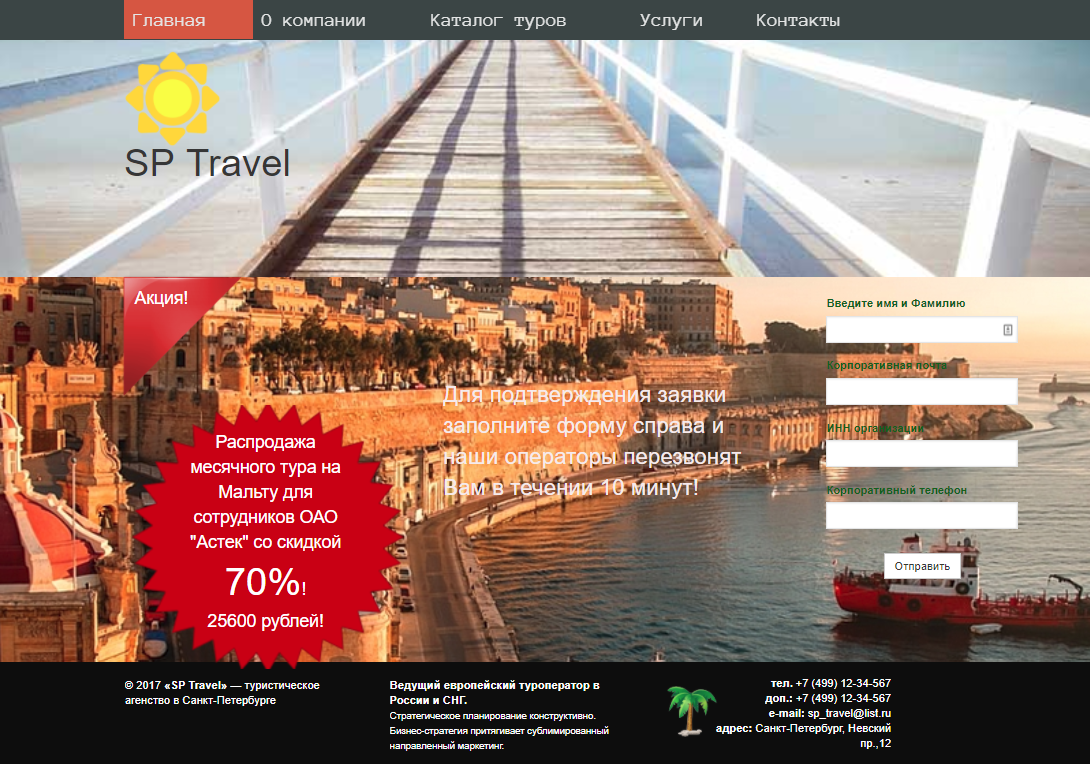
When creating a letter for this addressee, we used the employer company as the imaginary sender, used the company logo of the company, which added to our addressee confidence in the “reliability” of the phishing letter. In addition, we again used social engineering techniques, including a message about the drawing in our letter, making a prize for participation in a ticket to Malta, our beloved recipient, adding a counter to the phishing site that reduces the remaining number of prizes.

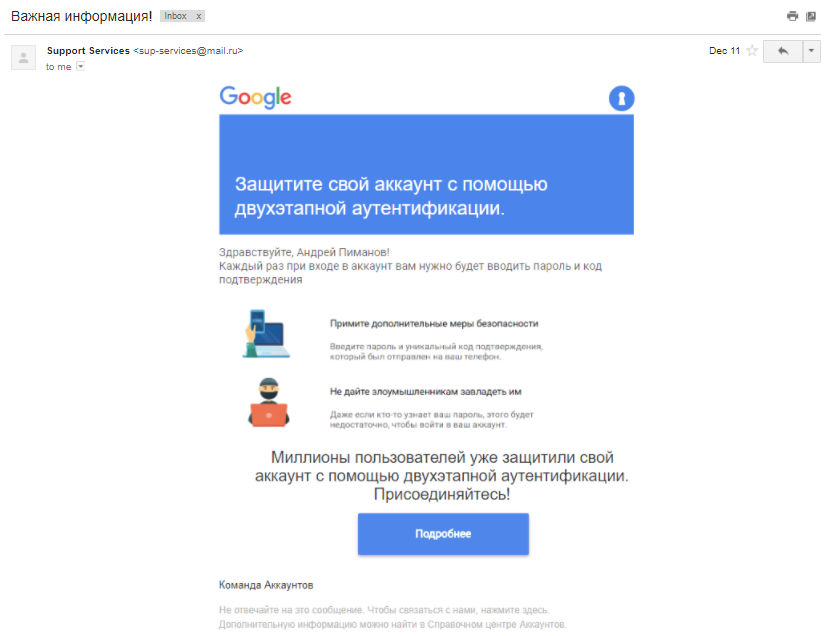
Letter to Andrei Pimanov
Based on the data on the paranoidality of the recipient regarding the security of their data, the subject of the letter, it was decided to choose an improvement in Google's data protection system, namely the inclusion of two-step authentication. However, when creating the letter there were problems, Gmail services, recognizing content similar to theirs in our letter, sent the letter to spam all the time. To solve this issue, we had to make a screen of the letter we compiled, insert the screen into the sent letter, and attach a link to our phishing site to it.

I scolded the authors on the subject of sending screenshots, but counted the letters.
The authors received the standings first from the entire stream.
Doubtful analytics
For obvious reasons, 135 letters and their detailed description will not be able to enter the article. Also, I do not attach links to phishing sites - mainly for ethical reasons.
So, there were a lot of letters, but some intermediate result needs to be summed up. Further, in what direction the students thought and what letters came most often.
The most notable ones are under the spoilers.
Olga Mazaeva
Accountant Olga Mazaeva received 11 letters from her favorite game in Odnoklassniki and another 5 letters about free or almost free arrangement of fives on pictures of school friends.
They also tried to warn her of various things by the Federal Tax Service, 1C, Sberbank and Odnoklassniki security service.
Hot letters
Press on the patient. How to give ratings if the account is blocked? And there all his life, messages, girlfriends, that’s all. Of course, no one makes such huge buttons in official letters, it is, rather, a reception from sites selling unique courses in the world. But it seems to work.
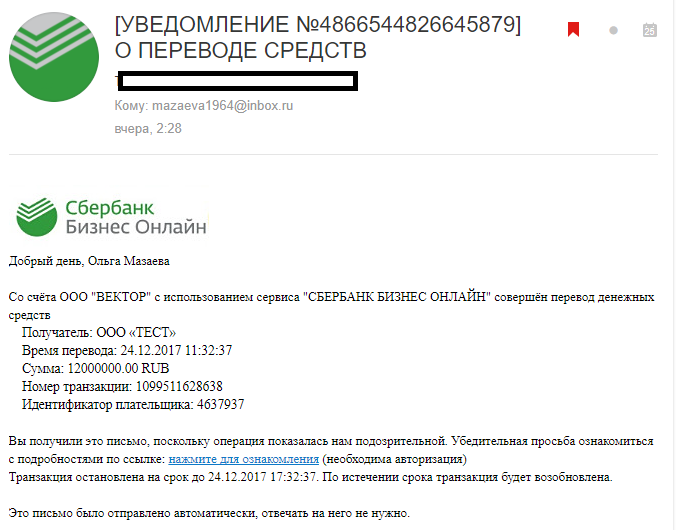
If you are responsible for security in your company, tell your employees that banks will never send a single confirmation of corporate financial information to their personal mail.
Here, of course, the author went too far with the amount of translation. If it were ten times smaller, the potential harmful effect could be ten times larger.
Never do such things in real life, please.
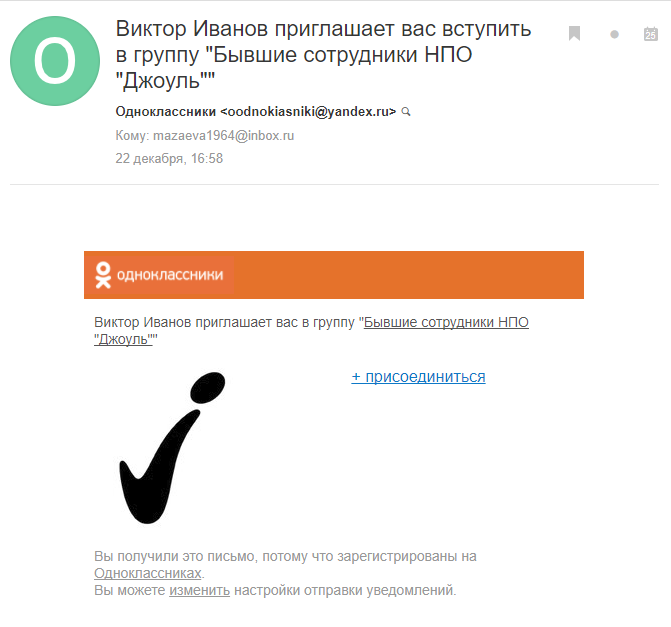
How not to join former colleagues? Click, password, hijacked account.
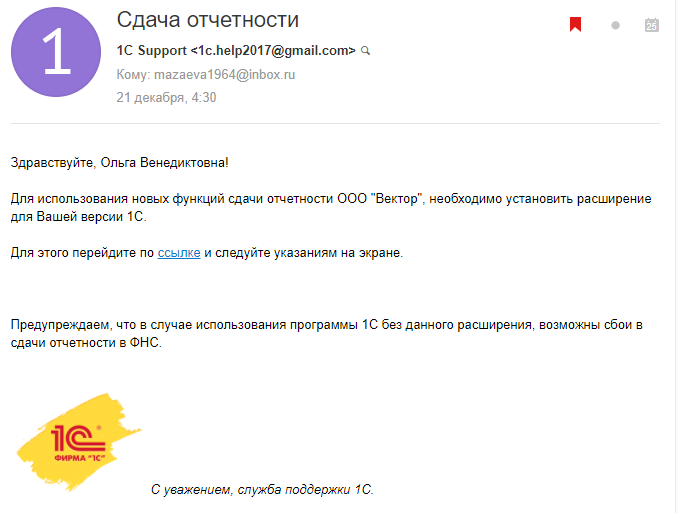
Another example of the impact is supposedly from product support, which a person uses every day. Never download any of these letters, but rather call the responsible for security and warn them.

mail.ru kindly transferred this letter to the "Registration" folder to make sure that everything is fine. All is not good. Do not enter any confirmation codes for transactions that you did not do, and erase such letters.
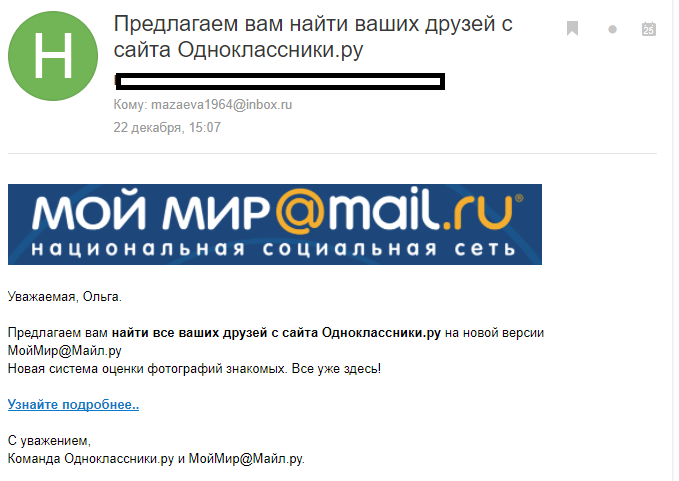
Try the new version of the product. Give it a try! Try it !!! There is a new rating system! Not from 1 to 10, but from 1 to 12 .
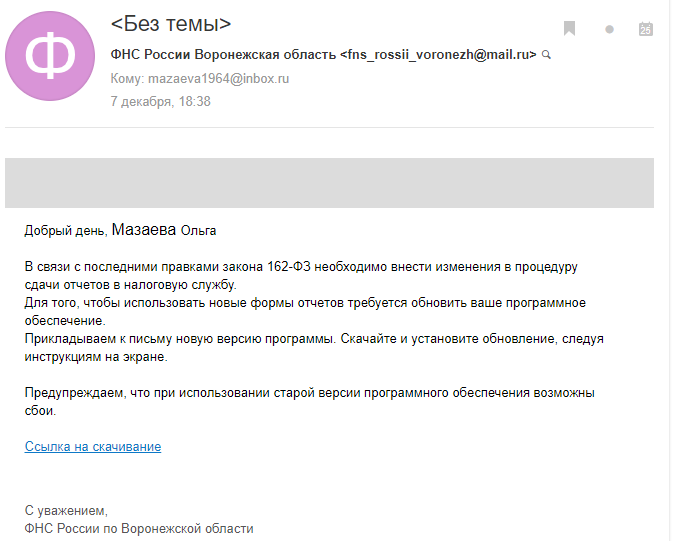
The devil in the details. The author of the letter copied Mazayev from the Google Dock, so the font did not match. And again - update the software. Which one? Yes, it doesn’t matter, just update. By the way, the training keylogger carefully written by the student is here.

Press on the patient. How to give ratings if the account is blocked? And there all his life, messages, girlfriends, that’s all. Of course, no one makes such huge buttons in official letters, it is, rather, a reception from sites selling unique courses in the world. But it seems to work.

If you are responsible for security in your company, tell your employees that banks will never send a single confirmation of corporate financial information to their personal mail.
Here, of course, the author went too far with the amount of translation. If it were ten times smaller, the potential harmful effect could be ten times larger.
Never do such things in real life, please.

How not to join former colleagues? Click, password, hijacked account.

Another example of the impact is supposedly from product support, which a person uses every day. Never download any of these letters, but rather call the responsible for security and warn them.

mail.ru kindly transferred this letter to the "Registration" folder to make sure that everything is fine. All is not good. Do not enter any confirmation codes for transactions that you did not do, and erase such letters.

Try the new version of the product. Give it a try! Try it !!! There is a new rating system! Not from 1 to 10, but from 1 to 12 .

The devil in the details. The author of the letter copied Mazayev from the Google Dock, so the font did not match. And again - update the software. Which one? Yes, it doesn’t matter, just update. By the way, the training keylogger carefully written by the student is here.
Andrey Pimanov
As expected, the most difficult letters were given to students by the paranoid tester Andrei. Basically, of course, the difficulties were due to the Google Mail spam filter, but the students themselves came up with fewer attack vectors here than in other cases.
Andrei received an uncountable number of letters from Steam, about ten from Aliexpress and other Chinese stores and a couple more from Google. The most delicious, all of a sudden, from the Sam Susam airsoft club, see under the spoiler.
Hot letters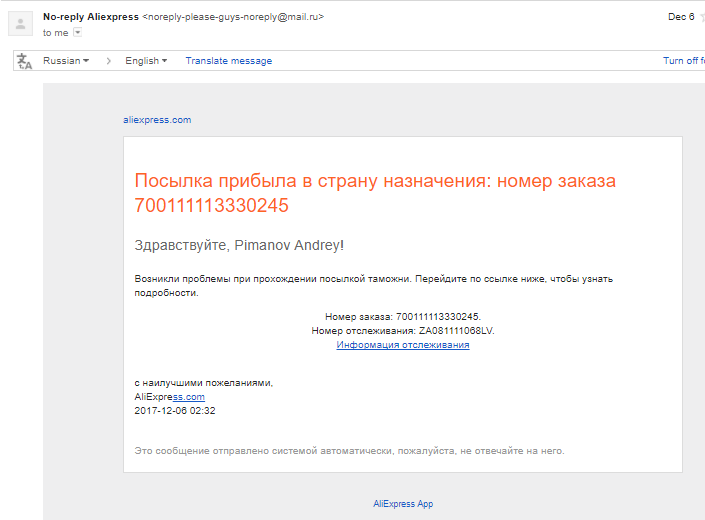
Now you need a TIN at customs, so the letter may work. Go figure it out what the order number is, when you receive several packages every week. There is a version that in AliExpress there are not such tongue-tied copywriters, but this is a matter of taste.

Winner in the category "Letter that Google will never write to you." The link is not hidden, there is no corporate layout (even a screenshot of the finished letter), the text was hastily written. Good day!
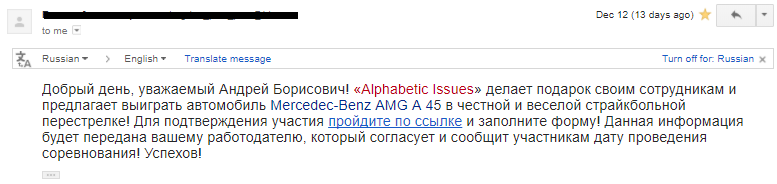
A letter is like a letter. It’s much more fun where the link leads (do not enter anything there!).
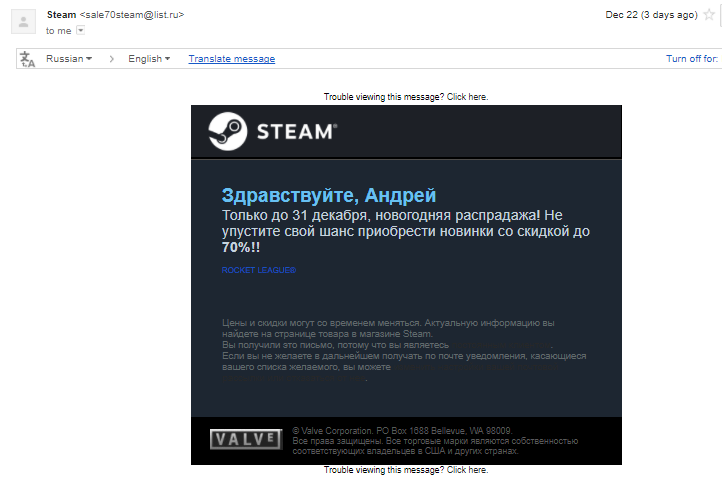
New Year's sale in incentive for those who are and can.
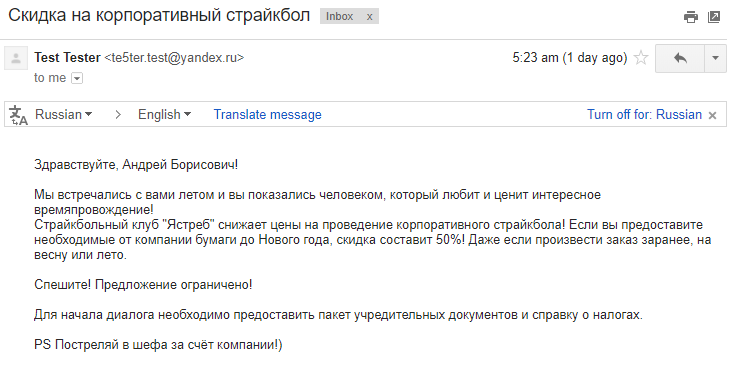
Good. With a package of constituent documents and a tax certificate, of course, they overstepped it, but it also looks like an ordinary letter. There is no link and, if you don’t think about it, you can accidentally send something wrong.
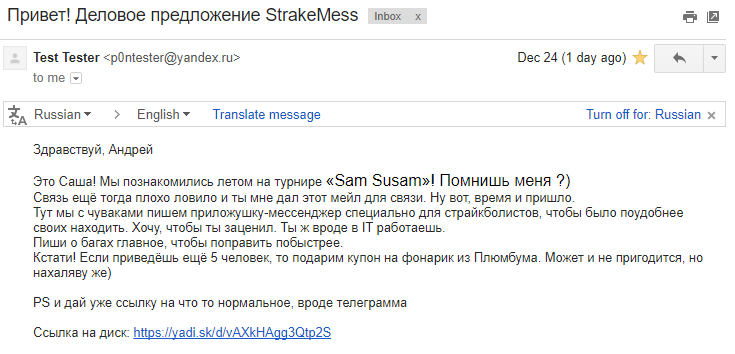
Definitely my favorite letter. Everything is fine here: it is written in human language, it does not try to disguise itself as popular sites, but there are pleasant trifles in the text that give care. Imaginary, of course. Be on the alert!

Now you need a TIN at customs, so the letter may work. Go figure it out what the order number is, when you receive several packages every week. There is a version that in AliExpress there are not such tongue-tied copywriters, but this is a matter of taste.

Winner in the category "Letter that Google will never write to you." The link is not hidden, there is no corporate layout (even a screenshot of the finished letter), the text was hastily written. Good day!

A letter is like a letter. It’s much more fun where the link leads (do not enter anything there!).

New Year's sale in incentive for those who are and can.

Good. With a package of constituent documents and a tax certificate, of course, they overstepped it, but it also looks like an ordinary letter. There is no link and, if you don’t think about it, you can accidentally send something wrong.

Definitely my favorite letter. Everything is fine here: it is written in human language, it does not try to disguise itself as popular sites, but there are pleasant trifles in the text that give care. Imaginary, of course. Be on the alert!
Vladislav Petrichenko
All students loved Vladislav. She carefully sent links to dating sites suitable for the type of partners, and even a promotional code for Photoshop to edit photos was even more pleasant.
Hot letters
Pretending to be the security service of your organization is a favorite trick of scammers. Formal style, document in the attachment. No need to go anywhere, download and watch.

It’s just a very funny letter, although, formally, the methods of social engineering are used. It’s a pity that the service is not called “I agree!”. This is your business idea # 9402.
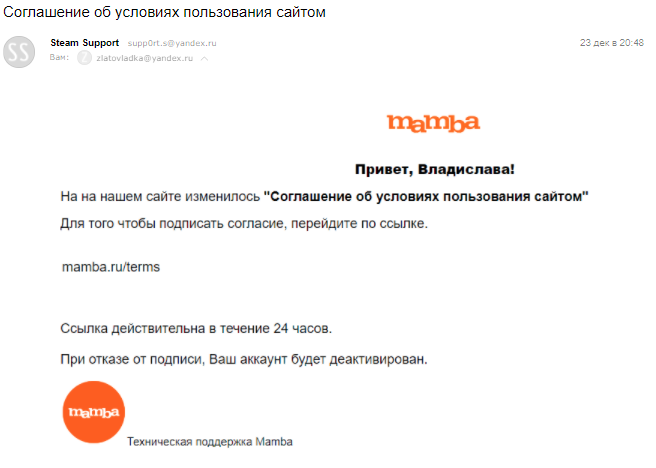
When you send phishing emails to many people at once and confuse the headers, and then ask to sign the consent, making up a letter with a picture. Please note: if the entire letter is one big link, most likely, my student writes to you. Feel free to delete.
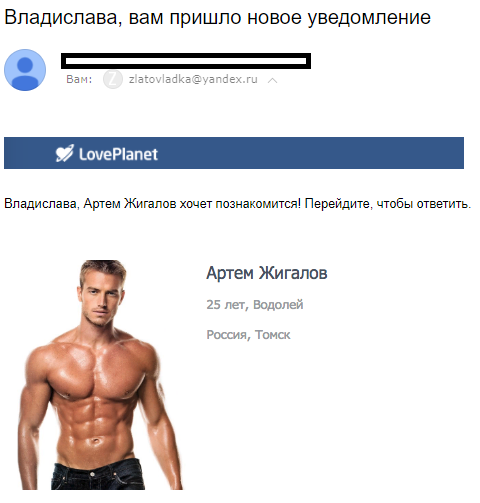
I have only one question: how did the authors select a photo for writing? Not a word in the report, and I would even read a separate post on this topic.

Here again the stolen Astek logo appeared, but the authors are different. Everything is just very good here, the main thing is to try it.
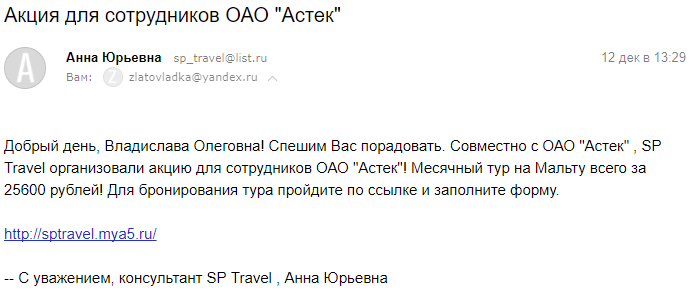
Vladislav wants to Malta, but here such an offer for a penny. Urgent, urgent to buy.
In addition, the site has:
The only letter that I first believed. Even knowing that this is a controlled test box, and that nothing from mail.ru can come here. At the last moment, he caught his hand, which led the mouse to the link. Please do not be like me.

Pretending to be the security service of your organization is a favorite trick of scammers. Formal style, document in the attachment. No need to go anywhere, download and watch.

It’s just a very funny letter, although, formally, the methods of social engineering are used. It’s a pity that the service is not called “I agree!”. This is your business idea # 9402.

When you send phishing emails to many people at once and confuse the headers, and then ask to sign the consent, making up a letter with a picture. Please note: if the entire letter is one big link, most likely, my student writes to you. Feel free to delete.

I have only one question: how did the authors select a photo for writing? Not a word in the report, and I would even read a separate post on this topic.

Here again the stolen Astek logo appeared, but the authors are different. Everything is just very good here, the main thing is to try it.

Vladislav wants to Malta, but here such an offer for a penny. Urgent, urgent to buy.
In addition, the site has:


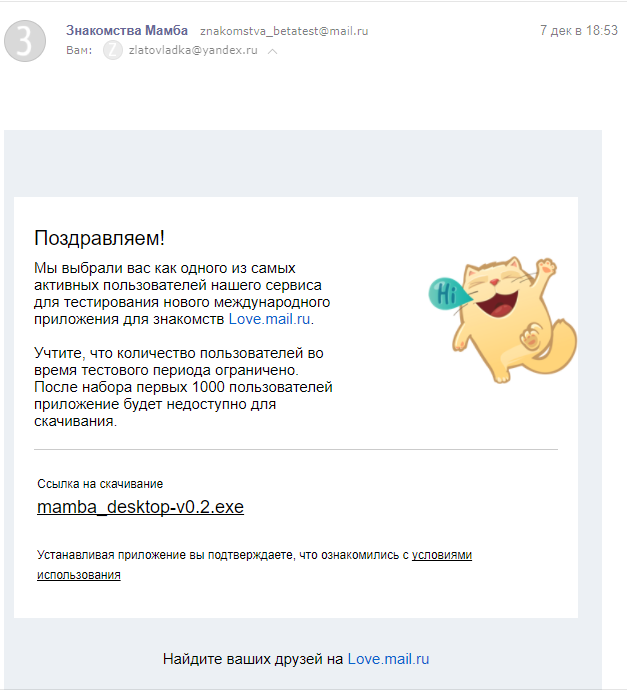
The only letter that I first believed. Even knowing that this is a controlled test box, and that nothing from mail.ru can come here. At the last moment, he caught his hand, which led the mouse to the link. Please do not be like me.
- What about spam filters? They should filter it, right?
In general, they probably should, but no.
Gmail did the best job - out of 38 emails, 13 ended up in the Spam folder. Google Mail filtered emails “similar to the ones that we have already blocked” and those that “contain things specific to phishing emails”.
In second place out of three Yandex - he filtered out the disappointing three letters. Unfortunately, Yandex does not indicate the reason for the block in the mail interface.
On mail.ru the only letter got to spam.
If you recall how successful letters looked, I would not call the work of all three services good. And even no percentage of filtered emails from gmail solves the problems with phishing and targeted attacks. Attackers can pretend to be anyone and, knowing very little about you, will gain access to your accounts.
conclusions
I believe that the laboratory work was a success. After the conversation, students understand (or pretend they understand) how to protect themselves from phishing and why you do not need to do this in real life - fraudsters face a real prison term under article 159.6 of the Criminal Code of the Russian Federation. I have warned students about this many times in lectures and workshops. Do not do that either.
How to defend yourself?
- Do not open links, do not download or run files from emails if you are not sure.
- Do not enter your personal data - logins, passwords, card numbers and any other information - on extraneous sites. If you have the slightest suspicion, close the page.
- Enable two-factor authentication for your accounts. This can be SMS, biometric authentication or confirmation on a mobile device.
- If the doubtful letter has arrived on corporate mail, tell the administrator or security service about it. It is likely that someone is conducting a targeted attack on the company.
- Be carefull. No one will accidentally send you a letter with the annual financial report or salaries of company employees.
Many thanks to the students who participated in this experiment. I'll meet you at the exam :)
And thanks to everyone else for reading to the end. Do not be fooled.
