2017 Summer Internship Results at Digital Security. Research department

In a previous article, colleagues from the audit department, in addition to their experience, talked a bit about the overall 2017 internship process at Digital Security. Today, the Research Department will share its impressions and present interviews with the interns of our department.
brief information
We are the research department of Digital Security. First of all, we are engaged in reverse engineering tasks, searching for vulnerabilities in binary applications and various devices, as well as writing exploits. We introduced ourselves in more detail in last year’s article .
Introduction
As already mentioned in an article by colleagues, this year the number of applications was many times greater than in the past. Of course, the majority of applicants wanted to engage in web-security, but the percentage of those wishing to immerse themselves in the "binary world" did not decrease from this.
By tradition, with the interns who decided to take an internship in our St. Petersburg office, we conducted a personal interview, and only after that made the final decision. During such meetings, not only the level of knowledge is determined, but also which topic is suitable for each candidate. In some cases, it was proposed not one, but several topics to choose from. The criteria for writing topics for the internship remained the same:
- At the end of the internship, the guys could publish the results of their research (github, gitlab and other repositories for open source projects) and / or speak to the public at the conference
- They are connected with real practical tasks.
Due to the specifics of the work of our department, unlike fellow auditors, we practice the approach of “one topic - one person” (though there are exceptions).
This allows the mentor to pay more attention to a particular intern, but limits the number of applicants that we can accept for an internship. Therefore, for those who did not succeed due to lack of experience, we advised to master the set of training materials, and then try again next year. In particular, this was the reason for the publication of our selection of materials on Habré, so that anyone can begin to study it in their free time.
We were pleasantly surprised that some of the guys themselves came to us for a local internship from other cities. We conducted interviews with them using video messengers (interesting statistics - most of those who wish completed the 3rd year of the university). Therefore, we tried to keep good memories (and pleasant gifts) of an internship in the Northern capital. And to last year’s lectures, our department added new ones:
- "SMT, Z3, SSE, DSE, ... In The Wild" (Georgy Nosenko)
- "PowerShell for Dummies: use in everyday life and on the battlefield" (Andrey Akimov)
Colleagues from the security analysis department also updated their lecture list and launched an interesting internal lab - a kind of wargame to enhance the skills of those involved.

By tradition, the interns themselves held several similar meetings for us, where they presented the results of their work. Such speeches can even be called a kind of final exam :) True, not everyone could do it, unfortunately, someone did not cope with the tasks for various reasons.
Participant reviews
Due to the nature of the tasks this year, we decided to abandon the remote internship, therefore, we present some comments only from those who completed the internship in our office.
Questions for the mini interview were as follows:
- Why did you decide to do your internship at DSec? What attracted you to the company?
- Did you like the internship? What was especially memorable? How did reality coincide with your expectations?
- Tell us about your task / tasks.
- Did the tasks you worked on during the internship seem interesting? Was there something you wanted to do but failed?
- Are you ready to return to the company for an internship or to work?
Alexander Trukhin (St. Petersburg State University)
Subject: "Improve the algorithms of the rootkit detection tool under GNU / Linux"
- I decided to try his luck when he saw the announcement on probation Linux.org.ru . Honestly, I knew almost nothing about the company at that time, the availability of free time and interesting topics played a decisive role.
- I liked the internship.
Most of all I remember the dining room with extremely unattractive prices near the office. In fact, I was surprised by the rather young age of the staff of the St. Petersburg branch. By the fact that they stay late at work, it can be determined that they like their job (or table football). It was very curious to listen to the lectures that were kindly prepared for us in the company. - I worked on a project of anti-rootkit under GNU / Linux , which in some initial form has already been implemented by my curator. Basically, I tried to bring to mind the functionality of the corresponding kernel module. It was necessary to put in order the process of transferring events from the kernel describing various important system resources (processes, sockets, etc.) to user mode for subsequent verification and detection of inconsistencies. I had to tinker with various core structures and its synchronization primitives, it was fun!

- Although it was not possible to advance particularly far (for example, I still wanted to implement some kind of self-defense mechanisms), working with the tasks to be solved was not at all boring, much was new. I hope the work on the project will continue.
- I’m always happy to work on something interesting.
Valeria Gubareva (Penza State University)
Topic: "Exploring the possibilities of boards Black Magic Probe and Bitsy"

- The person working here advised me to fill out a questionnaire. And the company itself is interesting to me because it deals with information security, for the study of which I spent the last five years of my life.
- Yes, I really liked it. Expectations were justified more than. I especially remember the moment when they gave me a bunch of different obscure boards, which I later, of course, successfully dealt with.
- My task was to deal with the recently appeared Black Magic Probe V2.1 board, to see the possibilities that open when working with it. And I had to try to break the firmware on other boards using Black Magic Probe. For clarity, the STM32F429I-disc1 board was selected, which has a touch screen, and for it I found firmware with the Reversi game. As a result, I was able to access the dynamic memory of the firmware, then using the IDA Pro disassembler I found the address, which is the starting address of the cells on the board. The values of these cells can be equal: 000 - an empty cell, 001 - a red chip, 002 - a blue chip. It occurred to me to equate the values of all cells to unity and thereby win the game from the first move. To do this, I wrote a small Python script. The result of my work was an article,
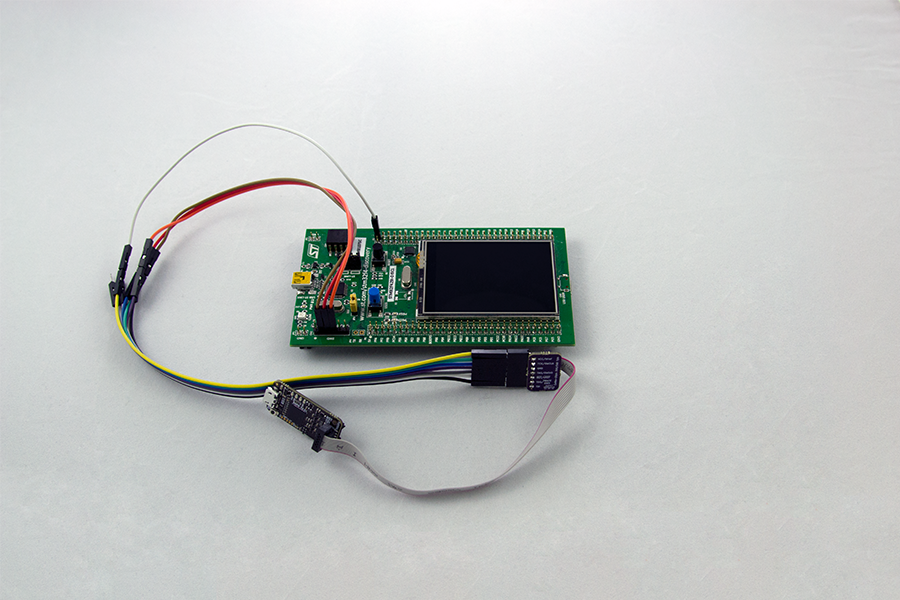
- Yes, the tasks were very interesting. Almost everything was new to me and there was very little information, but this did not become an obstacle.
- At work - of course, yes.
Nikita Trushin (TUSUR)
Subject: "A hanipot for logging interactive commands on a guest machine, using the means of a hypervisor"
- I like to study the internal structure of various kernels and software systems, while I am interested in programming. Therefore, the activity of DSec, as well as the blog on Habré, undoubtedly interested me.
- The internship left a positive impression. Especially the team, which turned out to be quite friendly, and, in general, a cozy atmosphere in the office.
- My task was to implement the patch for QEMU , according to the existing PoC, which was implemented as a gdb script and logged output from the guest terminal to the host machine, using the breaks on the write function in TTY. However, it pretty much reduced the speed of the guest machine. And I was required to do this inside QEMU itself, which would solve performance problems.
Accordingly, it was necessary to understand the internal structure of QEMU, find the most suitable place for patching and write a patch for x86-64, ARM and MIPS.

- Of course, the task was quite interesting. However, I would like to work in a team of several people.
- Of course, yes!
Conclusion
Summing up, we will say again “thank you” to everyone who took part in our summer internship in 2017. We all have gained great experience and hope that we could share it with the reader a little. Later, interesting articles will no longer be published from interns, but from our colleagues with the results of their research.
And of course, we are waiting for everyone for a new internship!
