Analysis of GSM network traffic in Wireshark
- Tutorial

The second article will be devoted to working with GSM traffic in Wireshark. I recommend that you read the first if you want to get more opportunities for practice.
For work, we need an osmocom-bb compatible phone capable of receiving a signal on GSM frequencies, for Russia it is 900 MHz and 1800 MHz and a computer with the installed Wireshark sniffer .
Cycle articles:
Launch a GSM network at home
Analyzing GSM network traffic in Wireshark
Add GPRS to your home GSM network
Practical examples of attacks inside a GSM network
GSMTAP
To correctly display GSM protocols in the latest versions of Wireshark, you do not need to install any additional dissectors.
The only thing that needs to be set for the LAPD protocol is Use GSM SAPI values.
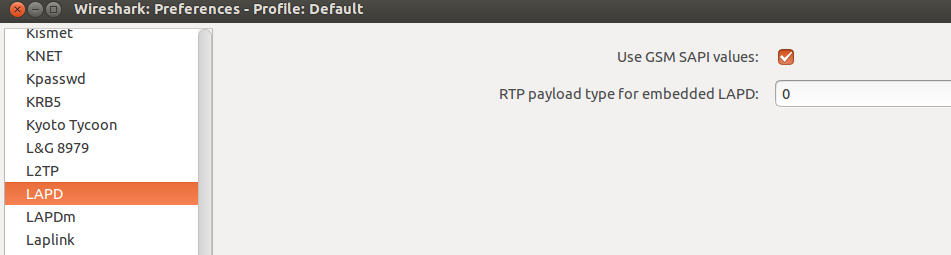
GSM protocols will be encapsulated in UDP packets with the GSMTAP header when transmitted via the Um interface or in TCP packets with OML, RSL headers when tracing the A-bis interface.

Run Wireshark to listen to the loopback interface and set filters to see only GSM Um traffic.
wireshark -k -f udp -Y gsmtap -i lo
Applications that can generate GSMTAP traffic for Wireshark usually operate as follows:
- Receive Um frame via radio interface
- Add GSMTAP header
- All this is sent to the specified IP address in UDP packets (in our case, loopback)
In addition to the GSMTAP filter, you can use other filters starting with gsm, for example gsm_sms, to search for SMS messages in traffic. But using the GSMTAP filter will allow you to view all GSM Um traffic, since all other headers are embedded in GSMTAP.

Traffic capture
To study GSM traffic, you must first record it somehow. Using the SDR device as a receiver, you can study the data transmitted on public CCCH channels, unless you know the Kc - session encryption key.
However, when using OsmocomBB, a phone with a SIM card and the mobile application, you know your Kc encryption key and you can view all your traffic in the clear, transmitted via the Um interface (radio interface) in Wireshark, and learn how real cellular networks work.
If you launched your GSM network on the basis of two OsmocomBB-compatible phones, as indicated in the previous article , you can transfer GSMTAP packets from OsmoBTS to Wireshark and thus study the network.
If you want to practice capturing your traffic using SDR transceivers, I recommend that you familiarize yourself with the gr-gsm utility package .
The budget option is to buy an RTL-SDR receiver .

I do not recommend buying cheap Chinese receivers, like this for 700 rubles.

Personally, he worked unstably for me and after a week completely stopped. In the RTL-SDR forums, people have had similar problems. So this is not an isolated case.
The fact is that both rtl2832u and r820t2 chips, usually used by RTL-SDR compatible devices, get very hot during operation, and cheap receivers do not provide any cooling. Secondly, there is no protection against statics and you can easily burn the receiver with careless handling. There are other problems.
Therefore, I recommend purchasing the official RTL-SDR receiver of the latest version in an aluminum case. It costs only 1,500 rubles, but in the kit you get 2 antennas, passive cooling, static protection, stable operation, improved filtering, and much more. As you know, "Avaricious pays twice."
Traffic analysis
I will not consider working with gr-gsm and RTL-SDR here, so we will go straight to Osmocom.
You can work with any commercial GSM network using the Open Source implementation of the GSM protocol stack from Osmocom. In other words, you can connect a Calypso-based phone to a computer, launch an application from the OsmocomBB package and make calls, send SMS and do everything that a regular 2G phone can do, plus gain access to any technical information about the current communication session.
The application we need for this is called mobile and is located here src / host / layer23 / src / mobile
I hope everyone has already compiled OsmocomBB on their computers. The process is described in my previous article and in this series .
Mobile is an application that runs on the computer side, but you also need to download layer1 firmware to your phone .
In the basic form, you need:
- Connect the phone to the computer via USB-TTL converter
- Check that the device / dev / ttyUSBx has appeared, load layer1 firmware into the phone via osmocon .
- Launch mobile and specify the interface for sending GSMTAP so that we can listen to this interface in Wireshark.
I already wrote about how to download firmware to the phone in a previous article. To start mobile, go to the directory with the application and run the following command
./mobile -i 127.0.0.1At the first start you can see a message about the absence of the configuration file. Create it empty in the directory indicated in the error message. (I have it /root/.osmocom/bb).
If you did everything correctly, you will see the log of mobile work in the console.
Now you can connect to the mobile terminal and control the phone like this
telnet localhost 4247You will be taken to an intuitive cisco-like VTY interface. Use the help command, TAB for auto completion or SHIFT +?
The show ms, show subscriber, show ba, and show cell commands will help you get information about the current connection. To switch to privileged mode, use enable and to write changes to the write file.
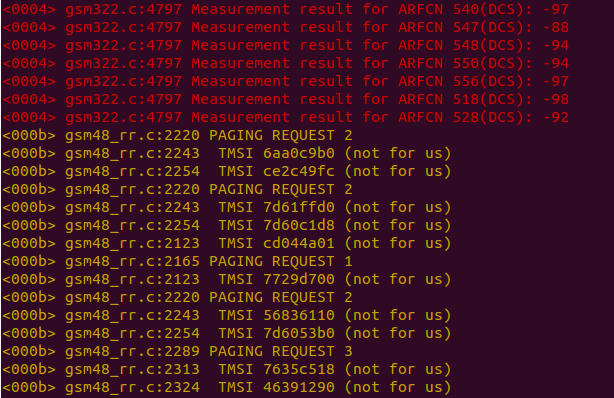
Wireshark has already been launched, and you can see the GSMTAP packets in the list. While the phone is in standby mode, and no one is sending us SMS or calling, the output will consist of open traffic from control channels.
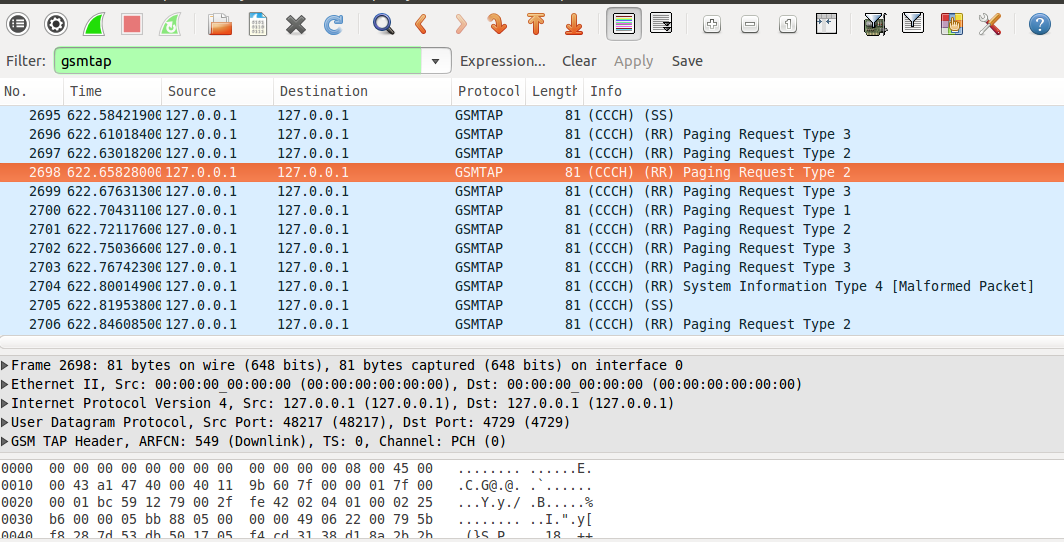
You can send SMS from your personal number to your mobile phone or send SMS to yourself through the VTY interface. Then, if you look at traffic in Wireshark by the gsm_sms filter, we will see.

There are other utilities that can capture various types of GSM traffic, you can find them here src / host / layer23 / src / misc
In particular, cell_log allows you to determine which base stations are around you and can send GSMTAP packets to Wireshark.
ccch_scan allows you to listen to messages on CCCH channels, including SMS, if you use a modified version from the osmocombb branch sylvain / burst_ind , which allows you to set the encryption key Kc.
However, in this case you will have to flash your USB-TTL converter to work at non-standard speeds.
As for capturing voice calls, here everything becomes more complicated, since the real operator can use Frequency HoppingThat “spreads” bursts at different frequencies and we need to follow the change in the phone frequency or record all traffic at all possible TCH frequencies of the cell, which in turn may not allow your receiver to do due to physical limitations.
If you are researching your own network, then you do not need Frequency Hopping, however Osmocom does not provide utilities for sniffing voice calls using osmocombb-compatible phones.
But the grgsm_decode utility of the gr-gsm package is able to decode speech when the receiver captures SDR traffic and grgsm_capture .
A-bis interface traffic analysis
A-bis is the messaging interface between BTS and BSC. We do not have access to studies of this kind of commercial network traffic. But you can learn such things using your own GSM network as an example.
To view RSL messages, you need to start listening to the loopback interface (note that TCP is used here, not UDP) and you will see messages like these:
For RSL, you can use the gsm_abis_rsl filter.
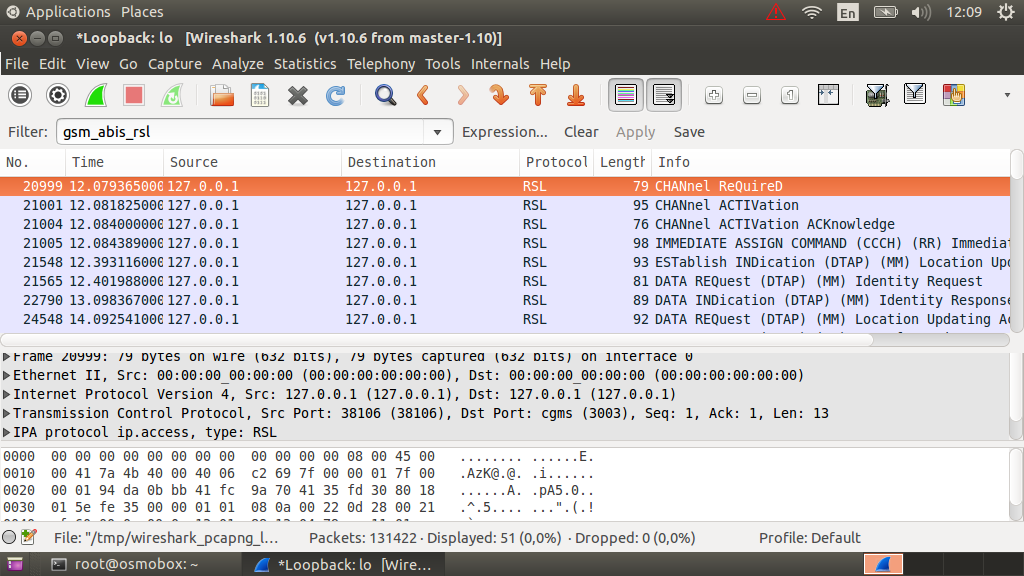
And for OML. You can use the gsm_abis_oml filter or filter by ports 3002 and 3003.

At the same time, SMS messages will be embedded in RSL packets, and not in GSMTAP, as is the case with transmission via the Um interface.
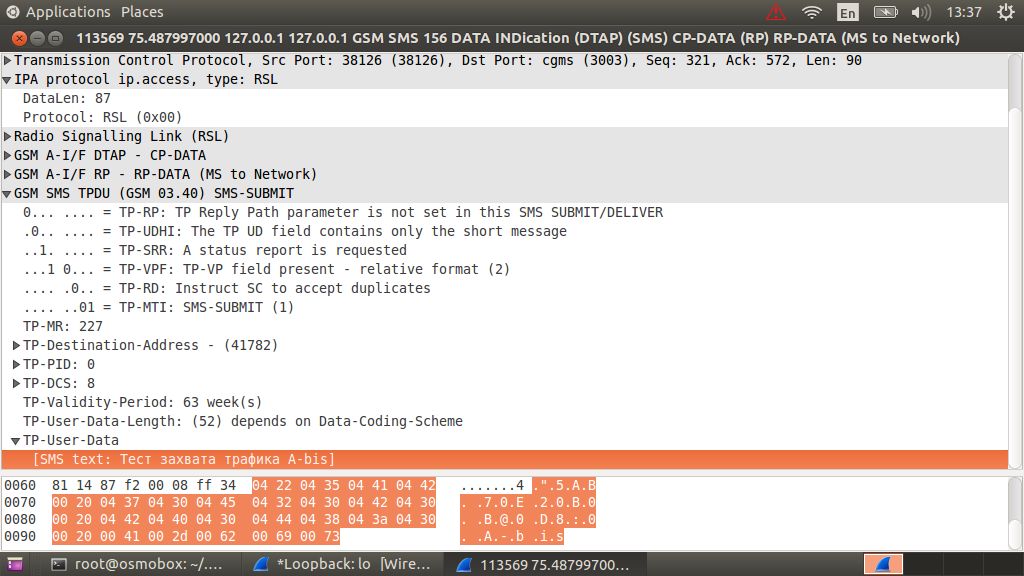
That's all. The next time I tell you about the addition to your home network support GPRS.
UPD: I recall that about practical examples of creating a base station and analyzing mobile traffic I will tell and show (at the stand) at the Pentestit Security Conference in my report: “Implementation of the GSM protocol stack”.
