Shielded VM Technology in Windows Server 2016
No need to delve into the technology of hypervisors and virtualization tools to understand what impressive opportunities virtual machines offer. In any data center, virtualization is a key element today. The tasks of deploying, managing, maintaining and automating IT infrastructure have been simplified with virtual machines, and VPS services have become widespread . But, despite its many advantages, virtualization also requires special approaches to ensure the security of virtual infrastructure and applications.
In the case of virtual machines (VMs), we take the operating system, applications and encapsulate them into several VM files, getting the opportunity to run several virtual machines (sometimes dozens) on the same system at the same time. Virtual machines simplify the processes of migration, backup, replication, but it also means that it has become easier to change or even copy the entire VM, your entire virtual server over the network or to a USB flash drive and take it with you.
This applies not only to commercial, but even corporate data centers. As an example, a domain controller deployed in your data center. Imagine if a domain controller leaves your organization. This is literally "the keys to the apartment where the money is." Since everything is stored centrally, you can take out dozens of VMs and run them somewhere else. And in the case of hosting with a third-party provider, the problem becomes even more acute.
Therefore, it is unnecessary to talk about the relevance of the problem of data protection inside virtual machines - hosted both in public clouds and in a private internal cloud. Moreover, it is typical for any virtualization platform, be it VMware, Hyper-V, Xen, KVM, etc. How and from whom should data be protected? Should admins with different roles have access to them - virtualization administrators, domain administrators, network administrators, disk storage administrators?
Some will say: if Windows Server is used as the host operating system, then the problem is solved by encryption. Just add a virtual Trusted Platform Module (TPM) to the VM, and you can encrypt its contents using BitLocker. The idea is good, but it does not work. Need stronger protection from the intrigues of admins. After all, the administrator can theoretically do anything with the system, that is, he is able to remove any protection of the VM, if you do not take special measures. For example, in the case of virtual TPM (vTPM), it can find the encryption key in memory and decrypt the VM.
We need real VM protection, which will allow us to run it only in a specific infrastructure environment and will completely protect against administrator actions, thereby eliminating the weak link in the information security system, because an administrator can potentially be forced to do anything by tricking, bribing or blackmailing. Moreover, this method is much cheaper and more affordable than hacker cyber attacks.
For this, Shielded VM technology in Windows Server 2016 serves (in Microsoft terminology - shielded virtual machines), restricting access to admins' VMs and protecting virtual machines from malicious code. VMs shielding technology Shielded the VM - one more reason to pay attention to Windows Server 2016. To whom it is necessary in the first place?
How is the Shielded VM protected ? First, information security technologies with hardware-based security features isolate VMs from host administrators. Second, the Host Guardian Service can identify legitimate Hyper-V hosts and protect the encryption keys of specific Shielded VMs. Thirdly, this is done by supporting the second-generation virtual Trusted Platform Module (vTPM) for the VM. Widely used encryption and authentication. So, in order.
Shielded VM - Essentially New Technology in Windows Server 2016. However, the good old encryption is also used in it. Although this is not a panacea, you cannot do without it. It allows the owner of the virtual machine to enable volume encryption inside the guest OS, for example, using the same BitLocker. Thus, the contents of the VM become inaccessible both for malicious code, if it appears on the Hyper-V host where the VM is located, and for the administrator of this host.
Shielded VM technology protects virtual machines from compromise and from admins of any level by encrypting the drive and the state of the VM, after which only the owner will have access to it. And, the most interesting thing is that encryption keys are never stored on Hyper-V hosts with shielded VMs, which can significantly increase the security of the solution as a whole.
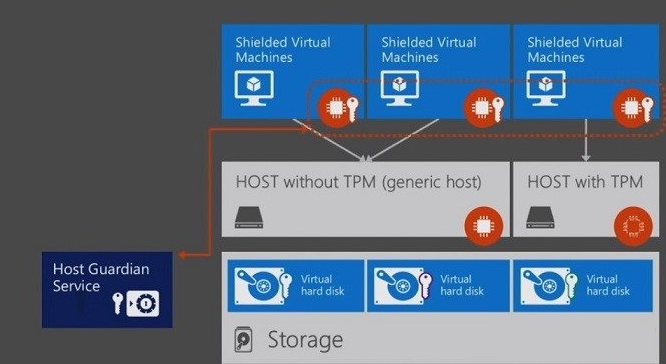
Another new Windows Server tool - Host Guardian Service (HGS) - checks if the Shielded VM can be running on this host, whether it is legitimate, whether it is a trusted host server. To do this, host certification tools and hardware boot metrics are used, as well as code verification functions (Code Integrity). All this allows you to check whether the host meets the required criteria, and whether it is possible to run VMs on it.
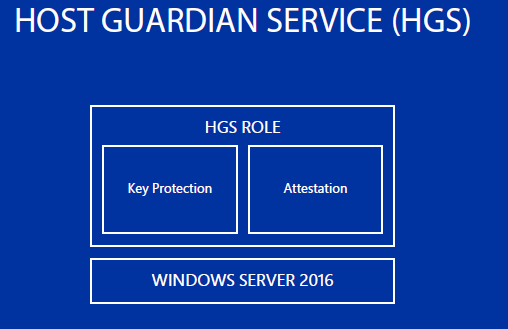
Host Guardian Service provides certification — Hyper-V host verification and key protection required to run the Shielded VM secure virtual machine. HGS starts as the Windows Server 2016 role and includes two separate services - certification and key protection.
Thus, a simplified process of shielding a VM in steps looks like this:
Host Guardian Host Protection is a new role in Windows Server 2016 that helps protect virtual machines and their data from unauthorized access, even by Hyper-V administrators. Since encryption keys are never stored on Hyper-V hosts with shielded VMs, this can significantly improve the security of the whole solution.
HGS works as follows:

Thus, the contents of the VM remain inaccessible both for malicious code on the Hyper-V host where the VM is located and for the administrator of this host. What types of attacks does Shielded VM technology protect against? They are listed below.
Note that Shielded VM does not protect against DDoS attacks - you need a separate service .
To boot the Shielded VM, the Unified Extensible Firmware Interface (UEFI) is used, and not the traditional BIOS, Secure Boot protection is provided, and VM disk encryption is enabled using BitLocker. VM data is protected by BitLocker even during Live Migration migration.

Shielded VM restricts access to administrators of different levels to the virtual machine. Only the VM administrator himself has such access.
Thus, the Host Guardian Service, a new role in Windows Server 2016, helps protect VMs from unauthorized access by Hyper-V host administrators. An administrator who does not have full rights to the Shielded VM can only start or stop such a virtual machine, but not change its settings or see the contents.
Shielded VM requires guest OS Windows Server 2012 or Windows 8 or higher. Shielded Shielded VMs can also be created on the Azure Management Pack Portal. Standard virtual machines can also be converted to secure. At the same time, as already noted, virtual disks are encrypted using BitLocker.
How can I certify a host, that is, make sure that a VM starts on a trusted system and on a domain member? There are two ways to do this: lightweight (Admin-Trusted) and enhanced (TPM-based).
The first is mainly intended for enterprise data centers or for especially trusted hosting providers and is based on Active Directory: to authorize a host to start a VM, it is included in the AD group. There is no hardware check - any servers are suitable (without a cryptoprocessor). This is a software way to verify trusted sites.
The second one, designed for the bulk of hosters, is more complex and requires equipment that supports TPM 2.0 and UEFI 2.3.1 crypto processor. Such equipment is still rare. So the choice of a specific protection method also depends on the capabilities of the hardware. The hardware certification process looks like this:
In the presence of TMP, hardware verification is applied - depending on the settings, binaries, hypervisors, etc. are checked. What if there is no corresponding hardware - TPM 2.0 and UEFI? You can use software. Host certification is done through Kerberos and the domain controller. VM data is also encrypted and protected from admins, but there is no VM protection at the system level, for example, from viruses or keyloggers. However, in most cases this level of security is considered adequate. It only requires the configuration of an AD group.
AD with the program method (Admin-Trusted) is used to store information - instead of TMP. With the hardware method, more checks are performed, for example, the health status of the VM and the node is checked, however, the software method makes it possible to use the existing IT infrastructure, so it will be the main one in the near future. To protect against failures, it is recommended that you deploy three HGS servers. You can use DNS to search for the HGS host. Note that HGS needs to be updated with the virtualization host.
Theoretically, these HGS servers can be virtual (working like a Shielded VM), but such a configuration is unreliable and will not start after a failure - at least one physical HGS server or at least a normal virtual (not Shielded VM) is recommended.
Managed by HGS from PowerShell or from the console, supports high availability mode (HA), scaling. Particular attention should be paid to HGS security - physical server protection is recommended. Microsoft also recommends that you enable BitLocker and SecureBoot for HGS, enable a firewall, and assign at least one static IP to each HGS. To enable SSL for REST API calls, a valid SSL certificate is required. It indicates the name of the HGS Service FQDN.
All this fits into the concept of Microsoft Virtualization Based Security (VBS), which involves the protection of hypervisors, networks, etc. To ensure security and isolation, VBS uses extensions to the virtualization platform. In Hyper-V, VBS is used to protect the host OS and guest VMs, servers, and clients.

Virtualization-based Security (VBS) uses hardware-based protection technology to create a security zone that is isolated from the kernel and applications. This provides protection against external attacks.
The VBS hardware platform has the following requirements: availability of UEFI 2.3.1c for secure and controlled downloads, TPM v2.0 for resource protection, virtualization extensions (Intel VT-X, AMD-V), address translation (Intel EPT, AMD RVI), memory protection by the hypervisor.
An important task is to ensure the verification of code integrity (Hypervisor Enforced Code Integrity). Currently, CI checks are performed from the kernel, and if the kernel is compromised, the code will be executed. In VBS, this is done safely. The hypervisor checks the access rights to each memory page, the execution rights of the code placed there, and the integrity of the data. Thus, potential attacks through memory operations are significantly limited and protection against incorrect drivers is implemented.
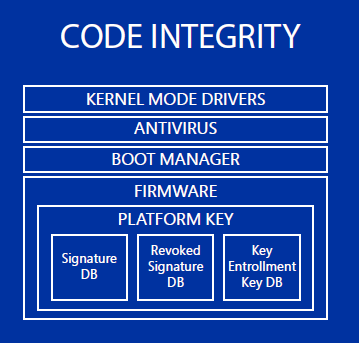
Code Integrity using Virtualization-Based Security ensures that only authorized binary code is launched on the system from the moment it starts.
VBS includes many architectural changes and individual tools. For example, Virtual Security Mode (VSM) severely restricts host and VM activity. Within the framework of VMS, a safe runtime environment for OS and guest VMs is implemented, their integrity is checked, and the security of the VM Worker Process used in Shielded VM is enhanced to protect information about the state of the VM. Virtual TMP (vTPM) for guest machines supports TPM services, such as disk encryption.
It is necessary not only to restrict the access rights of the host admin to the guest VMs. The administrator should not interfere with the operation of the host operating system - the hypervisor also needs to be protected from its actions. These mechanisms are key in the implementation of VSM, which provides for the protection of platforms, virtual machines and virtual equipment.
In essence, VMS is a set of methods for controlling RAM (its protection, distribution, access rights), distinguishing between operating systems, operations with the platform’s "secrets" without revealing them. VMS allows you to build new levels of security - Virtual Trust Levels (VTL). In Windows Server 2016, along with built-in security levels, you can create new VTLs with more stringent requirements. VTL provides memory isolation, protects access to physical memory. At the VTL0 level, unprotected VMs work, at the VTL1 level, shielded VMs work. You can create additional VTL levels - they are hierarchical. Admin cannot change VTL from host OS.
What is a VM running in VSM mode? This is a smaller kernel (proxy kernel, SMART or SKERNEL) that accesses the regular kernel through IUM (Isolated User Mode) using Intel VT-d. This mechanism protects virtual hardware resources from host administrator access.
An important point is protection against so-called DMA attacks, for example, “fake” drivers trying to compromise the VSM memory. The hypervisor uses the IOMMU system to control DMA memory.
The virtual machine must be protected in any state: off, running, or “moving”. To do this, you need a motherboard with support for UEFI, Secure Boot in VM, and support for TPM 2.0.
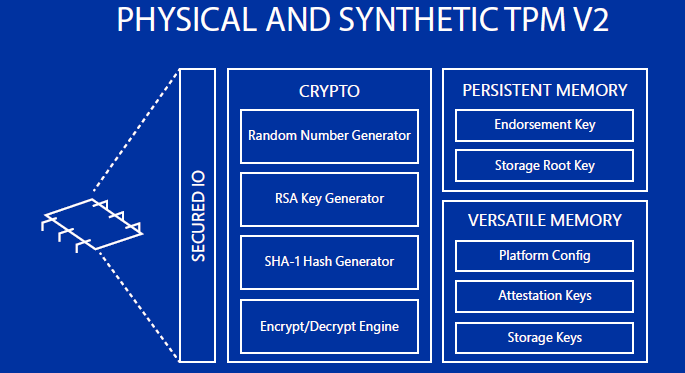
Trusted Platform Module (TPM) is an international standard crypto processor. Windows Server 2016 Hyper-V enables virtual TPM to protect VMs. As a result, VMs can use, for example, the BitLocker function. Virtual TPM does not require a physical TPM. vTPM is a kind of virtual TPM device for guest VMs that allows you to encrypt their disks.
To protect VMs in the “idle state”, vTPM is used. Virtual TPM does not require physical TPM and allows you to move VMs. This is a virtual TPM 2.0 device. In addition, the guest VM disk is encrypted using BitLocker. VM migration traffic is also encrypted.
A Virtual Machine Workerr Process (VMWP) is created for each VM. For Shielded VM, this is a secure process with debugger access denied and a number of functions limited. Administrative access to the Shielded VM is also limited. Access to it through VMconnect is closed (in basic mode), RemoteFX is denied, unprotected WMI, KVP calls, integration components are disabled, IMC registry insert, unprotected VDEV devices are removed. Such a VM can be controlled through built-in mechanisms. If the VM has “broken”, then to repair it, you will need to disable the Shielded VM mode or restore it from the backup.
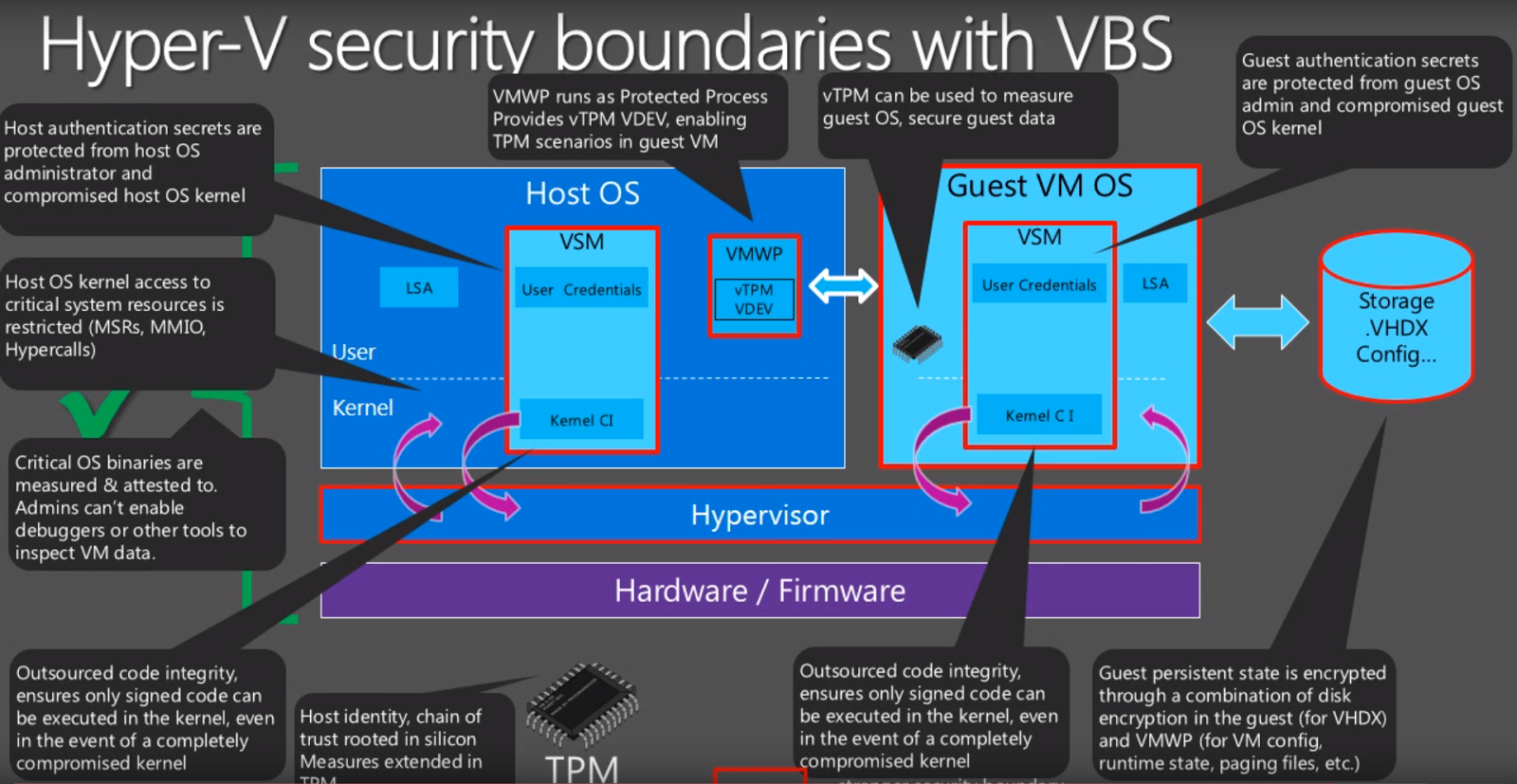
New Hyper-V Security Frontiers. Binaries in the OS are checked, the operating system restricts access to resources, authentication is widely used. The guest OS works with the host through a secure VMWP. Virtual TPM encrypts VM data, and encryption keys are stored on an external server. Hypervisor, VSM, guest OS implement separate security levels.
Of course, the shielding (protection) level of the VM can be adjusted. A weaker level of protection can be used when you trust the host admin, or the host system does not support all Shielded VM requirements. In this case, unproductive losses due to shielding are also reduced.
To make this work, changes have been made to the security modes of the hypervisor. By default, it does not trust the host system, there is no direct access to the hypervisor from it, its access to key system resources is limited. Everything you need is done from the guest VM OS. The host operating system mainly implements management functions. The state of the hypervisor in the hibernation file is encrypted.
Thus, the data and status of Shielded VM are protected from admins and malware, the host VSM is protected using vTPM, disk encryption is supported, and the Shielded VM can only be run on a trusted host. Shielded VM deployment and Shielded VM features are described in this document.
With a focus on hosting companies and large organizations, Windows Server 2016 also implements Guarded Fabric tools. With its help, it is possible to flexibly configure the network infrastructure and divide it into segments so that it is impossible to intercept data, intervene from one virtual machine to another, and perform other operations contrary to security policies. In the networks of cloud service providers, tens of thousands of virtual machines can function, in the infrastructure of which conflicts of IP addresses can occur, virtualization systems with malicious programs can appear. Guarded Fabric's job is to prevent this.
Shared hosting and clouds are no longer insecure - eliminated one of the main obstacles to the use of cloud services. Virtual servers can now be used for workloads that previously, for security reasons, could only be performed on hardware platforms.

Is hosting safe?
In the case of virtual machines (VMs), we take the operating system, applications and encapsulate them into several VM files, getting the opportunity to run several virtual machines (sometimes dozens) on the same system at the same time. Virtual machines simplify the processes of migration, backup, replication, but it also means that it has become easier to change or even copy the entire VM, your entire virtual server over the network or to a USB flash drive and take it with you.
This applies not only to commercial, but even corporate data centers. As an example, a domain controller deployed in your data center. Imagine if a domain controller leaves your organization. This is literally "the keys to the apartment where the money is." Since everything is stored centrally, you can take out dozens of VMs and run them somewhere else. And in the case of hosting with a third-party provider, the problem becomes even more acute.
Therefore, it is unnecessary to talk about the relevance of the problem of data protection inside virtual machines - hosted both in public clouds and in a private internal cloud. Moreover, it is typical for any virtualization platform, be it VMware, Hyper-V, Xen, KVM, etc. How and from whom should data be protected? Should admins with different roles have access to them - virtualization administrators, domain administrators, network administrators, disk storage administrators?
Encryption and TPM - not a panacea
Some will say: if Windows Server is used as the host operating system, then the problem is solved by encryption. Just add a virtual Trusted Platform Module (TPM) to the VM, and you can encrypt its contents using BitLocker. The idea is good, but it does not work. Need stronger protection from the intrigues of admins. After all, the administrator can theoretically do anything with the system, that is, he is able to remove any protection of the VM, if you do not take special measures. For example, in the case of virtual TPM (vTPM), it can find the encryption key in memory and decrypt the VM.
We need real VM protection, which will allow us to run it only in a specific infrastructure environment and will completely protect against administrator actions, thereby eliminating the weak link in the information security system, because an administrator can potentially be forced to do anything by tricking, bribing or blackmailing. Moreover, this method is much cheaper and more affordable than hacker cyber attacks.
For this, Shielded VM technology in Windows Server 2016 serves (in Microsoft terminology - shielded virtual machines), restricting access to admins' VMs and protecting virtual machines from malicious code. VMs shielding technology Shielded the VM - one more reason to pay attention to Windows Server 2016. To whom it is necessary in the first place?
| To | What for |
| Hosters | They can guarantee the protection of customer data from any actions of data center administrators. |
| For customers | They can transfer the load to the cloud or a commercial data center and at the same time not be afraid for the safety, confidentiality and integrity of their information assets, meet the requirements of regulators. |
| Enterprises | Get the ability to clearly separate Hyper-V administrators from critical workloads. |
How is this implemented?
How is the Shielded VM protected ? First, information security technologies with hardware-based security features isolate VMs from host administrators. Second, the Host Guardian Service can identify legitimate Hyper-V hosts and protect the encryption keys of specific Shielded VMs. Thirdly, this is done by supporting the second-generation virtual Trusted Platform Module (vTPM) for the VM. Widely used encryption and authentication. So, in order.
Shielded VM - Essentially New Technology in Windows Server 2016. However, the good old encryption is also used in it. Although this is not a panacea, you cannot do without it. It allows the owner of the virtual machine to enable volume encryption inside the guest OS, for example, using the same BitLocker. Thus, the contents of the VM become inaccessible both for malicious code, if it appears on the Hyper-V host where the VM is located, and for the administrator of this host.
Shielded VM technology protects virtual machines from compromise and from admins of any level by encrypting the drive and the state of the VM, after which only the owner will have access to it. And, the most interesting thing is that encryption keys are never stored on Hyper-V hosts with shielded VMs, which can significantly increase the security of the solution as a whole.
Another new Windows Server tool - Host Guardian Service (HGS) - checks if the Shielded VM can be running on this host, whether it is legitimate, whether it is a trusted host server. To do this, host certification tools and hardware boot metrics are used, as well as code verification functions (Code Integrity). All this allows you to check whether the host meets the required criteria, and whether it is possible to run VMs on it.

Host Guardian Service provides certification — Hyper-V host verification and key protection required to run the Shielded VM secure virtual machine. HGS starts as the Windows Server 2016 role and includes two separate services - certification and key protection.
Thus, a simplified process of shielding a VM in steps looks like this:
- Encryption of the VM state and its data, elimination of excessive administrative access to the virtual machine. Copying such a VM simply makes no sense.
- Encryption keys are stored on an external system. Just a virtual or hardware TPM is not suitable for this for two reasons: VMs are “prone to moving” from server to server, and the server administrator has access to TPM. In Server 2016, Host Guardian Service is used for such external storage.
- The VM at startup receives the key from a trusted host through HGS. Similarly, you can protect the guest OS Windows Server 2016, 2012 R2, 2008. The plans - Linux.

Host Guardian Host Protection is a new role in Windows Server 2016 that helps protect virtual machines and their data from unauthorized access, even by Hyper-V administrators. Since encryption keys are never stored on Hyper-V hosts with shielded VMs, this can significantly improve the security of the whole solution.
HGS works as follows:

- The Hyper-V host is requesting a key from HGS.
- HGS replies that it does not have Hyper-V host legitimacy data.
- Then the Hyper-V host sends its identity to the HGS.
- HGS sends the certificate of compliance to the Hyper-V host.
- The Hyper-V host sends the request again and sends the HGS certificate.
- In response, HGS sends the encryption key to the security zone of the Hyper-V host virtualization environment.
Thus, the contents of the VM remain inaccessible both for malicious code on the Hyper-V host where the VM is located and for the administrator of this host. What types of attacks does Shielded VM technology protect against? They are listed below.
| Attack vector | Shielded VM Protection |
| VHD Theft by System Administrator | Shielded VM provides VHD encryption, the key is stored outside the host. |
| Using Debug Mode in Hyper-V | The HGS host does not issue keys to debugged hosts. HGS allows you to control this. |
| Hyper-V host infection with malicious code. | All software on the host (in kernel mode, user mode and drivers) is monitored, code integrity (CI) is monitored. |
| Infection of the VM disk template. | Shielded VMs are deployed only from proven templates. |
| An attempt was made to migrate a Shielded VM to an untrusted host. | Trusted hosts are added to the HGS with unique identifiers for their TPMs. A new, not added host will not be recognized. |
Note that Shielded VM does not protect against DDoS attacks - you need a separate service .
To boot the Shielded VM, the Unified Extensible Firmware Interface (UEFI) is used, and not the traditional BIOS, Secure Boot protection is provided, and VM disk encryption is enabled using BitLocker. VM data is protected by BitLocker even during Live Migration migration.

Shielded VM restricts access to administrators of different levels to the virtual machine. Only the VM administrator himself has such access.
Thus, the Host Guardian Service, a new role in Windows Server 2016, helps protect VMs from unauthorized access by Hyper-V host administrators. An administrator who does not have full rights to the Shielded VM can only start or stop such a virtual machine, but not change its settings or see the contents.
Shielded VM requires guest OS Windows Server 2012 or Windows 8 or higher. Shielded Shielded VMs can also be created on the Azure Management Pack Portal. Standard virtual machines can also be converted to secure. At the same time, as already noted, virtual disks are encrypted using BitLocker.
Trust but check
How can I certify a host, that is, make sure that a VM starts on a trusted system and on a domain member? There are two ways to do this: lightweight (Admin-Trusted) and enhanced (TPM-based).
The first is mainly intended for enterprise data centers or for especially trusted hosting providers and is based on Active Directory: to authorize a host to start a VM, it is included in the AD group. There is no hardware check - any servers are suitable (without a cryptoprocessor). This is a software way to verify trusted sites.
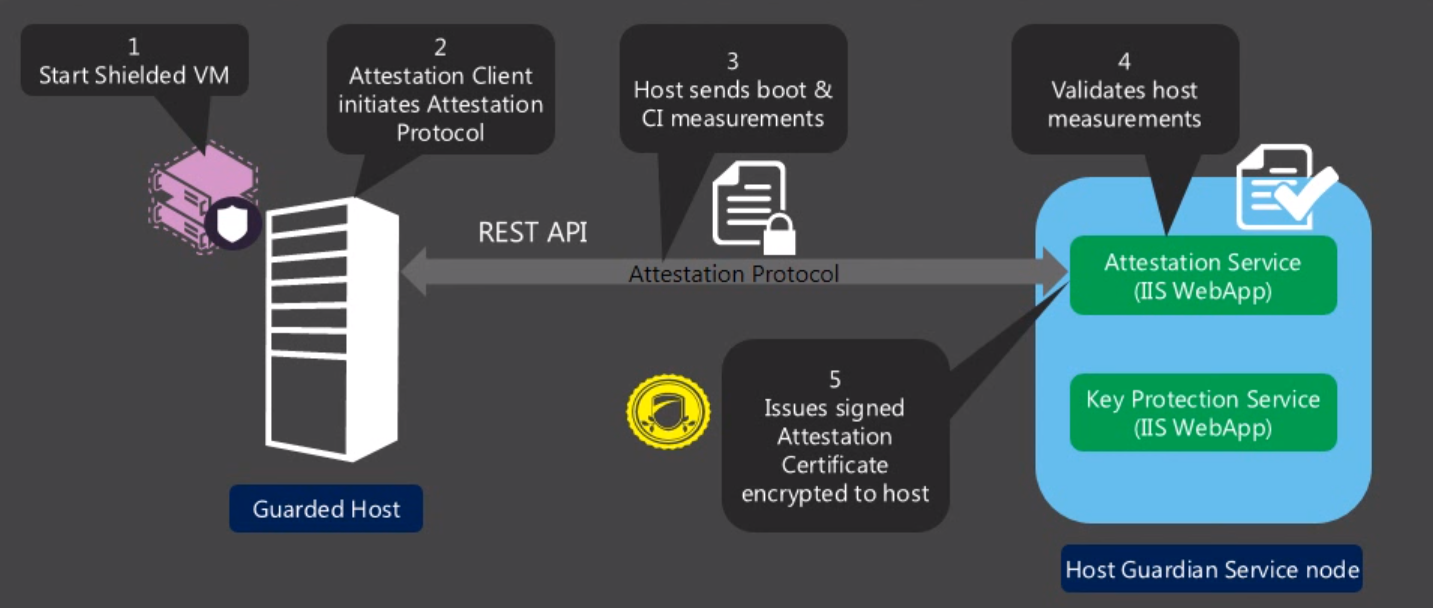
The second one, designed for the bulk of hosters, is more complex and requires equipment that supports TPM 2.0 and UEFI 2.3.1 crypto processor. Such equipment is still rare. So the choice of a specific protection method also depends on the capabilities of the hardware. The hardware certification process looks like this:

- Shielded VM starts.
- The client initiates the certification protocol.
- The host sends metrics and code integrity results.
- Host metrics are validated.
- The host is issued a signed certification certificate. This allows the VM to start.
In the presence of TMP, hardware verification is applied - depending on the settings, binaries, hypervisors, etc. are checked. What if there is no corresponding hardware - TPM 2.0 and UEFI? You can use software. Host certification is done through Kerberos and the domain controller. VM data is also encrypted and protected from admins, but there is no VM protection at the system level, for example, from viruses or keyloggers. However, in most cases this level of security is considered adequate. It only requires the configuration of an AD group.
AD with the program method (Admin-Trusted) is used to store information - instead of TMP. With the hardware method, more checks are performed, for example, the health status of the VM and the node is checked, however, the software method makes it possible to use the existing IT infrastructure, so it will be the main one in the near future. To protect against failures, it is recommended that you deploy three HGS servers. You can use DNS to search for the HGS host. Note that HGS needs to be updated with the virtualization host.
Theoretically, these HGS servers can be virtual (working like a Shielded VM), but such a configuration is unreliable and will not start after a failure - at least one physical HGS server or at least a normal virtual (not Shielded VM) is recommended.
Managed by HGS from PowerShell or from the console, supports high availability mode (HA), scaling. Particular attention should be paid to HGS security - physical server protection is recommended. Microsoft also recommends that you enable BitLocker and SecureBoot for HGS, enable a firewall, and assign at least one static IP to each HGS. To enable SSL for REST API calls, a valid SSL certificate is required. It indicates the name of the HGS Service FQDN.
Total protection
All this fits into the concept of Microsoft Virtualization Based Security (VBS), which involves the protection of hypervisors, networks, etc. To ensure security and isolation, VBS uses extensions to the virtualization platform. In Hyper-V, VBS is used to protect the host OS and guest VMs, servers, and clients.

Virtualization-based Security (VBS) uses hardware-based protection technology to create a security zone that is isolated from the kernel and applications. This provides protection against external attacks.
The VBS hardware platform has the following requirements: availability of UEFI 2.3.1c for secure and controlled downloads, TPM v2.0 for resource protection, virtualization extensions (Intel VT-X, AMD-V), address translation (Intel EPT, AMD RVI), memory protection by the hypervisor.
An important task is to ensure the verification of code integrity (Hypervisor Enforced Code Integrity). Currently, CI checks are performed from the kernel, and if the kernel is compromised, the code will be executed. In VBS, this is done safely. The hypervisor checks the access rights to each memory page, the execution rights of the code placed there, and the integrity of the data. Thus, potential attacks through memory operations are significantly limited and protection against incorrect drivers is implemented.

Code Integrity using Virtualization-Based Security ensures that only authorized binary code is launched on the system from the moment it starts.
VBS includes many architectural changes and individual tools. For example, Virtual Security Mode (VSM) severely restricts host and VM activity. Within the framework of VMS, a safe runtime environment for OS and guest VMs is implemented, their integrity is checked, and the security of the VM Worker Process used in Shielded VM is enhanced to protect information about the state of the VM. Virtual TMP (vTPM) for guest machines supports TPM services, such as disk encryption.
It is necessary not only to restrict the access rights of the host admin to the guest VMs. The administrator should not interfere with the operation of the host operating system - the hypervisor also needs to be protected from its actions. These mechanisms are key in the implementation of VSM, which provides for the protection of platforms, virtual machines and virtual equipment.
In essence, VMS is a set of methods for controlling RAM (its protection, distribution, access rights), distinguishing between operating systems, operations with the platform’s "secrets" without revealing them. VMS allows you to build new levels of security - Virtual Trust Levels (VTL). In Windows Server 2016, along with built-in security levels, you can create new VTLs with more stringent requirements. VTL provides memory isolation, protects access to physical memory. At the VTL0 level, unprotected VMs work, at the VTL1 level, shielded VMs work. You can create additional VTL levels - they are hierarchical. Admin cannot change VTL from host OS.
What is a VM running in VSM mode? This is a smaller kernel (proxy kernel, SMART or SKERNEL) that accesses the regular kernel through IUM (Isolated User Mode) using Intel VT-d. This mechanism protects virtual hardware resources from host administrator access.
An important point is protection against so-called DMA attacks, for example, “fake” drivers trying to compromise the VSM memory. The hypervisor uses the IOMMU system to control DMA memory.
The virtual machine must be protected in any state: off, running, or “moving”. To do this, you need a motherboard with support for UEFI, Secure Boot in VM, and support for TPM 2.0.

Trusted Platform Module (TPM) is an international standard crypto processor. Windows Server 2016 Hyper-V enables virtual TPM to protect VMs. As a result, VMs can use, for example, the BitLocker function. Virtual TPM does not require a physical TPM. vTPM is a kind of virtual TPM device for guest VMs that allows you to encrypt their disks.
To protect VMs in the “idle state”, vTPM is used. Virtual TPM does not require physical TPM and allows you to move VMs. This is a virtual TPM 2.0 device. In addition, the guest VM disk is encrypted using BitLocker. VM migration traffic is also encrypted.
A Virtual Machine Workerr Process (VMWP) is created for each VM. For Shielded VM, this is a secure process with debugger access denied and a number of functions limited. Administrative access to the Shielded VM is also limited. Access to it through VMconnect is closed (in basic mode), RemoteFX is denied, unprotected WMI, KVP calls, integration components are disabled, IMC registry insert, unprotected VDEV devices are removed. Such a VM can be controlled through built-in mechanisms. If the VM has “broken”, then to repair it, you will need to disable the Shielded VM mode or restore it from the backup.

New Hyper-V Security Frontiers. Binaries in the OS are checked, the operating system restricts access to resources, authentication is widely used. The guest OS works with the host through a secure VMWP. Virtual TPM encrypts VM data, and encryption keys are stored on an external server. Hypervisor, VSM, guest OS implement separate security levels.
Of course, the shielding (protection) level of the VM can be adjusted. A weaker level of protection can be used when you trust the host admin, or the host system does not support all Shielded VM requirements. In this case, unproductive losses due to shielding are also reduced.
- A basic level of. Uses TPM functions - vTPM works in VM, Secure Boot, disk encryption, VSC, etc. are supported.
- Protection of this level is complemented by encryption of the VM state and migration traffic.
- Full escaping, including limiting host admin operations.
To make this work, changes have been made to the security modes of the hypervisor. By default, it does not trust the host system, there is no direct access to the hypervisor from it, its access to key system resources is limited. Everything you need is done from the guest VM OS. The host operating system mainly implements management functions. The state of the hypervisor in the hibernation file is encrypted.
Thus, the data and status of Shielded VM are protected from admins and malware, the host VSM is protected using vTPM, disk encryption is supported, and the Shielded VM can only be run on a trusted host. Shielded VM deployment and Shielded VM features are described in this document.
With a focus on hosting companies and large organizations, Windows Server 2016 also implements Guarded Fabric tools. With its help, it is possible to flexibly configure the network infrastructure and divide it into segments so that it is impossible to intercept data, intervene from one virtual machine to another, and perform other operations contrary to security policies. In the networks of cloud service providers, tens of thousands of virtual machines can function, in the infrastructure of which conflicts of IP addresses can occur, virtualization systems with malicious programs can appear. Guarded Fabric's job is to prevent this.
Shared hosting and clouds are no longer insecure - eliminated one of the main obstacles to the use of cloud services. Virtual servers can now be used for workloads that previously, for security reasons, could only be performed on hardware platforms.
