Finding Use Cases for SIEM
Glossary:
SIEM (Security Information & Event Management) - a hardware-software complex for collecting information about events (logs), their correlation and analysis. Wiki edits .
Use Case (in relation to SIEM) is an established term that denotes a specific set of rules / scripts and / or visualization mechanisms. For example, to detect port scans, reconcile IP addresses with an external reputation database, etc. Use cases can be written yourself, taken ready-made from the manufacturer’s website, or ordered from contractors.
The purpose of this article is to systematize the information found on the Use Case catalogs and additional resources, as well as an active dialogue in the comments. Share your experience, please, and I will update the post with the information received.
Content:
1. SIEM rating in 2016
2. “Native” Use Case stores on the websites of SIEM manufacturers
3. Recommendations for self-writing Use Case
4. Custom development: map of integrators
5. Third-party Use Case catalogs: SOC Prime UCL, vendor forums (the list is being updated)
6. Links to blogs and additional information security resources related to SIEM
If you are still at the stage of choosing SIEM, then here is their current rating from two independent sources. Plus, it will become clear why the article itself devotes a different amount of attention to each of the solutions.
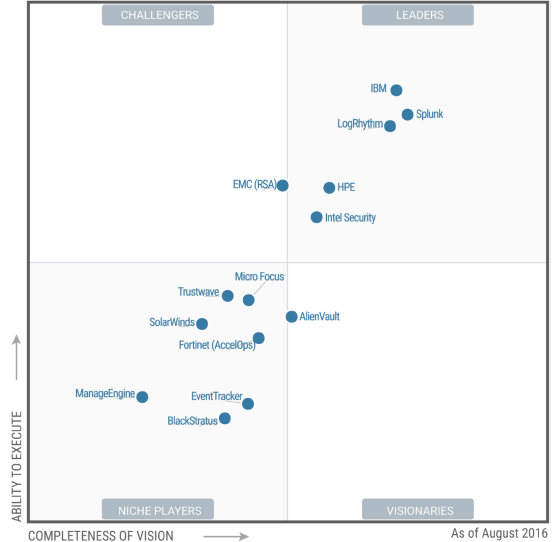
Source: Gartner Magic Quadrant 2016
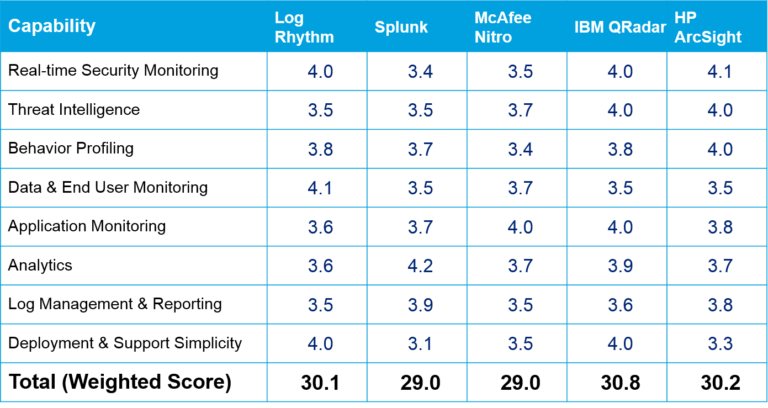
Source: 2016 InfoSec Nirvana
If the task of import substitution is relevant, then there are at least 3 SIEM with Russian roots:
The rating was not included, but it is worth mentioning:
→ OSSIM (Open Source Security Information Management) habr1 , habr2
→ OpenSOC , which grew up in Apache Metron
2. “Native” Use Case stores on SIEM manufacturers' websites
Information as of the date of publication (end of November 2016). Now only 4 manufacturers have organized their own sites for the publication of Use Case'ov. Also, most manufacturers have an internal forum for exchanging information and finding solutions to emerging problems.
HPE ArcSight Marketplace
There are paid and free. If you do not apply additional filtering, then the site has a total of 170 Use Case'ov.
IBM Security App Exchange
Free Download. A total of 73 Use Cases are available, developed both by IBM and partners.
LogRhythm
So far, only 19 Use Case'ov. Rather, their marketing descriptions.
Splunk
The Security, Fraud and Compliance subsection contains 487 applications. But if you filter out only applications (and not add-ons, although they are important too) and specify the product version 6.0 and higher, then the total number decreases to 236 Use Case'ov.
The development methodology for Use Case is well described in the blog (Anton Chuvakin) and the article .
In short, it is necessary to approach the task as a full-fledged mini-project:
If your own strengths / time / competency is not enough, then you can turn to professionals - in 99% of cases it will be an integrator company that, on its own, or with the involvement of Professional Services from a SIEM vendor, will perform custom development and support for Use Case's.
Links to the “partner locator” sections of popular SIEMs:
→ findapartner.hpe.com
→ www-356.ibm.com/partnerworld/wps/bplocator/search.jsp
→ logrhythm.com/partners/resellers-and-mssps/find-a -partner (the list of partners is non-public, they suggest filling out the request form, in response they will send the partner data)
→ www.rsa.com/en-us/partners/find
→ www.splunk.com/en_us/partners/find-a-partner.html
Based on the information about partners available at these links, I have compiled a general table using Ukraine as an example (and the SIEMs common with us). As you can see, some integrators are not “monogamous”.
Information is not 100% relevant, as partner status is updated quite inertly and situationally: someone can be given in advance, someone has already achieved significant results, but status will be updated only six months later, and someone has already lost engineers along with a reputation, but still with a full set of regalia is listed. Plus, for large vendors (HPE, IBM) it is quite difficult to understand which partner specializes in which of a great many products. Therefore, I additionally recommend (anonymously) call the distributors of your SIEM and ask which of the partners they recommend.
The lack of an official partner status, as a rule, does not interfere with the successful sale of products - only earnings will be less. Obtaining status during occasional work with the product can be irrational (for example, if it requires mandatory expensive certification of engineers and / or a certain annual level of sales).
At the moment, I have found only a few alternative resources where you can try to download Use Case to fit your needs:
Total: 22 applications. According to information from the site, the launch of the site was 08/31/2016, so there is hope for further growth. Another 22 Use Case are under development (Under R&D status).
Use cases are bought for points that you can pay with money, or earn with your own hard work (reviews on purchased applications, post your Use Case, suggest an idea through the feedback form).
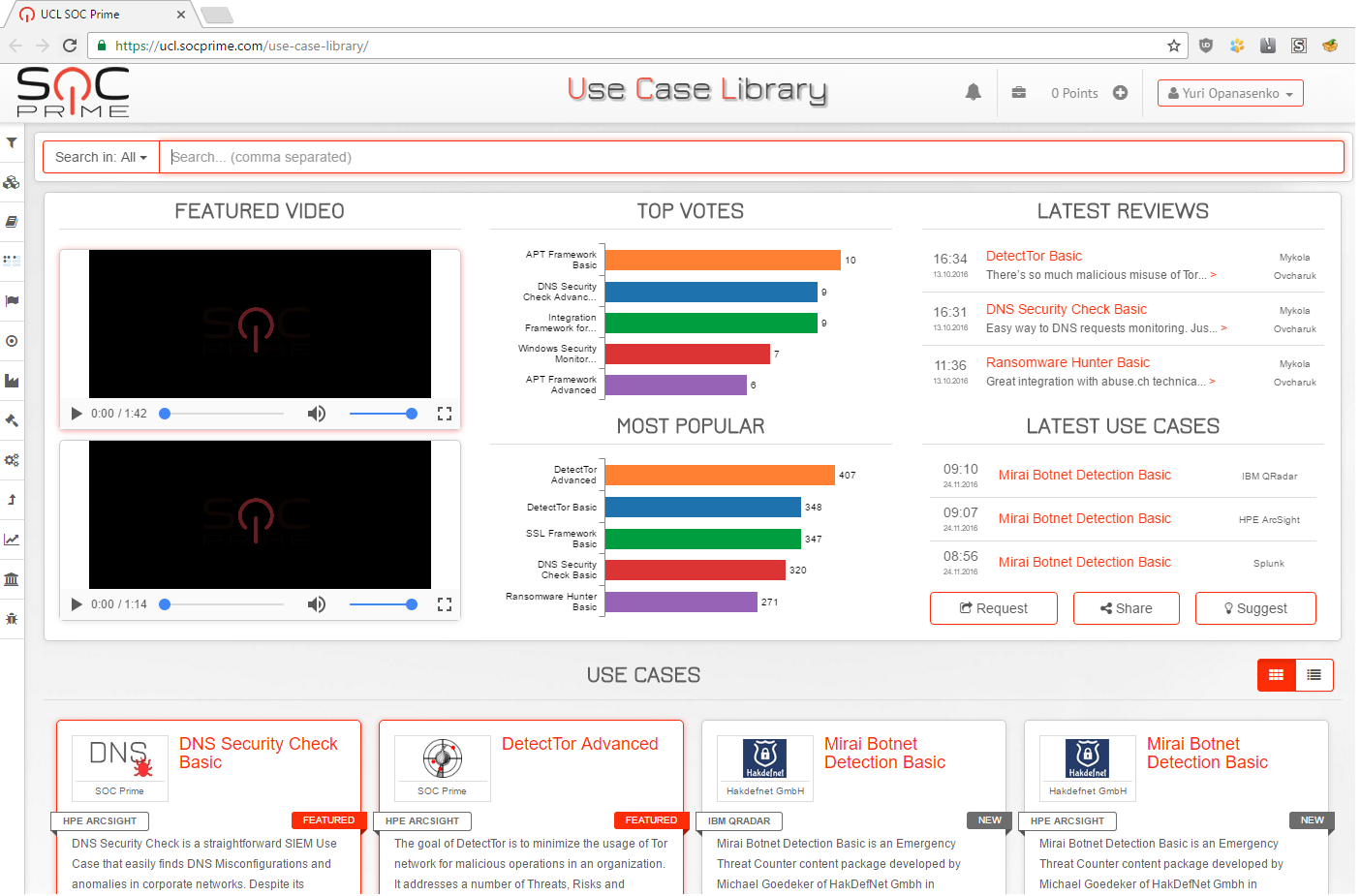
Continuation of the first screenshot, but with an alternative scheme for displaying the list:
I could not immediately register there, as it turned out later - I ignored the public gmail email address, forcing me to register only on the corporate one. “If attackers can easily register through a free emaill and learn the security algorithm, then they will quickly learn to circumvent such protection.”
About the author :
My experience is 4 years in the security integrator, 2 years in the security department of the distributor, and the last 3 years on the side of the FMCG customer on the position of IT Business Analyst. Out of habit, I still keep track of security news, and with the task of using Use Case, I helped my friend - in the wake of it and decided to prepare an article.
SIEM (Security Information & Event Management) - a hardware-software complex for collecting information about events (logs), their correlation and analysis. Wiki edits .
Use Case (in relation to SIEM) is an established term that denotes a specific set of rules / scripts and / or visualization mechanisms. For example, to detect port scans, reconcile IP addresses with an external reputation database, etc. Use cases can be written yourself, taken ready-made from the manufacturer’s website, or ordered from contractors.

The purpose of this article is to systematize the information found on the Use Case catalogs and additional resources, as well as an active dialogue in the comments. Share your experience, please, and I will update the post with the information received.
Content:
1. SIEM rating in 2016
2. “Native” Use Case stores on the websites of SIEM manufacturers
3. Recommendations for self-writing Use Case
4. Custom development: map of integrators
5. Third-party Use Case catalogs: SOC Prime UCL, vendor forums (the list is being updated)
6. Links to blogs and additional information security resources related to SIEM
1. SIEM rating in 2016
If you are still at the stage of choosing SIEM, then here is their current rating from two independent sources. Plus, it will become clear why the article itself devotes a different amount of attention to each of the solutions.

Source: Gartner Magic Quadrant 2016

Source: 2016 InfoSec Nirvana
If the task of import substitution is relevant, then there are at least 3 SIEM with Russian roots:
Additional Information Provided by PositiveTechnologies
- link to the MP SIEM LE page - www.ptsecurity.com/en-us/promo/siem-le
- separate link to the current booklet www.ptsecurity.com/upload/ptru/products/documents/mpsiem/PT-MaxPatrol-SIEM -Product-Booklet-rus.pdf
- link to a detailed webinar on MP SIEM my.webinar.ru/record/873458
“We believe that of all the“ Russian ”SIEMs, the PT product is perhaps the only one supported by extensive information security expertise (pentests and attack scenarios ) and also offers free coverage of current customer sources.
Back in MaxPatrol SIEM, a transfer mechanism to the examination product of the Positive Research research center based on the Positive Technologies Knowledge Base (PTKB) was implemented. This is a high-level, constantly updated data set, formed on the basis of 15 years of experience of the research center, including the experience of penetration tests and security audits. ”
- separate link to the current booklet www.ptsecurity.com/upload/ptru/products/documents/mpsiem/PT-MaxPatrol-SIEM -Product-Booklet-rus.pdf
- link to a detailed webinar on MP SIEM my.webinar.ru/record/873458
“We believe that of all the“ Russian ”SIEMs, the PT product is perhaps the only one supported by extensive information security expertise (pentests and attack scenarios ) and also offers free coverage of current customer sources.
Back in MaxPatrol SIEM, a transfer mechanism to the examination product of the Positive Research research center based on the Positive Technologies Knowledge Base (PTKB) was implemented. This is a high-level, constantly updated data set, formed on the basis of 15 years of experience of the research center, including the experience of penetration tests and security audits. ”
The rating was not included, but it is worth mentioning:
→ OSSIM (Open Source Security Information Management) habr1 , habr2
→ OpenSOC , which grew up in Apache Metron
2. “Native” Use Case stores on SIEM manufacturers' websites
Information as of the date of publication (end of November 2016). Now only 4 manufacturers have organized their own sites for the publication of Use Case'ov. Also, most manufacturers have an internal forum for exchanging information and finding solutions to emerging problems.
HPE ArcSight Marketplace
There are paid and free. If you do not apply additional filtering, then the site has a total of 170 Use Case'ov.
IBM Security App Exchange
Free Download. A total of 73 Use Cases are available, developed both by IBM and partners.
LogRhythm
So far, only 19 Use Case'ov. Rather, their marketing descriptions.
Splunk
The Security, Fraud and Compliance subsection contains 487 applications. But if you filter out only applications (and not add-ons, although they are important too) and specify the product version 6.0 and higher, then the total number decreases to 236 Use Case'ov.
3. Recommendations for self-writing Use Case'ov
The development methodology for Use Case is well described in the blog (Anton Chuvakin) and the article .
In short, it is necessary to approach the task as a full-fledged mini-project:
- Clearly determine the problem to be solved and its source (this may be a business requirement, the need to comply with industry standards and regulations for data protection, etc.).
- Define the boundaries of the project (i.e., a specific section of the protected IT infrastructure).
- After that, identify possible “sources of events”, the processing of which will allow you to implement a working Use Case. It can be logs from devices, event logs, configuration settings.
- Check that the source correctly supplies all the necessary data - otherwise the correctly developed Use Case will not be able to work effectively (will not work, or vice versa will produce False Positive - false positives).
- Finally, start developing the Use Case.
- Install and test by adjusting logic and thresholds.
- When the Use Case has already been tested and installed in the productive, it is important to correctly configure the reaction to its operation: is it enough to simply output the data to the dashboard, or need an SMS / email notification, or even automatically start changing the configuration of the slave devices (for example, IBM declares that it SIEM will be able to change the IPS / Firewall rules).
- Hooray, everything works! But work on this has not been completed - maintenance of the developed mini-product is necessary: periodically check whether data is being received for processing, whether its format has changed, modify the Use Case itself for the changing topology of IT infrastructure and the needs of the Business.
4. Custom Development: Integrator Card
If your own strengths / time / competency is not enough, then you can turn to professionals - in 99% of cases it will be an integrator company that, on its own, or with the involvement of Professional Services from a SIEM vendor, will perform custom development and support for Use Case's.
Links to the “partner locator” sections of popular SIEMs:
→ findapartner.hpe.com
→ www-356.ibm.com/partnerworld/wps/bplocator/search.jsp
→ logrhythm.com/partners/resellers-and-mssps/find-a -partner (the list of partners is non-public, they suggest filling out the request form, in response they will send the partner data)
→ www.rsa.com/en-us/partners/find
→ www.splunk.com/en_us/partners/find-a-partner.html
Based on the information about partners available at these links, I have compiled a general table using Ukraine as an example (and the SIEMs common with us). As you can see, some integrators are not “monogamous”.
SIEM Integrator | QRadar | Arcight | Splunk |
| Active Audit Agency | - | - | Reseller |
| Betta security | - | - | Reseller |
| BMS Consulting | Business partner | Gold partner | - |
| Cbs group | Business partner | - | - |
| Center of Systrem Integration | - | Business partner | - |
| COMPAREX Ukraine | Business partner | - | - |
| Comsec | - | - | Reseller |
| CS Integra | - | Business partner | - |
| IBPM | Business partner | - | - |
| ICSystems | - | Business partner | - |
| Integrity Vision | Business partner | - | - |
| ISSP | - | Silver partner. Engineer certified | - |
| IT for Business (Supportio) | - | Business partner | - |
| IT-Integrator (Incom) | Business partner | - | - |
| Lantec | - | Platinum partner | - |
| SI BIS | Business partner | - | - |
| SI Center | - | Business partner | - |
| Spezvuzavtomatika | - | Business partner | - |
| Spro | Business partner | - | - |
| SVIT IT | Business partner | Gold partner. Engineer certified | - |
| System integration service | Business partner | - | - |
Information is not 100% relevant, as partner status is updated quite inertly and situationally: someone can be given in advance, someone has already achieved significant results, but status will be updated only six months later, and someone has already lost engineers along with a reputation, but still with a full set of regalia is listed. Plus, for large vendors (HPE, IBM) it is quite difficult to understand which partner specializes in which of a great many products. Therefore, I additionally recommend (anonymously) call the distributors of your SIEM and ask which of the partners they recommend.
The lack of an official partner status, as a rule, does not interfere with the successful sale of products - only earnings will be less. Obtaining status during occasional work with the product can be irrational (for example, if it requires mandatory expensive certification of engineers and / or a certain annual level of sales).
5. Third-party directories Use Case'ov
At the moment, I have found only a few alternative resources where you can try to download Use Case to fit your needs:
Official manufacturers forums
Often, users do not have enough time / perseverance or motivation to fully complete the case for publication in the official catalog. And posting “as is” on the forum is not difficult.
→ www.protect724.hpe.com
→ www.splunk.com/en_us/community.html
IBM Support communities:
Marketplace support myibm.ibm.com/support/forum
Get answers to your products and services questions using a collaborative forum moderated by IBM
developerWorks experts www.ibm.com/developerworks/community
Learn from and share with the experts in the developerWorks community
dW Answers developer.ibm.com/answers
Post questions and look up answers in the developerWorks community
RSA Link community.rsa.com/community/rsa-customer-support
Intel McAfee community.mcafee.com
→ www.protect724.hpe.com
→ www.splunk.com/en_us/community.html
IBM Support communities:
Marketplace support myibm.ibm.com/support/forum
Get answers to your products and services questions using a collaborative forum moderated by IBM
developerWorks experts www.ibm.com/developerworks/community
Learn from and share with the experts in the developerWorks community
dW Answers developer.ibm.com/answers
Post questions and look up answers in the developerWorks community
RSA Link community.rsa.com/community/rsa-customer-support
Intel McAfee community.mcafee.com
LinkedIn Security Groups
In principle, this is similar to the previous paragraph. But on average, content can be better designed - after all, the publication is on the HR resource in the field of view of possible employers and has a clear link to the profile (it’s also a resume).
“SIEM Use-Cases” www.linkedin.com/groups/6704216
“SIEM Use-Cases” www.linkedin.com/groups/6704216
Commercial site Use Case Library vendor SOC Prime
As of now, three SIEMs are supported: HPE ArcSight, IBM QRadar, Splunk. The library itself contains Use Case'y developed by "SOC Prime", as well as posted there by other users. From the unexpected - all content is duplicated in English and Russian! (switches in profile settings).
ucl.socprime.com
ucl.socprime.com
Total: 22 applications. According to information from the site, the launch of the site was 08/31/2016, so there is hope for further growth. Another 22 Use Case are under development (Under R&D status).
Use cases are bought for points that you can pay with money, or earn with your own hard work (reviews on purchased applications, post your Use Case, suggest an idea through the feedback form).
Continuation of the first screenshot, but with an alternative scheme for displaying the list:
I could not immediately register there, as it turned out later - I ignored the public gmail email address, forcing me to register only on the corporate one. “If attackers can easily register through a free emaill and learn the security algorithm, then they will quickly learn to circumvent such protection.”
SIEM-Related Blogs and Additional Information Security Resources
Anton Chuvakin (more about SIEM) blogs.gartner.com/anton-chuvakin
Augusto Barros (more about SOC) blogs.gartner.com/augusto-barros
Deepak Kumar www.linkedin.com/today/author/0_0r-9MaWjS4pt2cnm0EWqkR
Rafael Marty raffy .ch / blog
Ofer Shezaf xiom.com
resources.infosecinstitute.com
infosecnirvana.com/category/siem
www.cybrary.it
securosis.com/search/results/e9fc8ff294a13141edb0affefd542297
securityintelligence.com/?s=siem
www.techtarget.com/search / query? q = siem
solutionsreview.com/security-information-event-management
LinkedIn Group “SIEM Use-Cases” www.linkedin.com/groups/6704216
Habra users:
AlexGryn Alexander Grinyuk IBM technical presale for security in the CIS region (not including Russia).
alekbr Alexander Bredikhin Technical Director of SOC Prime
SearchInform Ivan Mershkov, Technical Director of SearchInform
PositiveTechnologies - a representative of the same manufacturer, actively maintain a corporate blog on Habré.
Augusto Barros (more about SOC) blogs.gartner.com/augusto-barros
Deepak Kumar www.linkedin.com/today/author/0_0r-9MaWjS4pt2cnm0EWqkR
Rafael Marty raffy .ch / blog
Ofer Shezaf xiom.com
resources.infosecinstitute.com
infosecnirvana.com/category/siem
www.cybrary.it
securosis.com/search/results/e9fc8ff294a13141edb0affefd542297
securityintelligence.com/?s=siem
www.techtarget.com/search / query? q = siem
solutionsreview.com/security-information-event-management
LinkedIn Group “SIEM Use-Cases” www.linkedin.com/groups/6704216
Habra users:
AlexGryn Alexander Grinyuk IBM technical presale for security in the CIS region (not including Russia).
alekbr Alexander Bredikhin Technical Director of SOC Prime
SearchInform Ivan Mershkov, Technical Director of SearchInform
PositiveTechnologies - a representative of the same manufacturer, actively maintain a corporate blog on Habré.
About the author :
My experience is 4 years in the security integrator, 2 years in the security department of the distributor, and the last 3 years on the side of the FMCG customer on the position of IT Business Analyst. Out of habit, I still keep track of security news, and with the task of using Use Case, I helped my friend - in the wake of it and decided to prepare an article.
Only registered users can participate in the survey. Please come in.
SIEM used by me (if you have several, specify the main one)
- 13.4% IBM 7
- 15.3% Splunk 8
- 1.9% LogRhythm 1
- 26.9% HPE 14
- 3.8% EMC (RSA) 2
- 3.8% Intel Security 2
- 3.8% Micro Focus 2
- 9.6% AlienVault 5
- 0% Trustwave 0
- 0% SolarWinds 0
- 0% Fortinet 0
- 0% EventTracker 0
- 0% ManageEngine 0
- 1.9% BlackStratus 1
- 17.3% PositiveTechnologies 9
- 1.9% SearchInform 1
