Who sells your accounts?

In early 2016, an attacker acting under the pseudonym tessa88 put up for sale a wide list of compromised user databases of Vkontakte, Mobango, Myspace, Badoo, QIP, Dropbox, Rambler, LinkedIn, Twitter, etc. Recently, the attacker’s data were revealed by specialists from Insikt Group .
Note : To describe the hacker's profile, identify alternative nicknames, and obtain contact information belonging to the tessa88 account owner, Insikt Group experts used data provided by Recorded Future, conducted an OSINT investigation, and also analyzed numerous darknet resources.
Short review
At the beginning of 2016, a previously unknown hacker, acting under the pseudonym tessa88, first appeared in public, posting a wide list of compromised databases containing celebrity data for sale. These were the Vkontakte, Mobango, Myspace, Badoo, QIP, Dropbox, Rambler, LinkedIn, Twitter, and other databases. For several months, with the active participation of the hack community, hacker profiles were blocked in almost all the darknet communities. By May 2016, tessa88 had completely disappeared from the Internet. In the following months, numerous attempts were made to reveal the identity of the hacker. However, no concrete evidence linking tessa88 to any real person was presented.
New data suggest that under the pseudonym tessa88 may be Maxim Donakov, a resident of Penza, who used several different profiles on the darknet. It is possible that he had an accomplice who led the account tessa88, strictly adhering to the procedures OPSEC and to this day remaining anonymous. In any case, the Insikt Group experts are convinced that Maxim Donakov received a direct benefit from the sale of compromised databases and should be considered as the main actor.
Key Judgments
- The criminal career of tessa88 probably began as early as 2012, before the massive data leaks on LinkedIn, Dropbox, Yahoo, and others, which are the responsibility of the hackers acting under this pseudonym. Probably the tessa88 profile was created specifically for the sale of valuable databases.
- Analysis Insikt Group, based on the detected images of a real person, hiding under the nickname tessa88, and discussions from numerous forums, allows us to conclude with a high degree of probability that tessa88 is a man, not a woman.
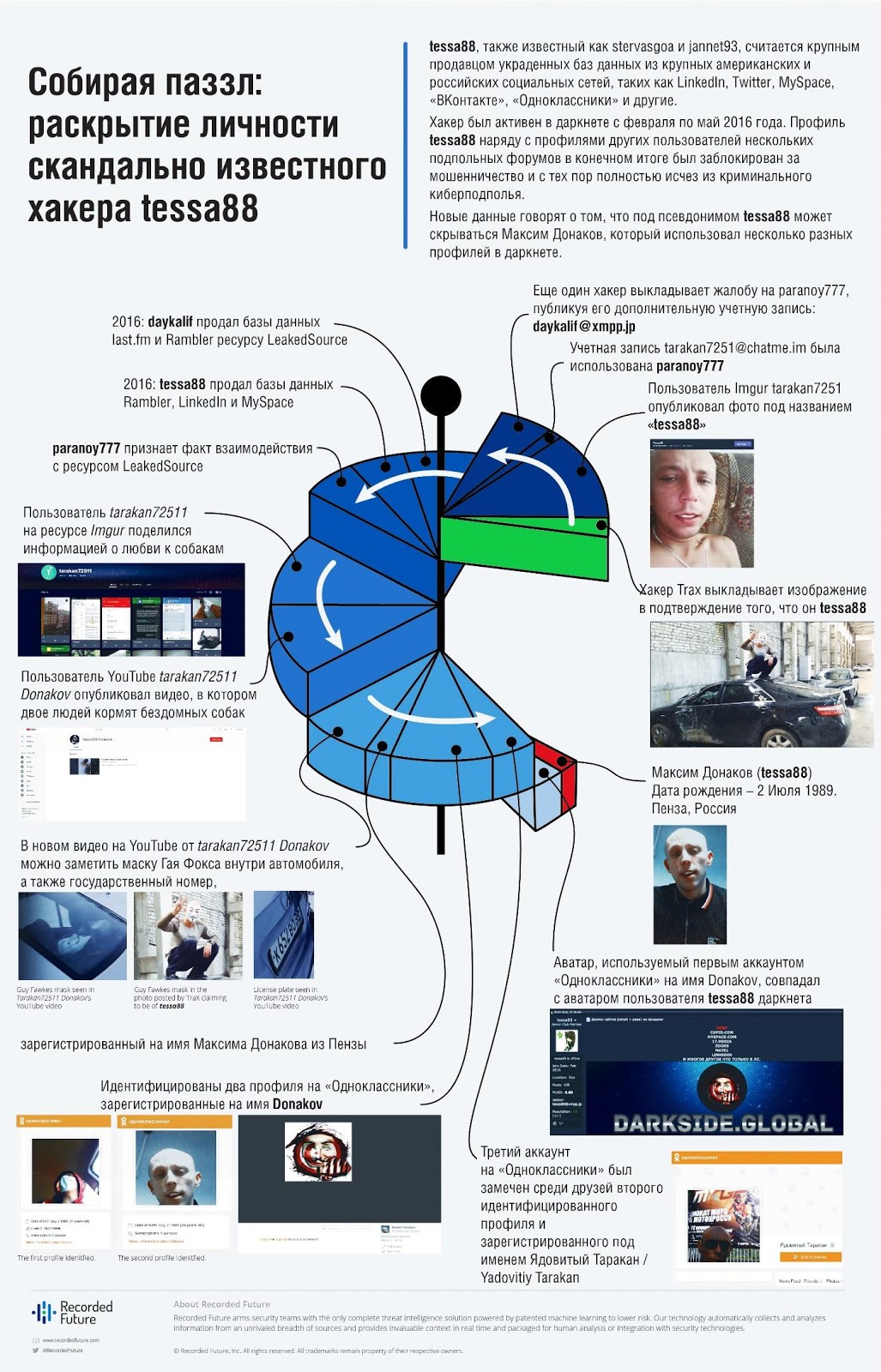
- According to the Insikt Group, the tessa88 profile is associated with a number of other accounts: Paranoy777, Daykalif and tarakan72511. These users posted similar photos on social networks, the corresponding photos in the passport of Maxim Donakov, a young man known in the network under the pseudonym Paranoy777.
- Insikt Group reports that Donakov Maxim Vladimirovich lives on the territory of the Russian Federation.
Disclosure of personality tessa88
Background
According to Recorded Future, Peace_of_Mind, also known as Peace, sold LinkedIn to the database on May 16, 2016 on the now-non-existent TheRealDeal Market. According to the results of the investigation of the theft of LinkedIn databases in October 2016, the FBI arrested a citizen of the Russian Federation Yevgeny Nikulin. He was arrested in the Czech Republic and later extradited to the United States. At the time of this writing, the investigation has not yet been completed and no objective evidence linking Nikulin to Peace_of_Mind has been provided.
The Motherboard edition published the findings of an interview with tessa88, who claimed that he was a longtime member of the criminal community, and accused Peace_of_Mind of stealing databases that were sold by tessa88. Peace_of_Mind, in turn, argued that tessa88 itself stole databases for sale on the Internet.
According to a report from InfoArmor, tessa88 acted as an intermediary who sold accounts and personal data stolen by a group of hackers called “Group E”. InfoArmor claims (Recorded Future also confirmed this) that tessa88 was the first to post a database for sale in February 2016. In May 2016, InfoArmor claimed that tessa88 and Peace_of_Mind agreed to share at least some of the compromised databases in a likely attempt to speed up the monetization of a huge amount of data. The relationship between tessa88 and Peace_of_Mind deteriorated as other members of the underground communities claimed that the data was unreliable. Thus, the report from InfoArmor confirms the findings of the Motherboard and explains the outright hostility between the two hackers.
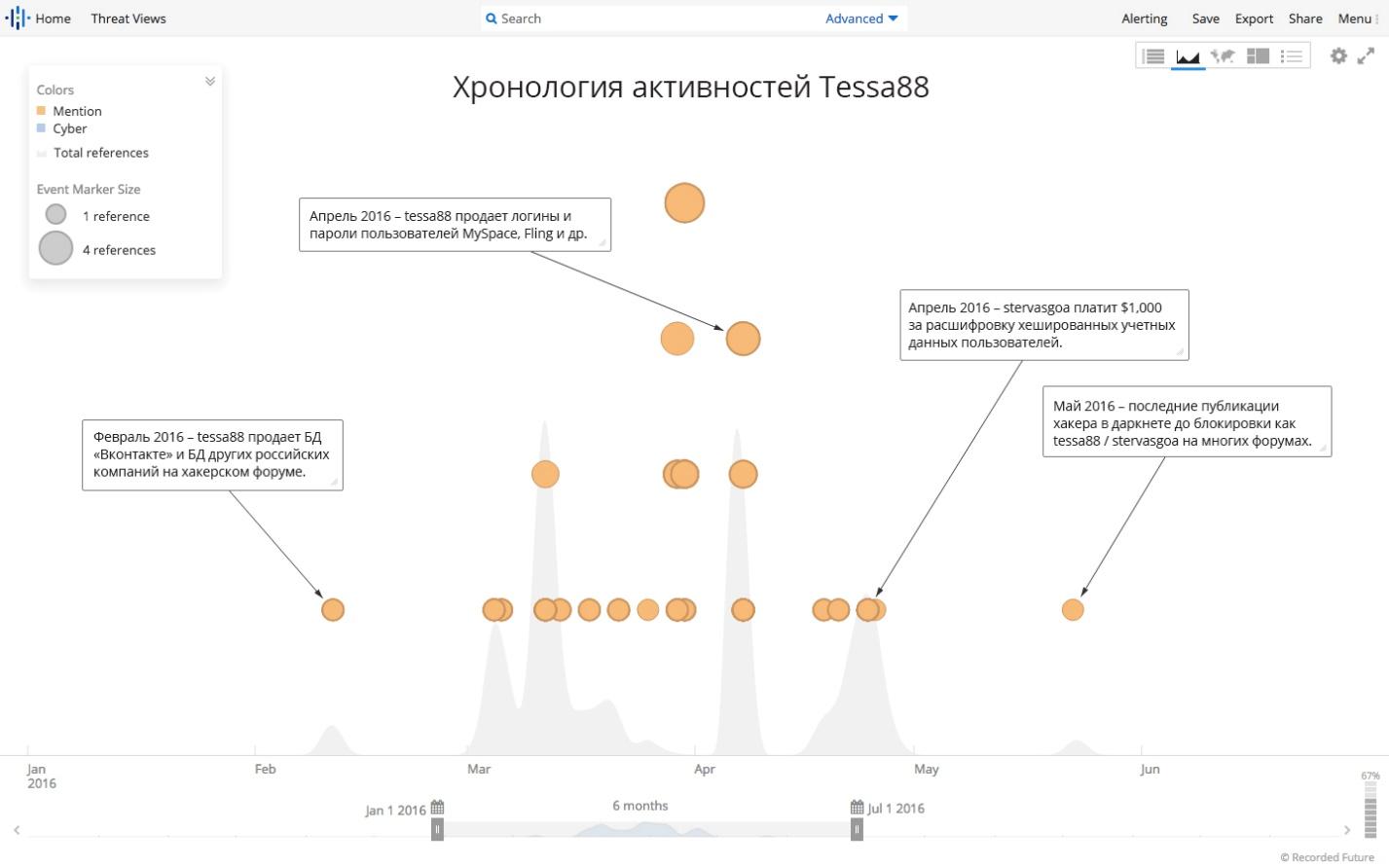
The activities of tessa88, also known as stervasgoa on darknet, are from February to May 2016.
Analysis
As a result of the analysis of the darknet resources, it was possible to match the tessa88 profile with a number of accounts, including Jabber (tessa88 @ exploit [.] Im, tessa88 @ xmpp [.] Jp, mrfreeman777 @ xmpp [.] Jp, darksideglobal @ exploit [.] Im) , ICQ 740455 account and firetessa @ yahoo e-mail [.] com.

Tessa88 sells a database of LinkedIn and MySpace websites in an underground forum that is currently closed.
On July 5, 2016, a Twitter user @firetessa announced that the Jabber account tessa88 @ exploit [.] Im, used by tessa88 for sale in underground forums, belongs to him.
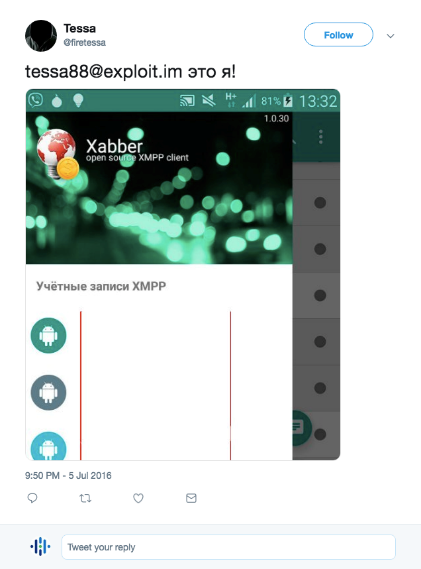
Tweet user @firetessa TraX
user, a member of the hacking community, said that tessa88 is male, and posted a prospective photo on the forum. TraX also said that tessa88 was behind the recent hacks and the subsequent sale of LinkedIn, MySpace and Yahoo, and even expressed its willingness to share this information with reporters.

Estimated photo of the user tessa88
During investigations based on open data (OSINT), the account tarakan7251 (on Imgur) was identified, from which screenshots of discussions regarding Yahoo and Equifax data leaks implemented by HelloWorld and Ibm33a14 users were published. It is noteworthy that Ibm33a14 is a Russian-speaking hacker who claimed in 2017 that he owns the originals of the dumps of the Yahoo and Equifax databases.
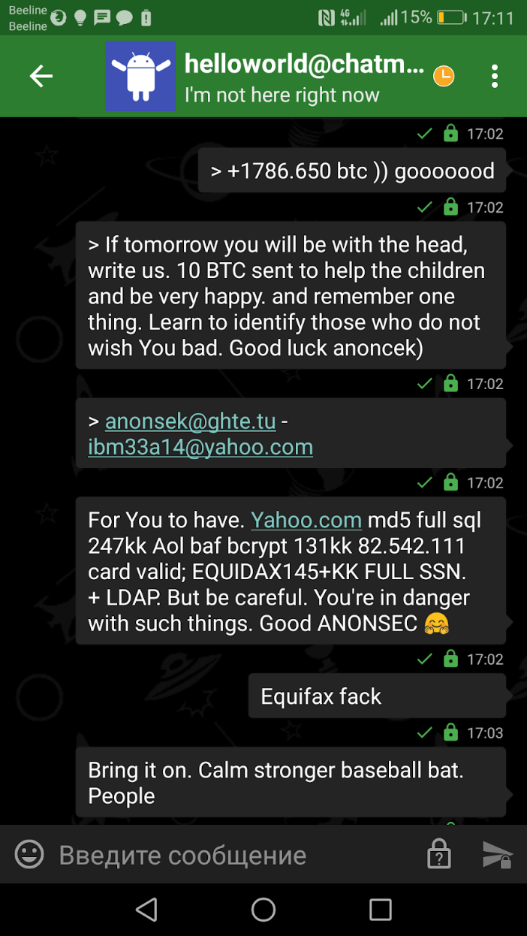
Screenshot of the chat in relation to Yahoo and Equifax
In the same Imgur account in 2017, a photo titled “tessa88” was published, which depicts a man whose appearance resembles the person depicted in the above photo posted by TraX.

Likely user image tessa88
Alias tarakan72511 is used by hacker Paranoy777, who owns the Jabber tarakan72511 account @ chatme [.] Im. Paranoy777 and tessa88 both sold stolen databases of large social networks and IT companies in 2016.
Recorded Future discovered a complaint filed against tarakan72511, which stated that Daykalif is a Russian-speaking criminal who traded in known databases and used Jabber daykalif @ xmpp [.] Jp and tarakan72511 @ chatme [.] Im accounts- the same Jabber account used by the user Paranoy777, which in turn is associated with the tarakan72511 account. If this statement is true, then it is likely that the users of Paranoy777 and Daykalif are the same person.
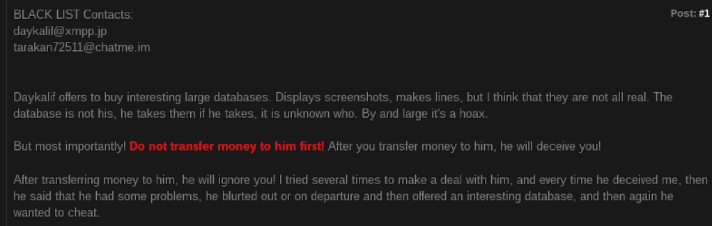
A complaint found on the underground forum
User tarakan72511 (on the resource Imgur) shared information about the love of dogs. YouTube account user Tarakan72511 Donakov posted a video in which two people feed stray dogs, which is a reference to a profile with Imgur. The video says that they are in Penza. Car on video - Mitsubishi Lancer with registration number K652BO 58.
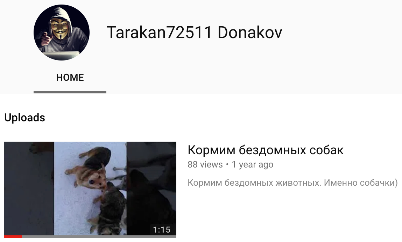
YouTube user profile Tarakan7251 Donakov.
In addition, Guy Fawkes mask is visible at the 56th second of the video. A similar mask was used as an avatar in the YouTube profile of Tarakan72511 Donakov, and also put on the person in the image shared by the user TraX.

Guy Fawkes mask on YouTube videos, YouTube user avatar and Trax user image.
In the course of the investigation of OSINT in relation to Donakov (Donakov) from Penza, it turned out that someone named MV Donakov. committed several crimes in the cities of Yaroslavl and Penza, including accidents involving the car Mitsubishi Lancer in 2017. Citizen Donakov Maxim Vladimirovich, who was born in Yaroslavl and moved to Penza, was noted in several articles on sudact.ru, which refers to the commission of a number of crimes, after which M. Donakov was sent into custody.
Based on these records, three profiles were identified on the Odnoklassniki resource, all named Maxim Donakov, two of which indicated their current location as Yaroslavl, and one as Penza. The first profile in “Classmates” belongs to a man who lived in Yaroslavl and was born on July 2, 1989. The last time a user visited the site was September 9, 2013. The second Odnoklassniki profile has the same name and date of birth as the previous profile. The photo of both profiles shows the same person as on the tarakan72511 profile in Imgur. The image of the Mitsubishi Lancer with state number A 134MK 76 is remarkable.
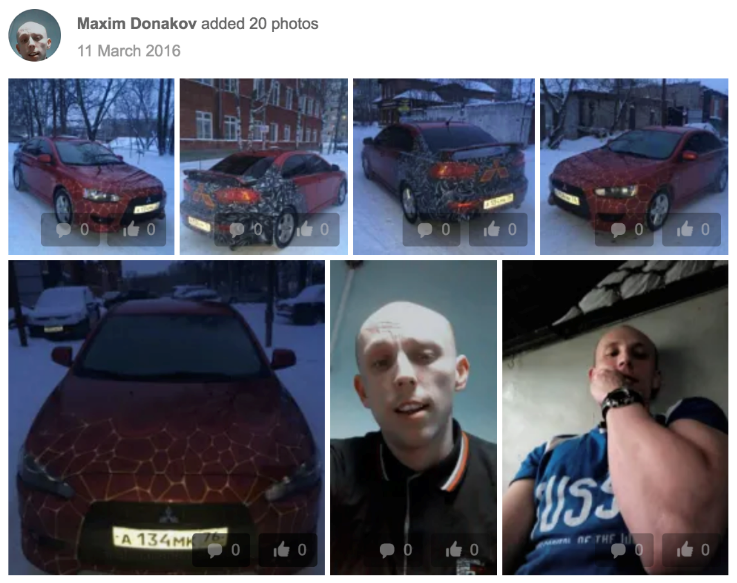
Profile photo of Maxim Donakov in Odnoklassniki
Analysis of the second profile in Odnoklassniki showed that the hacker is connected with another user, the Poisonous Cockroach, allegedly residing in Pervomaisk in Ukraine. The name “Poisonous Cockroach” is consonant with the tarakan72511 account on Imgur, and the profile picture of a person strongly resembles Maxim Donakov. It should be noted that Pervomaisk - the real place of birth of Maxim Donakov. Given the above facts, with a high degree of confidence we can say that the profile "Poisonous cockroach" also belongs to Maxim Donakov.
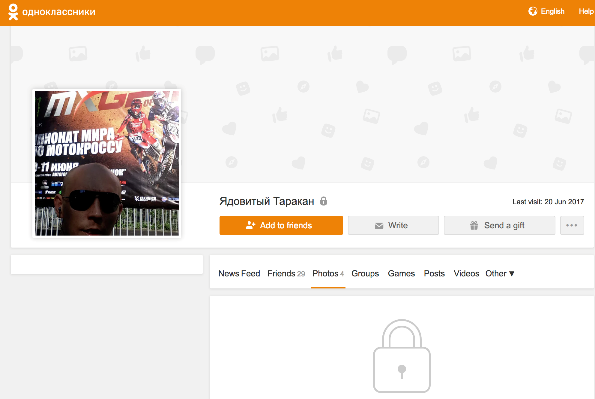
Photos of another profile of Maxim Donakov in “Classmates”
Confidential sources confirmed that Maxim Donakov is a real person, born on July 2, 1989. According to SudAct, Donakov was released under police supervision, but was then imprisoned after committing another crime in 2014. This may explain the existence of several profiles in Odnoklassniki, since Donakov may have been forced to create a new profile after being released from prison if he forgot the credentials for his previous account.
The OSINT investigation revealed a number of other accounts and contact information most likely related to Donakov (tessa88): the VKontakte profile of Maxim Ivanov with the phone number +79022222229, the profiles of Vkrugudruzei and Valet.ru, the YouTube account Maxim Donakov with the phone number +17789981919 . An open web search for Maxim Donakov showed the Gulik01 profile on Freelance.ru, which may belong to tessa88 (Donakov). In his account Gulik01 indicated that he is a Russian-speaking freelancer in the field of information technology.
Moreover, additional searches in the leaked databases revealed Maxim Donakov, a resident of Penza, born on July 2, 1989, coinciding with the user profile information from the above-mentioned Odnoklassniki profiles and an image titled "tessa88" posted by Imgur tarakan72511, which shows the same person. Again, all this suggests that tessa88 is really Maxim Donakov.

Bitcoin wallet user
analysis tessa88 Transaction analysis associated with a confirmed bitcoin -The tessa88 wallet using the Crystal Blockchain (conducted by the Insikt Group) showed that the hacker received at least 168 bitcoins, or about $ 90,000, and most of the funds were eventually laundered through LocalBitcoins, a popular peer-to-peer exchange service. Despite blocking the hacker in May 2016, he continued to use his Bitcoin wallet until August 2017.
Analysis results
Insikt Group with a high degree of confidence assesses tessa88 as one of the many nicknames created by Maxim Donakov for selling databases on underground forums. In addition, it is likely that Donakov was active on the darknet at least since 2012, and also used the pseudonyms Paranoy777, Daykalif, and tarakan72511.

Maxim Donakov, known as tessa88, Paranoy777 and Daykalif
Donakov Maxim Vladimirovich was born on July 2, 1989, a resident of the Russian Federation who had previously lived in Yaroslavl, and later moved to Penza. Analysis of accounts in social networks and other resources Recorded Future confirms the findings of the Insikt Group.
According to the analysis, the pseudonyms tessa88, Paranoy777 and Daykalif were created specifically for the sale of compromised data on the darknet. Given the controversial information about database theft of the above companies, it is difficult to determine the real strategy and methods used by hackers. However, the upcoming investigation into the case of Evgeny Nikulin, connected with a leak of data on LinkedIn, can shed light on this story and fill in the remaining gaps.
Articlepublished by Insikt Group on November 20, 2018.
Translation: Denis Gavrilov, Consultant of the Jet Infosystems Information Security Center
