Trends of DDOS attacks 2015-2016
- Transfer

DDOS attacks are one of the most common cyber threats today for online businesses. Understanding this threat is critical to developing an organization’s IT security strategy.
A study by Imperva provides key facts about how the current situation with DDOS attacks is changing. The study uses its own data from a company that provides site protection services and is one of the prominent players in this market. Therefore, the data presented can be a useful indicator of what is happening in the whole world of DDOS attacks.
For the period from the 2nd quarter. 2015 to 1st quarter In 2016, the majority of attacks (60%) were application-level attacks. However, if we consider their share on a quarterly basis, it decreased over the period under review by more than 5%.
If this trend continues, then by 2018 network-level attacks will become as common as application-level attacks.


As you can see from the graph, the number of attacks of both types has doubled over the past year. At this time, the number of customers at Incapsula increased, and this factor also affects this figure. But there are other factors, the authors note:
- The growth of services of the type "DDOS to order." Such services allow anyone to launch a short attack, for example, a 30-minute influx of network traffic without any advanced protection bypass technologies. The share of such attacks increased from 63.8% in the 2nd quarter of 2015 to 93% in the 1st quarter of 2016.
- Using tactics of multiple small attacks. Attackers use this tactic to “exhaust” IT security personnel, as well as to force the victim company to keep the means of suppressing attacks turned on, which can sometimes lead to the degradation of the services provided by the company. And finally, such frequent small attacks are used to disguise or distract from other attacks, for example, to hack a company’s network or steal data.
Network Attack Trends
Attack volume is usually defined in gigabits per second (Gbps) and is the main metric of such a threat. Over the past year, many attacks of more than 200 Gpbs have been suppressed, such attacks are no longer unusual.
The graph shows the largest network level attack volumes.
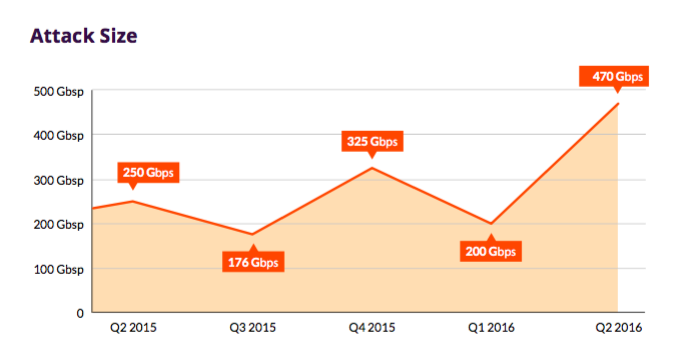
In particular, in the 2nd quarter of 2016, an attack of 470 Gbps was registered, one of the largest in the history of the Internet.
One of the features of this attack was the use of small network packets, which allowed attackers to achieve high speed forwarding packets, as well as high bandwidth. This has become a new feature that now manifests itself in many attacks.
Relying on the high speed of packet forwarding, attackers are trying to exploit the flaws of existing attack suppression devices, most of which cannot cope with such high loads. Presumably, the number of such attacks will increase further.
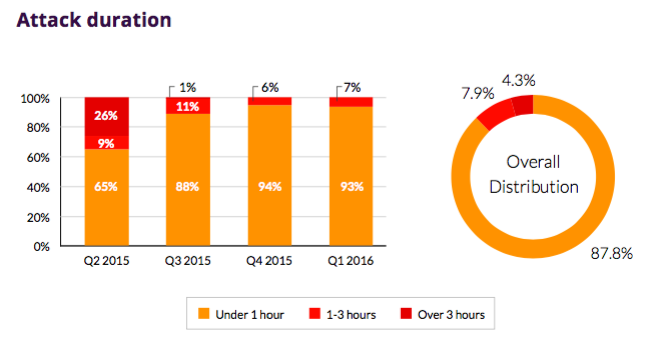
The longest attack lasted 54 days, but throughout the year there was a trend towards a decrease in the duration of the attack. The most widespread are short-term attacks lasting less than 30 minutes.
The increase in the number of network-level attacks is mainly due to the popularity of services such as “DDOS to order”. Such services allow you to launch an attack lasting from a minute and costing more than $ 5.
Since attacks of this level account for up to 90% of all attacks, this suggests that the profile of the attacker is changing. These are non-IT professionals who use DDOS attacks for extortion, and sometimes just for fun.
This trend leads to the fact that small-sized online businesses that previously could not consider themselves a possible target for attackers are becoming potential victims.

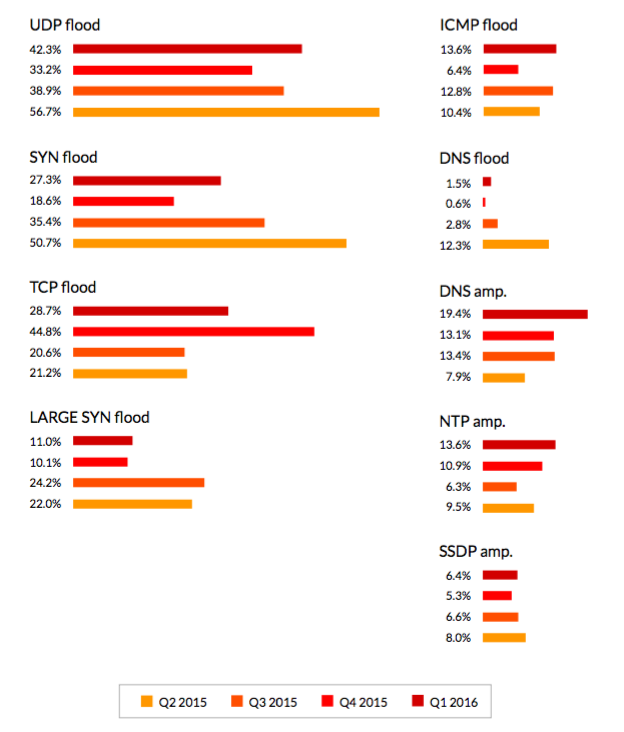
Using different types of traffic in one attack reflects the level of complexity. There is a trend towards a decrease in the share of multi-vector attacks, and the explanation for this is also that the proportion of attacks ordered by non-professionals is increasing.
It is interesting that in the 1st quarter of 2016, the percentage of attacks using 5 or more vectors significantly increased. This reminds us that while “amateurs” increase the number of simple attacks on their order, truly professional cybercriminals continue to improve their methods.
Trends in Application-Level Attacks
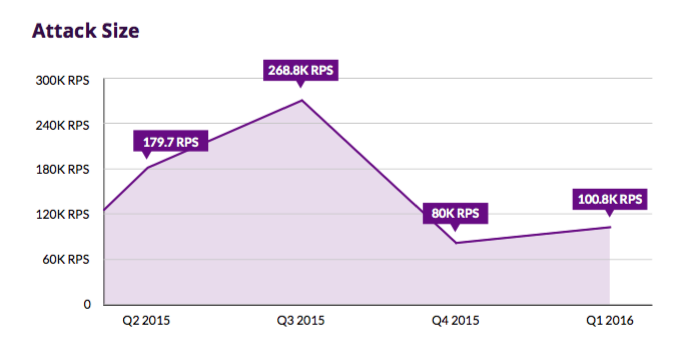
The attack volume of this kind is secondary, since most servers can be crashed with just a few hundred requests per second (RPS).
But throughout the year, attacks of gigantic volumes were observed, including 268,000 RPS - the largest in the history of the service. The purpose of such attacks is not only to “drop” the target, but also to breach the defensive perimeter.
As with network-level attacks, there are examples of more complex attacks, where attackers experiment with rare and unique methods. In particular, in one case of attacks through HTTP traffic, the target was bombarded with abnormally large POST requests (for downloading files).
With an attack volume of 163,000 RPS, attackers were able to generate 8.7 Gbps DDOS traffic. This is unheard of for application-level attacks where traffic rarely exceeds 0.5 Gbps. This attack exploited some of the nuances and weaknesses of the hybrid DDOS suppression system. This complexity of the attack gives an idea of how deeply some attackers have an understanding of the internal mechanisms of anti-DDOS solutions.
Unlike network-level attacks, application-level attacks are much easier to maintain for a long time, since this requires much less botnet resources. As a result, more than 44% of such attacks lasted more than 1 hour, while at the network level of attacks of such duration only 12%.

In contrast to network-level attacks, which are often directed against the Incapsula network as a whole, in each application-level attack, you can trace the specific target against which it was directed. This makes it possible to measure the frequency of attacks against each attacked company.
On average, more than 40% of companies are attacked more than once, and 16% more than 5 times. There is a clear trend towards an increase in repeated attacks, and the attackers do not seem to be stopped by their failed attempts and the realization that their target is well protected.

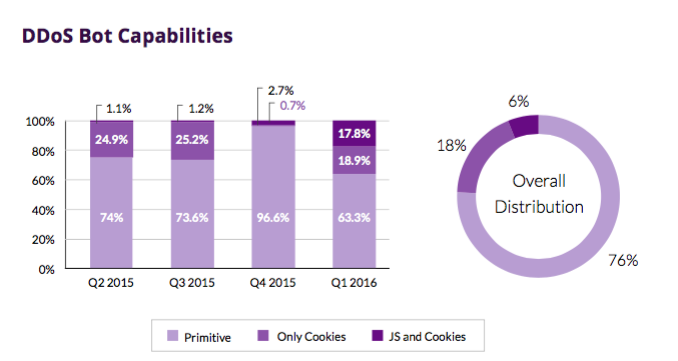
Application-level attacks use botnets to create multiple TCP connections to the server to drain its resources. To hide their nature, bots of this type use fake user-agent HTTP headers, as a rule, indicating the most popular types of browsers. Some advanced bots can emulate behavior similar to browser behavior, for example, they can save cookies and parse JavaScript. Such bots can deceive many basic security systems that rely only on these factors when determining “fake” users.
The evolution of bots indicates the development of tools for attack at the application level. 24% of DDOS bots are of the “advanced” type, that is, they are able to overcome basic security checks. In the 1st quarter of 2016, the share of such bots reached a record 36.6%.
Attack Geography Trends
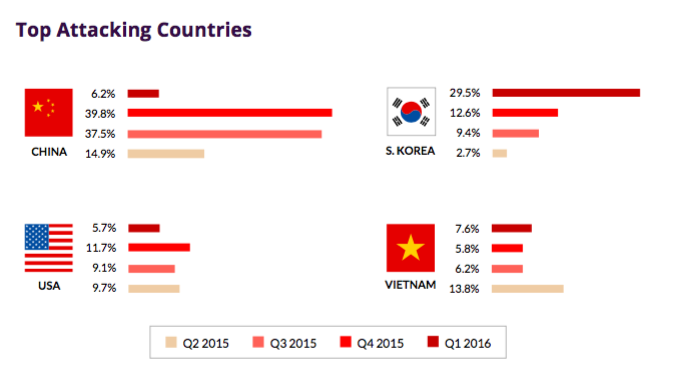
Regarding the geographical distribution of attack sources, China remains the leader: 3 quarters out of 4 China was the main source of botnet activity.
An interesting trend is a sharp increase in the traffic of bots from South Korea. In particular, in the 1st quarter of 2016, almost a third of the application-level DDOS traffic originated from South Korea. This is not surprising when you consider the powerful Internet infrastructure of this country. Its high-speed Internet backbone allows botnet owners to increase their outgoing traffic. It is likely that this will not last long, as the South Korean authorities are increasing investments in cybersecurity.
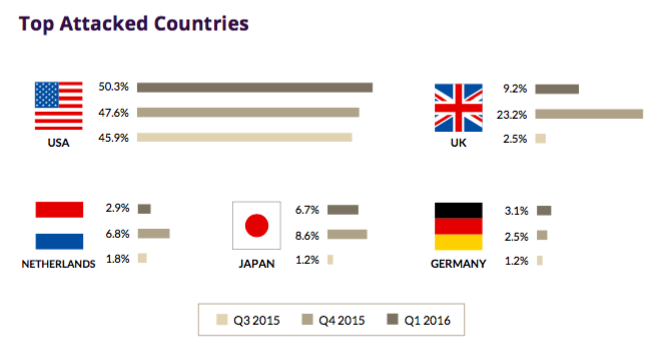
The geography of the “victims” has remained largely the same. Since cybercriminals usually attempt to extort attention or cybervandalism in order to attract attention, the main targets of attacks are companies in highly developed countries.
Of particular note is the surge in DDOS attacks in the UK over the past six months. The peak occurred in the 4th quarter of 2015, and then the trend went down, but this period was marked by several highly professional attacks, such as the “collapse” of the BBC, HSBC and Irish National Lottery sites.
During the study period, most attacks used botnets on various varieties of Nitol, Cycloe and PC Rat. On average, these attacks accounted for 55.1% of all botnet attacks.
In the 2nd and 3rd quarters of 2015, there were multiple attacks by routers for the home and office infected with Mr.Black malware. Attackers also used the Sentry MBA password cracker, which can be used for DDOS attacks when working with a high hit rate.
In the 1st quarter of 2016, there was a rise in the activity of botnets on Generic! BT, mainly from Russia and Ukraine. They accounted for 12.8% of botnet activity this quarter.

Conclusion
In conclusion, we note once again two important points:
- Basic level DDOS attacks are becoming more common due to services such as “DDOS to order”. Now, even a little understanding user in IT can order such an attack for ridiculous money simply because he was angry at the support service of your company.
- In the upper segment of the complexity of DDOS attacks, there is a constant evolution of methods and tools, and this indicates the need to monitor such trends and invest in IT security.
