Everything is under control: we protect corporate conversations. Part 3: Secure SIM
During the discussion of the previous two parts of the Tottoli GSM project description “Everything is under control: we protect corporate conversations” ( Part 1 , Part 2 ), it became clear that the technology for using and implementing MULTI SIM requires a separate description. In this article, we will talk in detail about the MULTI SIM technology.

Everyone is used to perceiving the SIM card as a certain unconditional element of subscriber authentication in the network. Within the framework of the Tottoli GSM platform, the MULTI SIM module is an integral part of the system and performs the necessary functions required by the project. Since the SIM card is an element of the network, it is impossible to consider its functionality outside the system. A more visual consideration will be the functional module in relation to specific scenarios.
First about the MULTI SIM itself:
• Memory size: 256 Kb
• Hardware-level support for the MILENAGE algorithm card and lower COMP128v1-v3.
• Support for javacard 2.2
• Download applets using APDU, as well as support for downloading GSM 03.48
Support of functions for the implementation of MULTI SIM functionality: changing “files” (EF GSM 11.11) in a (u) SIM card to change the profiles of a mobile operator: IMSI, KI, HPLMN, PLMN, FPLMN.
Also on the SIM-cards the applets developed by us and the basic profile (IMSI / KI and other parameters necessary for registering on the network) of one of the operators available to us are preinstalled. By “operator accessibility” in this context is meant a support contract with this operator and the implementation of the profile pool in our HLR.

In the described scenarios, we intentionally omitted the standard procedures for interacting with the network and focused on the main points.
Scenario 1:
The employee receives a telephone set (SLT) with MULTI SIM installed. When you turn on the phone, MULTI-SIM is automatically registered in the local network thanks to the preset network settings in the SIM card. The local network, in turn, allows this SIM card to register based on the prescribed SIM parameters in the HLR of its network.
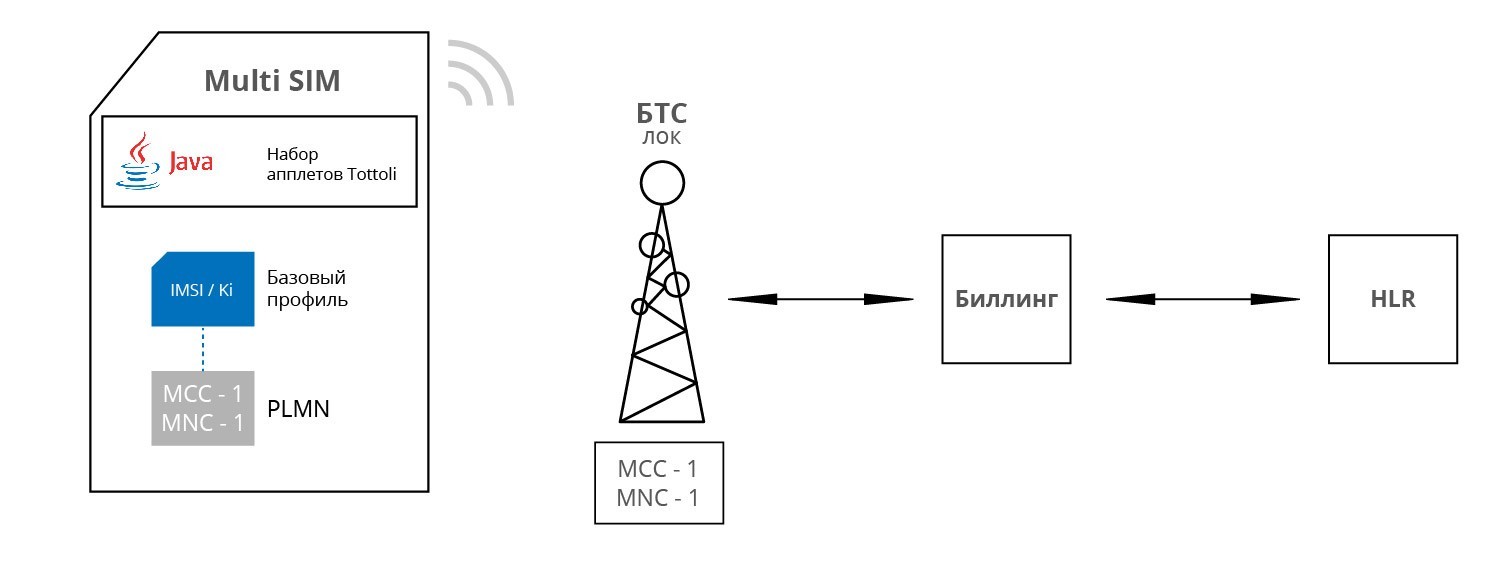
Scenario 2:
Outgoing calls within the local network are made in a standard way. For calls between employees, FMC short numbers are used. FMC numbers and routing rules for them are configured in the company's billing. Employees can use FMC numbers both inside the local network and outside it.
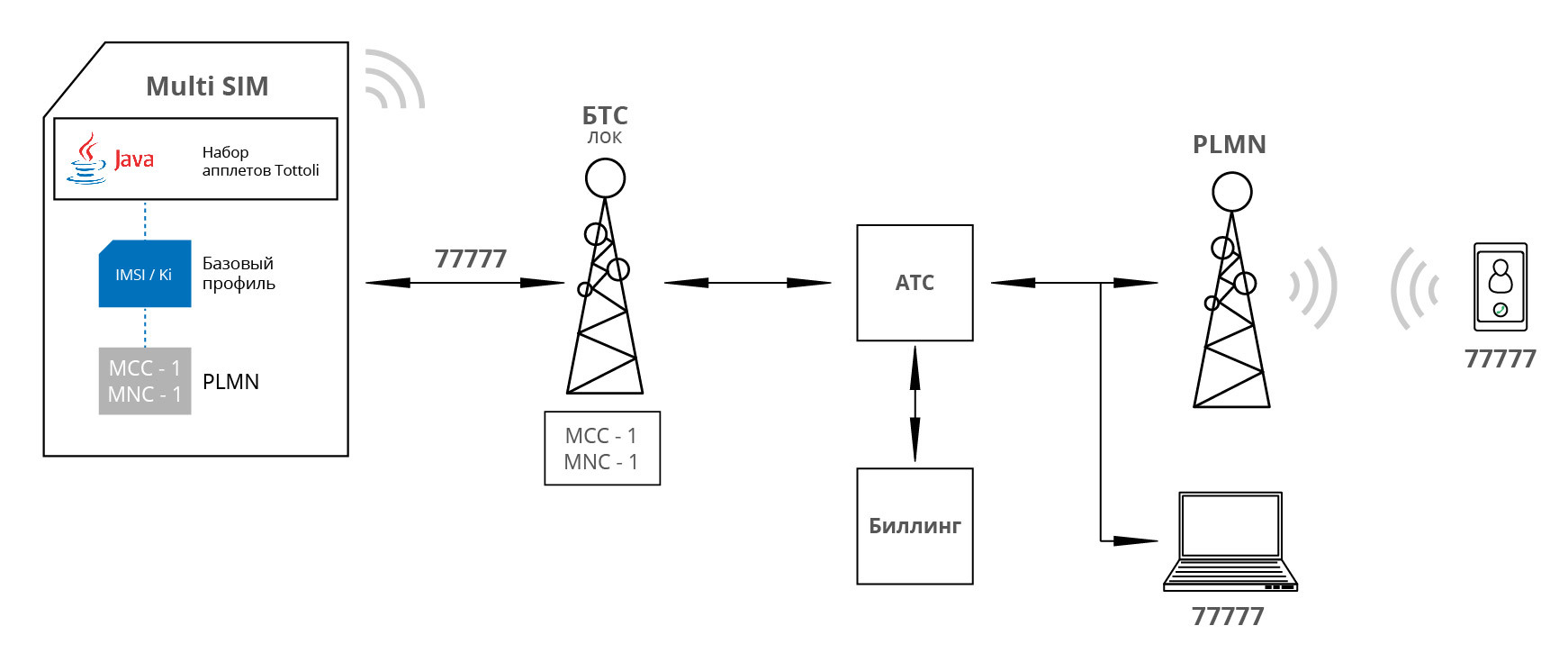
Scenario 3:
The employee leaves the local network coverage area; the telephone sets out the Location Update (LU) procedure from the networks currently available. All network parameters at LU automatically fall into the billing company for further analysis and management. If necessary, the server decides to change the current profile and / or change the operator. To do this, an OTA team is formed with the profile and priority network parameters. This command is sent to the subscriber device and the profile is changed and the network is reselected. When an employee is on public networks, all his communications also go through the company's resources and are subject to internal rules. This makes it possible to allow or prohibit the use of specific networks or make them priority. A special applet constantly transfers network parameters to the company’s server.
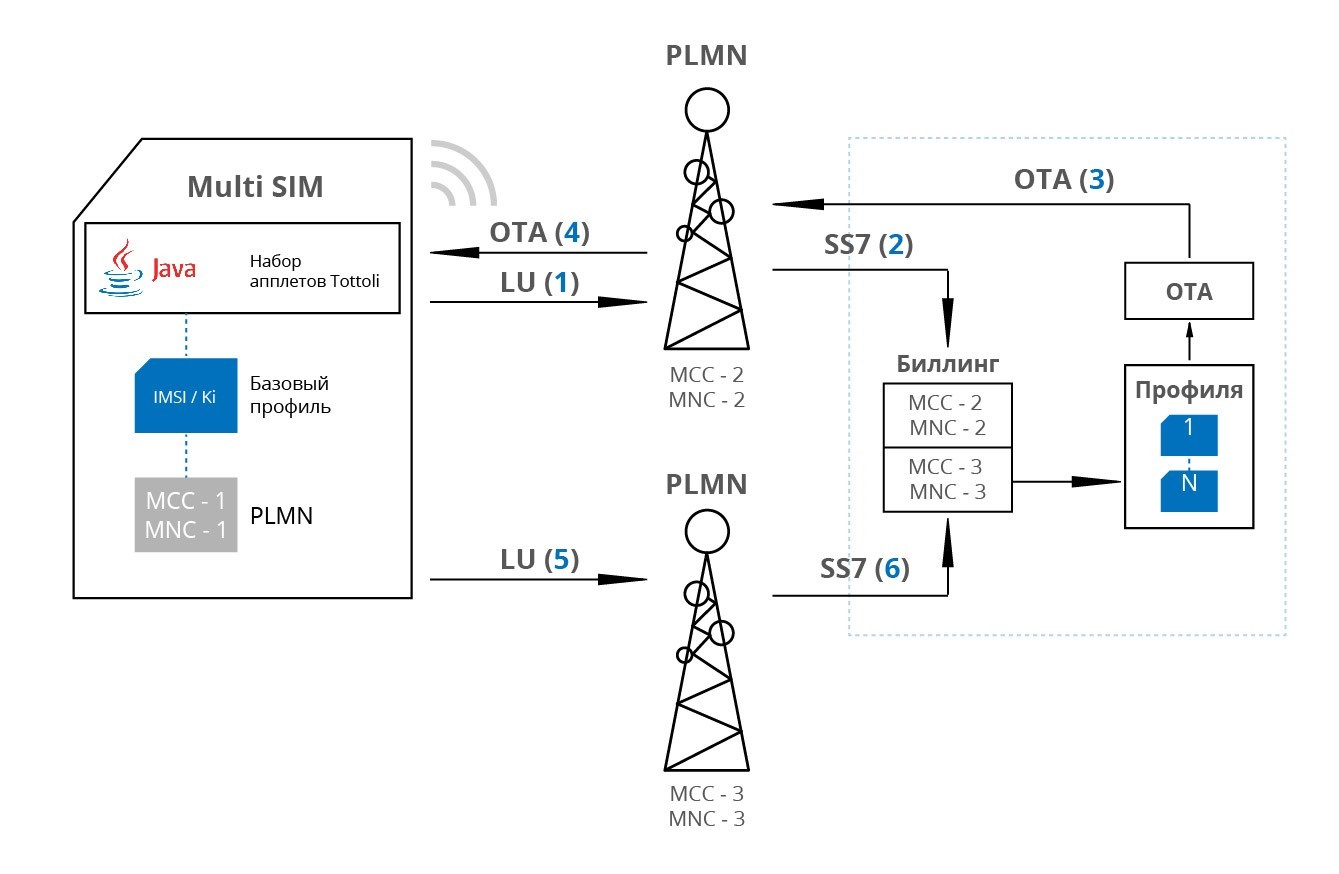
Scenario 4:
If the outgoing call goes on the external PLMN network, it also passes through the company's PBX. This is achieved by the operation of a special applet on the SIM card. After dialing the number and pressing the call button, the applet intercepts the call and routes it to the service number, which is allocated by the billing company for each call. Thus, between the subscriber A and the subscriber B there is always a telephone exchange of the company, which does not allow to detect a direct connection between the subscribers.

Scenario 5:
Organization of an incoming call is made using a virtual number (DID).
Each employee has a virtual number in ABC / DEF format. The routing rules for calls to these numbers are also spelled out in the company's billing. Thus, a call from an external PLMN network to a virtual number (DID) also passes through the company's PBX.

Scenario 6:
Using the Internet (DATA) in an external network occurs according to the rules prescribed in the billing company. Access point parameters are registered on the SIM card. APN is provided by the company and thus all DATA traffic is routed to company equipment (GGSN). The company also has a Policy Controller (DPI) deployed to analyze employee DATA traffic. This ensures security at the Internet level, regardless of which operator’s network the employee is on.
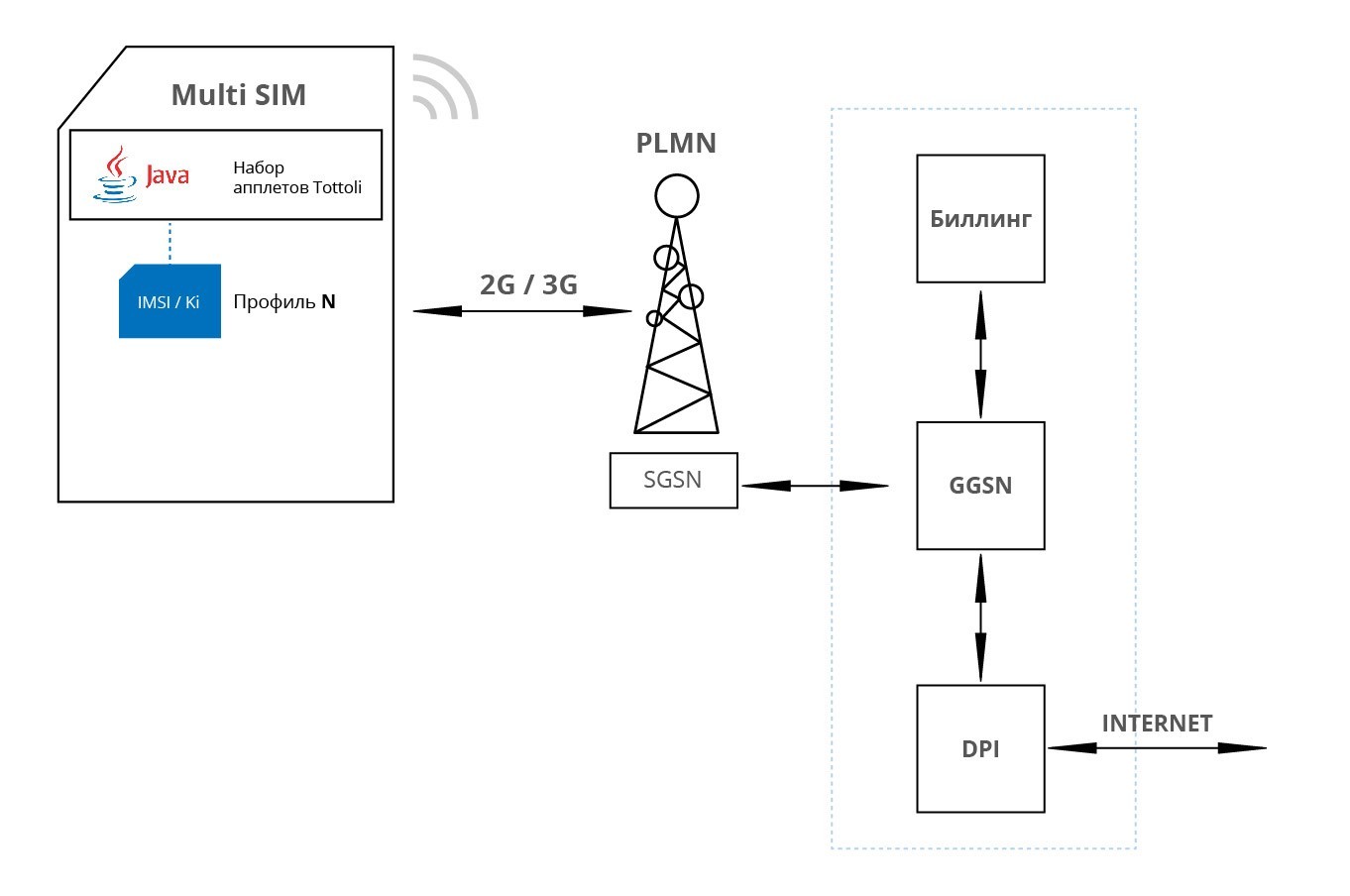
Scenario 7:
SMS service is also on the side of the company. Thus, the company has all the SMSC management tools: enable / disable sending / receiving SMS, routing and logic management. All this is done at the network level. Thus, if the company’s billing flag contains a ban on incoming SMS, such an attempt will be suppressed at the level of the initiating operator. This mechanism does not allow attacks using SMS of any class, including the so-called Silent SMS.
Scenario 8:
All employees have access to the USSD service. An employee can use the services of this service through the SIM MENU SIM card. All logic is deployed on the company's service. Thus, the employee receives all relevant information and manages the available services and services that are allowed for a particular employee or group of employees.
Scenario 9:
A profile change (IMSI / KI) on a SIM card can occur according to various events: during the LU procedure, a profile change is initiated by the employee himself via SIM MENU, a profile change is initiated from the server side without the employee’s participation, and the profile is changed according to the specified timing. Profile change is provided by a pre-installed applet on the SIM-card. Profiles are loaded using OTA from the server side of the company. The procedure for changing the profile occurs simultaneously with the TA function and changing the IMEI. Thus, all identifiers in the network are changed.
Also on these MULTI-SIM cards are available applets with functions:
- Track IMEI
- Remote control
- Dynamic SIM menu
- History location
- Notification bar
As a result, thanks to software add-ons implemented on MULTI-SIM, we were able to implement the necessary interaction between the subscriber unit and the server part both in the local network and in public networks without compromising security.
Read more:
Everything is under control: we protect corporate conversations. Part 1.
Everything is under control: we protect corporate conversations. Part 2: a secure telephone
