Gateway for the mail server
Not so long ago I was lucky to change my job. I got into a company that, in principle, deserves a separate article for a number of reasons and may appear here later. If in a nutshell about the structure of our department: doing something other than your main activity is not forbidden, so my gaze fell on our mail server, which causes a lot of trouble.
The company has remote affiliate branches, evenly distributed throughout Western Europe, using a single mail server. Unfortunately, the budget of the IT department is not very large, and there are a lot of users (about 700 email accounts). It was used, and now it is used for Exchange 2010 mail with the latest updates and more or less configured spam filtering rules, but it somehow went wrong with the antivirus. The purchased solution refused to work normally, inflating the incoming mail queue to indecent sizes and tightly hanging all the mail. (Yes, I know that all best practice talks about the need for an edge server and a separate archive server, but what happened at that time was what it was.)
We take the initiative in our own hands. To my great surprise, I could not immediately find a detailed manual for solving such a problem, so the idea arose to share my trial and error in RuNet.
From what was ultimately tested and tested:
Zentyal , ASSP and Xeams .
After more googling and trying out a few more products, I opted for Xeams. Yes, unfortunately, this is not OpenSource , but a closed product, however, it is very friendly to those administrators who do not have much experience in Linux & Dovecot & Postfix & etc bundles. In addition, it is cross-platform, so that even those with a link to you will not have problems. It can work in three modes: Stand alone server - yes, xeams can be just a mail server. How much good I can’t say, because this function interested me last. Spam firewall - in this mode, xeams only accepts all mail traffic on itself and further distributes it to corporate mail servers. Hybrid mode
- Hybrid mode. It combines the other two, I recommend setting it, because it cannot fully filter spam without passing outgoing traffic through itself.

Since we already had a mail server, we used the SMTP-Proxy
option. Installation was performed on a clean machine with Ubuntu 14.04. The only thing that needed to be delivered was Java, which, in fact, runs the Xeams engine.
Xeams uses ClamAV, however, it recommends putting it on a separate machine, but no problems were noticed during use on one machine. If you need to reconfigure the ClamAV settings later, this can also be done without problems.
Download the archive with the installer from here . Unpack, give rights and execute.
If everything went well, the Web-Interface will be available on port 5272.
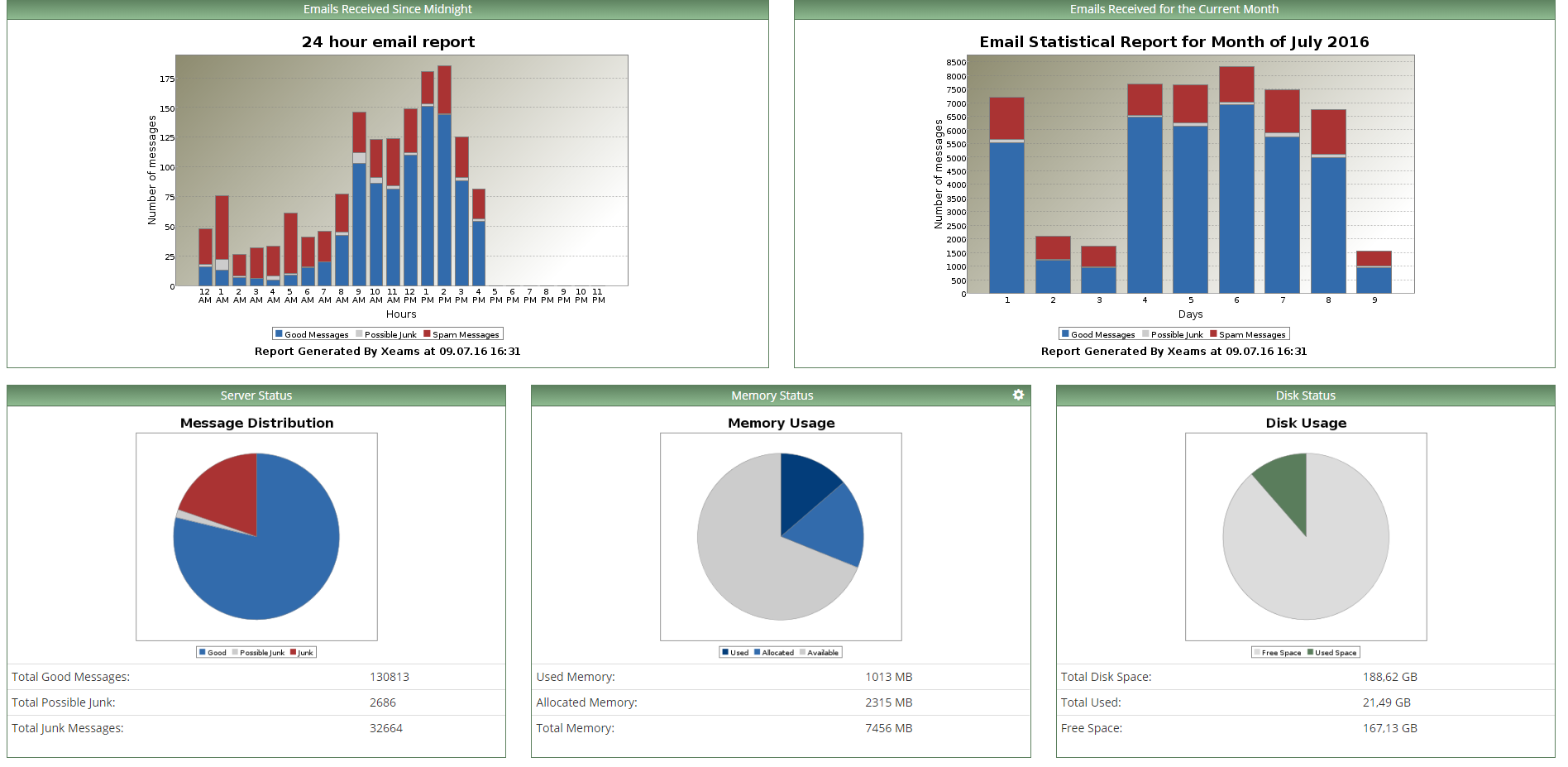
The main page contains reports, graphs and basic parameters of resource consumption. We gave the machine 8GB of RAM, the peak load several times reached 6, so these numbers are justified.
We pass to the setting itself. On Firewall, we wrap all traffic on port 25 on our Xeams IP on port 2525. This is because Xeams not only receives, but also sends mail through it, so that incoming mail arrives at port 2525, and outgoing traffic arrives at port 25.
In general, the Xeams setup is simple and quite convenient. On which moments, nevertheless, I would like to draw attention to:
Spam filters
Xeams has a fairly large set of spam filters:
Real-time Black-hole servers (RBL) . Each list can be given its own importance points, on the basis of which Xeams determines the reliability of the letter.
Of adaptive filters, Bayesian Analysis is used , which completely copes with the functions assigned to it. There were fears that it will work poorly, due to the large number of languages of correspondence (Russian, German, English, Spanish, Italian, Polish, Greek), however, the percentage of false positives is quite low.
Auto Learn Sender. Great thing, it is because of it that we pass all outgoing mail traffic through Xeams, which analyzes the addresses of the recipients and takes them into account when making the final assessment of the reliability of the letter.
The other filters are standard and I don’t think that they need to be described in this article, which has already turned out to be bloated.
Now I would like to devote a few words to the not entirely obvious nuances:
After several days of use, we changed the standard filter settings and the configuration of the glasses:
and the Bayesian Score were raised to 115.
The most common false positive was the problem of correct encoding, since, nevertheless, Xeams was imprisoned in English, decided to turn off this setting.
By default, ClamAV does NOT check macro attachments in Ofiice documents, i.e. the newfangled .locky can safely pass,
you can fix this with one line:
In general, two weeks after using and analyzing spam, possible spam, we can say that 98% of spam does not go through.
I will be glad to suggestions, comments and criticism in the comments.
The company has remote affiliate branches, evenly distributed throughout Western Europe, using a single mail server. Unfortunately, the budget of the IT department is not very large, and there are a lot of users (about 700 email accounts). It was used, and now it is used for Exchange 2010 mail with the latest updates and more or less configured spam filtering rules, but it somehow went wrong with the antivirus. The purchased solution refused to work normally, inflating the incoming mail queue to indecent sizes and tightly hanging all the mail. (Yes, I know that all best practice talks about the need for an edge server and a separate archive server, but what happened at that time was what it was.)
We take the initiative in our own hands. To my great surprise, I could not immediately find a detailed manual for solving such a problem, so the idea arose to share my trial and error in RuNet.
From what was ultimately tested and tested:
Zentyal , ASSP and Xeams .
I will not describe them in detail, but a few words are worth saying
Let's start in order. Zentyal dropped quickly enough, because the goal was to change the entire Active Directory infrastructure and move to an open-source solution, and indeed, it is rather a kind of combine from everything that is possible. It seems to me that it would perfectly suit SMB for up to 50 users.
Перейдем ко второму нашему кандидату. Anti-Spam SMTP Proxy. Весь набор для проксирования почтового трафика в нем есть, т.е. и Байесовская фильтрация спама, и пенальти очки, и черные/белые списки, и ClamAV и куча-куча всего еще. Есть единственный недостаток: юзабельность. Т.е. веб-интерфейс ASSP это обернутые в какой-то ад конфиги, которые лично мне проще править через консоль. Штука эта простояла у нас около 2х месяцев в продакшене, а потом какой-то из админов что-то поменял в конфигах и все заверте… В общем, мы поймали пару раза .locky и в последний раз актуального бэкапа не нашлось, потому человек ушел в отпуск, а когда пришел уже было поздно. Это заставило нас пересмотреть нашу политику резервного копирования, но об этом в другой раз. К огромному сожалению, отдельного Linux-администратора у нас нет, т.к. почти вся инфраструктура на Microsoft, поэтому ковырять монструозные награмождения через веб-интерфейс для админов была реальная пытка.
Перейдем ко второму нашему кандидату. Anti-Spam SMTP Proxy. Весь набор для проксирования почтового трафика в нем есть, т.е. и Байесовская фильтрация спама, и пенальти очки, и черные/белые списки, и ClamAV и куча-куча всего еще. Есть единственный недостаток: юзабельность. Т.е. веб-интерфейс ASSP это обернутые в какой-то ад конфиги, которые лично мне проще править через консоль. Штука эта простояла у нас около 2х месяцев в продакшене, а потом какой-то из админов что-то поменял в конфигах и все заверте… В общем, мы поймали пару раза .locky и в последний раз актуального бэкапа не нашлось, потому человек ушел в отпуск, а когда пришел уже было поздно. Это заставило нас пересмотреть нашу политику резервного копирования, но об этом в другой раз. К огромному сожалению, отдельного Linux-администратора у нас нет, т.к. почти вся инфраструктура на Microsoft, поэтому ковырять монструозные награмождения через веб-интерфейс для админов была реальная пытка.
After more googling and trying out a few more products, I opted for Xeams. Yes, unfortunately, this is not OpenSource , but a closed product, however, it is very friendly to those administrators who do not have much experience in Linux & Dovecot & Postfix & etc bundles. In addition, it is cross-platform, so that even those with a link to you will not have problems. It can work in three modes: Stand alone server - yes, xeams can be just a mail server. How much good I can’t say, because this function interested me last. Spam firewall - in this mode, xeams only accepts all mail traffic on itself and further distributes it to corporate mail servers. Hybrid mode
- Hybrid mode. It combines the other two, I recommend setting it, because it cannot fully filter spam without passing outgoing traffic through itself.

Since we already had a mail server, we used the SMTP-Proxy
option. Installation was performed on a clean machine with Ubuntu 14.04. The only thing that needed to be delivered was Java, which, in fact, runs the Xeams engine.
sudo apt-get update && upgrade
sudo apt-get install libc6-i386
sudo update-alternatives --config java
sudo apt-get install default-jre
java -version
Xeams uses ClamAV, however, it recommends putting it on a separate machine, but no problems were noticed during use on one machine. If you need to reconfigure the ClamAV settings later, this can also be done without problems.
sudo apt-get install clamav-daemon
Download the archive with the installer from here . Unpack, give rights and execute.
wget http://www.xeams.com/files/XeamsLinux64.tar
tar -xf ./XeamsLinux64.tar
chmod +x ./Install.sh
./Install.sh
If everything went well, the Web-Interface will be available on port 5272.
The main page contains reports, graphs and basic parameters of resource consumption. We gave the machine 8GB of RAM, the peak load several times reached 6, so these numbers are justified.
We pass to the setting itself. On Firewall, we wrap all traffic on port 25 on our Xeams IP on port 2525. This is because Xeams not only receives, but also sends mail through it, so that incoming mail arrives at port 2525, and outgoing traffic arrives at port 25.
In general, the Xeams setup is simple and quite convenient. On which moments, nevertheless, I would like to draw attention to:
Server Configuration> Server Configuration> Basic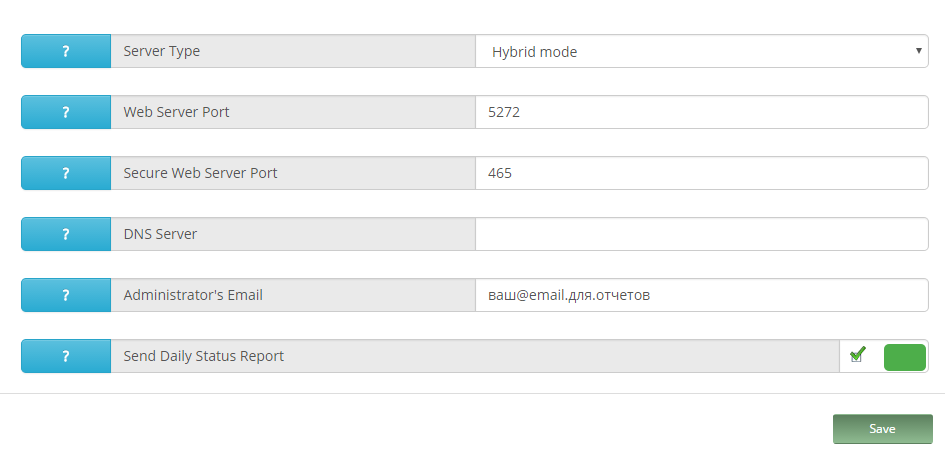
Указываем порт для http/https web-доступа.
DNS, если указан в настройках самой машины, то можно не указывать
И адрес, для ежедневных отчетов.
Указываем порт для http/https web-доступа.
DNS, если указан в настройках самой машины, то можно не указывать
И адрес, для ежедневных отчетов.
Server Configuration> Server Configuration> Advanced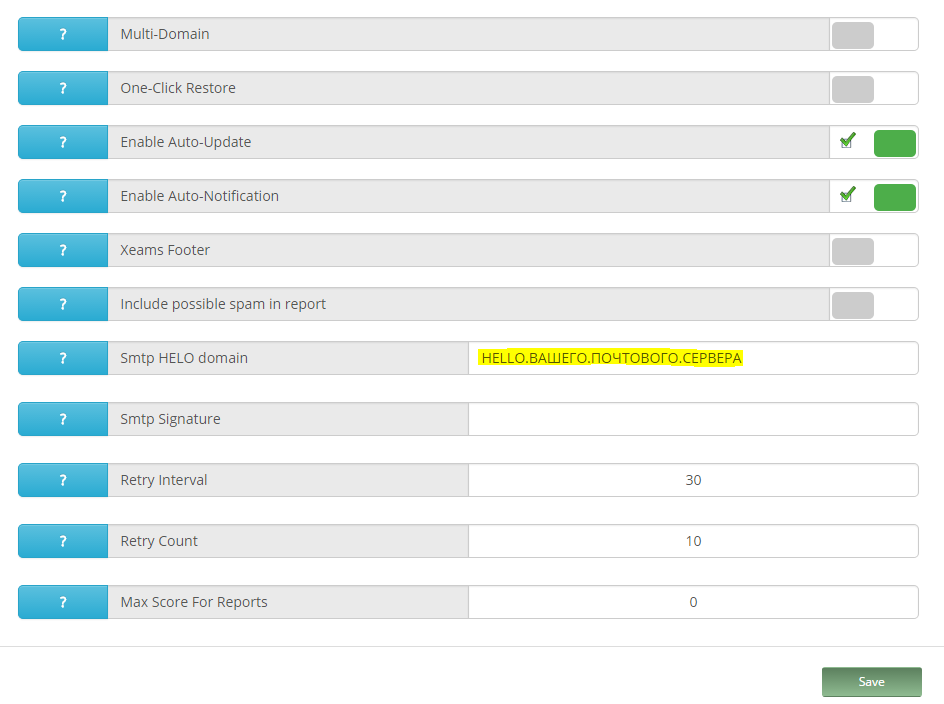
На вкладке Advanced необходимо указать HELO (как правило, можно просто скопировать из настроек имеющегося почтового сервера), чтобы самим не попасть в СпамЛисты.
На вкладке Advanced необходимо указать HELO (как правило, можно просто скопировать из настроек имеющегося почтового сервера), чтобы самим не попасть в СпамЛисты.
Server Configuration> SMTP Configuration> Relaying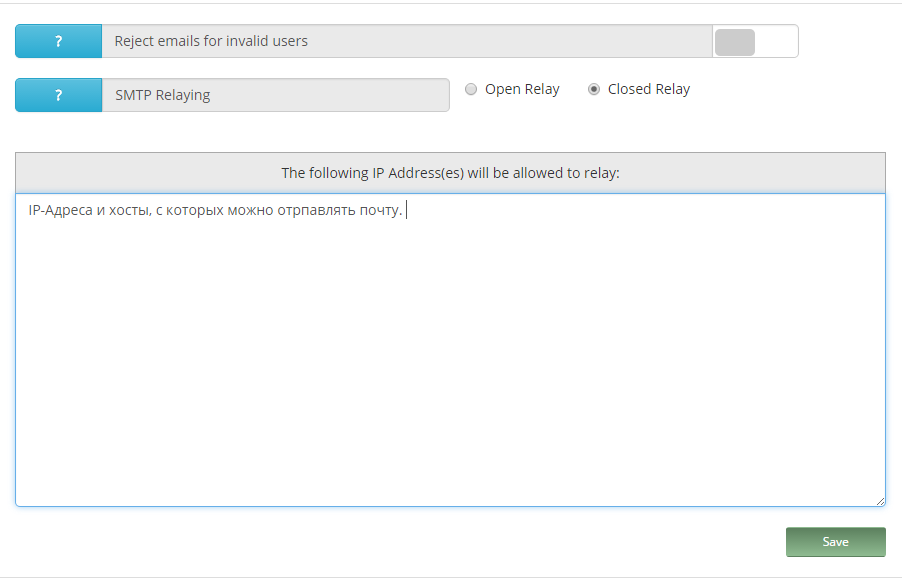
Используйте только Closing relay и пропишите адреса и хосты, с которых можно будет отправлять почту без аутентификации.
Со стороны Exchange это выглядит вот так, где закрашенным прописан адрес smtp-relay
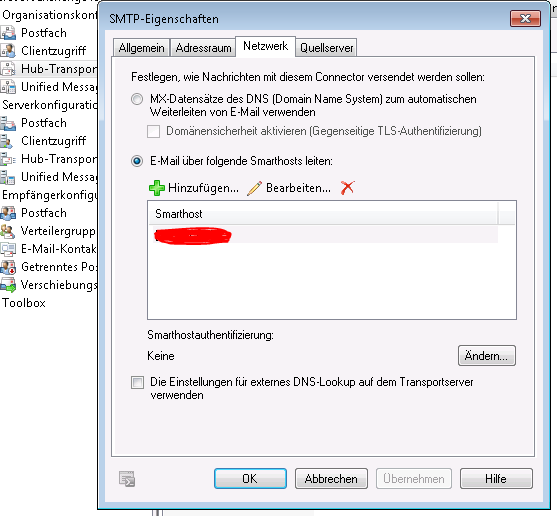
Используйте только Closing relay и пропишите адреса и хосты, с которых можно будет отправлять почту без аутентификации.
Со стороны Exchange это выглядит вот так, где закрашенным прописан адрес smtp-relay
Server Configuration> SMTP Proxy Server Configuration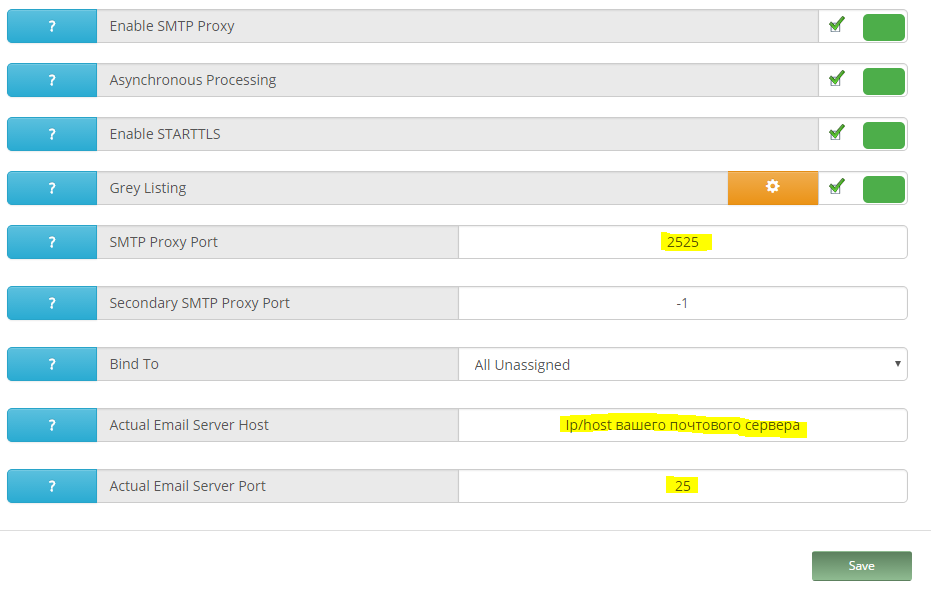
Здесь все просто, указываем порты, на которые принимается почта, указываем адрес пересылки и порт. В нашем случае, это адрес корпоративного Exchange
Здесь все просто, указываем порты, на которые принимается почта, указываем адрес пересылки и порт. В нашем случае, это адрес корпоративного Exchange
Greylisting
. I strongly recommend that you register all public mail and white list domains there, because a letter delay of 10 hours due to incorrect settings on the sending mail server side, alas, is not uncommon.Отдельно хотелось бы сказать о <a

href=«ru.wikipedia.org/wiki/%D0%A1%D0%B5%D1%80%D1%8B%D0%B9_%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA»>Грейлистинге
href=«ru.wikipedia.org/wiki/%D0%A1%D0%B5%D1%80%D1%8B%D0%B9_%D1%81%D0%BF%D0%B8%D1%81%D0%BE%D0%BA»>Грейлистинге
Server Configuration> Active Directory Integration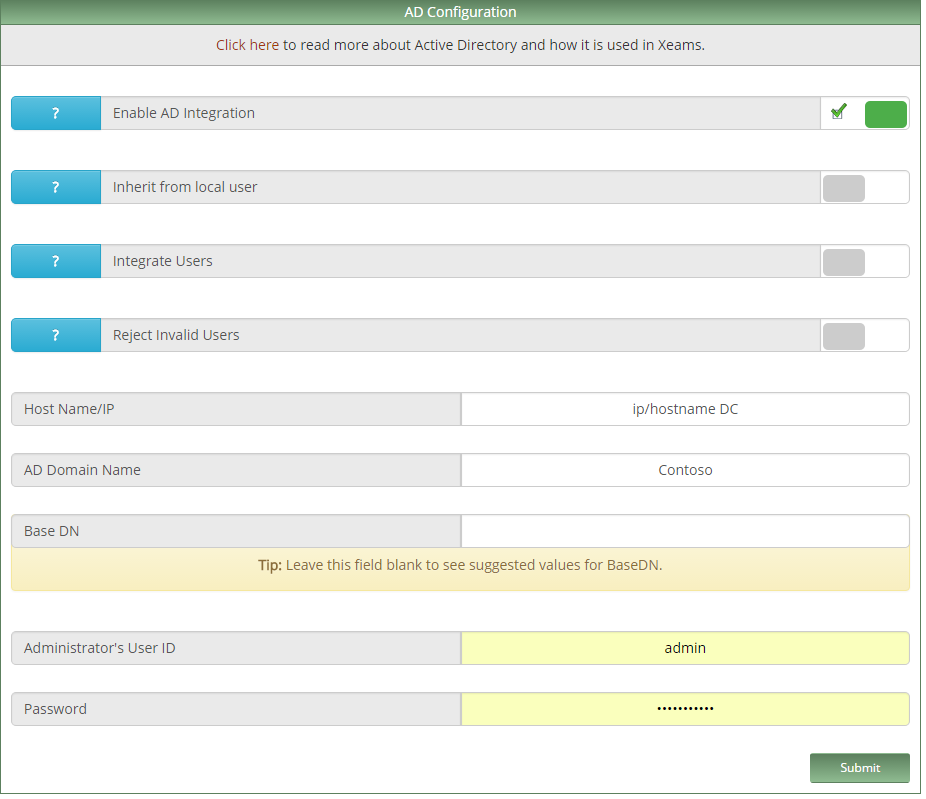
Если у Вас поднят Active Directory, то его без проблем можно интегрировать в Xeams. Зачем? Хотя бы для того, чтобы пользователи не мучали Вас в первое время, что у них не доходит почта. Пользователь без проблем сможет зайти и проверить свой почтовый ящик, просмотреть свой спам и прописать свои black/whitelist:
Кроме этого, это предоставляет возможность использовать SMTP только аутентифицированным пользователям. В общем, удобно.
Если у Вас поднят Active Directory, то его без проблем можно интегрировать в Xeams. Зачем? Хотя бы для того, чтобы пользователи не мучали Вас в первое время, что у них не доходит почта. Пользователь без проблем сможет зайти и проверить свой почтовый ящик, просмотреть свой спам и прописать свои black/whitelist:
Кроме этого, это предоставляет возможность использовать SMTP только аутентифицированным пользователям. В общем, удобно.
Clamav
Если Вы, также, как и я установили ClamAV на тот же сервер, что и Xeams, то страница настройки будет приглядеть примерно вот так:
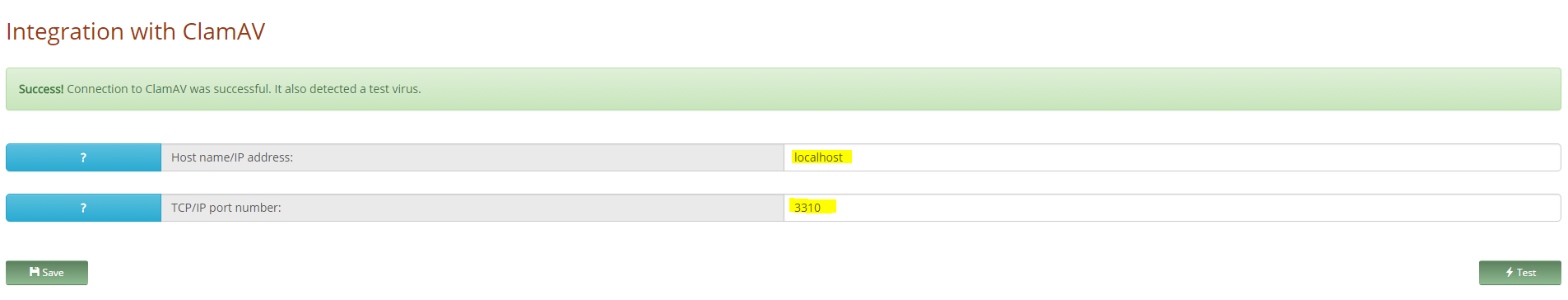
чуть ниже я расскажу о некоторых нюансах его использования.
чуть ниже я расскажу о некоторых нюансах его использования.
Spam filters
Xeams has a fairly large set of spam filters:
Real-time Black-hole servers (RBL) . Each list can be given its own importance points, on the basis of which Xeams determines the reliability of the letter.
Of adaptive filters, Bayesian Analysis is used , which completely copes with the functions assigned to it. There were fears that it will work poorly, due to the large number of languages of correspondence (Russian, German, English, Spanish, Italian, Polish, Greek), however, the percentage of false positives is quite low.
Auto Learn Sender. Great thing, it is because of it that we pass all outgoing mail traffic through Xeams, which analyzes the addresses of the recipients and takes them into account when making the final assessment of the reliability of the letter.
The other filters are standard and I don’t think that they need to be described in this article, which has already turned out to be bloated.
Now I would like to devote a few words to the not entirely obvious nuances:
After several days of use, we changed the standard filter settings and the configuration of the glasses:
Graduation of letters by points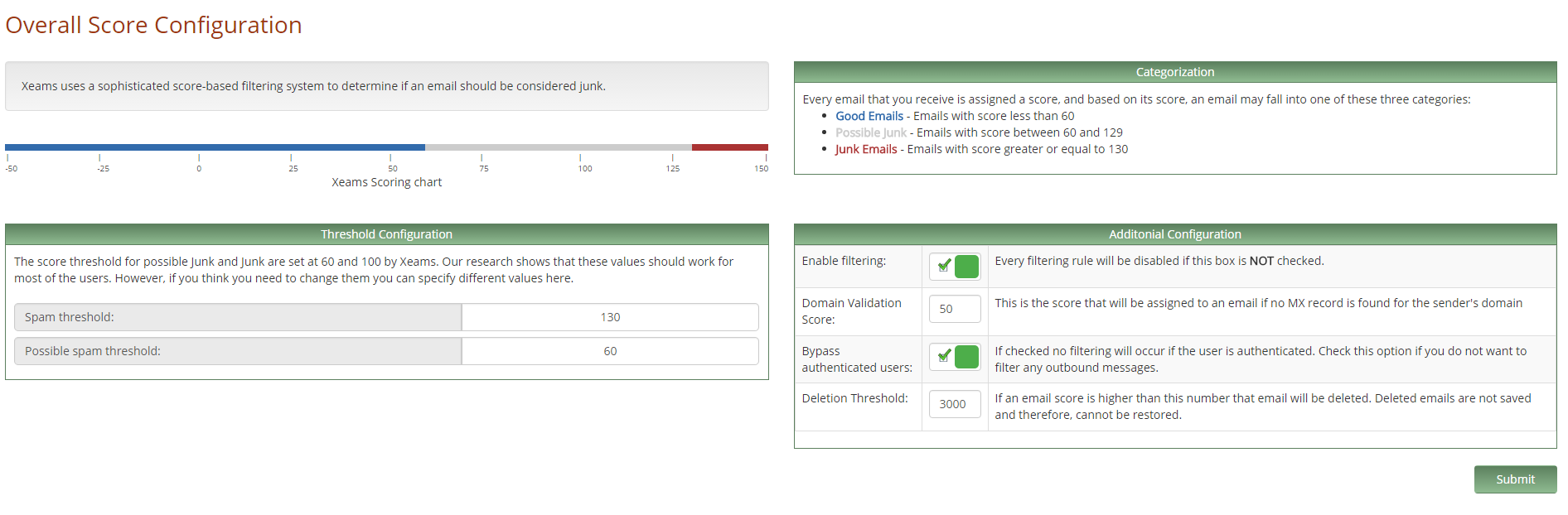
and the Bayesian Score were raised to 115.
The most common false positive was the problem of correct encoding, since, nevertheless, Xeams was imprisoned in English, decided to turn off this setting.
By default, ClamAV does NOT check macro attachments in Ofiice documents, i.e. the newfangled .locky can safely pass,
you can fix this with one line:
echo'ScanOLE2 true' >> /etc/clamav/clamd.conf
If anyone is interested, then here is the config that we use now
cat /etc/clamav/clamd.conf
#Automatically Generated by clamav-base postinst#To reconfigure clamd run #dpkg-reconfigure clamav-base#Please read /usr/share/doc/clamav-base/README.Debian.gz for details
TCPSocket 3310
# TemporaryDirectory is not set to its default /tmp here to make overriding# the default with environment variables TMPDIR/TMP/TEMP possible
User clamav
AllowSupplementaryGroups true
ScanMail true
ScanArchive true
ArchiveBlockEncrypted false
MaxDirectoryRecursion 15
FollowDirectorySymlinks false
FollowFileSymlinks false
ReadTimeout 180
MaxThreads 12
MaxConnectionQueueLength 15
LogSyslog true
LogRotate true
LogFacility LOG_LOCAL6
LogClean false
LogVerbose false
PidFile /var/run/clamav/clamd.pid
DatabaseDirectory /var/lib/clamav
SelfCheck 3600
Foreground false
Debug false
ScanPE true
MaxEmbeddedPE 10M
ScanOLE2 true
ScanPDF true
ScanHTML true
MaxHTMLNormalize 10M
MaxHTMLNoTags 2M
MaxScriptNormalize 5M
MaxZipTypeRcg 1M
ScanSWF true
DetectBrokenExecutables false
ExitOnOOM false
LeaveTemporaryFiles false
AlgorithmicDetection true
ScanELF true
IdleTimeout 30
PhishingSignatures true
PhishingScanURLs true
PhishingAlwaysBlockSSLMismatch false
PhishingAlwaysBlockCloak false
PartitionIntersection false
DetectPUA false
ScanPartialMessages false
HeuristicScanPrecedence false
StructuredDataDetection false
CommandReadTimeout 5
SendBufTimeout 200
MaxQueue 100
ExtendedDetectionInfo true
OLE2BlockMacros false
ScanOnAccess false
AllowAllMatchScan true
ForceToDisk false
DisableCertCheck false
DisableCache false
MaxScanSize 100M
MaxFileSize 25M
MaxRecursion 10
MaxFiles 10000
MaxPartitions 50
MaxIconsPE 100
StatsEnabled false
StatsPEDisabled true
StatsHostID auto
StatsTimeout 10
StreamMaxLength 25M
LogFile /var/log/clamav/clamav.log
LogTime true
LogFileUnlock false
LogFileMaxSize 0
Bytecode true
BytecodeSecurity TrustSigned
BytecodeTimeout 60000
OfficialDatabaseOnly false
CrossFilesystems true
OnAccessMaxFileSize 25M
In general, two weeks after using and analyzing spam, possible spam, we can say that 98% of spam does not go through.
I will be glad to suggestions, comments and criticism in the comments.
