A bit about the trends in the field of "cloud" security
/ photo Alexandre Dulaunoy CC
Cloud computing is one of the most exciting technologies currently in use. At 1cloud, we constantly monitor the latest news and trends in this area. More recently, we published material on changes in IT infrastructure, and today we would like to look at trends in the field of security.
Three last materials from our blog on Habré:
- How to choose a direction for the development of an IT project
- Technological solutions for data centers
- Friday format: Unusual data center solutions
According to Amit Pandey, CEO of Avi Networks, a wave of cyber attacks will soon sweep the clouds:
“The international cloud resiliency research team is constantly monitoring downtime and evaluating security risks,” says Pandey. - So far there have been no serious threats or problems with the availability of services. However, as more and more businesses begin to outsource their infrastructures, the number of DDoS and other cyber attacks will increase. ”
However, this does not stop people. An increase in the number of cybercriminals in a rapidly developing field is a natural process. The RightScale project regularly explores the cloud market. Since 2013, security was considered an obstacle No. 1 to cloud adaptation, but in 2016 the “palm” was seized by a lack of resources and IT staff expertise. This is due to the fact that people see what work is being done in the field of cloud security, and their fears are gradually dispelling.
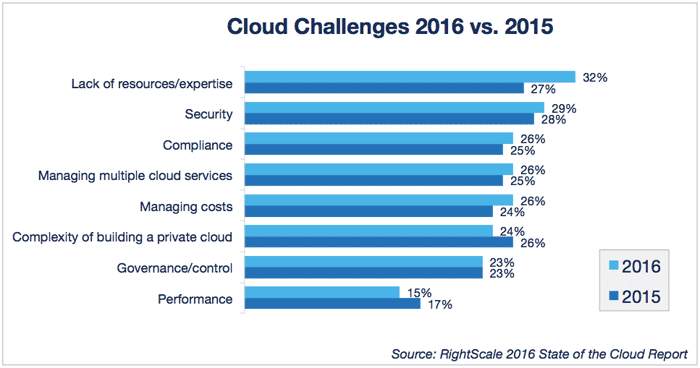
According to RightScale
At a conference of CNews Conferences and CNews Analytics, round-table representatives of vendors, providers and customers discussed vectors for further development of the cloud industry. At the moment, clouds representThey are vertical structures when users, if necessary, turn to a higher data center and receive a response to their request.
According to the experts of the forum, from time to time they should be replaced by horizontal decentralized structures when there is no single data center, and data is transferred from one device to another. For example, the FireChat messenger works by this principle.
In this new paradigm, classic security features will prove ineffective. The firewall will not be able to provide protection, since all important events occur at the borders of the network, and there will be no central verification service for user authentication. Market participants believe that the solution to the problems will be the blockchain technology used in transactions with cryptocurrency.
“Blockchain is a distributed database where all participants in the process are the owners of information and confirm each other,” explains Nikolai Nosov, an RCCPA expert.
The experts also agreed that in the near future, issues of growing traffic and security will be addressed through virtualization of network functions (NFV) and the construction of software-defined networks (SDN). Interop Las-Vegas 2016, also dedicated to network security, supported these trends.
“The proliferation of software-defined networks will impact the modern IT market, as has happened with virtual machines,” said Cameron Camp, security researcher at ESET. “If you have experience working in the field of network security, SDN will open up new possibilities for you.”
The technology of software-defined networks is a logical continuation of the evolution of network technologies, which are increasingly integrated with program management and virtualization .
According to analysts, by 2018 the global SDN market will grow to $ 35 billion, and 40% of all expenses for data networks will be associated with SDN. First of all, software-defined networks will be in demand by service providers and corporate data centers.
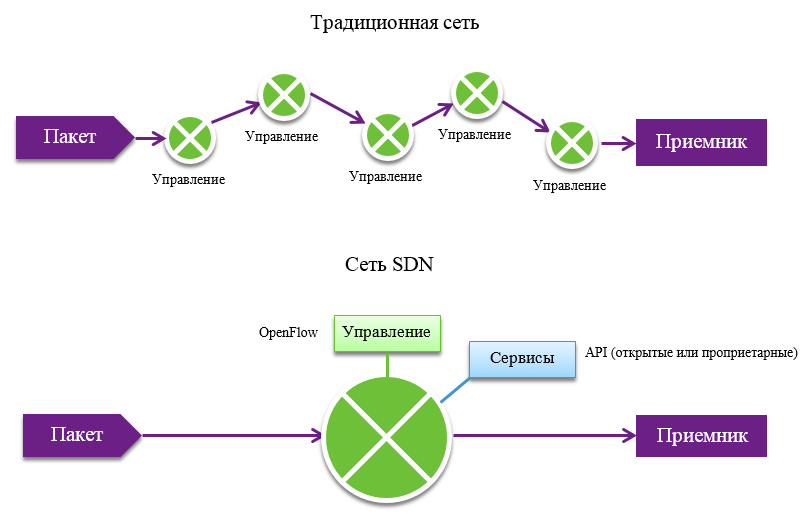
The essence of the SDN is to separate the "control plane" from the "data plane." In traditional switches and routers, these processes are combined and inseparable, and in the case of SDN, control is given to controllers that monitor the status of the entire network. Devices no longer need to know hundreds of protocols - they just need to follow the instructions of the controller, which means saving on hardware stuffing.
Thanks to SDN technology, the company gains vendor-specific control over the network from one place, and administrators can program the network as a whole without spraying efforts on separate devices. Moreover, it will be possible "on the fly" to change the characteristics of the network, which will shorten the deployment time for new applications and services.
On the north side, the controller provides an API that enables developers to create network management applications. Such applications can perform various business tasks: access control, bandwidth management, etc., and their developers do not need to know the details of the operation of specific network devices.
Another topic of discussion at the conference was the VMware NSX network virtualization platform. According to Dom Delfino, VMware’s vice president of networking and information, “Security is the main reason for switching to NSX.”
If an attacker manages to "penetrate" into the network environment, then he gains access to processes and data and is capable of causing serious damage. VMware NSX Software Defined Network Management solves this problem. Each process has its own micro-network environment, which isolates systems operating on the same platform.
Microsegmentation is a good way to counter various kinds of attacks - if an attacker manages to “break through” into the system, he will not be able to go beyond the boundaries of the selected segment. The level of microsegmentation of virtual networks with VMware NSX represents another step towards the adaptation of cloud technologies and solves the problems of security and flexible use of network resources. However, despite all the advantages, today virtualized and SDN-based network security tools are not yet widely distributed.
“These technologies are relatively early stages of development and are the exception rather than the rule,” concludes Dave Lewis, Akamai Security Advisor.
However, there is potential. Considering how intensively these technologies are discussed by conference participants, it can be expected that these solutions will soon take their place in the data center technology stack .
PS A little more about how we improve the performance of the virtual infrastructure provider 1cloud :
