Security Week 46: let's update something
 Sooner or later it happens: you open YouTube on your mobile phone, but instead of a pack of videos you get an offer to be updated urgently. Or finally, find the time to play in the Playstation, but just then flew updates, you download and install them for half an hour, then turn off the console. Or go to the WordPress admin panel to write a brilliant post, but it's time to update WordPress and the plugins.
Sooner or later it happens: you open YouTube on your mobile phone, but instead of a pack of videos you get an offer to be updated urgently. Or finally, find the time to play in the Playstation, but just then flew updates, you download and install them for half an hour, then turn off the console. Or go to the WordPress admin panel to write a brilliant post, but it's time to update WordPress and the plugins. Today's release is about updates of the Android operating system, patches for two plugins in WordPress, in short, about what you have to do if you have a smartphone or a website. Updates for Wordpress plugins are interesting because they show what will happen if you still do not spend time on updating the code.
Vulnerability in WordPress plugin for compliance with the rules of the GDPR
News . Study .
About the GDPR this year we had a separate issue . Strict standards for the protection of private data of EU citizens are useful for users, even from other countries, but for owners of sites and network services they still present a certain headache. Many WordPress site owners solve the issue of compliance with the legislation in the usual way - by installing a plug-in. One of these plugins, WP GDPR Compliance , as it turned out, solves one problem and adds another.
The plugin is quite simple - it adds links to a confidentiality agreement to comments or personal information forms (if you buy something) and tracks the fact that the client has agreed to the processing of personal data. Wordfence specialists found out that plugin version 1.4.2 and older contains a serious vulnerability: input from the user is not verified, and the settings of the WordPress engine itself can be overwritten by the prepared message. The vulnerability was detected in the wake of an active attack on sites with a plug-in installed: unknown persons opened by default closed user registration on the site and assigned new administrator status to all new users.
This opens up full access to the data stored on the site: thus, the plugin to comply with the standards of GDPR potentially leads to problems with this very GDPR. Leakage of user data, according to the law, must be properly handled, and information about the incident should be transmitted to the competent authorities. The attack was discovered because of the inability to cover up traces, although an attempt to clean the logs took place. For this attack scenario, it is not known for what purpose the sites were hacked. Another scenario discovered by Sucuri involved loading data from a specific domain. That site was promptly disabled, so (presumably) the malicious code on the victim sites is not loaded. Instead, the affected sites just slowly, with errors and do not fully open.
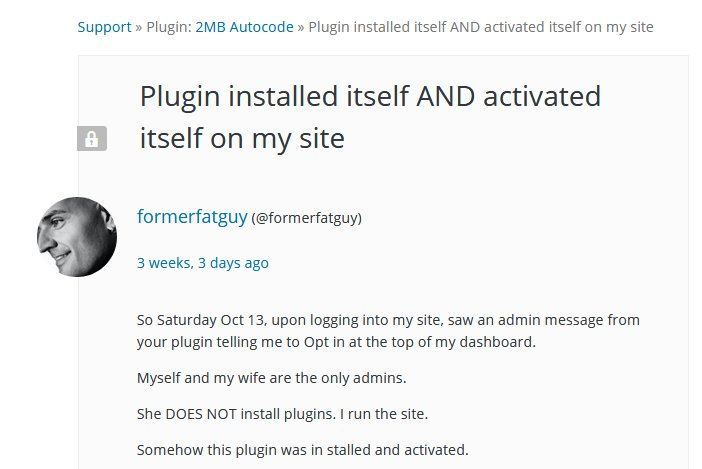
And this is how it looked from the unsuspecting site administrator: you go into the admin area, and there is some new plugin installed (embedding the PHP code in all pages of the site), unknown names in the admin list, and what happens is not clear. In the version of plugin 1.4.3, the vulnerability is eliminated, according to estimates on the WordPress site, it is installed on more than one hundred thousand sites.
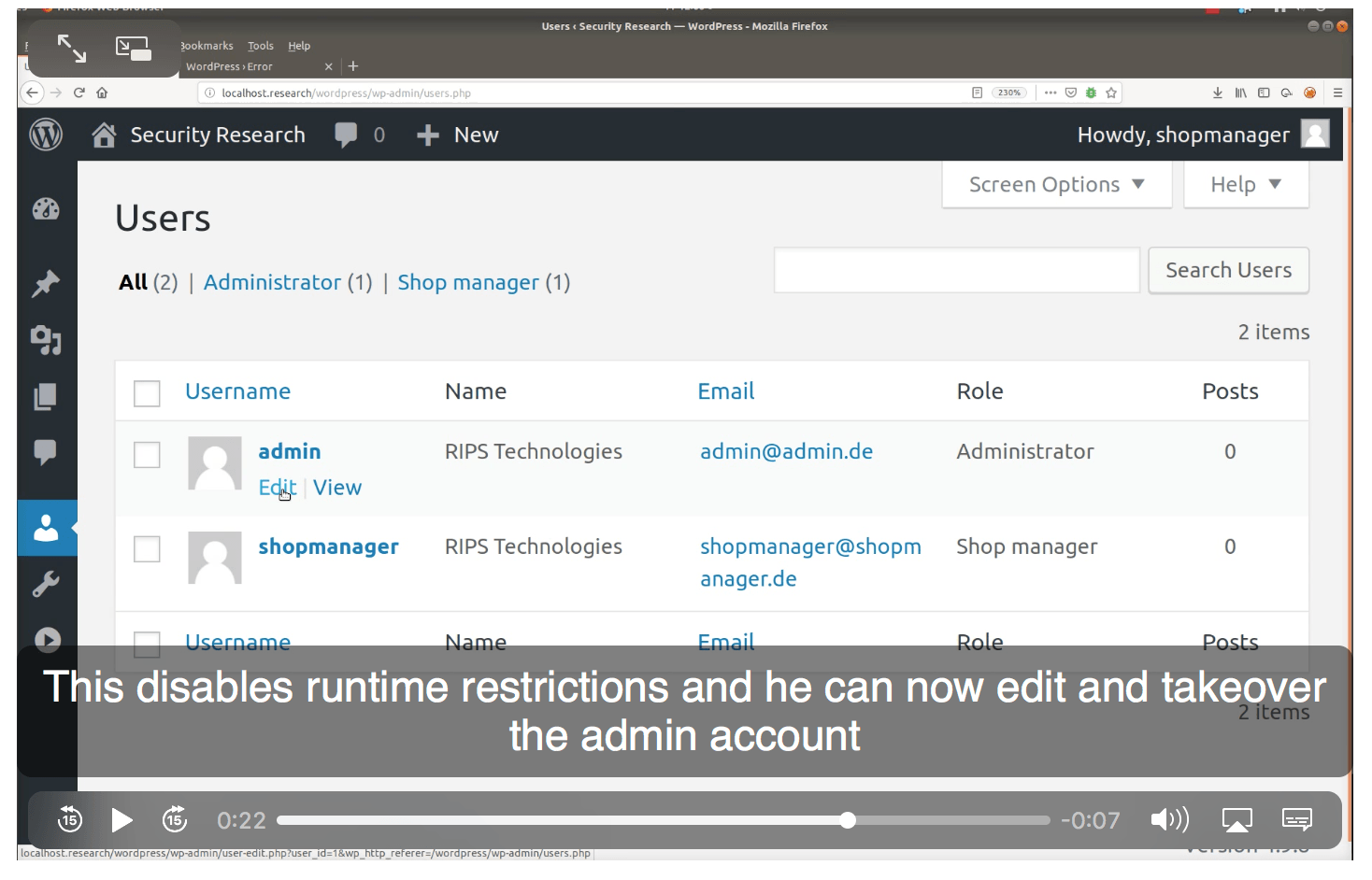
The WP GDPR plugin works with one of the most popular e-Commerce systems for the WordPress platform, known as WooCommerce . It itself was discovered a serious vulnerability ( news ). The platform offers several levels of access to the content of the site, and it is not necessary to be the administrator to manage the store, there is a special role of the Shop Manager. Theoretically, such a manager may be given such administrator rights due to the vulnerability found by the RIPSTech company specialists.
The vulnerability is interesting: the role of the shop manager implies the ability to edit users of lower rank, more precisely, just buyers. This feature was (not without the aid of crutches) integrated with the rights control system of the WordPress platform itself. While the plugin is there, everything works: the role of the shop manager has the ability to edit profiles, and the WooCommerce system specifies that these are only buyers. But if you remove the plugin, it becomes more interesting: the user with the role of shop manager remains a WordPress user, and the rights to edit other profiles are extended to the entire platform, including the site administrators.

Thus, the attack is carried out in two stages: one tear in the security allows the disgruntled working condition manager to remove the WooCommerce plugin. The second gives you the opportunity to get admin rights; however, if the plug-in online store is demolished, then the attacker becomes the administrator of an almost empty site. According to WordPress, the WooCommerce plugin is installed on more than 4 million sites, and this is one third of the total e-commerce network. The vulnerability was closed in October, and the latest versions of the WooCommerce plugin are not affected.
Android update closes seven critical vulnerabilities
News . November Android Security Bulletin .
WordPress plugins updated, it's time to update Android. In the next set of patches from the fifth November in the Android code, seven critical vulnerabilities are closed. Four of them were found in the Media Framework component - in the same place where the well-known StageFright vulnerability was found three years ago . They enable the remote execution of arbitrary code when opening a website with a “prepared” media element. Three more critical vulnerabilities have been discovered in the Qualcomm closed code. Google does not disclose detailed information about them, expecting the equipment supplier to do this. In addition, 18 vulnerabilities are closed in the libxaac library - an experimental module for compressing and decoding media content, which it was decided not to include in the main Android code base anymore.
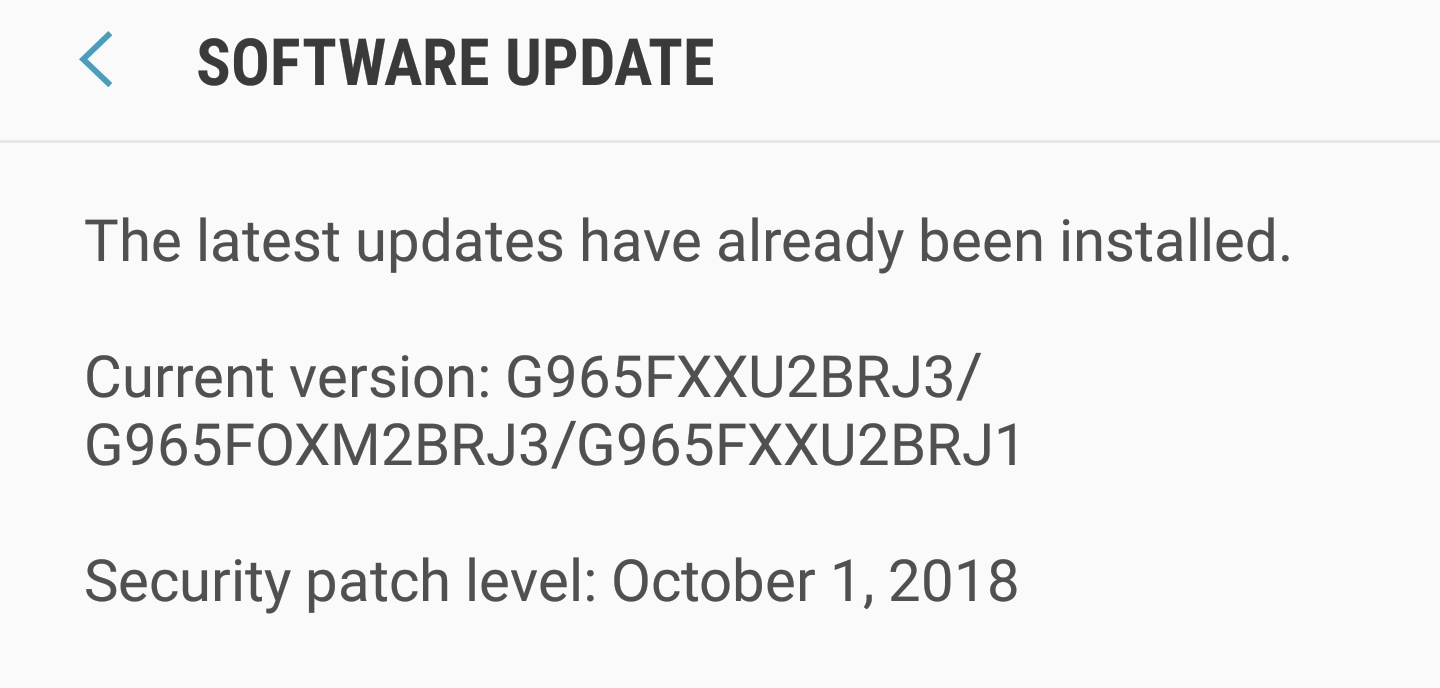
Updates close problems mainly in the latest (ninth) version of Android, but a number of vulnerabilities, including one critical vulnerability in the Media Framework, have been patched for earlier versions of the OS, starting with the seventh. Manufacturers of smartphones receive information about upcoming patches a month before the public release in order to prepare an update update in advance. But, as can be seen from the screenshot above, during the week the update was not delivered to all supported smartphones.
We are waiting and updating.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
