UniFi Controller Password Reset
- Tutorial
Like any system administrator who was convinced that his own memory was perfect and his ability to remember the 25-digit Windows XP installation code in the middle of the night, I recently caught this exception.
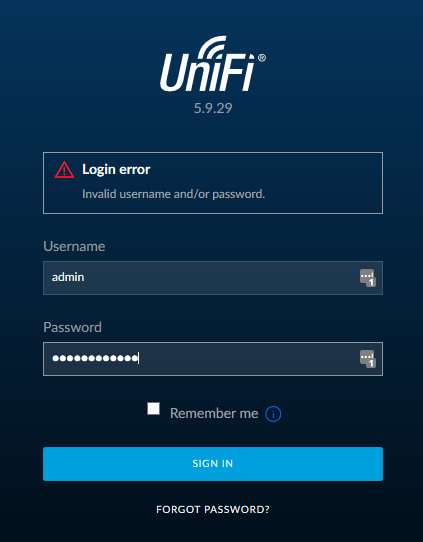
One fine day, having decided to come to check what was there with my UniFi controller, I received an amazing message: Login error.
I scratched my head and remembered how at one moment I forgot the pin-code from the card, which was stuffed purely mechanically, and began to sort through the possible options. After half an hour of attempts, searching for notes in a notebook, reviewing sclerotosus glued to the monitor, I realized that I had to look for workarounds.
Immediately make a reservation for lovers of criticism - account / password manager, ala LastPass, is used. As a matter of fact, LastPass is used. And the data from there did not contribute to successful authentication.
Having searched the bourgeois forums, the necessary information for resetting the password from any account in the controller was obtained, comprehended, digested and collected in a brief memo.
So, it is given:
1. UniFi controller (does not play the role of the OS - Linux or Windows) with access to the OS itself.
2. Internet access.
3. Straight arms.
UniFi controller stores all configuration in Mongo database.
Check if we need information on the account we are looking for:
In this particular case, we request information for the admin account .
If you are looking for uchetki VasyaPupkin query would look as follows:
Exhaust we get about the following:
Field of interest to us:
Afteranalyzing google, we learn that the encryption algorithm is SHA-512 crypt (3) compatible.
Oops. We postpone the idea of decrypt to the far shelf and go the other way.
We have access to the database, so we just need a hash of a known password. And to update the record in the database is something simple.
We go to:
Select the desired algorithm, enter the password that we will use:

Press the magic Blue button:

The resulting hash is carefully copied, then we will need it.
And now it is time for the final step:
Drum roll ... Press Enter.
Go to the UniFi controller's authentication page, enter the username: admin (we also changed the password for it), enter the password for which the hash was generated.
And, voila, everything works, there is access, everyone is happy and dancing.
One fine day, having decided to come to check what was there with my UniFi controller, I received an amazing message: Login error.

I scratched my head and remembered how at one moment I forgot the pin-code from the card, which was stuffed purely mechanically, and began to sort through the possible options. After half an hour of attempts, searching for notes in a notebook, reviewing sclerotosus glued to the monitor, I realized that I had to look for workarounds.
Immediately make a reservation for lovers of criticism - account / password manager, ala LastPass, is used. As a matter of fact, LastPass is used. And the data from there did not contribute to successful authentication.
Having searched the bourgeois forums, the necessary information for resetting the password from any account in the controller was obtained, comprehended, digested and collected in a brief memo.
So, it is given:
1. UniFi controller (does not play the role of the OS - Linux or Windows) with access to the OS itself.
2. Internet access.
3. Straight arms.
UniFi controller stores all configuration in Mongo database.
Check if we need information on the account we are looking for:
mongo --port 27117 ace --eval'db.admin.find().forEach(printjson);'In this particular case, we request information for the admin account .
If you are looking for uchetki VasyaPupkin query would look as follows:
mongo --port 27117 ace --eval'db.VasyaPupkin.find().forEach(printjson);'Exhaust we get about the following:
MongoDB shell version: 2.6.12
connecting to: 127.0.0.1:27117/ace
{
"_id" : ObjectId("567bfd4fe4b0c81300ff3158"),
"email" : "admin@company.com",
"email_alert_enabled" : true,
"email_alert_grouping_enabled" : true,
"html_email_enabled" : true,
"is_professional_installer" : false,
"last_site_name" : "default",
"name" : "admin",
"requires_new_password" : false,
"time_created" : NumberLong(1450966351),
"ui_settings" : {
"dashboardConfig" : {
"dashboards" : {
"5b4c57aadc236c7de53e3c3c" : {
"order" : 1
}
},
"lastActiveDashboardId" : "5b4c57aadc236c7de53e3c3c"
},
"statisticsPreferBps" : true
},
"x_shadow" : "$6$0YiSt9dQ$YrNKedOCjOP2xl3y9FhRasafdhbdfadamBKIjZ4l9Mm4cy/m49dt0bN.sYaFvgVb5vce45KypFe07iNYc1"
}Field of interest to us:
x_shadow" : "$6$0YiSt9dQ$YrNKedOCjOP2xl3y9FhRasafdhbdfadamBKIjZ4l9Mm4cy/m49dt0bN.sYaFvgVb5vce45KypFe07iNYc1"After
Oops. We postpone the idea of decrypt to the far shelf and go the other way.
We have access to the database, so we just need a hash of a known password. And to update the record in the database is something simple.
We go to:
Select the desired algorithm, enter the password that we will use:

Press the magic Blue button:

The resulting hash is carefully copied, then we will need it.
And now it is time for the final step:
admin.mongo --port 27117 ace --eval'db.admin.update({name:"admin"},{$set:{x_shadow:"$6$ee74396ce4c563de$oLm93BwJywYo1sUFgX8U0FC.p75t1Jv838.0defRCe36jgX6PU3h.m3NL6tjCs8Q/1Ymtge0DXz9shb//dyEN."}})'Drum roll ... Press Enter.
MongoDB shell version: 2.6.12
connecting to: 127.0.0.1:27117/ace
WriteResult({ "nMatched" : 1, "nUpserted" : 0, "nModified" : 1 })Go to the UniFi controller's authentication page, enter the username: admin (we also changed the password for it), enter the password for which the hash was generated.
And, voila, everything works, there is access, everyone is happy and dancing.
