Gozi bot source code leaked online
Subj, the Gozi ISFB bot source package (aka Ursnif) is published in the public domain and is available to everyone. The malicious program Ursnif is a fairly serious tool for working with http and https traffic on the victim’s computer; it contains 32-bit and 64-bit payload components for embedding them into various working processes of such web browsers as Google Chrome, Microsoft Internet Explorer , Mozilla Firefox, and the preferred Services Manager process manager Services.exe.

Ursnif began to be actively used by cybercriminals five years ago, and its very first versions were released back in 2008. Attackers actively used the Blackhole exploit kit to distribute Trojan droppers. We recently wrotethat the author of Blackhole himself received seven years in prison. Gozi or Ursnif was used by attackers as a thief of various information on the victim’s system, including credentials of services such as FTP, Telnet, POP3, and IMAP.
The source code contains a fairly detailed description of the functions performed by the bot, as well as the purpose of its various components and files. Operators control Ursnif through a C&C server command, passing appropriate instructions to it. The configuration files and command sets sent to the bot are signed using the asymmetric RSA algorithm. In case of incorrect signature of such files, the bot discards the data sent to it.

Fig. Information about the Ursnif project part from the Readme file.
The bot uses encryption of dropper files, as well as DLL files used as a payload, which complicates their analysis by antivirus analysts. An example is the following Gozi files. Link
dropper file . Decrypted dropper body link . Extracted 32-bit DLL link file . The extracted file is a 64-bit DLL link . Gozi uses the following trusted registry key to register the payload HKLM \ System \ CurrentControlSet \ Session Manager \ AppCertDlls. It also intercepts a number of system functions of various Windows libraries to gain control over system functions:
Since Gozi is embedded in the Windows Explorer process, it can control the creation of all the processes of interest from there, including the aforementioned web browsers by intercepting the CreateProcess and CreateProcessAsUser functions . An example of such an interception is shown below in the figure.

Fig. Part of the source code for the kernel32! CreateProcess interception function . The presence of the _KERNEL_MODE_INJECT macro indicates a possible rootkit component of the bot.
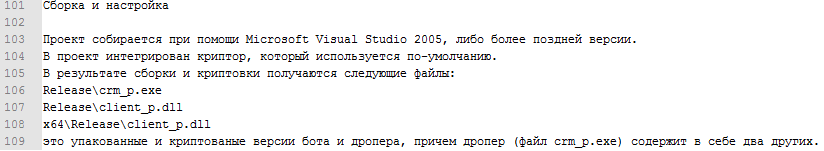
Fig. Information about the assembly of the project.
According to IBM Security researchers, a hybrid of this malware with the Nymaim Trojan has already been created on the basis of Gozi sources, more about this can be found here . ESET antivirus products detect Gozi asWin32 / PSW.Papras .

Ursnif began to be actively used by cybercriminals five years ago, and its very first versions were released back in 2008. Attackers actively used the Blackhole exploit kit to distribute Trojan droppers. We recently wrotethat the author of Blackhole himself received seven years in prison. Gozi or Ursnif was used by attackers as a thief of various information on the victim’s system, including credentials of services such as FTP, Telnet, POP3, and IMAP.
The source code contains a fairly detailed description of the functions performed by the bot, as well as the purpose of its various components and files. Operators control Ursnif through a C&C server command, passing appropriate instructions to it. The configuration files and command sets sent to the bot are signed using the asymmetric RSA algorithm. In case of incorrect signature of such files, the bot discards the data sent to it.

Fig. Information about the Ursnif project part from the Readme file.
The bot uses encryption of dropper files, as well as DLL files used as a payload, which complicates their analysis by antivirus analysts. An example is the following Gozi files. Link
dropper file . Decrypted dropper body link . Extracted 32-bit DLL link file . The extracted file is a 64-bit DLL link . Gozi uses the following trusted registry key to register the payload HKLM \ System \ CurrentControlSet \ Session Manager \ AppCertDlls. It also intercepts a number of system functions of various Windows libraries to gain control over system functions:
- CreateProcessAsUser (A / W)
- CreateProcess (A / W)
- CryptGetUserKey
- InternetReadFile
- HttpSendRequest (A / W)
- InternetReadFileEx (A / W)
- InternetCloseHandle
- InternetQueryDataAvailable
Since Gozi is embedded in the Windows Explorer process, it can control the creation of all the processes of interest from there, including the aforementioned web browsers by intercepting the CreateProcess and CreateProcessAsUser functions . An example of such an interception is shown below in the figure.

Fig. Part of the source code for the kernel32! CreateProcess interception function . The presence of the _KERNEL_MODE_INJECT macro indicates a possible rootkit component of the bot.

Fig. Information about the assembly of the project.
According to IBM Security researchers, a hybrid of this malware with the Nymaim Trojan has already been created on the basis of Gozi sources, more about this can be found here . ESET antivirus products detect Gozi asWin32 / PSW.Papras .
