Why Wi-Fi will not work as planned, and why know which employee uses the phone

Hello!
Let's talk about what really affects the speed of data transmission in modern wireless networks, debunk a couple of myths and answer if it's time to change your old router to a sparkling horned alien with MU-MIMO on board.
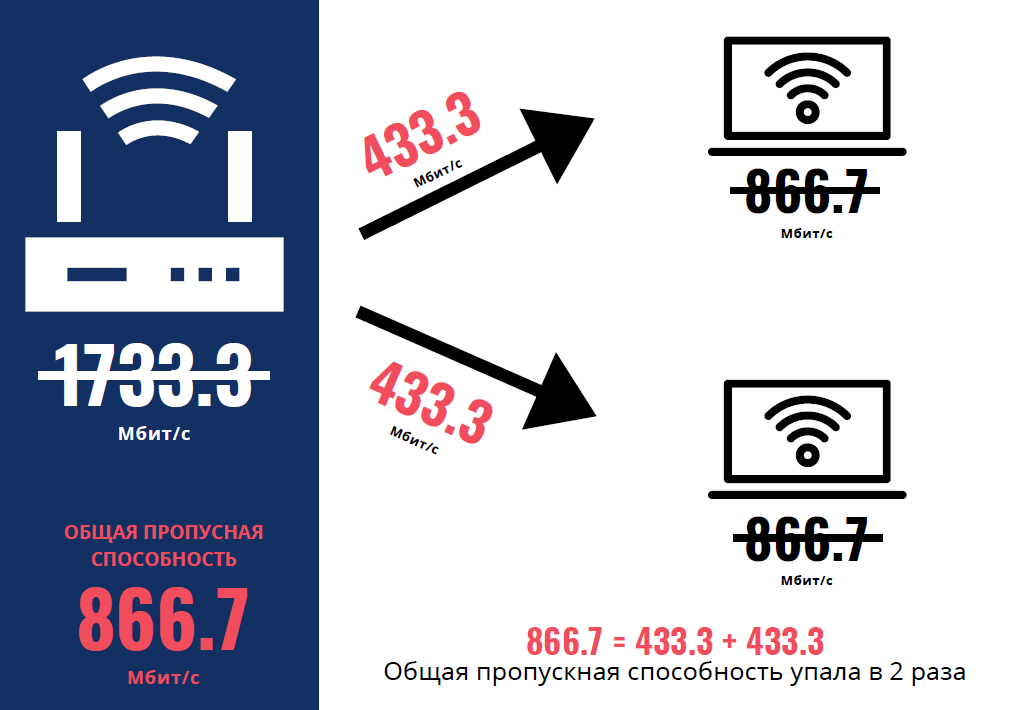
To warm up - a small task. Imagine a wireless Wi-Fi network consisting of an access point (AP) and two identical client devices (STA1 and STA2).
We read the inscriptions on the boxes:
AP: 1733.3 Mbit / c
STA1, STA2: 866.7 Mbit / c
Attention, question. Both clients simultaneously start downloading a large file from the server. What bandwidth can each device count on?
Immediately make a reservation - for simplicity and clarity, we will call the bandwidth (channel speed) simply speed . Yes, the speed of the transport layer protocols may be two times lower than our speed , but you already know all this. Now about the other.
Our task is designed to remind you of the main limitation of wireless networks.
The shared transmission medium (shared medium) implies that only one device should broadcast per unit of time.
This circumstance leads us to a counterintuitive answer: in spite of the fact that the access point is capable of supporting 1733.3 Mbit / s, each of the devices will work, on average, at a speed of 433.3 Mbit / s.
Where are the remaining 866.7 Mbit / c? Let's figure it out.
To describe the principles of wireless networks, it is convenient to use the Airtime Utilization metric. It shows how much time the broadcast is busy transmitting data.
Now - attention! In order to develop the claimed 1733.3 Mbit / s, the device must solely take over the air 100% of the time. In this case, the second device (the receiver) must also maintain this speed.
We emphasize once again - the connection between devices that support different speeds, is carried out at the speed of the least rapid of the pair.
Everything becomes sadder if the maximum of the device, for example, 72.2 Mbit / s. It will take the same 100% ether, but the result is not impressive at all.
By the way, 72.2 Mbit / s - the speed is not random. Most modern smartphones can not count on more, but more on that later.
Now back to STA1 and STA2. Under the terms, they started uploading the file to the server at the same time. We remember that only one device can broadcast per unit of time.
Coordinates the transfer on the Wi-Fi network mechanism CSMA / CA - Carrier Sense Multiple Access with Collision Avoidance. In short, his task is to consistently give the right to vote to all devices, while, if possible, not allowing simultaneous transmission from two or more devices (collisions).
You can read Wikipedia , if you want more details.
And better is . Or - here , if you are very serious.
And here Airtime Utilization? And despite the fact that as a result of CSMA / CA for this case, each of the two ready-to-transmit client devices will receive about half of the airtime for their needs - or 50% of Airtime.
100% Airtime - 866.7 Mbit / s;
50% Airtime - 433.3 Mbit / s for each device.
This picture will not change, even if the access point will support all 6933.3 Mbit / s. The connection between the AP and the STA is always limited by the speed of the least fast device.
Out of curiosity, you can slightly play
around with the conditions of the problem: Change the speed for STA2 - 72.2 Mbit / s;
Add STA3, speed - 72.2 Mbit / s.
What remains of the claimed 1733.3 Mbit / c?

Important clarification №1
In fairness, we add that these calculations are correct when the Airtime Fairness functionality is enabled on the BS , everything would have been much worse without it - slow client devices would lead to the most inefficient distribution of Airtime. It’s good that the technology was implemented by almost all self-respecting vendors.
But there is a nuance here: Airtime Fairness only works in Downlink (from AP to STA). Anarchy still prevails in Uplink.
Important clarification number 2
Due to the workload of the air, collisions and peculiarities of the protocol operation, the maximum achievable level of Airtime Utilization is in the range from 70% to 80% in a real network.
The speed we calculated will change accordingly.
Why so long prelude? Know which client devices are used on your network. Their impact on performance in a shared data environment is critically underestimated. Next, we will understand - as far as.
Part 1 - Customers are to blame
Or client devices, if you like. What are they guilty and what, in fact, distinguishes them from access points?

It's simple. Most often, customers are compact, autonomous and mobile. All problems arise from this.
Stylish metal case with a thickness of 7 mm? To accommodate 4 radio paths MIMO is better than that.
Is multi-threaded data transfer and wide channels too energy consuming? Nothing, let the device charge several times a day.
Are customers constantly moving? Nonsense - unscrew the power points to the maximum.
In such circumstances, developers are forced to compromise.
Remember the powerful access point (1733 Mbit / s) from the introduction to the article? Let's go even further. The 802.11ac standard allows us to accelerate to an impressive 6933 Mbit / s.
The conditions for this are as follows:
- 5 GHz;
- 8 spatial streams (MIMO 8x8: 8);
- 160 MHz - channel width;
- 256QAM - modulation.
Corresponding access points on the market are represented even in the consumer segment. What about customers?
For clarity, we will conduct a mental experiment: connect to our abstract point a very specific smartphone - iPhone 8. Let's see what it can do.
2.4 GHz vs 5 GHz
Long-term observations confirm - the devices working in the "five", more and more. And it is beautiful.
The only advantage of 2.4 GHz - less attenuation - today has become almost a disadvantage.
When designing dense networks, one of the tasks is the fight against interference. We struggle, among other things, by isolating the AP coverage zones from each other. Walls are used, power on the transmitter is lowered, and the “range” of the two is clearly superfluous.
One way or another, the future of Wi-Fi is behind the “top five”, if you don’t even consider the very narrow cases.
Statistics, however, does not give unambiguously reliable data on the distribution of devices - too many variables (country, region, location, event, and others).
Perhaps today we can be careful to say that in Russia we have reached the 50/50 ratio of support in client devices in the 5 GHz band.
How will your network - another question.
Our imaginary iPhone 8, by the way, supports the "top five", well, well.
MIMO
The ability to simultaneously transmit multiple data streams in a single frequency channel appeared back in 802.11n. However, things are still there:
- MIMO 8x8: 8 clients do not yet support. Quite;
- The almost complete absence of client devices with MIMO 4x4: 4 - see the comment below;
- Top laptops that support MIMO 3x3: 3;
- Top smartphones and tablets that support MIMO 2x2: 2;
- The absolute majority of devices are SISO 1x1: 1.
And all because MIMO technology is very demanding:

MIMO, SISO - what is it, anyway? And what are the numbers?
SISO (Single Input Single Output) — устройства с одним входным и одним выходным трактами. С них всё начиналось.
MIMO (Multiple Input Multiple Output) — соответственно, множественные входные и выходные каскады. Благодаря MIMO, появилась возможность передавать в одном частотном канале несколько полезных сигналов.
MIMO 4x4:4 значит [4 передающих тракта]x[4 приёмных тракта]:[4 пространственных потока].
MIMO 4x4:3 — бывает.
MIMO 3x3:4 — не бывает.
Точка доступа с MIMO 4x4:4 позволяет, по сути, увеличить скорость передачи данных в 4 раза. Разумеется, если оба устройства (ТД и клиент) обладают равными способностями.
MIMO (Multiple Input Multiple Output) — соответственно, множественные входные и выходные каскады. Благодаря MIMO, появилась возможность передавать в одном частотном канале несколько полезных сигналов.
MIMO 4x4:4 значит [4 передающих тракта]x[4 приёмных тракта]:[4 пространственных потока].
MIMO 4x4:3 — бывает.
MIMO 3x3:4 — не бывает.
Точка доступа с MIMO 4x4:4 позволяет, по сути, увеличить скорость передачи данных в 4 раза. Разумеется, если оба устройства (ТД и клиент) обладают равными способностями.
Client devices with MIMO 4x4: 4 began to appear on the market recently. Basically, these are dedicated Wi-Fi adapters, but Samsung recently stunned us, stating in the description for its new Galaxy Note 9 - MIMO 4x4. Very inappropriate, because we wanted to write that there are no mobile devices with similar characteristics on the market yet.
In this regard - the competition.
Conditions
Нам нужен Association Request от Galaxy Note 9 (или любого другого смартфона), подтверждающий поддержку передачи четырёх пространственных потоков. Первый приславший на wireless@comptek.ru PCAP-файл, содержащий указанный фрейм, получит отличный подарок от CompTek.
Важное условие — снять трафик нужно самостоятельно. Можем попросить фото устройства :)
Важное условие — снять трафик нужно самостоятельно. Можем попросить фото устройства :)
As they say - exceptions confirm the rule.
Devices with MIMO 4x4: 4 - almost none. MIMO 3x3: 3 - the lot of rare Macbook Pro. MIMO 2x2: 2 - in top smartphones and tablets. The statistical majority is devices that do not support MIMO.
We will not be like most. Our iPhone 8 is a top-end smartphone that supports the transfer of two spatial streams.
How did we know this - an important question. We will tell in the last part of the article.
As we remember, the connection between devices that support different speeds, is carried out at the speed of the least rapid of the pair.
Out - and there are 1733.3 Mbit / s. It's sad. But fun is almost two gigabytes!
Maths
В случае с пространственными потоками (Spatial Streams) всё просто.
Их число — это множитель.
Берём базовую скорость для SISO (с учётом ширины канала) и умножаем на число пространственных потоков (SS).
6933 ~ 866.7×8 (SS=8)
1733.3 ~ 866.7×2 (SS=2)
Если лень считать — просто воспользуйтесь таблицей.
Их число — это множитель.
Берём базовую скорость для SISO (с учётом ширины канала) и умножаем на число пространственных потоков (SS).
6933 ~ 866.7×8 (SS=8)
1733.3 ~ 866.7×2 (SS=2)
Если лень считать — просто воспользуйтесь таблицей.
Channel width
802.11ac allows us to use 160 MHz channels.
Please, do not do that.
Moreover, 80 MHz channels are also strongly discouraged.
Again:

The thing is that by expanding the band, we, in fact, open the gates for the interference of all stripes - we spoil the air both for ourselves and our neighbors.
We will not analyze in detail why this is happening - it pulls into a separate article, however you can independently read the recommendations and Best practice guides of leading vendors - only 20 MHz, with rare exceptions.
40 MHz is allowed only in the “top five”, in case the density of clients and the situation on the air allows.
But we are optimists, we will assume that our network is just that.
So, from 1733.3 Mbit / s there is 400 Mbit / s - for a 40 MHz channel.
Maths
С шириной канала немного интереснее. Множители следующие:
×2.1 (40 МГц)
×4.5 (80 МГц)
×9.0 (160 МГц)
За базовую скорость можете взять 96,3 Мбит/c (20 МГц, 1SS, Short Guard interval, 5/6 coding rate).
1733.3 ~ 96.3×9×2 (160 МГц, 2SS)
400 ~ 96.3×2.1×2 (40 МГц, 2SS)
Нелинейные коэффициенты — потому что при объединение каналов удаётся задействовать служебные пограничные OFDM-поднесущие.
Жаль, что в реальной сети вреда от широких каналов больше чем пользы.
Не забываем про удобную таблицу.
×2.1 (40 МГц)
×4.5 (80 МГц)
×9.0 (160 МГц)
За базовую скорость можете взять 96,3 Мбит/c (20 МГц, 1SS, Short Guard interval, 5/6 coding rate).
1733.3 ~ 96.3×9×2 (160 МГц, 2SS)
400 ~ 96.3×2.1×2 (40 МГц, 2SS)
Нелинейные коэффициенты — потому что при объединение каналов удаётся задействовать служебные пограничные OFDM-поднесущие.
Жаль, что в реальной сети вреда от широких каналов больше чем пользы.
Не забываем про удобную таблицу.
Ok, not so impressive anymore, but still not bad, right?
PS: If you live in the forest and know very well what you are doing, well, turn on 160 MHz. Not the fact that there will be a sense. For example, the notorious iPhone 8 does not support this channel width, although it was released only a year ago.
Read to the end to find out what your device is capable of.
Modulation
A curious fact: client devices are the main sources of interference in the network.
What is it for? And the fact that even a perfectly planned and tuned network does not guarantee work on maximum modulations, because 256QAM places very high demands on the signal quality - RSSI and SNR.
We'll talk more about RSSI, and SNR directly suffers from clients with omnidirectional antennas - such mobile and unpredictable. Well, and not only from them, of course.
As a result - count that used on most of the time customers will use less demanding modulation. For example, 64QAM.
In our experiment, this mercilessly reduces the speed to 300 Mbit / s.
Maths
Зачем вам всё это? Просто воспользуйтесь таблицей.
As for RSSI, this is our favorite option. In the 802.11 standard, there are no descriptions and requirements for it, so each vendor sees this metric in its own way. Accordingly, different client devices will display different RSSI in the same place.
By the way, what level are you planning? -67 dBm? And for which device?
But that's not all.
Оказывается, разные устройства одной модели могут по разному оценивать уровень приёма.
Для тех, кто готов во всём идти до конца — пугающий подкаст.
А вот сайт, где можно полюбоваться на собранные по теме данные.
Для тех, кто готов во всём идти до конца — пугающий подкаст.
А вот сайт, где можно полюбоваться на собранные по теме данные.
Subtotal number 1
Even with a very optimistic scenario, the client will receive only 300 Mbit / s bandwidth - instead of 6933 Mbit / s. And this is the case if there is only one client! Do you know many such networks?
We remember puzzles. The more customers, the worse. Did not want to upset ahead of time, but the relationship is nonlinear. With the increase in the number of devices in the network, the percentage of overheads increases.
Here is the rule that the respected Devin Akin suggests using in his article on real Wi-Fi bandwidth.
Статья очень хорошая. Обязательно прочитайте.
- Один клиент: пропускная способность = 0,5 × (MCS rate);
- Небольшое количество клиентов: пропускная способность на одно устройство = 0,45 × (MCS rate) / (количество пользователей);
- Большое количество клиентов, высокие нагрузки на сеть: пропускная способность на одно устройство = 0,4 × (MCS rate) / (количество пользователей);
Статья очень хорошая. Обязательно прочитайте.
Bottom line: performance is highly dependent on the connected clients. Most likely, their abilities will be very limited.
Optimistic scenario — 300 Mbit / s (5 GHz, 40 MHz, 2SS, 64QAM).
Realistic scenario - 72 Mbit / s (2.4 or 5 GHz, 20 MHz, 1SS, 64QAM).
Part 2 - What else is wrong with client devices
Yes, everything is just beginning.
There are three major problems:
- Manifold;
- Unpredictability;
- Vulnerability.
Let's look at them in more detail.
Manifold
Remember our iPhone 8? Good phone, by the way. Do you know that Apple has stopped receiving certification of the Wi-Fi Alliance since the iPhone 6?
You can check it yourself - the information is open. . At the same time write in the comments about other amazing discoveries.
What, in fact, for the organization - Wi-Fi Alliance?
The guys are trying to keep order in the zoo. The Wi-Fi Certified icon means that the device has been tested for compliance with the main points of the 802.11 standard. Verification is carried out in accredited laboratories, more or less seriously.
Why did this need arise?
In order to ensure compatibility with millions of various devices, working on different chipsets and developed by people with different degrees of qualification and moral guidelines.
Helped?
Not really. As practice shows, each vendor has its own unique vision and allows itself to deviate from the standard (well-meaning, of course).
One of the funniest examples is last year's KRACK. Not all devices were vulnerable, since many manufacturers interpreted the key exchange procedure in their own way. In particular, how to behave in the absence of a response to the third message of the 4-Way Handshake sequence. Read more if interested.
What is the result?
Zoo.
The easiest, for obvious reasons, with Apple. Although they do not certify their new products, the fleet of devices is still limited. Therefore, you can test the behavior in certain scenarios.
Next comes Android. Here a lot depends on the manufacturer, but in general - even more unknowns. Add the Chinese here.
This classification ideas end. Operating systems, drivers, legacy devices, multicookers, door locks, security cameras - BYOD and IoT in all its glory.
The problem is aggravated by the fact that many critical decisions are made by client devices on their own, and you cannot directly influence them.
Connect to the "five" or "two"?
Roam or stay on old AP?
What modulation to work on?
More on this in the next chapter.
Unpredictability
Wi-Fi is designed so that client devices are trying to cope with the difficulties that arise. These solutions are not always optimal.
If it seems to the device that it is better to sit on the sixth channel with the level of –85 dBm, than to reconnect to the neighboring point with the level of –50 dBm working in the free “five” - then this will be the case.
There are no effective mechanisms for directly controlling the behavior of client devices. This is the difference, for example, from cellular communication.
Would you mind - what about 802.11k (Radio resource measurement enchancements) and 802.11v (Wireless network management), adopted in 2008 and 2011, respectively?
These standards are theoretically aimed at solving the problem. Practically nothing works.
Yes, the point can send a Load Balancing Request - politely ask the client to make roaming. No one is obliged to satisfy this request. Moreover, there are still very few customers that support 802.11k and v.
The main application of the standards described above is the assistance in fast roaming of the 802.11r mechanism (Fast BSS transition). The client receives a list of the nearest APs to which he should reconnect — and the extravagant device already decides that it is better for him.
About roaming many copies are broken, good articles can be found here, on Habré.
Time. Two.
There is also a monumental (but unfinished) study of the beautiful Andrew von Nagy -
three.
We will not repeat, just emphasize once again: switching between APs is on the client’s conscience. From this and most problems.
Vendors are trying to deal with customer autonomy. Standard tools do not help, so the tricks are used. It is just like in business books: do not try to convince - make sure that the client himself comes to the right choice.
For example, Band Steering works (the mechanism for transferring customers from the “two” to the looser “five”):
- The device is trying to connect to the network. Most likely, it will be exactly 2.4 GHz: it seems to the device driver that it would be better this way - see what a strong signal!
- The AP checks if the device supports 5 GHz. The smart system constantly keeps records of all MAC addresses from which requests were sent or were connected to the “five” earlier;
- DualBand clients (supporting both bands) simply do not receive a response to their request in the 2.4 GHz band;
- This happens several times in a row, and eventually the frustrated driver decides to look for a better share in another range;
- Voila!
Unfortunately, some devices are very stubborn. The conviction does not work, and they continue to cling to the selected range until the point gives up and confirms the connection.
You have to give up, because otherwise you can run into an unexpected effect - a rejected and annoyed customer simply marks this SSID as unreliable and stops connecting automatically to the network (earlier Apple devices were noticed for this behavior, for example).
The list is endless:
- Unexpected and very sound sleep (features of the implementation of PowerSave);
- Work on modulations that clearly do not meet the conditions of the ether;
- Unauthorized traffic coloring (QoS);
- Specific development of scenarios on authorization portals (were there any problems connecting to Wi-Fi in public places?).
Let's fix: it is impossible to directly manage the solutions of client device drivers. Existing mechanisms allow only indirectly motivate customers to make the right choice. The client is not always right, but he does not care.
Vulnerability
As you know, the security of the system as a whole is at the level of the weakest of its elements. In a properly configured wireless network, the client device inevitably becomes such an element. What is the problem?
- There are no or limited resources to control and counteract suspicious activity;
- Security policy updates are unavailable or appear late;
- Manufacturers comply with the requirements of the standard selectively, there is no universality;
- Legacy devices do not meet current security requirements;
- Administrators have no control over client devices;
- People — device users — are vulnerable to social engineering.
Below are examples of solutions used in corporate networks:
- Ban BYOD. Employees are given devices with pre-installed software, the administrator controls the security policies;
- MDM (Mobile Device Management), NAC (Network Access Control) and other solutions that allow, with varying degrees of efficiency, monitor customer devices. You can, for example, remotely prohibit the use of the camera on a smartphone.
Regular users often neglect security problems altogether.
The topic of wireless security is extensive. In this article, we limit ourselves to the fact that the main attack vector of cybercriminals is the so-called low hanging fruit. Most often, the client device becomes such a fruit.

Why try to directly get into a secure network, if it is enough to get access to the employee’s smartphone, which, from pride, does not install updates on its OS?
Subtotal number 2
These problems (diversity, unpredictability and vulnerability of client devices) pose a serious challenge to designers and wireless network administrators.
Perfect planning, high-grade radio survey and high-quality installation do not guarantee stable network operation.
To know what devices subscribers use is really important. It remains to understand what characteristics this or that device possesses.
Suddenly - this is not the easiest task.
Part 3 - Manufacturers are hiding something
Method 1. Logical
It would seem that it can be easier - go to the manufacturer's website and look at the detailed specifications of the devices.
Let's try on the example of the usual iPhone 8:
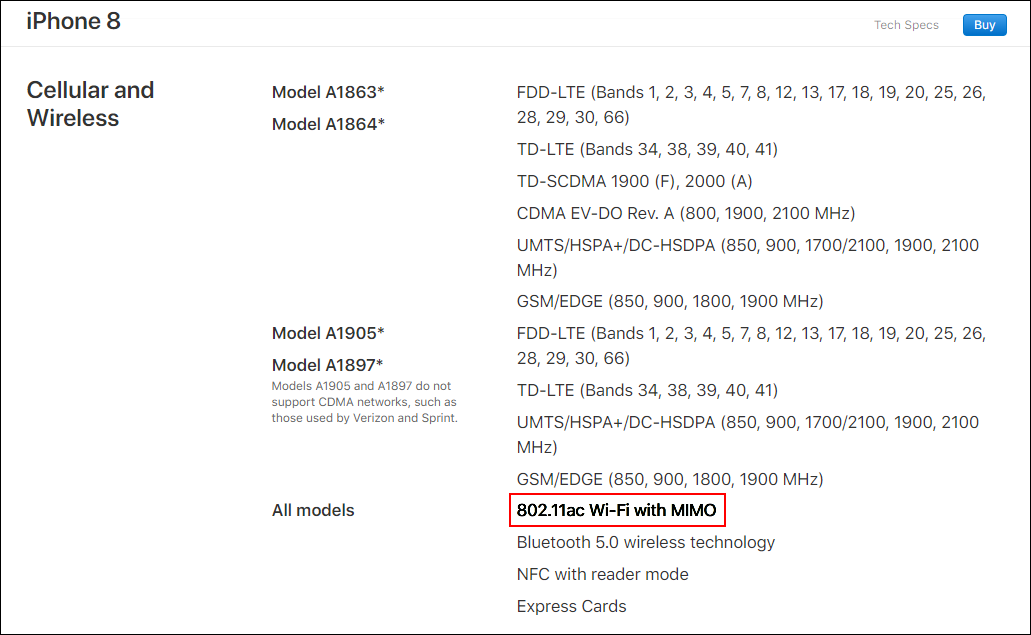
On the Apple site.
802.11ac Wi-Fi with MIMO ... Not very informative. How many spatial streams? What is the maximum channel width? Is there support for 802.11r, k, v? MU-MIMO?
Samsung shares information about its Galaxy S9 more readily:
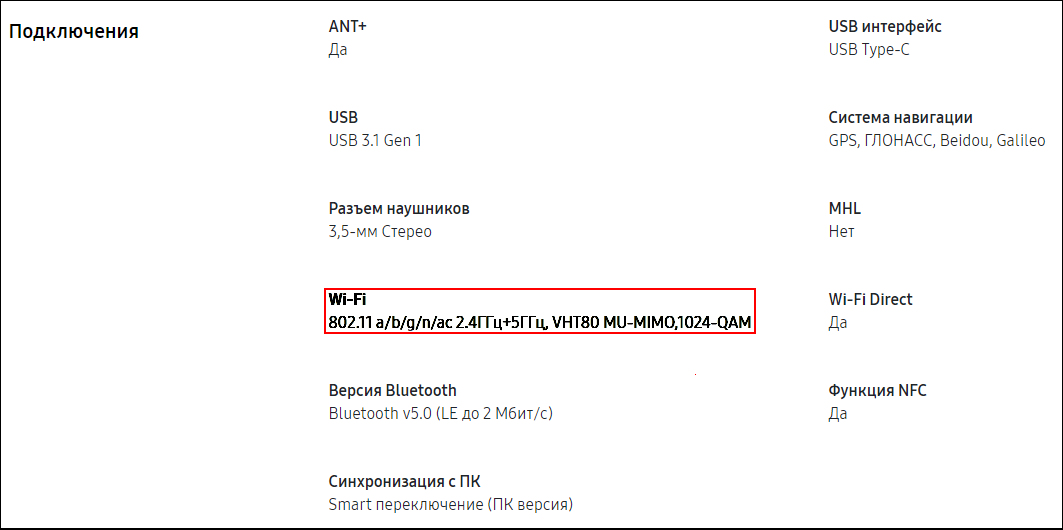
On the Samsung website.
Even if we discard the mysterious modulation of 1024QAM (officially it will only appear in 802.11ax), we still know too little about the device.
The degree of manufacturers' openness varies widely - there are pleasant exceptions. Basically, nobody is allowed into the internal kitchen (again, for our benefit, of course), because a lot of knowledge is a lot of sadness.
Not everyone agrees.
Method 2. Practical
Dissatisfied users have been keeping their own bases for a long time, where the extracted device characteristics are entered
A prime example is the site of the respected Mike Albano.

Here you can find the following information:
- The list of channels available to the device;
- Supported standards;
- The number of spatial streams;
- MU-MIMO support;
- Maximum transmitter power.
To trust or not this information is everyone's business.
Anyone who is not indifferent can do his bit by sharing the results of his research with the public. Instructions - in the How To Contribute section . From this manual, you can find out that all of the information we are interested in is contained in the Association Request frame sent by the client device when connected to an AP.
Method 3. For geeks
All that is needed is to intercept the message exchange between the subscriber and the AP, which accompanies the initial connection establishment. This traffic is not encrypted, but difficulties may arise - not all Wi-Fi adapters allow sniffing 802.11 frames. Operating systems can also alleviate or complicate the task to varying degrees.
The topic is superbly googled, so we will not give links.
The lucky ones will be able to observe the following picture:
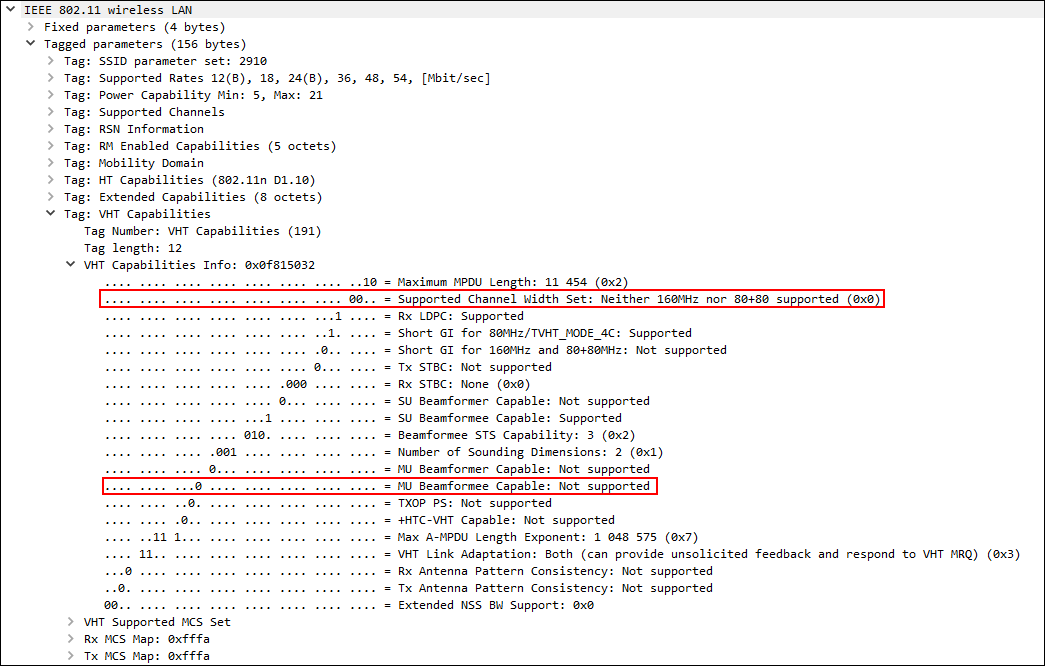
There is everything, friends.
From the curious - the same, already annoying, iPhone 8 does not support MU-MIMO. But we will not spoil your pleasure.
By the way, ready-made PCAP files received by users can be downloaded at the same clients.mikealbano.com
Method 4. Bonus
There is another great way to find out the entire underworld of the device. What is remarkable - without registration and SMS.
All devices sold in the United States must obtain certification from the FCC - Federal Communications Commission (Federal Communications Commission). As a result, the device is assigned an FCC ID - a unique number through which you can get a huge amount of information directly on the FCC website .
The code itself (FCC ID) can often be found on the device or on the box of it. In a pinch, the Internet will help.
The code consists of two parts: Grantee Code and Product Code. Enter as in the picture:
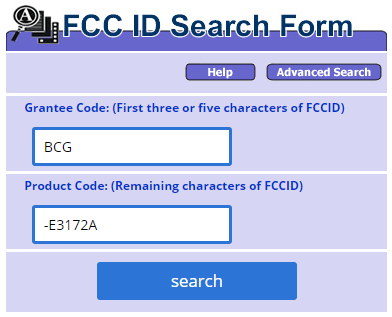
We have access to an extensive archive of documents with data used during certification. Even internal photos of the device are available - in some cases, you can even see the chip models.
Pay special attention to the SAR Report file - based on this report, you can not only determine the thickness of the foil cap, but also get detailed information about the characteristics of the device. Bingo!
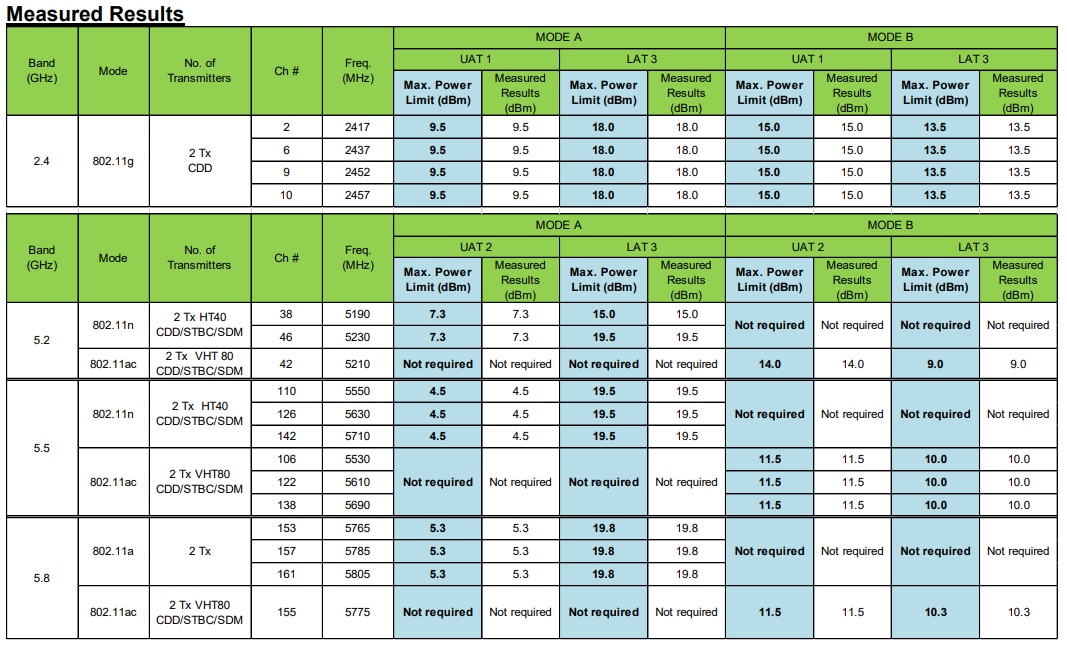
Subtotal number 3
Manufacturers are in no hurry to disclose full information about the characteristics of client devices. However, due to community activity, open sources and own perseverance, you can get all the necessary data.
Conclusion
Why to know, what employee uses what phone? And is it time to change your old router?
Of course, it all depends on the tasks. If you want to build reliable and predictable networks, you will not be able to dismiss client equipment. Consider its features when planning and servicing - you will be rewarded with lower costs and higher user satisfaction.
All this does not negate the need to use high-quality access points: many of the leading vendors' work is really effective - read our blog to keep up to date.
And once again - consider the characteristics of customers to spend money on working solutions.
We hope that this article will help you.
Good luck!
Author: Leonid Tekanov, CompTek wireless engineer.
A presentation based on the article took place on 10/25/2018 at our annual conference “BESSEDA” . Do not miss the following.
Useful resources:
CWNP - if you want not only to understand wireless networks well, but also to receive official recognition in the form of a certificate;
Revolution Wi-Fi - the site of Andrew von Nagy - the authoritative comrade who gave the world the most convenient Revolution Capacity Planner;
Divergent Dynamics - the site of the distinguished Devin Akin, an uncompromising expert and author of many valuable articles;
WLAN Professionals is the brainchild of Keith Parsons, a real Wi-Fi veteran. Lots of useful materials and a whole annual conference for those who are serious;
badfi.com is a good site about bad Wi-Fi.
