A botnet was discovered that fixes vulnerabilities in the routers infected by it and informs the administrator about it
 Mario Ballano , one of Symantec’s analysts, announced the discovery of a strange botnet called Linux.Wifatch , which, using a vulnerability in the Telnet service, infects various network devices and combines them into a peer-to-peer network. At the same time, not only does it not show any destructive activity (such as spamming or DDoS organization), but it also behaves like a kind of virus antivirus for infected devices. The botnet agent tries to find and terminate the processes known to it by malware, configures a reboot once a week to protect it from threats working only in RAM, and also kills the vulnerable Telnet daemon, leaving a message to the administrator asking him to disable the leaky service, change passwords or update the firmware!
Mario Ballano , one of Symantec’s analysts, announced the discovery of a strange botnet called Linux.Wifatch , which, using a vulnerability in the Telnet service, infects various network devices and combines them into a peer-to-peer network. At the same time, not only does it not show any destructive activity (such as spamming or DDoS organization), but it also behaves like a kind of virus antivirus for infected devices. The botnet agent tries to find and terminate the processes known to it by malware, configures a reboot once a week to protect it from threats working only in RAM, and also kills the vulnerable Telnet daemon, leaving a message to the administrator asking him to disable the leaky service, change passwords or update the firmware!Message for vulnerable device administrators:
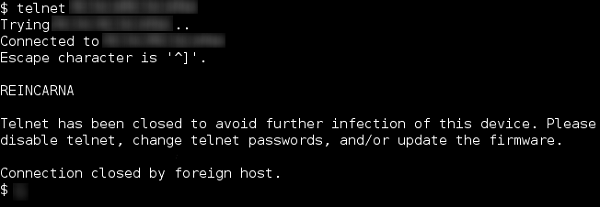
The first traces of the botnet were discovered back in November 2014 by a researcher who noticed that his home router was behaving somehow strangely. It turned out that the infection turned his device into a “zombie” connected to an ad hoc network from infected devices. The malware is written in Perl for various architectures and comes with its own static Perl interpreters for each.
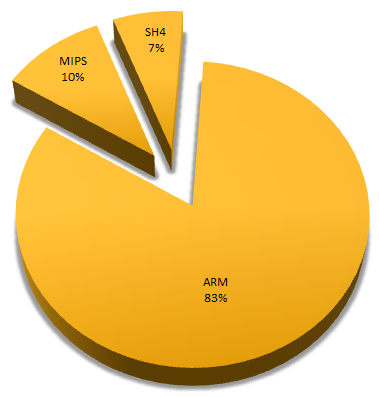
According to Symantec, tens of thousands of devices were infected, most of them in China, Brazil, Mexico, and India.

The source code uses compression, but not obfuscation. As stated in Semantec, it seems that the author did not try to complicate the analysis of the code in any way, on the contrary, he even made a lot of explanatory comments. In the scripts that the botnet uses for its work, such a remarkable text was found: The

authorship of this phrase is attributed to Richard Stallman, but the author of the botnet, apparently, was inspired by the exploits of Edward Snowden.
Theoretically, the botnet agent still carries an additional threat, because can execute arbitrary commands from the host (the command center is hidden using Tor), but they must be signed with a cryptographic key, which eliminates the possibility of unauthorized use. The most interesting thing is whether the author will remain on the side of the good or, over time, will nevertheless use the botnet for profit ...
Only registered users can participate in the survey. Please come in.
Will the author of the botnet go to the dark side?
- 17.6% Yes, money rules the world. 369
- 82.3% No, I believe in noble hackers! 1725
