Odlanor Malicious Software Specializes in Compromising Poker Players
Two years ago, we published information about the PokerAgent malware ( MSIL / Agent.NKY ). Cybercriminals used it to compromise user accounts of the social network Facebook, as well as to steal information and valuable data from the online game Zynga Poker. In that case, the social network Facebook was used as a platform for spreading malware.

Recently, our analysts discovered another malicious program - Win32 / Spy.Odlanor , which is also aimed at poker players. This time we are talking about the customers of the PokerStars and Full Tilt Poker websites.
For the attacker, the situation looks quite simple: after the victim has successfully infected with the Trojan, the cybercriminal will gain access to information about her playing cards, thus, he will have an undeniable advantage in the game. Below we will examine in more detail how this scheme works.
As in the case with other trojans, a user can become infected with this malicious program, trying to download one or another software useful for him from unreliable sources. Attackers disguise Win32 / Spy.Odlanor as installers of legitimate general-purpose software, for example, Daemon Tools or Torrent. Odlanor can also be disguised as specialized poker programs, such as Tournament Shark, Poker Calculator Pro, Smart Buddy, Poker Office.
After its execution, Win32 / Spy.Odlanor will try to take screenshots if the user has PokerStars and Full Tilt Poker clients running. Screenshots are then sent to the attacker on the remote server.
These screenshots taken by cybercriminals in the future can be obtained from attackers by compromising their data. The data also includes the player identifier. Both of the aforementioned poker sites contain a function to search for players by their identifiers, so an attacker can quite simply connect to the game tables he needs.
We cannot say for sure whether the attacker is playing the game manually or using some other automated method.
In newer versions of the malware, the ability to steal user password data was added to the body of the Oldanor Trojan by integrating one of the versions of the NirSoft WebBrowserPassView tool into it. This tool is unwanted software and is detected by ESET antivirus products like Win32 / PSWTool.WebBrowserPassView.B . He specializes in extracting passwords from web browsers.
The Win32 / Spy.Odlanor Trojan program interacts with its C&C server via a simple HTTP protocol. Its address is hardwired in the body of the malware. Some of the data that identifies the victim, such as the version of the malware and computer information, is sent as URL parameters. The rest of the collected information, including the archive with screenshots or stolen passwords, is sent in the body of the POST request of the HTTP protocol.
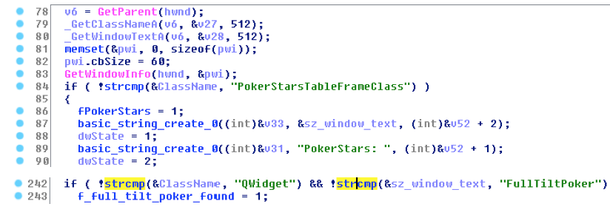
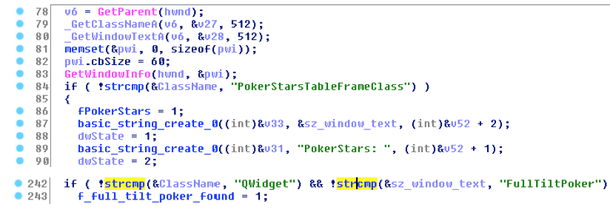
Below are two screenshots of the malware code in IDA Pro, which is responsible for finding application windows with the titles of the games PokerStars and Full Tilt Poker.
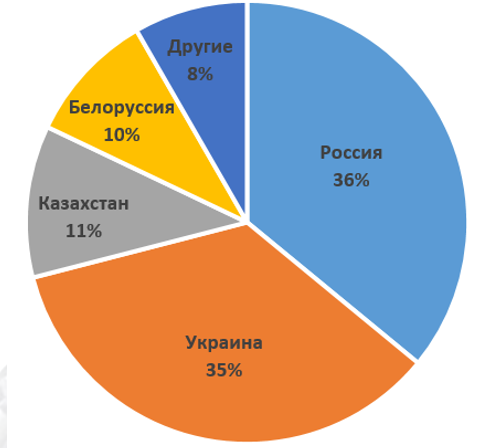
We were able to detect several versions of this malware, the earliest of which dates back to March 2015. Data from our cloud technology ESET LiveGrid show that the largest number of detections of this malware was recorded in countries of Eastern Europe. However, the trojan is a potential threat to any online poker player. From his actions affected users in the Czech Republic, Poland and Hungary. On September 16th, we recorded several hundred infected Win32 / Spy.Odlanor users.
The SHA-1 identifiers for some malware samples are listed below.
18d9c30294ae989eb8933aeaa160570bd7309afc
510acecee856abc3e1804f63743ce4a9de4f632e
dfa64f053bbf549908b32f1f0e3cf693678c5f5a

Recently, our analysts discovered another malicious program - Win32 / Spy.Odlanor , which is also aimed at poker players. This time we are talking about the customers of the PokerStars and Full Tilt Poker websites.
For the attacker, the situation looks quite simple: after the victim has successfully infected with the Trojan, the cybercriminal will gain access to information about her playing cards, thus, he will have an undeniable advantage in the game. Below we will examine in more detail how this scheme works.
As in the case with other trojans, a user can become infected with this malicious program, trying to download one or another software useful for him from unreliable sources. Attackers disguise Win32 / Spy.Odlanor as installers of legitimate general-purpose software, for example, Daemon Tools or Torrent. Odlanor can also be disguised as specialized poker programs, such as Tournament Shark, Poker Calculator Pro, Smart Buddy, Poker Office.
After its execution, Win32 / Spy.Odlanor will try to take screenshots if the user has PokerStars and Full Tilt Poker clients running. Screenshots are then sent to the attacker on the remote server.
These screenshots taken by cybercriminals in the future can be obtained from attackers by compromising their data. The data also includes the player identifier. Both of the aforementioned poker sites contain a function to search for players by their identifiers, so an attacker can quite simply connect to the game tables he needs.
We cannot say for sure whether the attacker is playing the game manually or using some other automated method.
In newer versions of the malware, the ability to steal user password data was added to the body of the Oldanor Trojan by integrating one of the versions of the NirSoft WebBrowserPassView tool into it. This tool is unwanted software and is detected by ESET antivirus products like Win32 / PSWTool.WebBrowserPassView.B . He specializes in extracting passwords from web browsers.
The Win32 / Spy.Odlanor Trojan program interacts with its C&C server via a simple HTTP protocol. Its address is hardwired in the body of the malware. Some of the data that identifies the victim, such as the version of the malware and computer information, is sent as URL parameters. The rest of the collected information, including the archive with screenshots or stolen passwords, is sent in the body of the POST request of the HTTP protocol.
Below are two screenshots of the malware code in IDA Pro, which is responsible for finding application windows with the titles of the games PokerStars and Full Tilt Poker.


We were able to detect several versions of this malware, the earliest of which dates back to March 2015. Data from our cloud technology ESET LiveGrid show that the largest number of detections of this malware was recorded in countries of Eastern Europe. However, the trojan is a potential threat to any online poker player. From his actions affected users in the Czech Republic, Poland and Hungary. On September 16th, we recorded several hundred infected Win32 / Spy.Odlanor users.

The SHA-1 identifiers for some malware samples are listed below.
18d9c30294ae989eb8933aeaa160570bd7309afc
510acecee856abc3e1804f63743ce4a9de4f632e
dfa64f053bbf549908b32f1f0e3cf693678c5f5a
