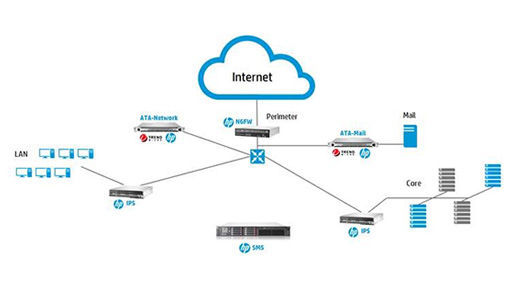
HP TippingPoint ATA Network and HP TippingPoint ATA Mail
One of the most pressing security issues today is Advanced Permanent Threats (APTs). Traditional network security solutions are far from always able to prevent an invasion in time and eliminate its results. HP TippingPoint Advanced Threat Appliance family of products will effectively neutralize an attack at its very beginning.
Targeted attacks use various methods, such as infecting mobile devices, slow-moving malware, hidden loads, and other ways to penetrate familiar security solutions. A threat can be detected by the simultaneous use of several scanning methods. HP TippingPoint Advanced Threat Appliance (ATA) Solutions uses unique software developed by the Hewlett-Packard and Trend Micro consortium to help locate malware that is not immediately active. A secure test environment is used to identify advanced threats. When each suspicious object enters the network, the detection technology checks its action in a test virtual machine, monitors suspicious behavior and reports this. Quickly respond and localize the source of the threat,
The HP TippingPoint ATA family includes two solutions — the HP TippingPoint ATA Network — for networks and the HP TippingPoint ATA Mail — for mail. The network security product detects APT threats by monitoring a wide range of ports and protocols across a wide range of operating systems. Pochtar works with a mail gateway to detect and block malicious emails, including phishing emails, which are often the initial stage of targeted attacks. It forms an additional “layer” of verification to detect malicious content, attachments and URLs that go unnoticed through standard email security tools.
On guard network
As already mentioned, to protect HP TippingPoint ATA networks, they use a custom test environment - an isolated sandbox that fully matches the customer’s network configuration. System emulation allows you to identify threats and quickly and react to them accordingly. Because ATP threats use a wide range of network penetration methods, HP TippingPoint ATA uses a variety of detection algorithms, special tracking functions, and correlation rules to identify all threat characteristics associated with malware. The system monitors all ports and more than 80 protocols to detect attacks anywhere in the network. In addition, threat detection occurs regardless of the operating system of the devices, whether it be Android, Linux, Mac OS X, Windows or any other OS.
Of course, identifying a threat is only half the battle. The second half - the implementation of actions to neutralize it. The integration of TippingPoint ATA with the HP TippingPoint Security Management System (SMS) provides quick awareness of the severity of the threat by assessing the impact on user data, geographic location, and source reputation based on ThreatLinQ databases, consolidating all the information into a single console. This allows you to create new rules to block existing and potential attacks by coordinating them with the HP TippingPoint NGFW and IPS tools to respond to threats using the HP TippingPoint Threat Digital Vaccine (ThreatDV) service.
The principle of protection itself is quite simple. TippingPoint ATA creates a test environment with virtual machines repeating typical configurations of user computers within the company. In case of penetration of malicious software, it “detonates” on the ATA device inside one of the virtual machines, infecting “patient-zero”. Also, within the sandbox, time is compressed 10-100 times to get a faster reaction and identify an infected object. After threat detection, the ATA sends event information to the HP TippingPoint SMS security management system. In turn, SMS updates security policies and blocks the threat, infected hosts and the source of the intrusion.
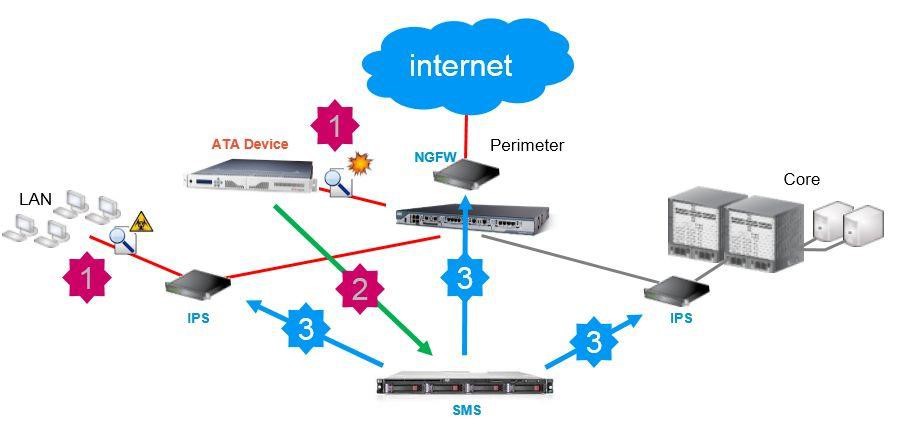
1) Malware detonates on the ATA device, infecting the patient-zero
2) ATA sends the event to TippingPoint SMS
3) SMS updates policies, blocking the threat, infected hosts and source of intrusion
In the language of numbers
The HP TippingPoint ATA line has been developed in close collaboration with Trend Micro, a leader in advanced persistent threats. In the 2014 Breach Detection Tests of the well-known independent laboratory NSS Labs, the product showed the highest detection rate in the industry - 99, 1% with a zero result of false positives. In addition, the lowest total cost of ownership was noted - 25% lower than the average for all products tested.
Mail under control
HP TippingPoint ATA for Mail provides the ability to detect and neutralize threats that can penetrate the network through the mail gateway. The solution tracks email attachments using various detection engines and a test environment. The range of analyzed attachments includes Windows executables, Microsoft Office, PDF, web content and compressed files. Specialized detection tools identify malware and exploits in common office documents.
In addition to attachments, emails also analyze URLs. As tools for this, we use the reputation of sources, analysis of page content, and, traditionally, a sandbox. In addition, the system unlocks password-protected files and archives using heuristics and provided keywords.
HP TippingPoint ATA Line
| ATA - Network 250 | ATA - Network 500 | ATA - Network 1000 | ATA - Network 4000 | ATA - Mail 6000 | |
| Performance | 250 Mbps | 500 Mbps | 1 Gbps | 4 Gbps | 400,000 letters / day |
| Form factor | 1U, 48.26 cm (19 ') | 2U, 48.26 cm (19 ') | 1U, 48.26 cm (19 ') | ||
| Weight (max.) | 16.78 kg | 23.6 kg | 16.78 kg | ||
| Dimensions | 43.47x69.85x4.32 cm | 44.55x67.94x8.73 cm | 43.47x69.85x4.32 cm | ||
| Ports | 10/100 / 1000BASE-T RJ45x4 | 10/100 / 1000BASE-T RJ45x4, 10GbE SFP + x2 | 10/100 / 1000BASE-T RJ45x4 | ||
| Input voltage | 100 to 120 V, 200 to 240 V | ||||
| Input current | 2.78 A (100 V) to 1.15 A (240 V) | 4.58 A (100 V) to 1.88 A (240 V) | 2.78 A (100 V) to 1.15 A (240 V) | ||
| Hard disks | 600 GB SASx2 | ||||
| RAID configuration | RAID 1 | RAID 10 | RAID 1 | ||
| Power (hot swap) | 500 watts | 800 watts | 500 watts | ||
| Power consumption (max.) | 276.9 watts | 456.1 watts | 276.9 watts | ||
| Heat dissipation (max.) | 944 BTU / hour | 1,556 BTU / hour | 944 BTU / hour | ||
| Frequency | 50/60 Hz | ||||
| Working temperature | 10 - 35 ° C (50 - 95 ° F) | ||||
Distribution of HP solutions in Ukraine , Georgia , Tajikistan , CIS countries .
Training courses on HP technologies in Kiev (UT MUK)
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
