Potao Operation: Analysis of cyber espionage malware, part 1
Analysts at our antivirus lab have investigated a series of cyber attacks and malware campaigns using Win32 / Potao malware . Despite the fact that the anti-virus products of our company, as well as some other anti-virus vendors, already detected this malware, it remained outside the public field. The first samples of Win32 / Potao dated 2011
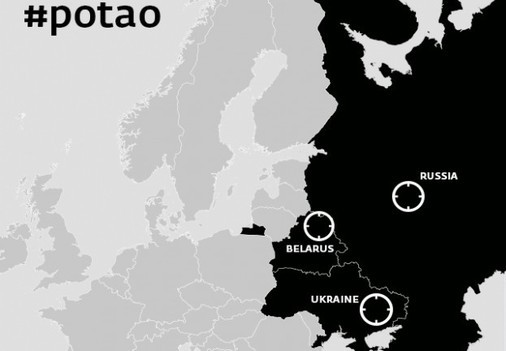
Cyber attacks using Potao are a type of targeted attacks, some examples of which we have already discussed earlier . We are talking about the BlackEnergy malware (aka Sandworm, Quedagh), which prevails in Ukraine, Russia, as well as in some CIS countries, including Georgia and Belarus.
The victims of Potao were computer networks of the military and the government of Ukraine, as well as one of the leading Ukrainian news agencies. In addition, the malicious program was used by cybercriminals to spy on participants in the MMM financial pyramid, which is popular in both Russia and Ukraine. One of the most interesting features of this malicious campaign is that attackers compromised the well-known open-source legitimate software for TrueCrypt encryption, and then used it to spread malware.
The Russian website of this encryption tool with the address truecryptrussia.rudistributed the TrueCrypt application, which contained a backdoor. An interesting feature is that malicious copies of this application were delivered only to some users, which is an indicator of the direction of this malicious campaign. This feature also explains the fact that the backdoor has long been invisible to users and visitors to the specified website. This above domain was used by operators as the managing C & C server for the malware. In some cases, Win32 / Potao is loaded onto the computer by another malicious program that is detected by our products as Win32 / FakeTC .
Our report contains detailed information about the large number of attacks using Win32 / Potao that attackers have organized over the past 5 years. Like the BlackEnergy malware used by the Sandworm cybergroup, Potao is a versatile modular cyber espionage tool. The cyber attacks in which Potao was used are of the Advanced Persistent Threat (APT) type and are targeted. We observed only isolated cases of using Potao in massive malicious campaigns.
general information
As we mentioned earlier, Potao malware is not new, it was discovered back in 2011. One of the possible reasons why this malware has not yet been publicly disclosed is its activity. Between 2011 and 2013 the number of detections of this malware was low. A significant increase in Potao prevalence, according to ESET LiveGrid, was observed in 2014 and 2015. (Fig 1.)

Fig. 1. Statistics of the distribution of Win32 / Potao at different time intervals according to ESET LiveGrid.
The diagram above shows that we did not provide statistics for Win32 / Potao for 2011. This was done because during this period of time Potao was distributed by cybercriminals as part of mass campaigns, i.e. at this time the malware was not used in targeted attacks against users. Debugging versions of Potao discovered in 2013 were also excluded from the chart data.
Using Potao in massive campaigns against users makes it look like malware such as BlackEnergy or even Stuxnet. These well-known malicious programs were used by cybercriminals to target cyberattacks, but ultimately became widespread, infecting those users for whom they were not originally designed. During the investigation of malicious campaigns involving Potao, we discovered that attackers used debug versions of this malware to test it before being used in targeted attacks.
The main reason for the increase in the number of Potao detections in 2014 and 2015. A mechanism for infecting removable USB devices was added by cybercriminals.

Fig. 2. Timeline of malware campaigns using Potao.
To compile the above chronology, we used data from our ESET LiveGrid cloud system, as well as time stamps of executable PE files of the malicious program.
The first cyber campaign using Potao was recorded in August 2011. This was not a targeted attack, since it was massive. The malware executables used in this campaign contained an encrypted GlobalPotao string .
The distribution mechanism of Potao in this malicious campaign was rather trivial, but quite effective. Malware droppers were distributed as attachments for phishing e-mail messages, and the MS Word document icon was used as an executable file icon. This disguise helps lull the attention of users who receive such phishing messages. It should be noted that the attackers did not use any exploits to automatically install the malware. In addition to the payload, droppers contained a fake Word document that was displayed to the user to mask the process of installing the malicious program into the system.

Fig. 3. Fake decoy-document (bait), which dropper Potao shows the user to mask the process of installing it in the system.
Other Potao droppers, which were used in malicious campaigns in 2011, contained documents in Armenian. It is interesting to note that a legitimate document belonging to the Armenian Ministry of Labor and Social Affairs was used as one of the decoy documents.

Fig. 4. A legitimate decoy-document in Armenian, which was used by Potao droppers in 2011.
Another malicious cyber campaign was sent by attackers to the participants of the MMM financial pyramid. The Potao executables that were used in the campaign against MMM members had compilation timestamps on April 27, 2012 and the campaign ID 00km . The fake decoy document uses the pyramid entry theme.

Fig. 5. The dropper's Decoy document, which was used in malicious campaigns against MMM participants.
Potao droppers with decoy documents that contained random sequences of Cyrillic characters were also discovered in this malicious campaign. As we discovered later, the use of documents with arbitrary character sets is a kind of calling card of this cyber group.

Fig. 6. Decoy document used in malicious campaigns against MMM participants.
The file that was listed above was called by the attackers "Report on the payment of Kovaleva Alexandra.exe." In addition, the campaign ID, mmmL, confirms the use of malicious software by cybercriminals against MMM users.
The founder of the MMM pyramid Sergey Mavrodi, on June 19, 2012 posted a warning on the pyramid’s website that cybercriminals send phishing messages on his behalf that contain a link to malware that is hosted on Dropbox.

Fig. 7. A warning message about malicious mailing from the founder of MMM, Sergey Mavrodi.

Fig. 8. A malware archive hosted on Dropbox.
The attackers used the following file names, which are indicated above: “Questionnaire and rules”, “anketa_i_pravila”, droppers contained the compilation mark on June 13, 2012 and the campaign ID “NMMM”.
We can assume that Potao operators used this spyware to spy on the participants or the organizers of this financial pyramid.
In 2013, traces of Potao were discovered in Georgia. The malware executable, which had a timestamp dated October 15, 2013, was called Wedding_invitation.exe. This time, the decoy document contained the text of the wedding invitation. The file name and document text contained English text.

Fig. 9. Appearance of the decoy-document, which was used in droppers Potao, aimed at users of Georgia.
Potao in Ukraine
Before detecting the growth of Win32 / Potao activity in Ukraine in 2014, we discovered several debug versions of this malware in the fall of 2013. It can be assumed that attackers tested a new version of the malware before using it in targeted cyber attacks against Ukrainian users .

Fig. 10. Code snippet of the debug version of the malicious program.
It is interesting to note that one of the identifiers of the campaign in these debug versions of Potao was the word krim (Crimea).
In March 2014, the criminal group switched to using the new Potao distribution vector. They began to use the so-called. A landing page for installing malware. The web page was called MNTExpress. We believe that the design of this website was taken from the website of the Russian postal service Pony Express.

Fig. 10. The appearance of the Pony Express delivery service web page.

Fig. 11. Appearance of the MNTExpress web page.
Disguising a phishing message as a notification of a mail service is a very common method for cybercriminals to spread malware. Instructions for downloading malware may be located in the body of the message. However, the Potao cybergroup takes a different approach. Alleged victims received SMS messages that contained a link to a maliciously crafted web page. The victim was also sent a special “tracking code” (tracking code), as well as the name of the recipient. This method is also another indicator of the direction of a cyber attack, since, firstly, attackers needed to conduct reconnaissance and obtain the victim’s full name, as well as her phone number. Secondly, in order to receive the malware file, the victim had to enter the code sent to her in the SMS message.

Fig. 12. SMS message sent by cybercriminals.

Fig. 13. One of the recipients of an SMS message from attackers is trying to get information about him in a public group of the vkontakte social network.
A similar malware distribution scenario was used by the attackers as early as March 2015. This time, the attackers registered the WorldAirPost.com domain, and the design for the website was taken from the Singapore postal service. They simply replaced the logo from the Singapore Post with the Italy Post.

Fig. 14. Appearance of the legitimate Singapore Post website.

Fig. 15. The appearance of a fake WorldAirPost.com website.
At the time of our analysis, the attackers were still active by registering another WorldAirPost.net domain in June 2015. It should be noted that MNTExpress supported two languages, Russian and English, and WorldAirPost only English. When using this website, attackers resorted to disguising droppers as an MS Excel document, not a Word.
In addition, instead of displaying a decoy document (bait), the dropper shows the user a special system message (Fig. 16).

Fig. 16. The system message displayed by the dropper to the user at startup in the system.
Since March 2015, our anti-virus laboratory has detected Potao malicious files on the computers of Ukrainian military and government organizations, as well as on the computers of one of the largest Ukrainian news agencies. Distributed droppers were disguised as MS Word documents and were given meaningful file names.

Figure 17. File names of droppers that were used in cyber attacks on high-ranking institutions in Ukraine.
It can be seen that the names of the files indicate their focus on the military and government institutions of Ukraine. The droppers' Decoy document was apparently damaged (Figure 18).

Fig. 18. Appearance of the decoy-document that was used in Potao droppers on March 5, 2015.
Compromise of the TrueCrypt encryption application
In the process of monitoring the Potao botnet, we detected infections on computers that were originally executed by other malware using suspicious websites.
We found that Win32 / Potao was installed on the system using an executable file called TrueCrypt.exe. At first glance, this was not surprising, since attackers often assign special trusted names to malicious files. However, in this case the situation was different, since a compromised version of the legitimate encryption software called TrueCryptacted as the loader (downloader) dropper Potao. Further investigation revealed that such a TrueCrypt modification was distributed through the truecryptrussia.ru website. Moreover, we were able to establish the fact that cybercriminals used this domain name as one of the addresses of the managing C & C server. This fact leads us to believe that this site is not legitimate, but was originally conceived by the owners to conduct malicious operations. Thus, the website itself and software called “TrueCrypt Russia” were used to perform the following malicious functions.
It should be noted that not every visitor to the above website will download a malicious modification of TrueCrypt. The malicious copy download mechanism is organized on a selective basis. This is further evidence of the targeted cyberattack using Potao.

Fig. 19. Web site of TrueCrypt Russia.
According to our statistics from ESET LiveGrid, the specified website has been distributing a malicious version of TrueCrypt software since at least June 2012. In this case, the timestamps of malware files refer to April 2012.
Georgian cyber campaign
To confirm the fact that the attackers behind Potao were very active even at the time of writing this study, one of the malware droppers with the compilation date July 20, 2015 can be cited. Dropper was used to compromise users in Georgia. This time, the decoy document was a PDF file.

Fig. 20. An example of a decoy document from a “Georgian dropper”.

Cyber attacks using Potao are a type of targeted attacks, some examples of which we have already discussed earlier . We are talking about the BlackEnergy malware (aka Sandworm, Quedagh), which prevails in Ukraine, Russia, as well as in some CIS countries, including Georgia and Belarus.
The victims of Potao were computer networks of the military and the government of Ukraine, as well as one of the leading Ukrainian news agencies. In addition, the malicious program was used by cybercriminals to spy on participants in the MMM financial pyramid, which is popular in both Russia and Ukraine. One of the most interesting features of this malicious campaign is that attackers compromised the well-known open-source legitimate software for TrueCrypt encryption, and then used it to spread malware.
The Russian website of this encryption tool with the address truecryptrussia.rudistributed the TrueCrypt application, which contained a backdoor. An interesting feature is that malicious copies of this application were delivered only to some users, which is an indicator of the direction of this malicious campaign. This feature also explains the fact that the backdoor has long been invisible to users and visitors to the specified website. This above domain was used by operators as the managing C & C server for the malware. In some cases, Win32 / Potao is loaded onto the computer by another malicious program that is detected by our products as Win32 / FakeTC .
Our report contains detailed information about the large number of attacks using Win32 / Potao that attackers have organized over the past 5 years. Like the BlackEnergy malware used by the Sandworm cybergroup, Potao is a versatile modular cyber espionage tool. The cyber attacks in which Potao was used are of the Advanced Persistent Threat (APT) type and are targeted. We observed only isolated cases of using Potao in massive malicious campaigns.
general information
As we mentioned earlier, Potao malware is not new, it was discovered back in 2011. One of the possible reasons why this malware has not yet been publicly disclosed is its activity. Between 2011 and 2013 the number of detections of this malware was low. A significant increase in Potao prevalence, according to ESET LiveGrid, was observed in 2014 and 2015. (Fig 1.)

Fig. 1. Statistics of the distribution of Win32 / Potao at different time intervals according to ESET LiveGrid.
The diagram above shows that we did not provide statistics for Win32 / Potao for 2011. This was done because during this period of time Potao was distributed by cybercriminals as part of mass campaigns, i.e. at this time the malware was not used in targeted attacks against users. Debugging versions of Potao discovered in 2013 were also excluded from the chart data.
Using Potao in massive campaigns against users makes it look like malware such as BlackEnergy or even Stuxnet. These well-known malicious programs were used by cybercriminals to target cyberattacks, but ultimately became widespread, infecting those users for whom they were not originally designed. During the investigation of malicious campaigns involving Potao, we discovered that attackers used debug versions of this malware to test it before being used in targeted attacks.
The main reason for the increase in the number of Potao detections in 2014 and 2015. A mechanism for infecting removable USB devices was added by cybercriminals.

Fig. 2. Timeline of malware campaigns using Potao.
To compile the above chronology, we used data from our ESET LiveGrid cloud system, as well as time stamps of executable PE files of the malicious program.
The first cyber campaign using Potao was recorded in August 2011. This was not a targeted attack, since it was massive. The malware executables used in this campaign contained an encrypted GlobalPotao string .
The distribution mechanism of Potao in this malicious campaign was rather trivial, but quite effective. Malware droppers were distributed as attachments for phishing e-mail messages, and the MS Word document icon was used as an executable file icon. This disguise helps lull the attention of users who receive such phishing messages. It should be noted that the attackers did not use any exploits to automatically install the malware. In addition to the payload, droppers contained a fake Word document that was displayed to the user to mask the process of installing the malicious program into the system.

Fig. 3. Fake decoy-document (bait), which dropper Potao shows the user to mask the process of installing it in the system.
Other Potao droppers, which were used in malicious campaigns in 2011, contained documents in Armenian. It is interesting to note that a legitimate document belonging to the Armenian Ministry of Labor and Social Affairs was used as one of the decoy documents.

Fig. 4. A legitimate decoy-document in Armenian, which was used by Potao droppers in 2011.
Another malicious cyber campaign was sent by attackers to the participants of the MMM financial pyramid. The Potao executables that were used in the campaign against MMM members had compilation timestamps on April 27, 2012 and the campaign ID 00km . The fake decoy document uses the pyramid entry theme.

Fig. 5. The dropper's Decoy document, which was used in malicious campaigns against MMM participants.
Potao droppers with decoy documents that contained random sequences of Cyrillic characters were also discovered in this malicious campaign. As we discovered later, the use of documents with arbitrary character sets is a kind of calling card of this cyber group.

Fig. 6. Decoy document used in malicious campaigns against MMM participants.
The file that was listed above was called by the attackers "Report on the payment of Kovaleva Alexandra.exe." In addition, the campaign ID, mmmL, confirms the use of malicious software by cybercriminals against MMM users.
The founder of the MMM pyramid Sergey Mavrodi, on June 19, 2012 posted a warning on the pyramid’s website that cybercriminals send phishing messages on his behalf that contain a link to malware that is hosted on Dropbox.

Fig. 7. A warning message about malicious mailing from the founder of MMM, Sergey Mavrodi.

Fig. 8. A malware archive hosted on Dropbox.
The attackers used the following file names, which are indicated above: “Questionnaire and rules”, “anketa_i_pravila”, droppers contained the compilation mark on June 13, 2012 and the campaign ID “NMMM”.
We can assume that Potao operators used this spyware to spy on the participants or the organizers of this financial pyramid.
In 2013, traces of Potao were discovered in Georgia. The malware executable, which had a timestamp dated October 15, 2013, was called Wedding_invitation.exe. This time, the decoy document contained the text of the wedding invitation. The file name and document text contained English text.

Fig. 9. Appearance of the decoy-document, which was used in droppers Potao, aimed at users of Georgia.
Potao in Ukraine
Before detecting the growth of Win32 / Potao activity in Ukraine in 2014, we discovered several debug versions of this malware in the fall of 2013. It can be assumed that attackers tested a new version of the malware before using it in targeted cyber attacks against Ukrainian users .

Fig. 10. Code snippet of the debug version of the malicious program.
It is interesting to note that one of the identifiers of the campaign in these debug versions of Potao was the word krim (Crimea).
In March 2014, the criminal group switched to using the new Potao distribution vector. They began to use the so-called. A landing page for installing malware. The web page was called MNTExpress. We believe that the design of this website was taken from the website of the Russian postal service Pony Express.

Fig. 10. The appearance of the Pony Express delivery service web page.

Fig. 11. Appearance of the MNTExpress web page.
Disguising a phishing message as a notification of a mail service is a very common method for cybercriminals to spread malware. Instructions for downloading malware may be located in the body of the message. However, the Potao cybergroup takes a different approach. Alleged victims received SMS messages that contained a link to a maliciously crafted web page. The victim was also sent a special “tracking code” (tracking code), as well as the name of the recipient. This method is also another indicator of the direction of a cyber attack, since, firstly, attackers needed to conduct reconnaissance and obtain the victim’s full name, as well as her phone number. Secondly, in order to receive the malware file, the victim had to enter the code sent to her in the SMS message.

Fig. 12. SMS message sent by cybercriminals.

Fig. 13. One of the recipients of an SMS message from attackers is trying to get information about him in a public group of the vkontakte social network.
A similar malware distribution scenario was used by the attackers as early as March 2015. This time, the attackers registered the WorldAirPost.com domain, and the design for the website was taken from the Singapore postal service. They simply replaced the logo from the Singapore Post with the Italy Post.

Fig. 14. Appearance of the legitimate Singapore Post website.

Fig. 15. The appearance of a fake WorldAirPost.com website.
At the time of our analysis, the attackers were still active by registering another WorldAirPost.net domain in June 2015. It should be noted that MNTExpress supported two languages, Russian and English, and WorldAirPost only English. When using this website, attackers resorted to disguising droppers as an MS Excel document, not a Word.
In addition, instead of displaying a decoy document (bait), the dropper shows the user a special system message (Fig. 16).

Fig. 16. The system message displayed by the dropper to the user at startup in the system.
Since March 2015, our anti-virus laboratory has detected Potao malicious files on the computers of Ukrainian military and government organizations, as well as on the computers of one of the largest Ukrainian news agencies. Distributed droppers were disguised as MS Word documents and were given meaningful file names.

Figure 17. File names of droppers that were used in cyber attacks on high-ranking institutions in Ukraine.
It can be seen that the names of the files indicate their focus on the military and government institutions of Ukraine. The droppers' Decoy document was apparently damaged (Figure 18).

Fig. 18. Appearance of the decoy-document that was used in Potao droppers on March 5, 2015.
Compromise of the TrueCrypt encryption application
In the process of monitoring the Potao botnet, we detected infections on computers that were originally executed by other malware using suspicious websites.
We found that Win32 / Potao was installed on the system using an executable file called TrueCrypt.exe. At first glance, this was not surprising, since attackers often assign special trusted names to malicious files. However, in this case the situation was different, since a compromised version of the legitimate encryption software called TrueCryptacted as the loader (downloader) dropper Potao. Further investigation revealed that such a TrueCrypt modification was distributed through the truecryptrussia.ru website. Moreover, we were able to establish the fact that cybercriminals used this domain name as one of the addresses of the managing C & C server. This fact leads us to believe that this site is not legitimate, but was originally conceived by the owners to conduct malicious operations. Thus, the website itself and software called “TrueCrypt Russia” were used to perform the following malicious functions.
- Hosting malware modification software for TrueCrypt encryption.
- As a consequence of the first paragraph, hosting is Win32 / Potao malware.
- The website address was used as the managing C & C server for Win32 / FakeTC.
It should be noted that not every visitor to the above website will download a malicious modification of TrueCrypt. The malicious copy download mechanism is organized on a selective basis. This is further evidence of the targeted cyberattack using Potao.

Fig. 19. Web site of TrueCrypt Russia.
According to our statistics from ESET LiveGrid, the specified website has been distributing a malicious version of TrueCrypt software since at least June 2012. In this case, the timestamps of malware files refer to April 2012.
Georgian cyber campaign
To confirm the fact that the attackers behind Potao were very active even at the time of writing this study, one of the malware droppers with the compilation date July 20, 2015 can be cited. Dropper was used to compromise users in Georgia. This time, the decoy document was a PDF file.

Fig. 20. An example of a decoy document from a “Georgian dropper”.
