Survey: Vulnerabilities in Industrial Management Systems in 2014

During NATO’s Estonian cyber orders in April 2015, it became known that the main cyber subdivision of the North Atlantic Alliance is not so interested in Android devices or webcams: the focus of military hackers has shifted to Windows and SCADA systems .
A month ago, researchers from Dell noted that in 2014 there was a twofold increase in the number of malware designed to attack store POS systems and SCADA systems, and today we will talk about some numbers and observations in the field of automated process control systems (ISC / SCADA), collected by our experts over the past three years.
Industrial control systems in recent years have reached a whole new level thanks to the development of information technology and the Internet. However, a new round of automation brings its own problems: the incorrect use of protection and data processing technologies leads to serious vulnerabilities.
In this regard, industrial control systems are increasingly becoming a target for attackers and cyber army. The individual worms Stuxnet (2010) and Flame (2012) were replaced by more sophisticated multi-stage attack schemes. So, to distribute the Havex Trojan in 2014, hackers hacked into the sites of manufacturers of industrial enterprise management software (SCADA) and infected official distributions of SCADA systems, which were then installed at enterprises, which allowed attackers to gain control over control systems in several European countries.
In 2012, Positive Technologies experts released the analytical report “Industrial Systems Security in Numbers”. Below are the results of our new study, which makes it possible to assess the changes that have occurred from 2012 to 2015.
Among the general trends that we observe in the process of analyzing the security of process control systems, the following can be noted.
Open doors . Many systems that manage production, transport, water and energy can be found on the Internet using publicly available search engines. As of January 2015, Positive Technologies researchers have thus discovered more than 140,000 different components of process control systems. Moreover, the owners of such systems do not realize how well their resources are “visible from the outside”. We find opportunities for attacks on industrial control systems through kiosk mode and cloud services, through sensors and physical ports, through industrial Wi-Fi and other types of access, which are often not considered to be threats at all.
One key to many locks. The rapid growth in the number of organizations implementing industrial control systems, with a limited number of manufacturers, leads to a state where the same SCADA platform is used to manage critical facilities in a wide variety of industries. For example, our experts identified vulnerabilities in the system that manages the Large Hadron Collider, several airports in Europe and Iran’s nuclear power plants, the largest pipelines and water supply systems in different countries, trains and chemical plants in Russia. Once discovered, a similar vulnerability allows attackers to attack many different objects around the world.
Threats develop faster than protection. The complex organization of industrial control systems and the requirement for the continuity of technological processes lead to the fact that the basic components of control systems (industrial protocols, operating systems, DBMS) are outdated, but not updated, and their vulnerabilities are not eliminated for years. On the other hand, the development of automated tools significantly increases the speed of hackers. Within the framework of the Critical Infrastructure Attack contest on the PHDays IV forum, several modern SCADA platforms used at industrial enterprises were hacked over two days .
Mad House. The term industrial control system (automated process control system) appeared in the 80s, when the main objects of automation were large industrial enterprises. However, the cost reduction and miniaturization of technology has led to the fact that computerized devices that manage the life support of buildings, monitoring and distribution of electricity, are actively involved in everyday life. At the same time, neither manufacturers nor consumers pay due attention to the security of these systems: this study shows how many such devices are available via the Internet.
Research Methodology
Vulnerability databases (ICS-CERT, NVD / CVE, SCADA Strangelove, Siemens Product CERT, etc.), exploit collections (SAINTexploit, Metasploit Framework, Immunity Canvas, etc.), vendor notifications, and scientific reports were used to collect information about vulnerabilities. conferences and publications on specialized sites.
The vulnerability was determined based on CVSS v. 2. It should be borne in mind that statistics are influenced by factors such as the absence of typical descriptions of vulnerabilities or a disclosure policy: manufacturers often reduce the risk or do not disclose information about vulnerabilities (for more details on these factors, see the full version of the report). Thus, the real security situation of ICS can be even worse than our statistics show.
Data on the availability of ICS on the Internet was collected using passive methods using publicly available search engines (Shodan, Project Sonar, Google, Bing) and port scan results. Data analysis was carried out using the fingerprint database, which consists of 740 entries, which allows us to make a conclusion about the manufacturer and version of the product based on the banner. Most fingerprints relate to the SNMP (240) and HTTP (113) protocols, about a third to various industrial protocols (Modbus, DNP3, S7, etc.).
Number of vulnerabilities
In total, the study identified 691 vulnerabilities in the components of ICS. There has been a sharp increase after 2009: over the next three years (2010-2012), the number of vulnerabilities in automated process control systems has grown 20 times (from 9 to 192). After that, the average annual number of detected vulnerabilities stabilized (181 in 2014).

Number of ICS vulnerabilities
Vulnerability analysis
The severity level of the identified vulnerabilities also retains the 2012 trends. The main number of vulnerabilities has a high (58%) and medium (39%) degree of danger .
If we look at CVSS vectors, then more than half of the vulnerabilities have a high metric for such an important indicator as accessibility . The remote exploitation rate is also high , which, combined with weak authentication mechanisms, increases the risk of attacks.
Since open access to information on the process of eliminating vulnerabilities is not published, the study used data obtained by Positive Technologies experts from manufacturers. The situation looks more depressing than in 2012, when most security flaws (about 81%) were promptly eliminated by manufacturers even before they became widely known, or within 30 days after uncoordinated disclosure of information. According to the data for the first quarter of 2015, only 14% of vulnerabilities were fixed within three months, 34% were fixed more than three months, and the remaining 52% of errors were either simply not fixed, or the manufacturer did not report the time to fix it.
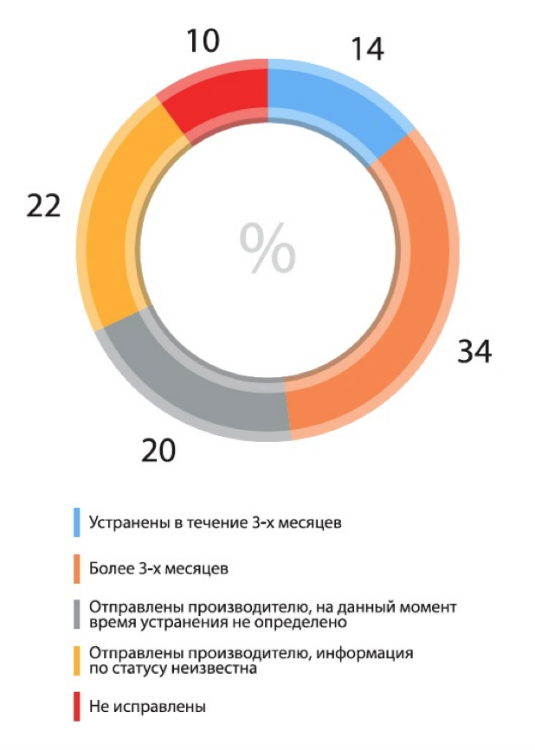
Automated process control vulnerabilities elimination
Vulnerabilities by Manufacturer
The list of manufacturers leading in the number of vulnerabilities in products has not practically changed: Siemens (124 vulnerabilities), Schneider Electric together with its acquired company Invensys (96), Advantech (51), General Electric (31). At the same time, the general list of manufacturers with identified vulnerabilities has grown. The diagram below shows the companies with the most vulnerabilities; the remaining 88 manufacturers are combined in the line “Other”.
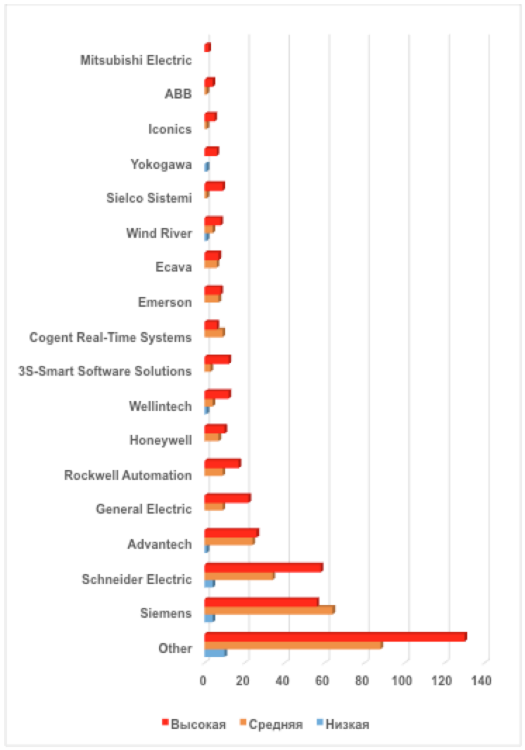
Vulnerabilities in ICS of various manufacturers (by risk)
Geography of accessibility and vulnerability of ICS
In total, within the framework of the study, 146 137 components of industrial control systems were identified , which can be accessed via the Internet. The most common are Tridium building automation systems (Honeywell) , as well as energy monitoring and control systems, including those based on solar technology ( SMA Solar Technology ). The largest number of components available is PLC / RTU , followed by inverter monitoring and control systems. The following are network devices and HMI / SCADA components.
It is quite natural that countries - technological leaders have a high level of automation, and therefore the concentration of industrial systems of these countries on the Internet is quite high. The leader, as before, remainsUSA (33%) , but in second place is no longer Italy, but Germany , with a wide margin ( 19% ). In general, the European Region has shown a marked increase in the Internet accessibility of industrial systems. On the other hand, in the Asian region local, little-known components of industrial control systems are known on the world market, which cannot always be identified.

Distribution of available process control systems
By analyzing the versions of available process control components, more than 15,000 vulnerable components were identified. The largest number is in the United States, followed by France, Italy and Germany, which is consistent with the overall picture of the prevalence of these systems. On the other hand, it should be noted that in the components that are most common on the Internet, few vulnerabilities are revealed. In general, more than 10% of the available process control systems were vulnerable .

Distribution of vulnerable ICS components by country
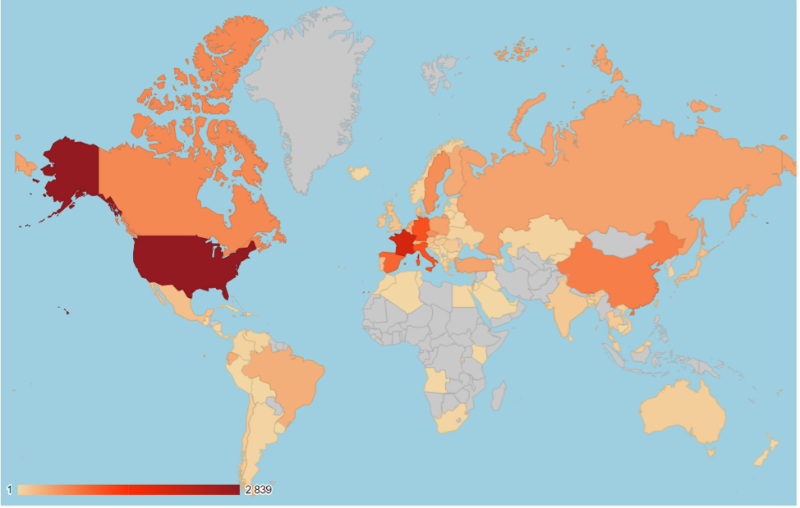
Distribution of vulnerable ICS components by country
During the Positive Hack Days information security forum (to be held May 26-27 in Moscow), Positive Technologies experts will present a detailed report on the results of the vulnerability study of industrial control systems in 2014. There you can participate in contests for hacking automated process control systems.
