Amazing Kingston DataTraveler DT6000 USB Flash Drive and Recovering Information Lost from a Crash
Greetings to dear Khabrovchan. I am Artem Makarov aka Robin, a leading engineer at Hardmaster, for many years specializing in recovering data from a variety of media. Today I would like to share with you the history of recovering files from one very interesting flash drive. I hope to get feedback on my habradebutut in the comments.
Despite the fact that there was a huge pile of browsing all kinds of devices, I never had to deal with a task like the one described below.
So, the Kingston DT6000 USB Flash drive, declared by the manufacturer as a reliable file storage, using the AES256 FIPS140-2 Level 3 cryptographic algorithm.
Logically, the flash drive is organized as follows: the 68 megabyte partition formatted in FAT16 is kind of bootable. When the device is connected to the PC, autorun is triggered (or the user is prompted to launch the executable):
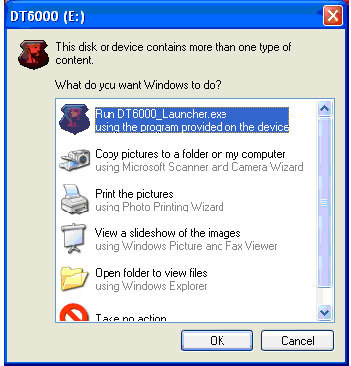
Then the following window comes to the fore:
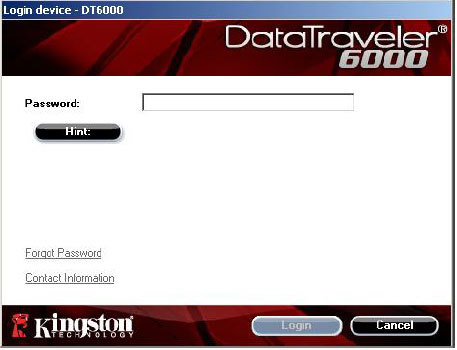
Enter the password, voila - a hidden section is mounted with carefully hidden photos and videos of known content.
But one day a user had trouble, a flash drive was inserted, and the “bootloader” turned out to be empty. With a password, it turned out that stupidly there is no way to enter this password somewhere. They brought a diagnostic disk to us.
First of all, connecting the drive to the test PC and opening my favorite WinHEX hex editor, I climbed into the list of physical disks. So it is, two volumes. The first is empty, and, most importantly, in read-only mode! The second is unavailable. I shot the image from the first section, analyzed it. Both copies of FAT tables are missing in their normal form.
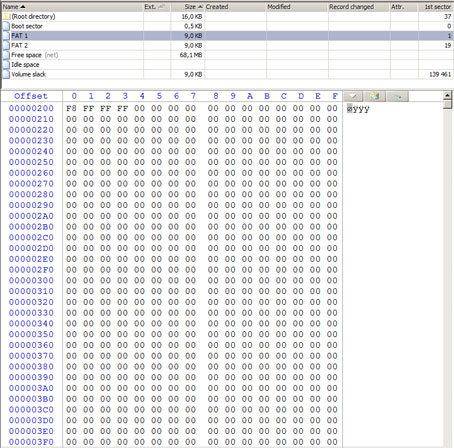
That is, with the ability to get files with names and structure from the “boot partition”, you can say goodbye. By “rough recovery” or recovery from known file headers (aka raw recovery), we managed to pull out some zip archive and pdf-ku. From the content of the latter, it became clear how everything was arranged, and what is missing on the boot partition.
Considering that the section was locked by the manufacturer for recording, it was clear that there could be no talk about any random formatting by the user, and the most likely reason for the section “zeroing” was a failure in the NAND processing translation table area, as a result of which part of the correct blocks was replaced by “alternative” ones.
This effect is called the “pseudo-logical problem with the flash drive” and looks like a glitch at the file system level, in fact, it is a hardware failure, in fact. So, most likely, you will have to transfer the USB flash drive to the pathological table and open it, in order to unsolder the memory chip (s) and try to collect something meaningful from the read images.
About encryption and how to collect dumps with encrypted content in general, at that moment I did not bother with my head.
Problems are supposed to be solved as they appear, so the first thing to do was to find the DT6000_Launcher with all the surroundings. On the manufacturer’s website, the product download section was empty. It is logical - it makes sense to upload files if it is assumed that you will not be able to write them (see locked record)? He threw a cry to his colleagues. The necessary files were sent. The next problem is to tell the launcher where we have encrypted.
Attempts to unlock the FAT16 partition on the flash drive itself using OS tools and record a launcher on it were unsuccessful. Attempts to launch the launcher from another medium and set the flash drive on the flash drive under investigation also proved unsuccessful. Further hardware intervention in the internals of Traveler's date became inevitable.
Removing the external plastic case, the researcher’s gaze revealed this:

With the exception of the USB connector, everything is flooded with plastic. It was possible to remove it with the help of a hot-air soldering station, heating the area after area to a temperature of about 150 C, after which the plastic began to slowly bend and break off in small pieces. Wielding with dental hooks and a scalpel, feeling like an archaeologist, he cleaned one side of plastic. I saw the following:
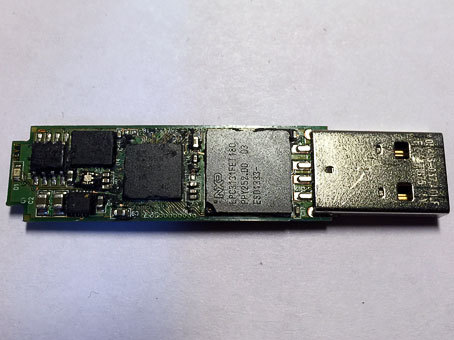
LPC3131FET180 workstation controller, 3s500e plate (it is also PLISS, PLD is a programmable logic integrated circuit) from XILINX, ROSETTA crypto module from Spyrus and Atmelovskaya ROM 25DF081A ROM cabinet. We must take on the second half, because the desired memory NAND has not yet been found.
I start to clean the second side. Something brilliant appears. Quartz? Does not look like. A couple more sweeping strokes of a sledgehammer and chisel, a shame - a card reader!
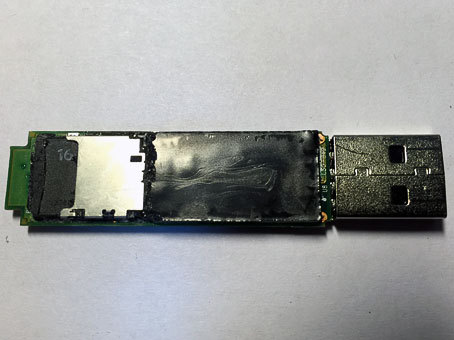
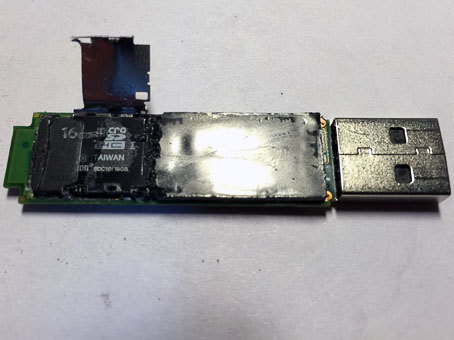
Looks like a crisis hit Kingston. In order not to bother with the hardware implementation of a full-fledged flash drive, Kingston Eagles bought Uncle Liao's MicroSD batch at a reasonable price and hung a cipher on top, abundantly filling it with quickly setting plastic. So that no one guessed, therefore. Given the impressive price for which this DT6000 is being traded on the same YandexMarket, the manufacturer’s profit is obvious.
We dig out the micro-sdshku, everything is flooded with plastic and glued on all sides. We clean the remains, except for the strapping there is nothing to watch there.
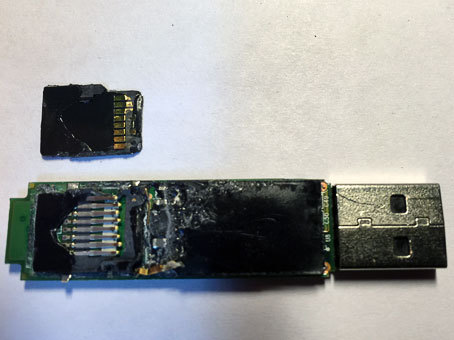
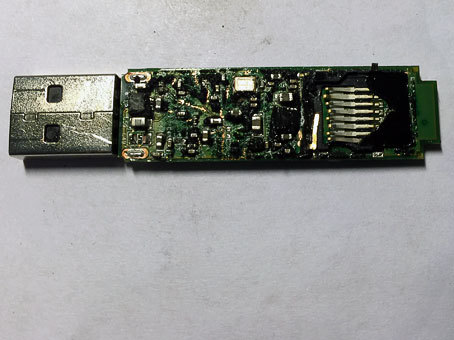
I insert the microSD plastic extracted from under the rubble into the card reader. A flash drive is defined on all its 16 gigs. From the zero sector “white noise” characteristic of encryption.

Around the middle are zeros. I look under the tail. Oops, - and here is our “boot” section! He determined the beginning and the end of the section, compared it with the previously shot image, when the rootless MicroSD was still a thoroughbred Kingston DataTraveler - no differences were found.
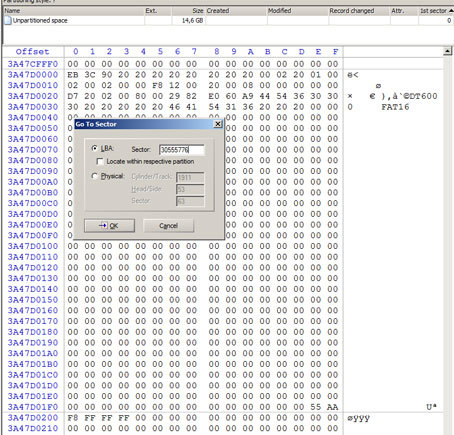
In view of the additional circumstances that have opened up, the initial hypothesis about the substitution of blocks in the NAND translation table is assigned the status of “insolvent”, and the working place is replaced by the assumption of an encryption hitch bug, she is also the builder of the micro-sd logical logging layout on the DT6000 USB interface.
I take a live 32-gig USB flash drive. I register, for the purity of the experiment, in the same VinHeks it zeros from top to bottom. To the beginning I write a previously inclined section. On it I write down the hard-won launcher, dt6000.zip and manifest.xml. I start, enter the password, a message that the encrypted partition is not found or damaged.
In the sector following the last sector of the “boot” section, I enter the entire encrypted MicroSD image.
I launch the launcher, enter the password. Bingo! An encrypted partition is found, mounted,
All user files in place - you can copy.
Despite the fact that there was a huge pile of browsing all kinds of devices, I never had to deal with a task like the one described below.
Preamble
So, the Kingston DT6000 USB Flash drive, declared by the manufacturer as a reliable file storage, using the AES256 FIPS140-2 Level 3 cryptographic algorithm.
Logically, the flash drive is organized as follows: the 68 megabyte partition formatted in FAT16 is kind of bootable. When the device is connected to the PC, autorun is triggered (or the user is prompted to launch the executable):

Then the following window comes to the fore:

Enter the password, voila - a hidden section is mounted with carefully hidden photos and videos of known content.
But one day a user had trouble, a flash drive was inserted, and the “bootloader” turned out to be empty. With a password, it turned out that stupidly there is no way to enter this password somewhere. They brought a diagnostic disk to us.
First of all, connecting the drive to the test PC and opening my favorite WinHEX hex editor, I climbed into the list of physical disks. So it is, two volumes. The first is empty, and, most importantly, in read-only mode! The second is unavailable. I shot the image from the first section, analyzed it. Both copies of FAT tables are missing in their normal form.

That is, with the ability to get files with names and structure from the “boot partition”, you can say goodbye. By “rough recovery” or recovery from known file headers (aka raw recovery), we managed to pull out some zip archive and pdf-ku. From the content of the latter, it became clear how everything was arranged, and what is missing on the boot partition.
Considering that the section was locked by the manufacturer for recording, it was clear that there could be no talk about any random formatting by the user, and the most likely reason for the section “zeroing” was a failure in the NAND processing translation table area, as a result of which part of the correct blocks was replaced by “alternative” ones.
This effect is called the “pseudo-logical problem with the flash drive” and looks like a glitch at the file system level, in fact, it is a hardware failure, in fact. So, most likely, you will have to transfer the USB flash drive to the pathological table and open it, in order to unsolder the memory chip (s) and try to collect something meaningful from the read images.
About encryption and how to collect dumps with encrypted content in general, at that moment I did not bother with my head.
Problems are supposed to be solved as they appear, so the first thing to do was to find the DT6000_Launcher with all the surroundings. On the manufacturer’s website, the product download section was empty. It is logical - it makes sense to upload files if it is assumed that you will not be able to write them (see locked record)? He threw a cry to his colleagues. The necessary files were sent. The next problem is to tell the launcher where we have encrypted.
Attempts to unlock the FAT16 partition on the flash drive itself using OS tools and record a launcher on it were unsuccessful. Attempts to launch the launcher from another medium and set the flash drive on the flash drive under investigation also proved unsuccessful. Further hardware intervention in the internals of Traveler's date became inevitable.
“Well, today some sensations await us ...” (c)
Removing the external plastic case, the researcher’s gaze revealed this:

With the exception of the USB connector, everything is flooded with plastic. It was possible to remove it with the help of a hot-air soldering station, heating the area after area to a temperature of about 150 C, after which the plastic began to slowly bend and break off in small pieces. Wielding with dental hooks and a scalpel, feeling like an archaeologist, he cleaned one side of plastic. I saw the following:

LPC3131FET180 workstation controller, 3s500e plate (it is also PLISS, PLD is a programmable logic integrated circuit) from XILINX, ROSETTA crypto module from Spyrus and Atmelovskaya ROM 25DF081A ROM cabinet. We must take on the second half, because the desired memory NAND has not yet been found.
I start to clean the second side. Something brilliant appears. Quartz? Does not look like. A couple more sweeping strokes of a sledgehammer and chisel, a shame - a card reader!


Looks like a crisis hit Kingston. In order not to bother with the hardware implementation of a full-fledged flash drive, Kingston Eagles bought Uncle Liao's MicroSD batch at a reasonable price and hung a cipher on top, abundantly filling it with quickly setting plastic. So that no one guessed, therefore. Given the impressive price for which this DT6000 is being traded on the same YandexMarket, the manufacturer’s profit is obvious.
We dig out the micro-sdshku, everything is flooded with plastic and glued on all sides. We clean the remains, except for the strapping there is nothing to watch there.


Finish line
I insert the microSD plastic extracted from under the rubble into the card reader. A flash drive is defined on all its 16 gigs. From the zero sector “white noise” characteristic of encryption.

Around the middle are zeros. I look under the tail. Oops, - and here is our “boot” section! He determined the beginning and the end of the section, compared it with the previously shot image, when the rootless MicroSD was still a thoroughbred Kingston DataTraveler - no differences were found.

In view of the additional circumstances that have opened up, the initial hypothesis about the substitution of blocks in the NAND translation table is assigned the status of “insolvent”, and the working place is replaced by the assumption of an encryption hitch bug, she is also the builder of the micro-sd logical logging layout on the DT6000 USB interface.
I take a live 32-gig USB flash drive. I register, for the purity of the experiment, in the same VinHeks it zeros from top to bottom. To the beginning I write a previously inclined section. On it I write down the hard-won launcher, dt6000.zip and manifest.xml. I start, enter the password, a message that the encrypted partition is not found or damaged.
In the sector following the last sector of the “boot” section, I enter the entire encrypted MicroSD image.
I launch the launcher, enter the password. Bingo! An encrypted partition is found, mounted,

All user files in place - you can copy.
