Yota site has been hacked
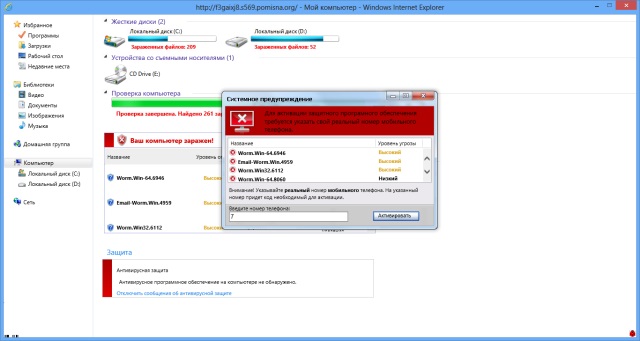
Be careful, the official website of Yota, www.yota.ru , has been attacked. A JavaScript code was introduced on the site’s pages, which, after clicking on any link the first time you log on to www.yota.ru, opens an additional browser window with a pseudo-antivirus that supposedly finds malware on the visitor’s computer and offers to get rid of it by entering the code via SMS .
The pop-up window does not contain any control elements (except for the address bar) and loads its contents from the pomisna.org subdomain registered through EvoPlus with hidden Whois data . On the main page of the site is a standard Apache stub.
A pop-up window imitates the interface of Explorer and Microsoft Security Essentials in Windows 7, as well as pork squeals of Kaspersky Anti-Virus. Then everything is standard: if you want to get rid of the virus - enter the phone number, receive an SMS with the code, enter the code in the window, and say goodbye to the money in the account.
After reporting the hack, the consequences, according to a company representative, were eliminated in about half an hour. However, the state of affairs has not changed, which suggests that the right hand does not know what the left is doing. So far, no comments about the nature of the vulnerability have been received from the company or the PR service .
Update. Six days later, a company representative distributed a messagethat the vulnerability has been fixed. The only thing that became known about its nature was that it was not found in the CMS, but the page with the standard login form for the 1C-Bitrix administrative panel stopped loading. Later it became known that the entrance to the panel is located at a different address and is possible only from the company's internal network.
Source: upweek.ru
