We deploy an OpenVPN server with a control panel in the InfoboxCloud cloud and configure access for clients
The process of setting up and managing a VPN on a Linux server usually takes a lot of time. And if you can configure it once and forget it, then it’s necessary to manage VPN users periodically and it would be nice if an ordinary employee of the company could do it without access rights to the server and SSH in general. A scenario is often used when VPN is used to organize access to the internal network of the cloud to connect virtual servers to the company's corporate network. Even for yourself, quickly raising a VPN can be useful.
In this article, in just a few minutes, we will set up an OpenVPN server with the ability to easily manage VPN servers, users and organizations and run it all in InfoboxCloud. This cloud is present in the regions of Moscow and Amsterdam, so you can use a VPN both for corporate purposes and to introduce yourself as a resident of the Netherlands on the network (for example, to use services that are not available in your country).

On the server we will use the Pritunl project , which is a control panel that automates the management of OpenVPN configurations. Pritunl sources are open and available on github. The free version is more than enough to use. Paid allows you to send access data by email or configure automatic fault tolerance of the service (which is not very important for InfoboxCloud, because the cloud itself works in a failover cluster) and manage load balancing between multiple servers.
At the same time in blizhaysheee InfoboxCloud will server template with pre-installed and can be Pritunl VPN-server for creating 1 click.
After connecting to the server from Ubuntu 14.04 via SSH, run the command:
Open in browser
The article uses a test address
It is proposed to configure the database path.
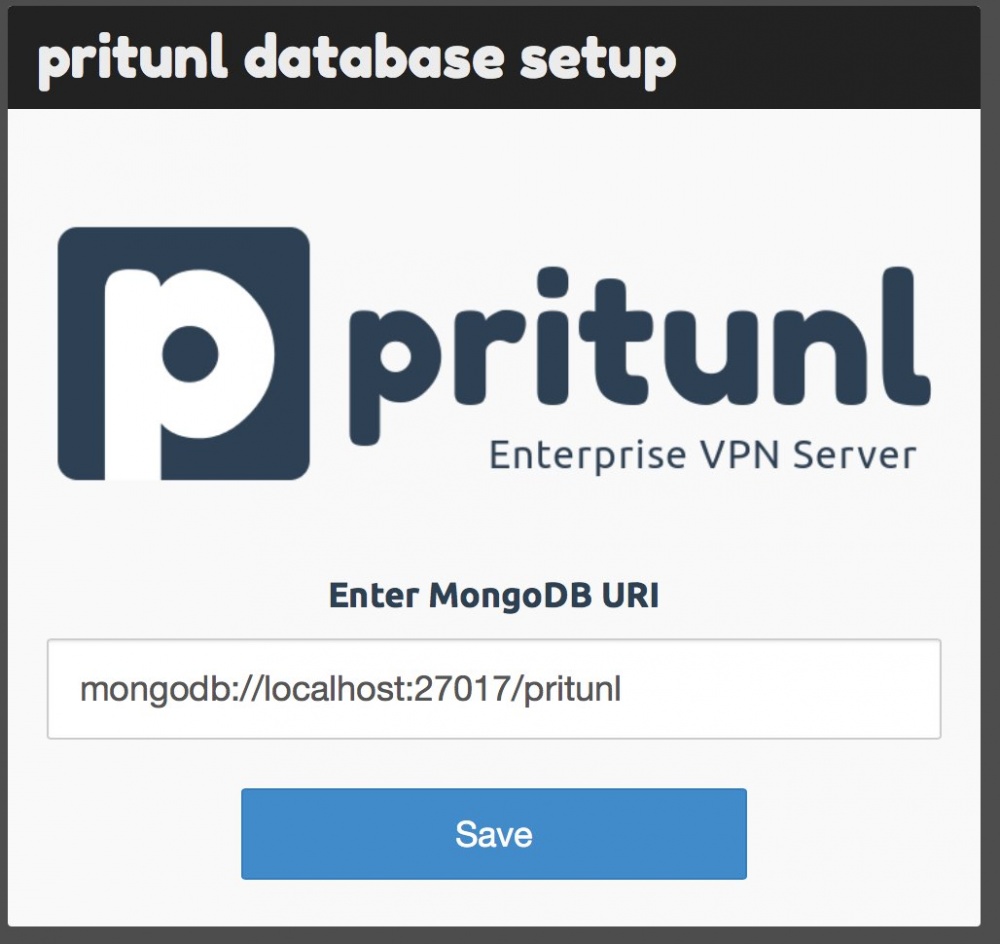
Just click “Save.” The login window will open.
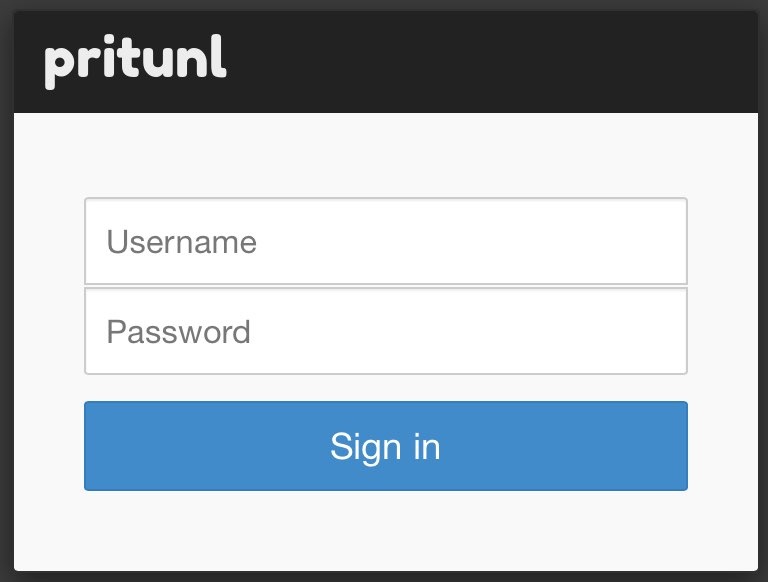
Use:
After logging in, you will be prompted to change the password (which is highly recommended), specify the SMTP server data for sending letters (optional) and the API key for VPN software management is displayed. Detailed API documentation here . If you leave the IP address as it is, the VPN will work through the Infobox public network (great for using the Internet from the Netherlands).
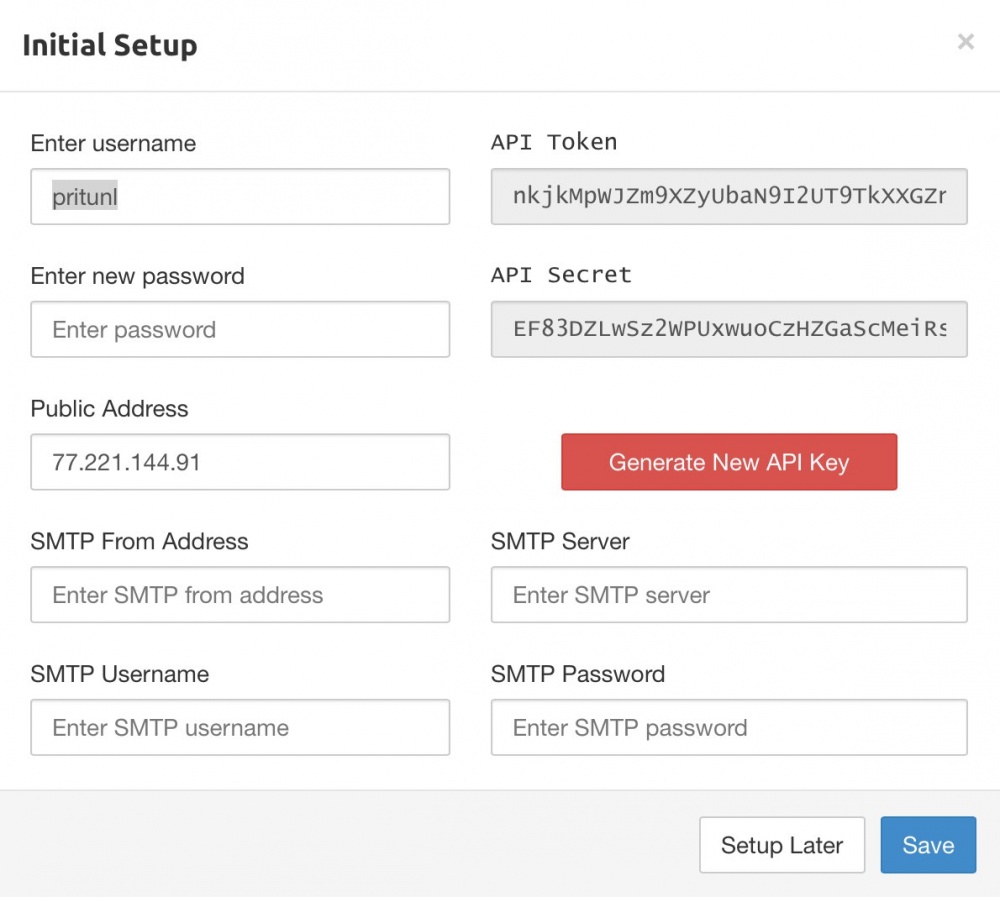
After filling out the form, you will be taken to the control panel. So far, there are no VPN users in the system.
Go to the "Users" section.
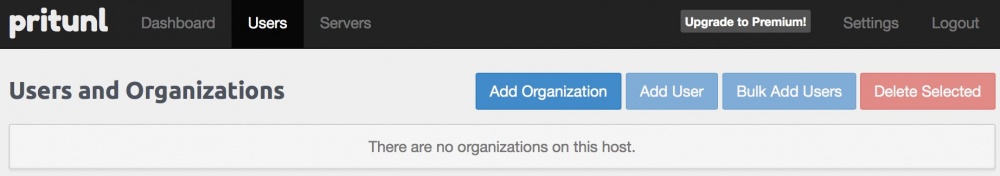
Add an organization.
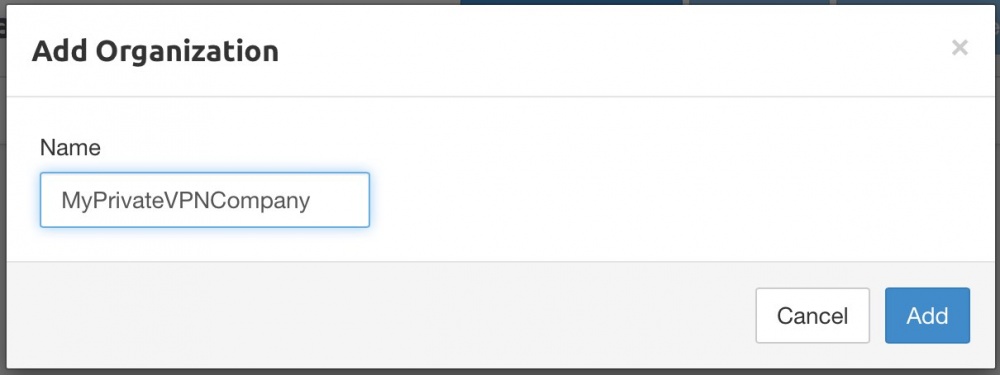
Now add the user.
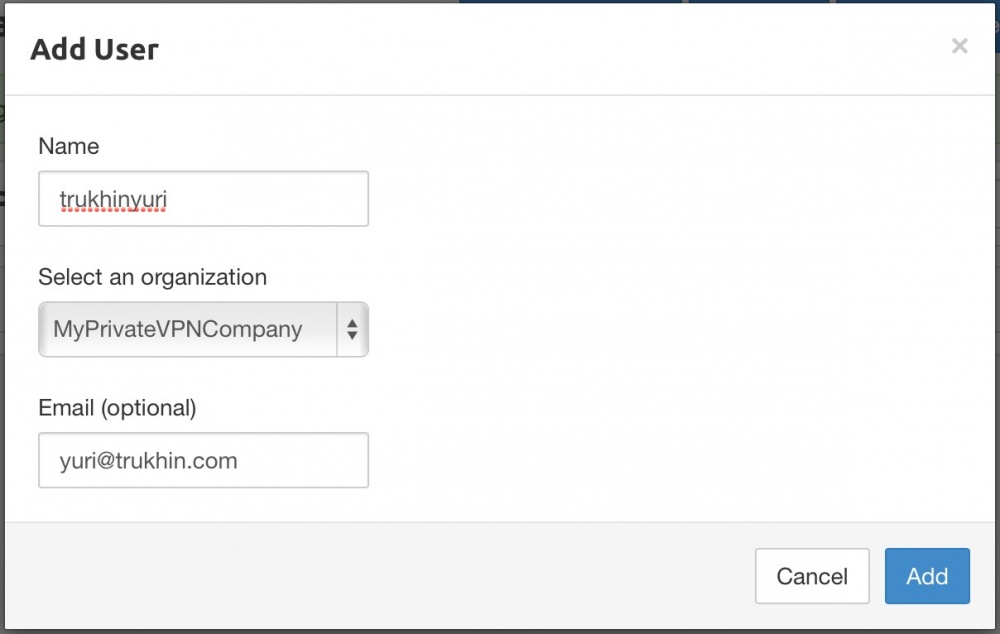
It's time to finally create our VPN server. Click on the “Servers” button.
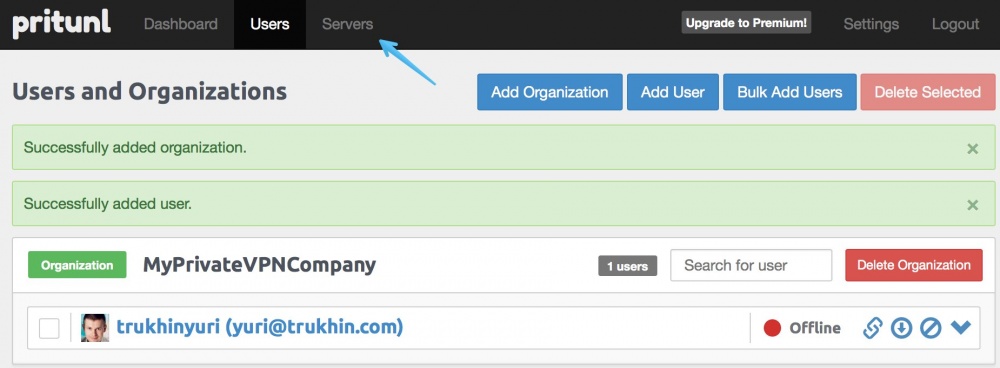
Click "Add server".
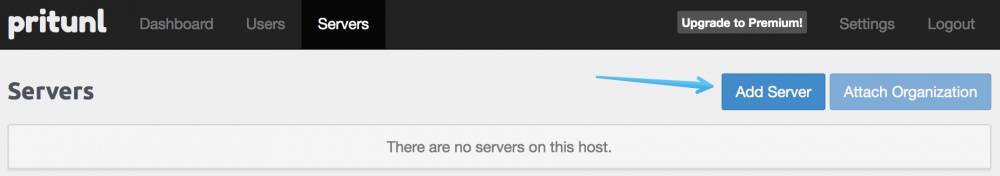
Enter the name of the VPN server (must match the domain directed to the VPN server! ) You can configure DNS, choose the way VPN works, allow multiple devices to connect at the same time, and you can even use two-factor authentication with Google Authenticator.
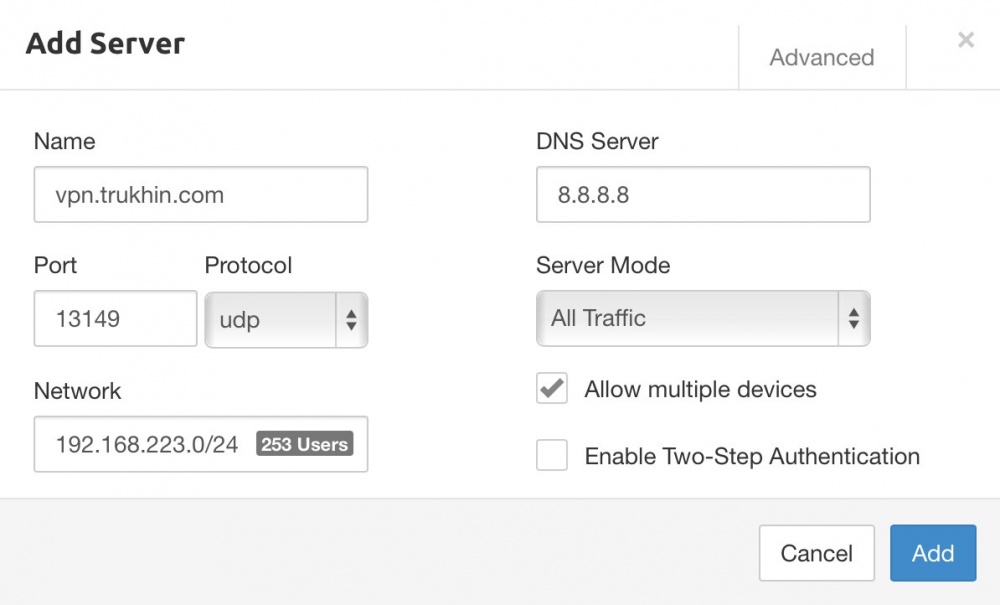
Now attach the organization (with all users) to the VPN server by clicking “Attach Organization”.
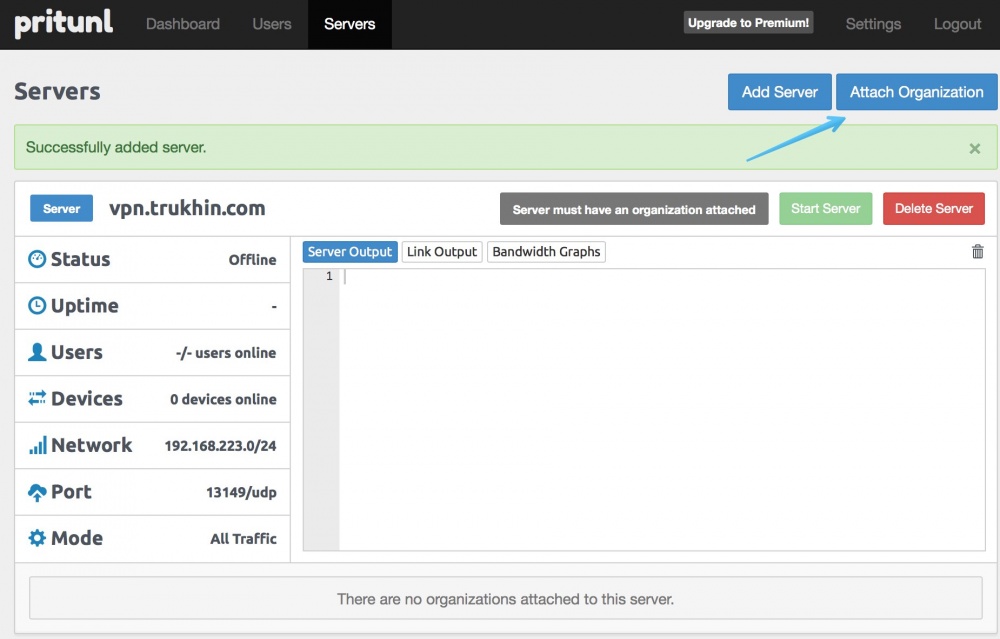
We are already offered our organization and VPN server. Just hit Attach.
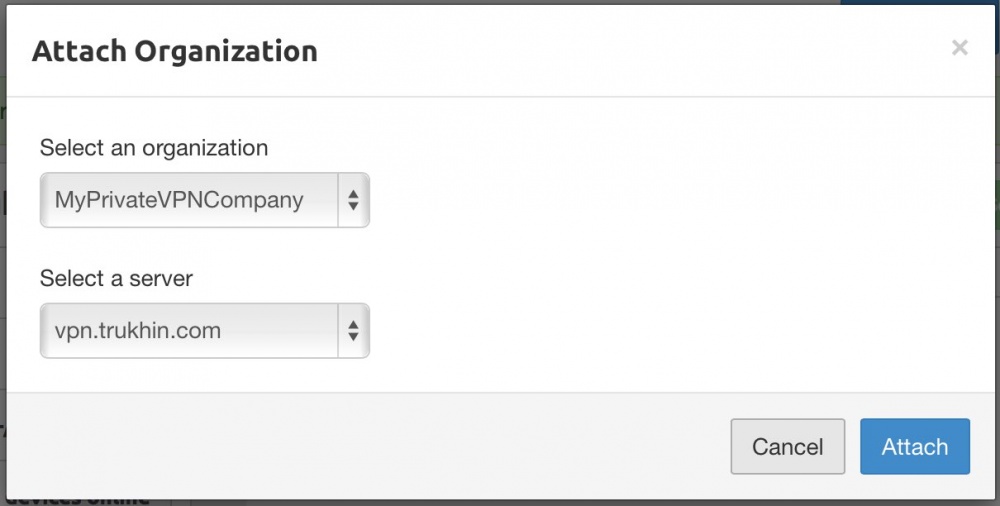
All is ready! Click “Start server” to start the VPN server.
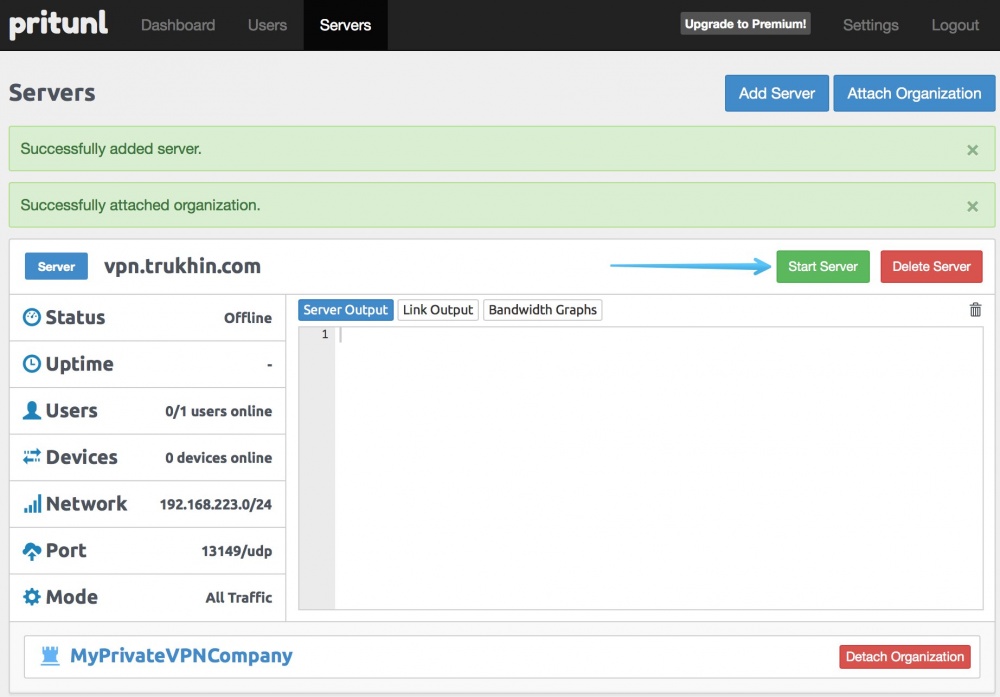
Our VPN server has been successfully launched!
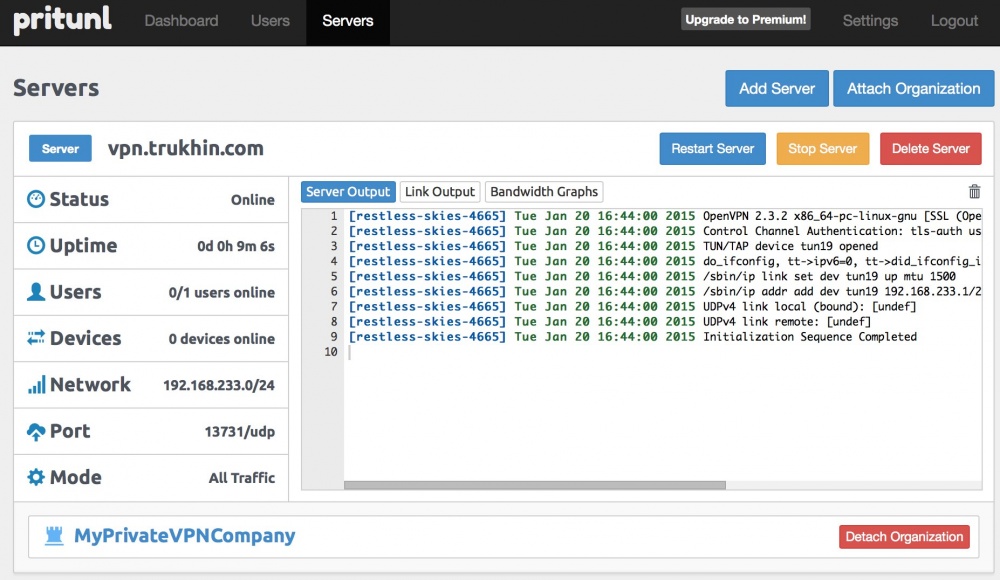
Now it remains only to download the OpenVPN configuration file for the user.
This is a very common scenario used by companies. Servers except the VPN server and the web server are not assigned a public ip address and they do not have access to an external network. The user connects via VPN and enters the company's internal network in the cloud.
In order for this scenario to work, first look in the InfoboxCloud control panel for the private IP addresses of the servers that you need access to.

When creating a VPN server in pritunl, select the “Local Traffic Only” server mode and set the cidr of the subnet, as shown in the screenshot.

After this, as before, add the company to the VPN server, download the settings for user connection again and connect to the VPN. Now you can connect to servers accessible only from the private InfoboxCloud network.

You can use any OpenVPN client to connect, including setting up a connection from a router if it supports OpenVPN (for example, Mikrotik). We will consider ways to connect from the desktop.
Download the OpenVPN client for Windows from here .
Install the client with the default settings. In the process, agree to install the OpenVPN driver.
Then download the OpenVPN configuration file from the user section of your VPN server:
Install 7zip and unzip the downloaded tar file.
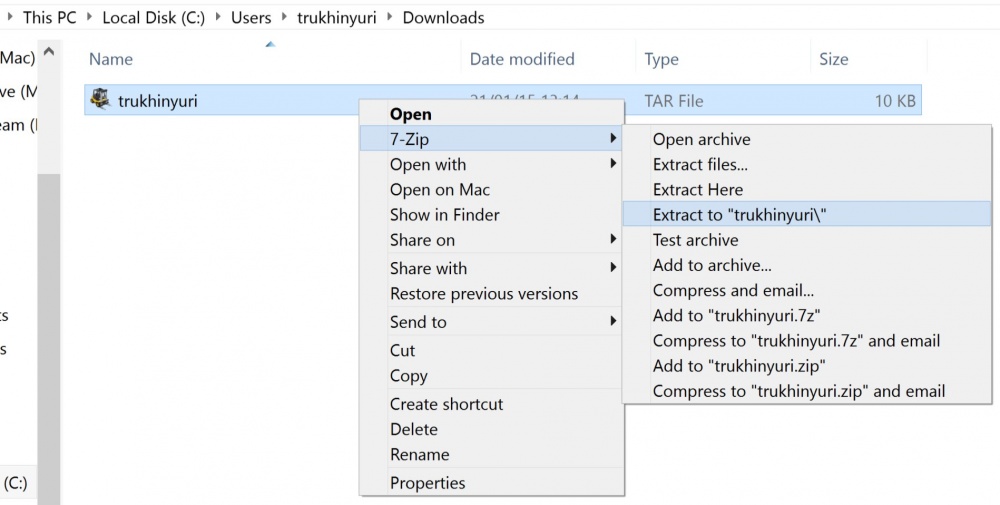
Copy the .ovpn file to the directory
Launch OpenVPN Gui from the desktop with administrator rights (in the properties of the shortcut you can set the launch with administrator rights permanently).
In the system tray, right-click on the OpenVPN shortcut and select “Connect”.
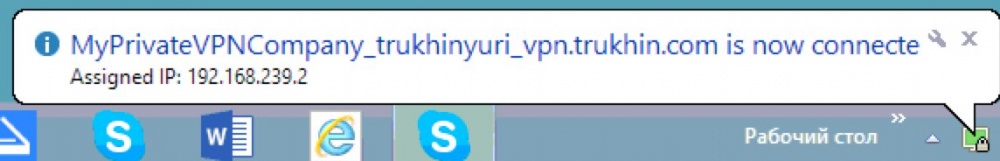
The connection will be successfully established.
Download Tunnelblick from here and install it.
Download the OpenVPN configuration file from the user section of your VPN server:

Install The Unarchiver to unzip the tar file without opening the terminal.
Unzip the tar file. Then double-click on the .ovpn configuration file. Allow the use of the configuration file only for yourself or for all users (optional).
Enter the administrator password.
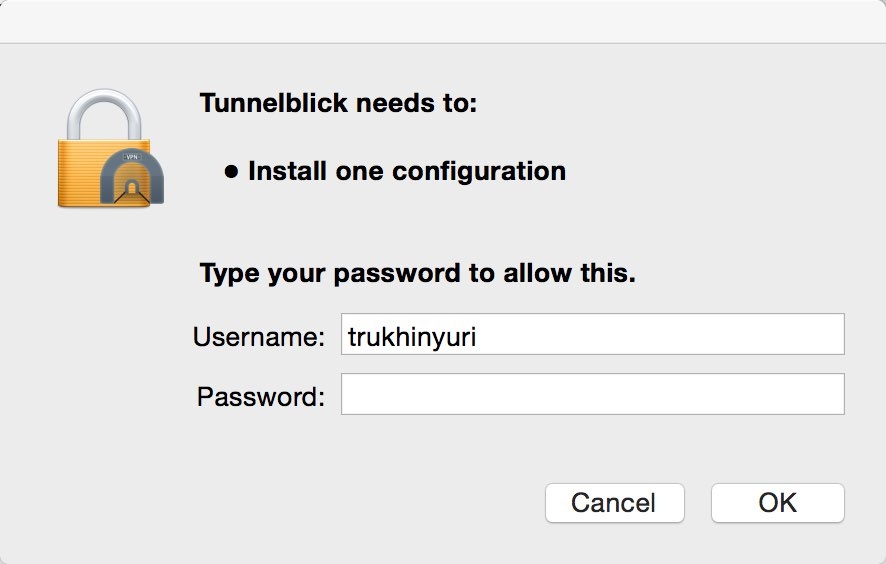
In the menu bar, click on the Tunnelblick icon and select “Connect”.
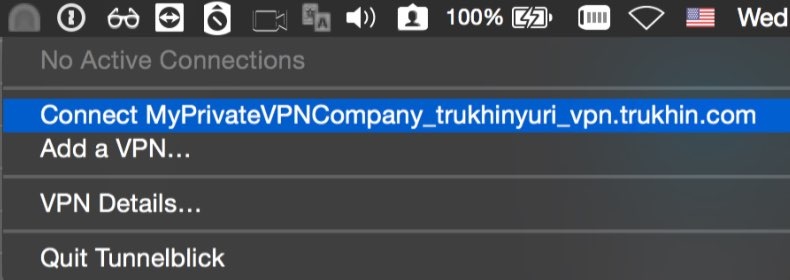
The connection will be successfully established.
Open a terminal and enter the following command:
Download the OpenVPN configuration file from the user section of your VPN server: The

tar file will load. In the terminal, go to the directory where the file was downloaded:
Unzip the file (the file name will match the username):
Due to an error in Network Manager, we cannot import the ovpn file directly. But there is a workaround:
Click on the Network Manager icon and select "Edit connections":

In the Network manager, click Add and select "Import a saved vpn configuration" and click "create":

Select the modified ovpn configuration file from the "OpenVPN" folder and click "Open":

Enter “Advanced” -> “TLS Authentication” and set “Key Direction” to the same as “key-direction” in the original ovpn configuration file. In our case, it is "1".

Click “Save” and close all Network manager windows. Connect to the VPN server as shown in the screenshot below:

You have successfully connected to the VPN from Ubuntu Desktop.
In this article, we learned how to quickly deploy a VPN server with a web interface in InfoboxCloud . If you want to try the cloud server, send us your email and we will provide a free trial version of the cloud for 15 days.
If you cannot write comments, ask a question in the InfoboxCloud Community . If you find a mistake in the article, the author will gladly correct it. Please write to the PM or e-mail about it.
Successful work!
In this article, in just a few minutes, we will set up an OpenVPN server with the ability to easily manage VPN servers, users and organizations and run it all in InfoboxCloud. This cloud is present in the regions of Moscow and Amsterdam, so you can use a VPN both for corporate purposes and to introduce yourself as a resident of the Netherlands on the network (for example, to use services that are not available in your country).

On the server we will use the Pritunl project , which is a control panel that automates the management of OpenVPN configurations. Pritunl sources are open and available on github. The free version is more than enough to use. Paid allows you to send access data by email or configure automatic fault tolerance of the service (which is not very important for InfoboxCloud, because the cloud itself works in a failover cluster) and manage load balancing between multiple servers.
At the same time in blizhaysheee InfoboxCloud will server template with pre-installed and can be Pritunl VPN-server for creating 1 click.
What do we need to configure
- We hope you already have an account with InfoboxCloud . If not yet, create one .
Then create a cloud server with Ubuntu 14.04 in the control panel (do not forget to select 1 public IP address for the server and set the necessary channel speed to gigabit). When creating a server, you need to check the "enable OS kernel management" box. After creating the server, your email will receive data for accessing the server. Connect to the server via SSH . - We also need a domain or subdomain to organize a VPN entry point. Domain A record should be directed to the ip – address of the created cloud server.
Install Pritunl
After connecting to the server from Ubuntu 14.04 via SSH, run the command:
apt-key update && apt-get update && apt-get -y upgrade && apt-get -y install python-software-properties && apt-get -y install software-properties-common && add-apt-repository -y ppa:pritunl && apt-get update && apt-get -y install pritunl
Configure the VPN server in the web interface
Open in browser
https://адрес_домена_направленного_на_сервер:9700
The article uses a test address
https://vpn.trukhin.com:9700
It is proposed to configure the database path.

Just click “Save.” The login window will open.

Use:
- Login: pritunl
- Password: pritunl
After logging in, you will be prompted to change the password (which is highly recommended), specify the SMTP server data for sending letters (optional) and the API key for VPN software management is displayed. Detailed API documentation here . If you leave the IP address as it is, the VPN will work through the Infobox public network (great for using the Internet from the Netherlands).

After filling out the form, you will be taken to the control panel. So far, there are no VPN users in the system.

Go to the "Users" section.

Add an organization.

Now add the user.

It's time to finally create our VPN server. Click on the “Servers” button.

Click "Add server".

Enter the name of the VPN server (must match the domain directed to the VPN server! ) You can configure DNS, choose the way VPN works, allow multiple devices to connect at the same time, and you can even use two-factor authentication with Google Authenticator.

Now attach the organization (with all users) to the VPN server by clicking “Attach Organization”.

We are already offered our organization and VPN server. Just hit Attach.

All is ready! Click “Start server” to start the VPN server.

Our VPN server has been successfully launched!

Now it remains only to download the OpenVPN configuration file for the user.

InfoboxCloud Internal Network Features
This is a very common scenario used by companies. Servers except the VPN server and the web server are not assigned a public ip address and they do not have access to an external network. The user connects via VPN and enters the company's internal network in the cloud.
In order for this scenario to work, first look in the InfoboxCloud control panel for the private IP addresses of the servers that you need access to.

When creating a VPN server in pritunl, select the “Local Traffic Only” server mode and set the cidr of the subnet, as shown in the screenshot.

After this, as before, add the company to the VPN server, download the settings for user connection again and connect to the VPN. Now you can connect to servers accessible only from the private InfoboxCloud network.

Configuring OpenVPN Clients
You can use any OpenVPN client to connect, including setting up a connection from a router if it supports OpenVPN (for example, Mikrotik). We will consider ways to connect from the desktop.
Configuring OpenVPN Client on Windows
Download the OpenVPN client for Windows from here .
Install the client with the default settings. In the process, agree to install the OpenVPN driver.
Then download the OpenVPN configuration file from the user section of your VPN server:

Install 7zip and unzip the downloaded tar file.

Copy the .ovpn file to the directory
C:\Program files\OpenVPN\config
Launch OpenVPN Gui from the desktop with administrator rights (in the properties of the shortcut you can set the launch with administrator rights permanently).
In the system tray, right-click on the OpenVPN shortcut and select “Connect”.

The connection will be successfully established.

Configuring OpenVPN Client on OS X
Download Tunnelblick from here and install it.
Download the OpenVPN configuration file from the user section of your VPN server:

Install The Unarchiver to unzip the tar file without opening the terminal.
Unzip the tar file. Then double-click on the .ovpn configuration file. Allow the use of the configuration file only for yourself or for all users (optional).

Enter the administrator password.

In the menu bar, click on the Tunnelblick icon and select “Connect”.

The connection will be successfully established.

Configuring OpenVPN Client on Ubuntu Desktop
Open a terminal and enter the following command:
sudo apt-get install network-manager-openvpn
Download the OpenVPN configuration file from the user section of your VPN server: The

tar file will load. In the terminal, go to the directory where the file was downloaded:
cd ~/Downloads/
Unzip the file (the file name will match the username):
tar -xvf trukhinyuri.tar
Due to an error in Network Manager, we cannot import the ovpn file directly. But there is a workaround:
- Create the “OpenVPN” folder and copy the ovpn configuration file that you unpacked earlier from the archive there.
- Open the ovpn configuration file from the OpenVPN folder in a text editor.
- Create the ca.crt file in the OpenVPN folder: copy the text between it
from the ovpn configuration file.и - Create a client.crt file in the OpenVPN folder: copy the text between it
from the ovpn configuration file.и - Create a client.key file in the OpenVPN folder: copy the text between it
from the ovpn configuration file.и - Create a ta.key file in the OpenVPN folder: copy the text between it
from the ovpn configuration file.и - Open the ovpn configuration file from the “OpenVPN” folder and edit it: delete the section
and all below and add to the end:ca ca.crt cert client.crt key client.key tls-auth ta.key
Click on the Network Manager icon and select "Edit connections":

In the Network manager, click Add and select "Import a saved vpn configuration" and click "create":

Select the modified ovpn configuration file from the "OpenVPN" folder and click "Open":

Enter “Advanced” -> “TLS Authentication” and set “Key Direction” to the same as “key-direction” in the original ovpn configuration file. In our case, it is "1".

Click “Save” and close all Network manager windows. Connect to the VPN server as shown in the screenshot below:

You have successfully connected to the VPN from Ubuntu Desktop.
Conclusion
In this article, we learned how to quickly deploy a VPN server with a web interface in InfoboxCloud . If you want to try the cloud server, send us your email and we will provide a free trial version of the cloud for 15 days.
If you cannot write comments, ask a question in the InfoboxCloud Community . If you find a mistake in the article, the author will gladly correct it. Please write to the PM or e-mail about it.
Successful work!
