Report of the Information Security Monitoring Center for the first half of 2018
We publish the seventh in a row regular report of our Monitoring Center, dedicated to the analysis of recorded events and information security incidents.
Main numbers:
Event sources are network and host IDS, network devices, security scanners, anti-virus solutions and honeypots.
As part of internal processing, we classify incidents according to the resources affected.
An analyst at the Monitoring Center arbitrarily determines the degree of criticality if he believes that an incident can lead to serious negative consequences.

In the period from January 1 to June 30, 2018 , employees of the Monitoring Center monitored information systems of organizations with a total number of connected nodes of about 28,200 (workplaces, web, mail, file storages, etc.). Due to the growing interest in the creation and operation of information security monitoring centers, we were able to attract new regular customers in the first half of 2018 and launch several pilot projects.
In the six months of 2018, sensors recorded 112 million information security events.
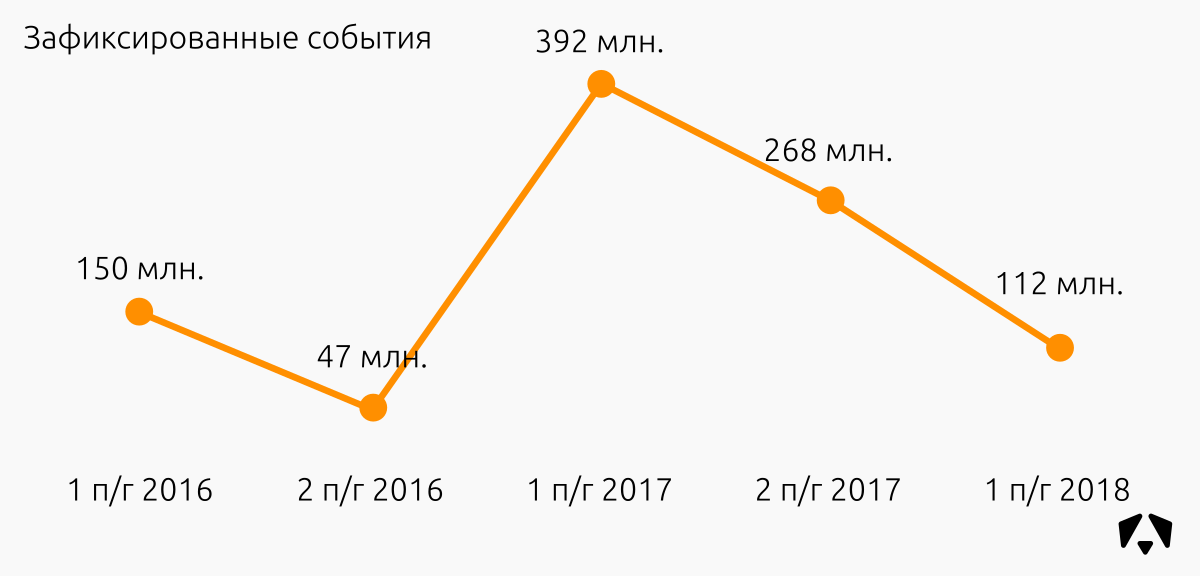
The decrease in the number of registered IS events, taking into account the increase in the number of monitored resources and incidents, is due to the following factors:
434 incidents were recorded .
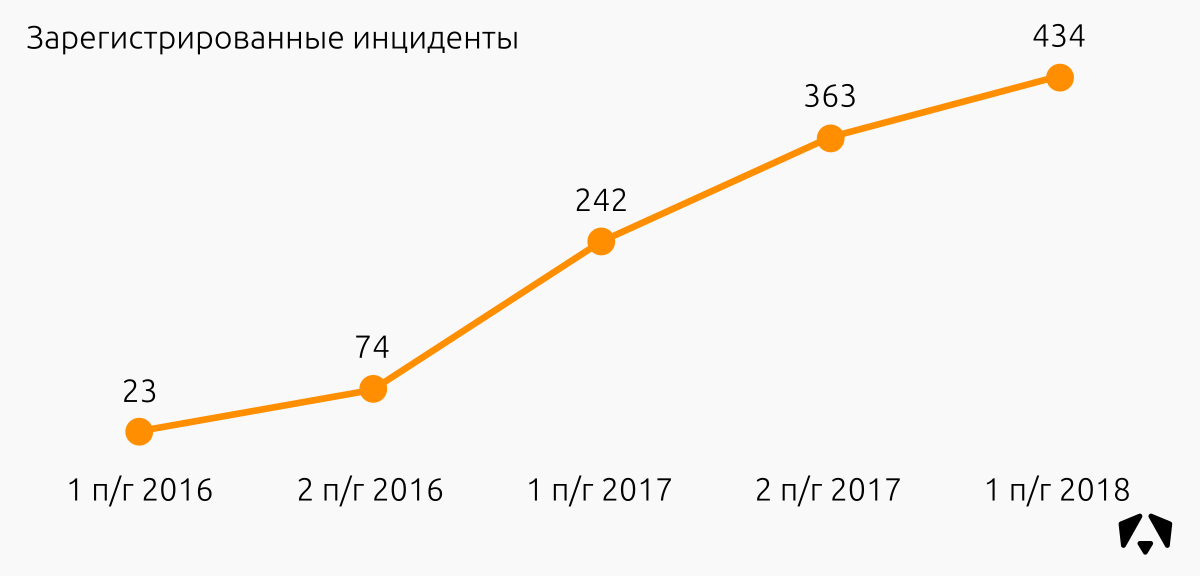
The 20% increase in the number of incidents compared to the second half of 2017 is due to the fact that new customers actively joined the Monitoring Center. And the new infrastructure on monitoring is almost guaranteed a surge in the number of detected incidents that the owner of the infrastructure previously simply could not notice. It is necessary to deal with this "new peak", and the number of recorded incidents is sharply reduced.
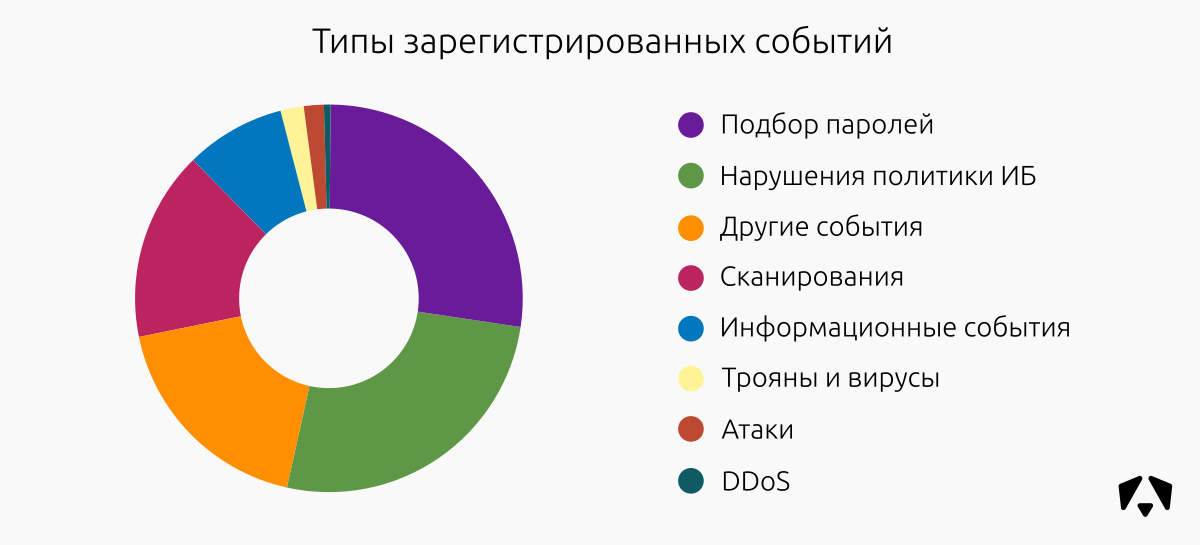
The distribution of recorded events by type did not change much compared with the second half of 2017. The most noticeable change is that the attempts to pick up passwords for various services take the first place. Policy violations, scans and informational events still remain in the "top".
The number of events in the "Scanning" category has increased. In the first half of the year, we increased the number of customers, and, consequently, the number of nodes. If the monitored node looks directly to the Internet, then it is daily exposed to a large number of scans by bots. Most clients take priority in controlling attacks from the external network, so they put nodes with white addresses on the monitoring. From this increase in the "Scan" and the reduction of "Informational events", more characteristic of internal nodes.
Among the identified 434 incidents:
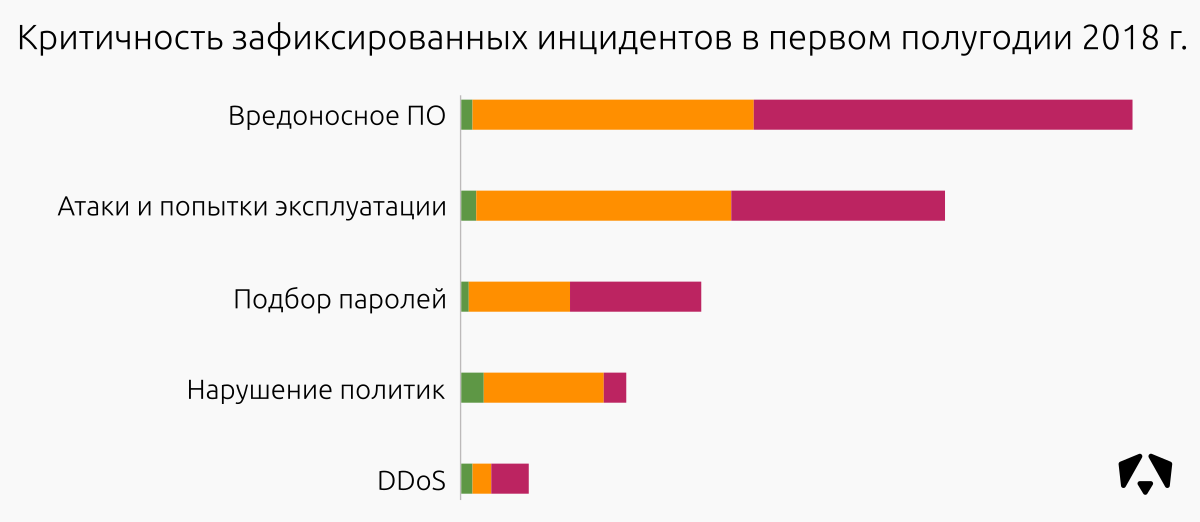
By the largest class of malware, we observed the following trends:
As for the "Exploitation of Vulnerabilities", we continue to observe a large number of attempts to exploit vulnerabilities in Apache Struts, Drupalgeddon, and EternalBlue.
A large number of incidents were instituted to exploit the EternalBlue vulnerability. It sounds sad, but statistics show that users have not yet been protected from such sensational vulnerabilities. Despite the fact that the download of encryptors through this vulnerability is already minimal, it is actively used to distribute other malware. And if the encrypted data is visible immediately, then the activity of other malicious software can not even be noticed by an ordinary user.
For example, at the end of June, we conducted a study of the machine infected with the coder. We found that the destructive actions were carried out through a remote connection to the system. The attacker launched an encryption program and, after a few minutes, disconnected from the victim's node.
Our researchers have found the file of the launched encrypter disguised as the svchost.exe process (the encryption program of the GlobeImposter 2.0 family, as it turned out during the detailed analysis of the file), as well as traces of the launch of other suspicious programs. Among them was the ProcessHacker utility installed (with the KProcessHacker driver). With its help, the attacker has completed the privileged processes and freed the files occupied by the processes for their subsequent encryption. The hacker did not stop there and, taking the opportunity, he introduced a miner into the infected system (why not take the maximum?).
Mining files for Litecoin (LTC) mining were found in the system directory. Among them was the miner's file itself, libraries for maintaining multithreading and sending HTTP requests, as well as a program that collected and launched all of this with the parameters the attacker needed. This file was added to the Task Scheduler and started at every system startup.
If the attacker had not launched a cryptographer on the hacked system, then perhaps the owner of the automated workplace would not have noticed a third-party presence. And the resources of the system would be used for the extraction of cryptocurrencies and / or attacks on other users in the local network.
The remaining mass of incidents in the category are attempts to exploit XSS, the introduction of PHP and SQL injections.
Distribution of information security incidents relative to the days of the week in the first half of 2018:
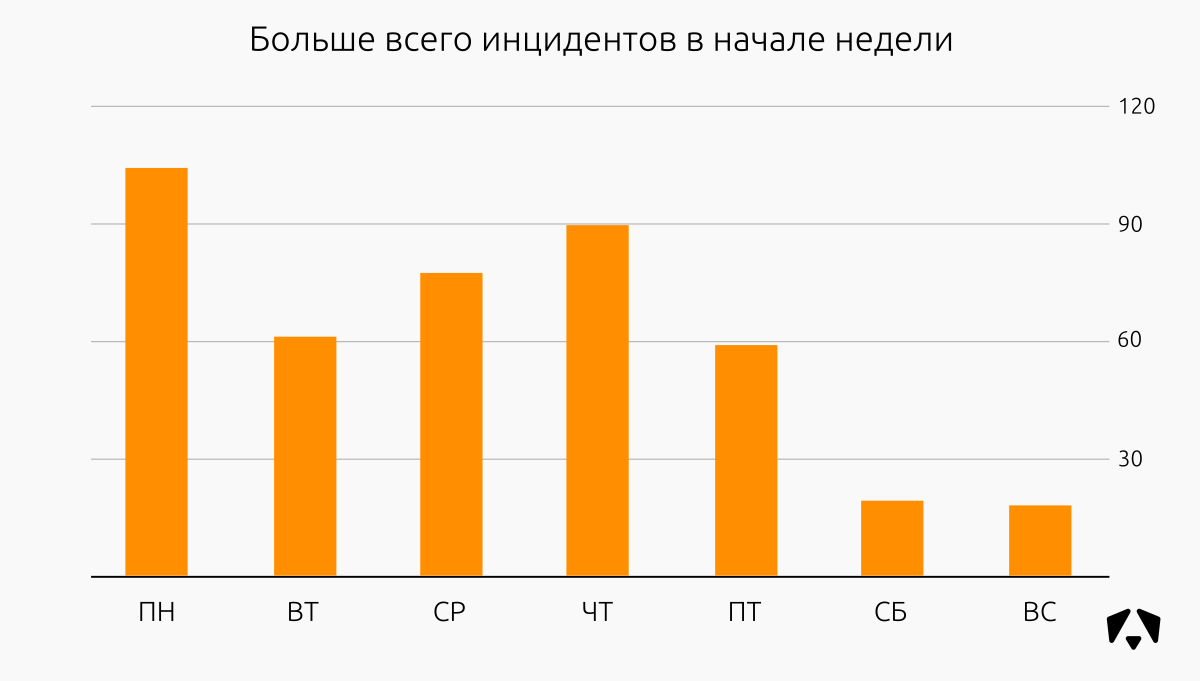
Usually phishing mailings are conducted on Monday, they send malware disguised as reconciliations, acts, etc. Most likely, such activity is aimed at people who have not yet retired from the weekend. We also connect the bulk of new customers from the beginning of the week, which also gives a big boost in the events, especially for categories such as password selection, attack and exploitation of vulnerabilities.
Distribution of information security incidents in the first half of 2018:

The increase in incidents is related to the expansion of our clients' networks. At least 2 organizations increased the number of sensors at controlled sites by April. Plus, in the spring and summer there were a lot of pilot projects.
Also, our signature-based analysts constantly write rules for fresh vulnerabilities, which helps to catch new attacks on client resources.
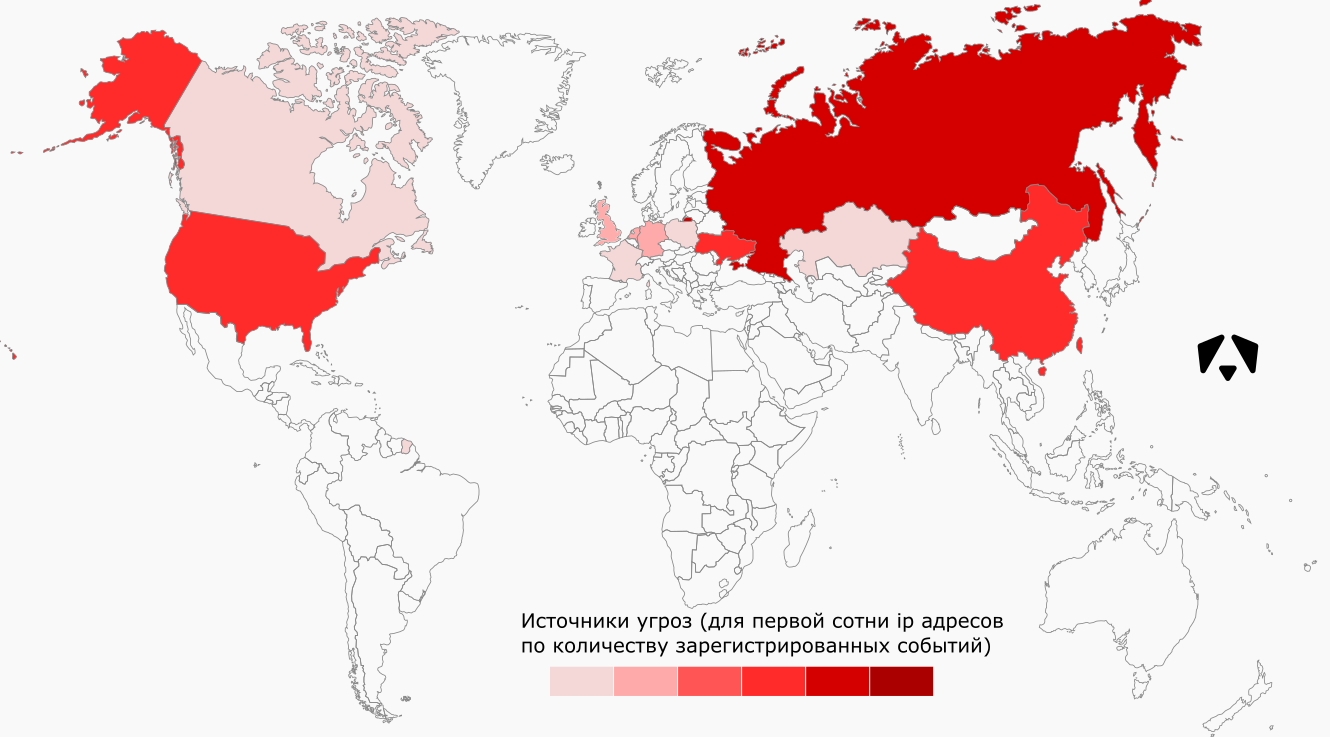
The sources of attacks in this case are IP addresses that were participants in the network interaction with controlled addresses and attempted to damage the infrastructure.
The map shows the location of the first hundred IP addresses by the number of registered events. Most of these addresses are located in Russia, Ukraine, China, USA, Germany and the Netherlands.
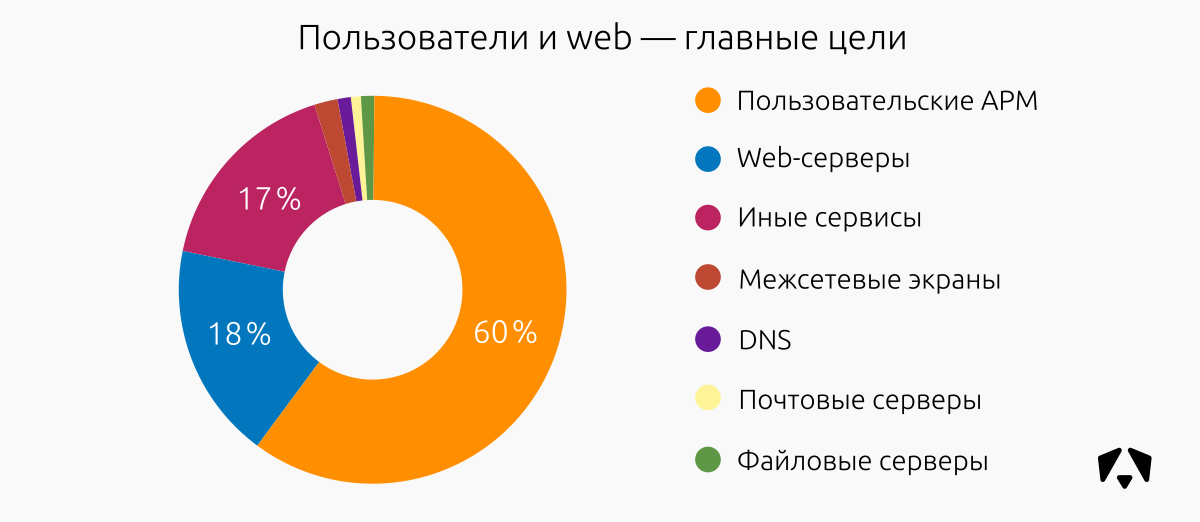
In the first half of 2018, user workstations were the most frequently affected by unwanted effects. These are 60% of all incidents on controlled resources. In second place are attacks on web-servers and other services.
The main types of attacks on web brutfors and attempts to exploit vulnerabilities, including the Apache web server. On user workstation - malware, attempts to exploit vulnerabilities in browsers. A large number of miners established by illegal means.
Previous articles:
Main numbers:
- 112 million events were recorded (two times less than in the previous period).
- 434 incidents were confirmed (we processed an average of three incidents per day).
- 28,200 nodes on monitoring (in two years the number of monitored nodes increased 19 times).
We define in terms of
- An information security event is an identified occurrence of a certain state of a system, service, or network indicating a potential violation of an information security policy or the failure of protective measures, or the occurrence of a previously unknown situation that may be related to security.
- An information security incident is the occurrence of one or more unwanted or unexpected security events that are associated with a significant likelihood of business operations being compromised and creating an information security threat.
Event sources are network and host IDS, network devices, security scanners, anti-virus solutions and honeypots.
As part of internal processing, we classify incidents according to the resources affected.
| High criticality | Incidents related to key server segment resources or critical user segment resources (resources that handle critical information from a business, financial or legal point of view). |
| Average criticality | Incidents related to non-critical server segment resources. |
| Low criticality | Incidents associated with non-critical resources of the user segment (ordinary user). |
An analyst at the Monitoring Center arbitrarily determines the degree of criticality if he believes that an incident can lead to serious negative consequences.
Monitoring results

In the period from January 1 to June 30, 2018 , employees of the Monitoring Center monitored information systems of organizations with a total number of connected nodes of about 28,200 (workplaces, web, mail, file storages, etc.). Due to the growing interest in the creation and operation of information security monitoring centers, we were able to attract new regular customers in the first half of 2018 and launch several pilot projects.
In the six months of 2018, sensors recorded 112 million information security events.

The decrease in the number of registered IS events, taking into account the increase in the number of monitored resources and incidents, is due to the following factors:
- Our signature analytics are refining signatures that give a large number of false-positive responses in a particular controlled information system. Thanks to the already significant experience in writing rules and evaluating their behavior in different organizations, signatures have become less dependent on network features and more unified, while at the same time not losing effectiveness in the presence of “bad” traffic.
- Some rules of the AM Rules database have been optimized. Due to this, many similar events are aggregated.
- Thanks to the first two points, the Monitoring Center responds faster to DDoS attacks and other information security incidents that manifest themselves in a large number of signature triggers, and helps prevent their development at an early stage.
434 incidents were recorded .

The 20% increase in the number of incidents compared to the second half of 2017 is due to the fact that new customers actively joined the Monitoring Center. And the new infrastructure on monitoring is almost guaranteed a surge in the number of detected incidents that the owner of the infrastructure previously simply could not notice. It is necessary to deal with this "new peak", and the number of recorded incidents is sharply reduced.

| “Informational event” - informational events that may be useful in the analysis of an incident. “Attack or exploitation” - events that indicate attempts to remotely execute a code or exploit vulnerabilities in controlled resources. "Scanning" - events that indicate the study of the network before attempting an attack. “Password Selection” - events that indicate attempts to gain access to monitored resources by selecting authentication data. | “Violation of the IS policy” - events that indicate actions that allegedly violate the requirements of the IS Policy of a controlled organization. “Trojans and viruses” are events indicating the fact of infection of controlled resources with viruses or malware activity. “DDoS” - events that indicate attempts to carry out distributed denial of service attacks. |
The distribution of recorded events by type did not change much compared with the second half of 2017. The most noticeable change is that the attempts to pick up passwords for various services take the first place. Policy violations, scans and informational events still remain in the "top".
The number of events in the "Scanning" category has increased. In the first half of the year, we increased the number of customers, and, consequently, the number of nodes. If the monitored node looks directly to the Internet, then it is daily exposed to a large number of scans by bots. Most clients take priority in controlling attacks from the external network, so they put nodes with white addresses on the monitoring. From this increase in the "Scan" and the reduction of "Informational events", more characteristic of internal nodes.
Recorded incidents
Among the identified 434 incidents:
| Incident class | Low criticality | Average criticality | High criticality | Total incidents | Share of incidents |
| Malicious software | 3 | 75 | 101 | 179 | 41% |
| Attacks and attempts to exploit vulnerabilities | four | 68 | 57 | 129 | thirty% |
| Password Selection | 2 | 27 | 35 | 64 | 15% |
| Violation of information security policy | 6 | 32 | 6 | 44 | ten% |
| DDoS | 3 | five | ten | 18 | four% |

By the largest class of malware, we observed the following trends:
- The more nodes on the monitoring - the more incidents with malware.
- As in the second quarter of 2017, infections by the WannaCry and Petya / notPetya malware families continue. Despite the universal coverage of this problem, there are still a lot of vulnerable nodes.
- Most of the malicious files found are cryptocurrency mining software. Hackers have become a bit “kinder” and are trying to capitalize on user resources.
- Also often we find adware potentially unwanted software. Most users download it along with hacked or free software and when installing software to quickly find drivers, for example, DriverPack and analogues.
As for the "Exploitation of Vulnerabilities", we continue to observe a large number of attempts to exploit vulnerabilities in Apache Struts, Drupalgeddon, and EternalBlue.
A large number of incidents were instituted to exploit the EternalBlue vulnerability. It sounds sad, but statistics show that users have not yet been protected from such sensational vulnerabilities. Despite the fact that the download of encryptors through this vulnerability is already minimal, it is actively used to distribute other malware. And if the encrypted data is visible immediately, then the activity of other malicious software can not even be noticed by an ordinary user.
For example, at the end of June, we conducted a study of the machine infected with the coder. We found that the destructive actions were carried out through a remote connection to the system. The attacker launched an encryption program and, after a few minutes, disconnected from the victim's node.
Our researchers have found the file of the launched encrypter disguised as the svchost.exe process (the encryption program of the GlobeImposter 2.0 family, as it turned out during the detailed analysis of the file), as well as traces of the launch of other suspicious programs. Among them was the ProcessHacker utility installed (with the KProcessHacker driver). With its help, the attacker has completed the privileged processes and freed the files occupied by the processes for their subsequent encryption. The hacker did not stop there and, taking the opportunity, he introduced a miner into the infected system (why not take the maximum?).
Mining files for Litecoin (LTC) mining were found in the system directory. Among them was the miner's file itself, libraries for maintaining multithreading and sending HTTP requests, as well as a program that collected and launched all of this with the parameters the attacker needed. This file was added to the Task Scheduler and started at every system startup.
If the attacker had not launched a cryptographer on the hacked system, then perhaps the owner of the automated workplace would not have noticed a third-party presence. And the resources of the system would be used for the extraction of cryptocurrencies and / or attacks on other users in the local network.
The remaining mass of incidents in the category are attempts to exploit XSS, the introduction of PHP and SQL injections.
Distribution of information security incidents relative to the days of the week in the first half of 2018:

Usually phishing mailings are conducted on Monday, they send malware disguised as reconciliations, acts, etc. Most likely, such activity is aimed at people who have not yet retired from the weekend. We also connect the bulk of new customers from the beginning of the week, which also gives a big boost in the events, especially for categories such as password selection, attack and exploitation of vulnerabilities.
Distribution of information security incidents in the first half of 2018:

The increase in incidents is related to the expansion of our clients' networks. At least 2 organizations increased the number of sensors at controlled sites by April. Plus, in the spring and summer there were a lot of pilot projects.
Also, our signature-based analysts constantly write rules for fresh vulnerabilities, which helps to catch new attacks on client resources.
TOP sources
The sources of attacks in this case are IP addresses that were participants in the network interaction with controlled addresses and attempted to damage the infrastructure.
The map shows the location of the first hundred IP addresses by the number of registered events. Most of these addresses are located in Russia, Ukraine, China, USA, Germany and the Netherlands.

TOP Incident Segments

In the first half of 2018, user workstations were the most frequently affected by unwanted effects. These are 60% of all incidents on controlled resources. In second place are attacks on web-servers and other services.
The main types of attacks on web brutfors and attempts to exploit vulnerabilities, including the Apache web server. On user workstation - malware, attempts to exploit vulnerabilities in browsers. A large number of miners established by illegal means.
Previous articles:
