Zoo on Nefteburovoy: we bring order
There is a company that builds a field or a drilling platform. They have a separate local network for video surveillance, separately for the automated process control system, separately for Internet access, a separate local network (in fact) for telephony.
It’s as if we used physical network delimitation instead of firewalls in such a corporate (production) network. As a result, in many enterprises there are ten homogeneous solutions. Owners overpay money for duplicate functionality.
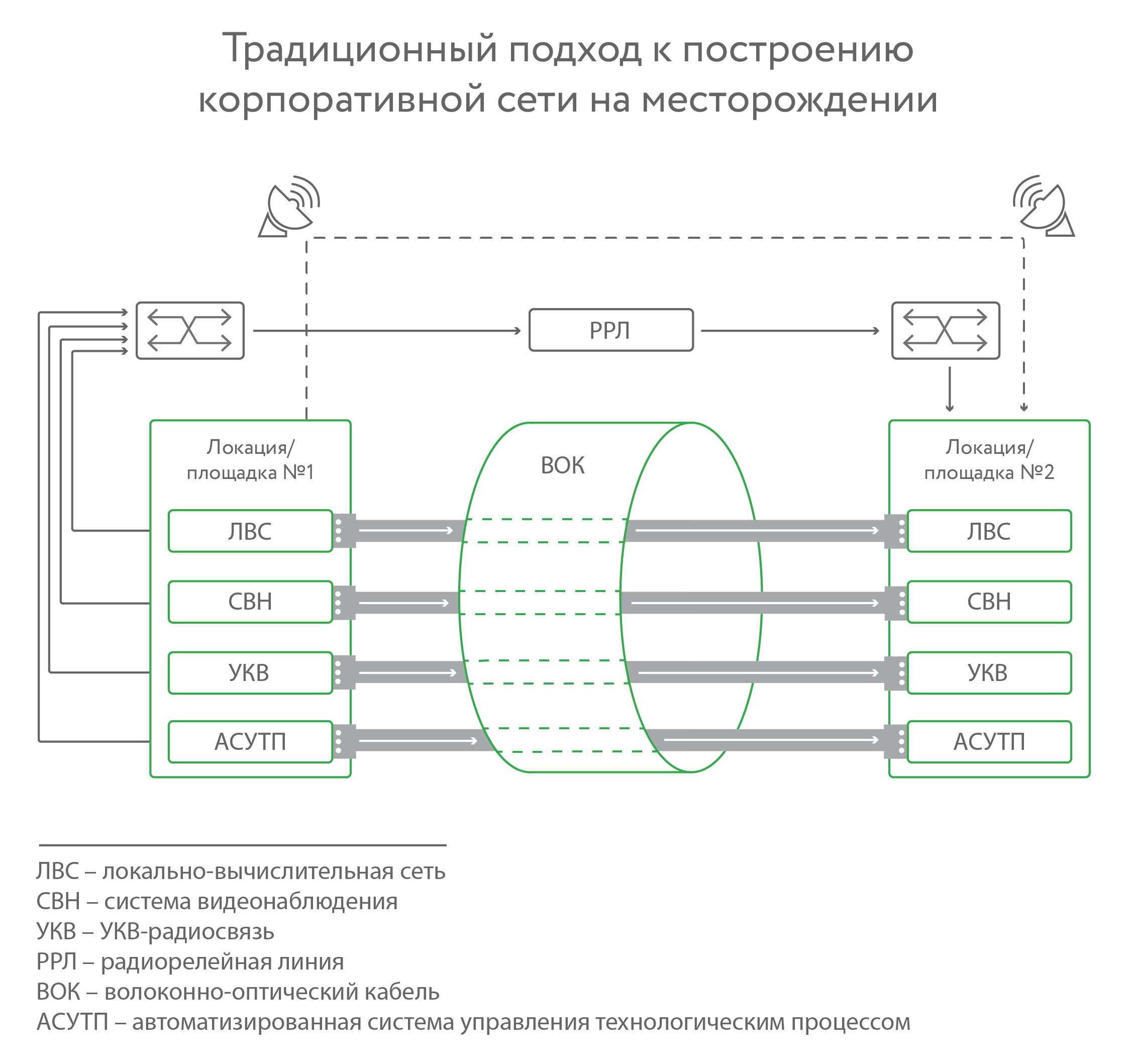
Here so the "uniform" local area network looks. It is much more effective to make one network, where it all comes together. And the second, to have a reserve. We did, and now tell you what it has done.
For a number of mining companies we have done complex projects. There are dozens of vendors and hundreds of different solutions, all intertwined with each other. There are optics, radio relay, there is Wi-Fi, radio access using other technologies, there are industrial Ethernet networks, ordinary telephone exchanges, IoT sensors for process control systems, and much more.
No one has a stable solution for Feng Shui: a terrible zoo from the Legacy makes itself felt. Even in this area often occur mergers and acquisitions, and it turns out that two different zoos are combined. It turns out the zoo in the square.
Our task is to convince the customer that networking is safe. This is the main stop of progress, for example, in the oil sector: here, as nowhere else, the principle “works - do not touch” is used.
First, the ACS TP-part always uses other switches than the rest of the network. This is a serious appreciation, but it is historically correct. It is assumed that the automated process control system will work in any conditions, since at least it is formally untied from the Internet.
At the same time, physical isolation of networks does not guarantee isolation from malicious programs: engineers regularly connect to the internal segment equipment with infected computers from the external one. Protecting the process control system is critical, and you still need to take the same measures as if it was just sticking out.
Video surveillance: it is believed that there is no need to protect it as an ACS segment. Yes, either the network is built separately and on an analog (very expensive), or it is considered that it is conditionally protected. In my practice, you can turn off the camera and access the network. Or replace the picture, and no one in the next six months until the end of winter will not know. Checking the availability of cameras and the presence of images. Many feel so safe: the picture may not change 100 years. Tundra and tundra. We must go around and see what and where.
As a result, we answered all the security questions. Let's get to the details.
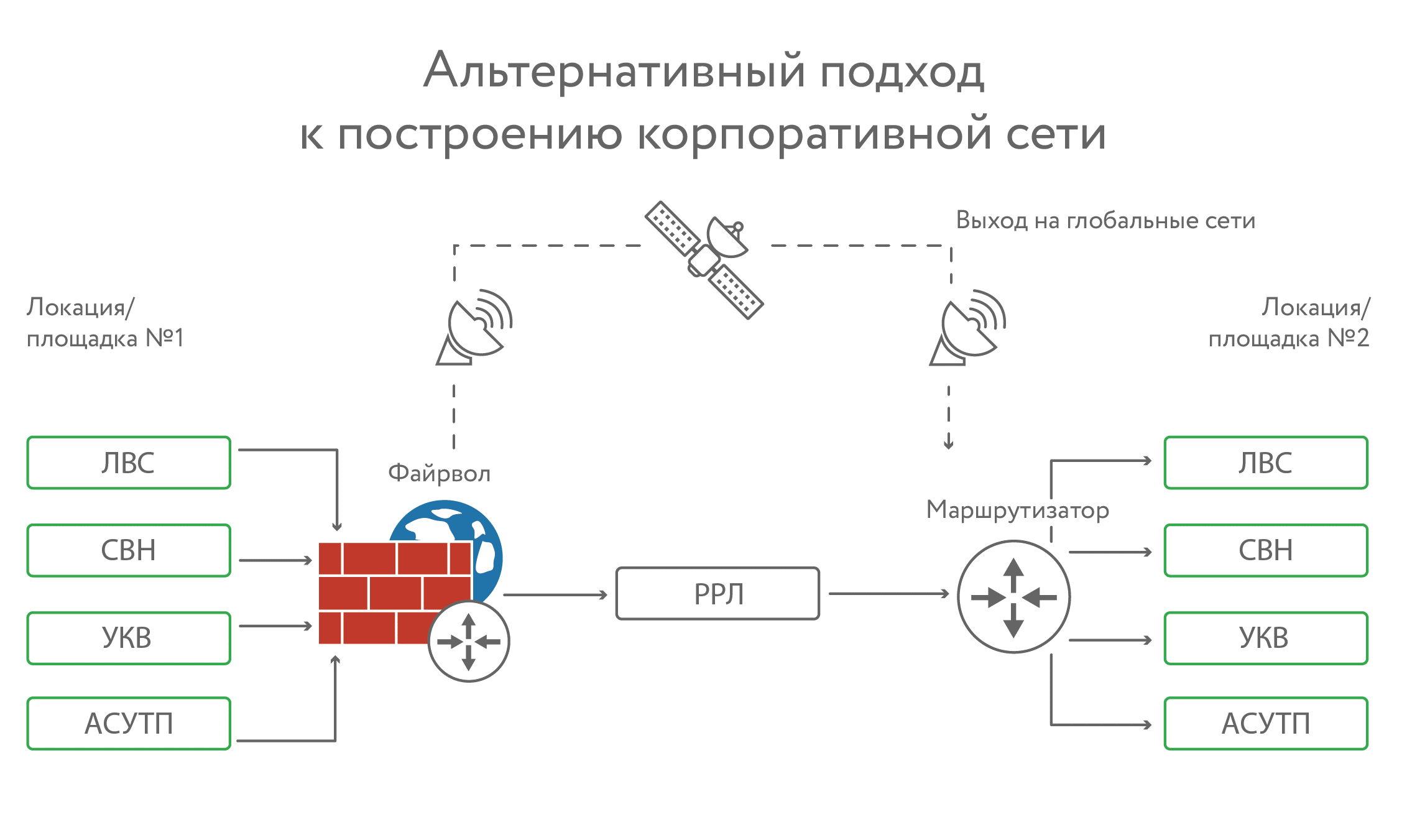
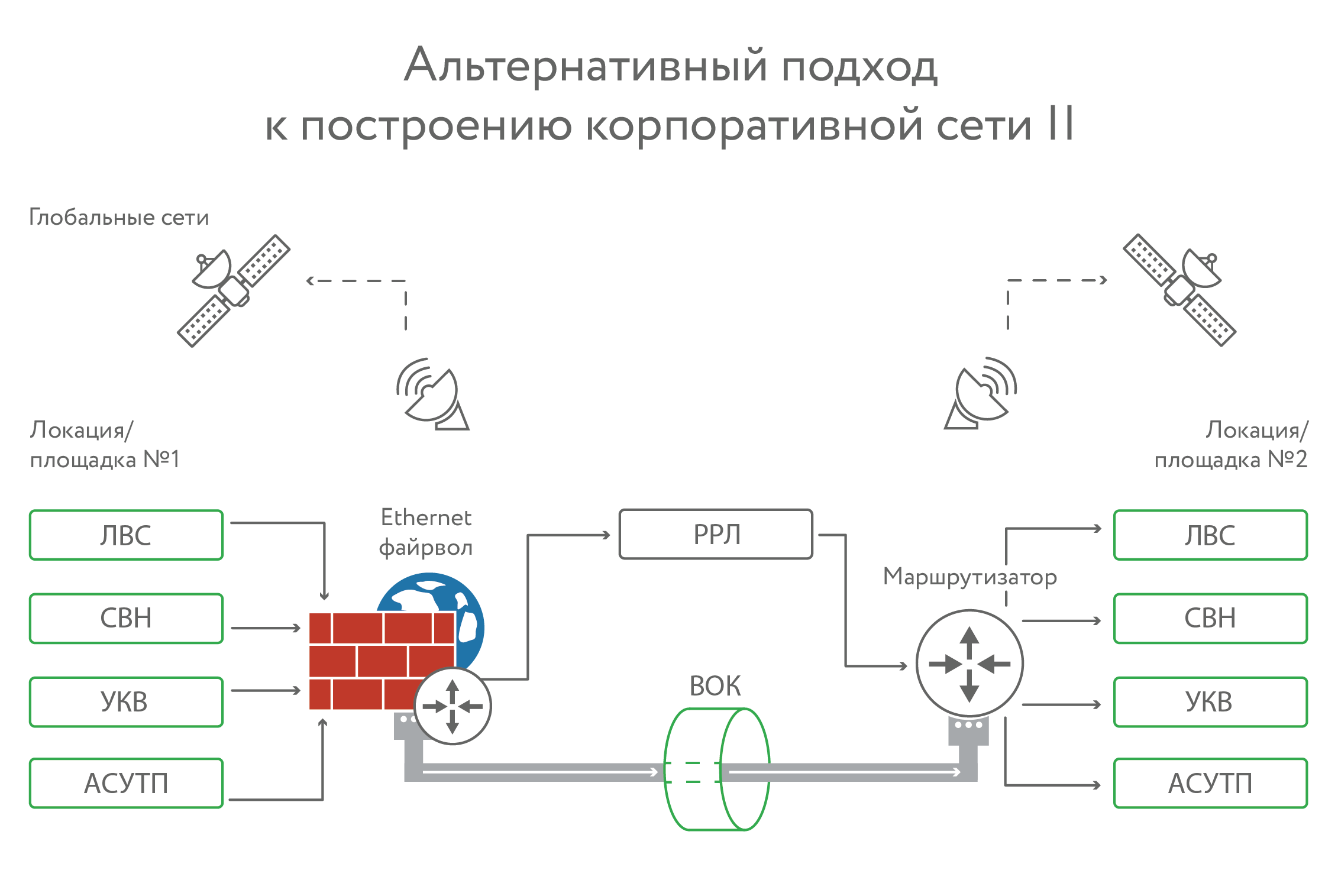
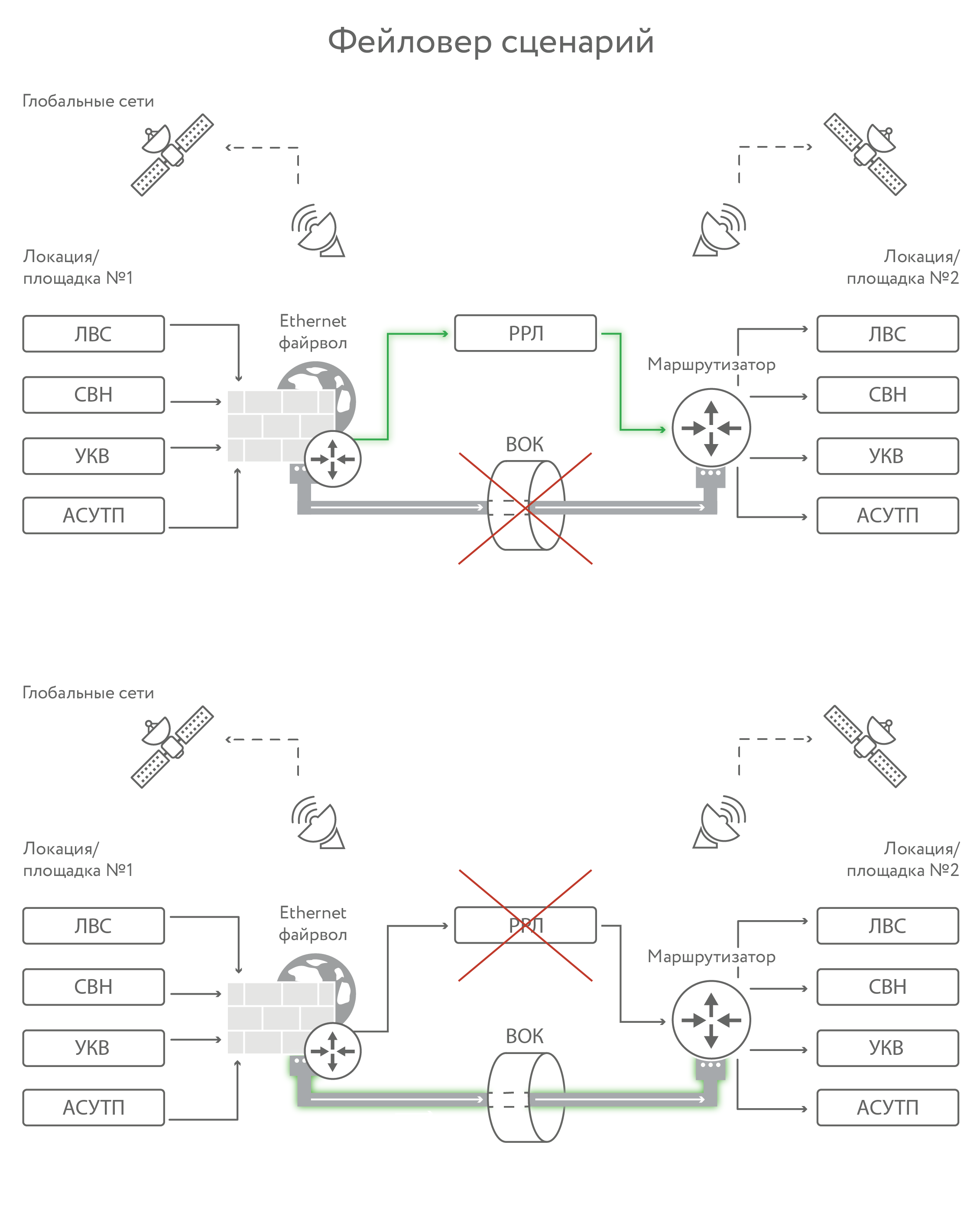
The first option is when radio relay only. It is good, but if heavy precipitations (rain, snow) started or a strong wind began, then failures begin. A strong wind can turn the antenna around, rain and snow shielding and creating interference. If there are any ice rains or something else, then the ice can deactivate the antenna. Radio relay will work well in ideal weather conditions. In bad weather conditions (and in Russia, mining, as a rule, occurs in severe weather conditions) must be duplicated.
From our point of view, the best option is optics + radio relay. But optics can also break, it is torn more often than it might seem. Regardless of whether they bury it or hang it on supports. And during one repair, pipes can break in dozens of places.
In our example there is an oil pipeline - about a hundred kilometers.
We have combined the network into a single complex, as in the diagram above. Fault tolerance is achieved through radio-relay bridges, there is a backup of telephony through a trunking network (integrated through walkie-talkies for calling telephone network subscribers).
The result is:
Now about security. Here, for example, an IP camera, a frequent node of malware infiltration:

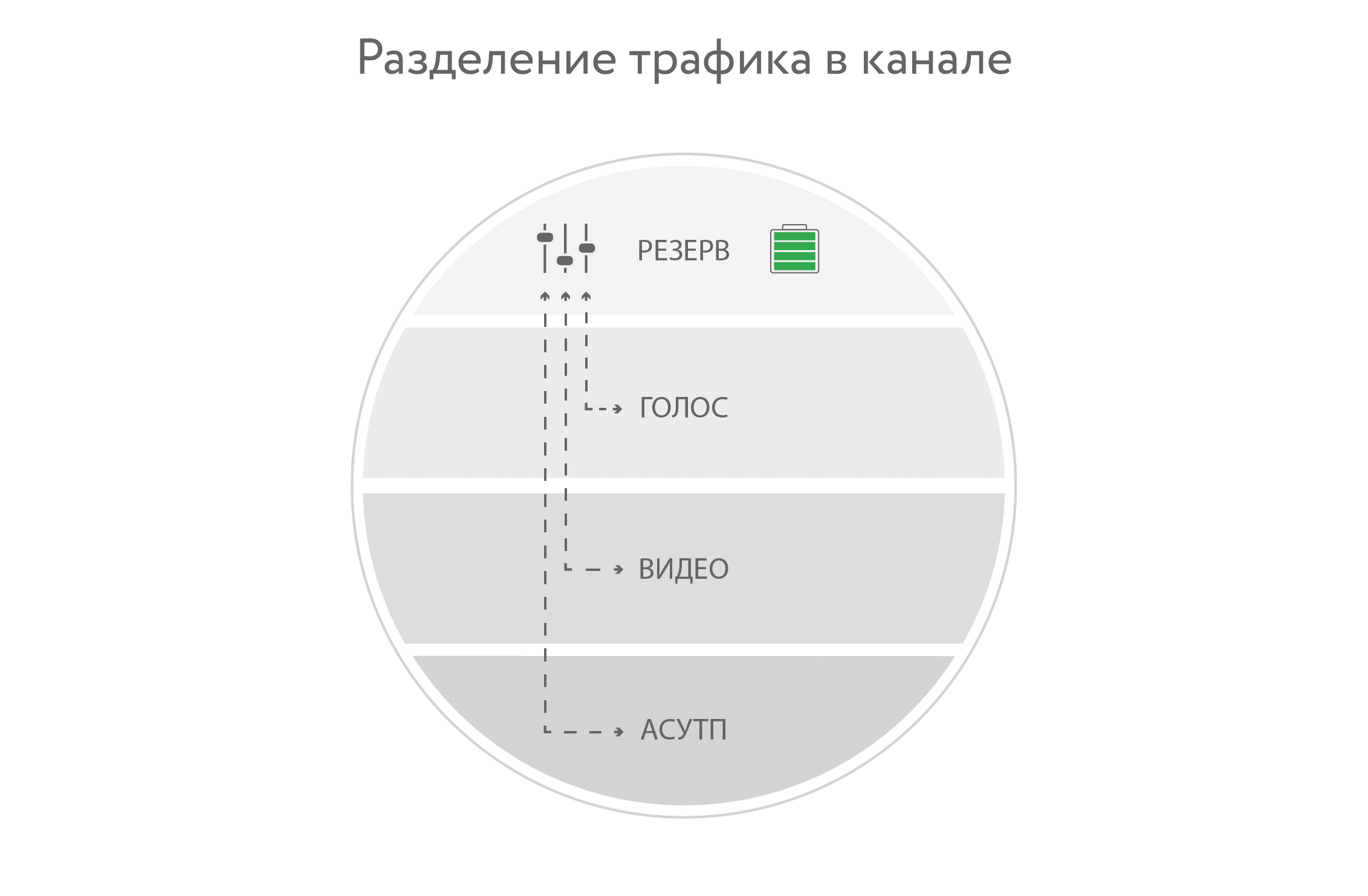
How is traffic delimited? Now I cut VLAN'Y. Conventionally, the automated process control system has the highest priority, then video and telephony, the rest of the traffic goes on.
Why is the VLAN set secure compared to the good old physical delineation?
When you share physically, you have your own piece of hardware for each task. It is absolutely safe. If malefactors got on one piece of iron, they will not get on the next. Need to get to the control segment. There is a common point of hacking - this is a management network. Accordingly, if there is a single point of failure, then what's the difference, on one piece of iron, the vilanas are cut or everything is spinning on different ones. Users are isolated, they do not see users from neighboring wilan. The probabilistic characteristic of some problems in virtual networks is not much higher than the same assessment in physical separated networks. Switches can be made isolated, switch clusters, optical links will be duplicated. Thus, the probability of failure is minimized.
Until recently, security insisted that video surveillance networks, automated process control systems, etc., be on physically dedicated networks, this is a definite point of view. And common sense is definitely there. But it's expensive. You can greatly reduce the price due to a very small reduction in fault tolerance.
The second reason is that if there are three different networks, they are extremely rarely duplicated by all three. We offered the option to combine fault-tolerant switches, fault-tolerant LANs - the key roles were duplicated here, but, accordingly, we divided all the networks virtually.
They made a calculation and showed that in fact such a solution is about a third cheaper. It is possible to minimize the amount of optics being laid, to minimize the recovery time. Because if you broke an optical fiber, for example 8-fiber, you have a conditional recovery time of half an hour, if it is 32-fiber, it is much longer. Also reduces maintenance costs.
There are guaranteed bands. 10G comes, it is divided into pieces under warranty and maximum utilization. All these calculations are individual.
Optics in any case lies on the field - for example, in the same leak detection system using fiber optic cable. When the temperature of the soil changes with the fiber lying there, it becomes clear that oil has flowed out. Therefore, there are simply no problems with switching and a narrow channel inside the local network. Yes, it can be built on copper or old technologies, but this is irrational. Therefore, fiber is a given.
Satellite channels are more likely to duplicate them, for critical telemetry and the same process control system. The sensor worked - immediately a reaction, even if there was war. Here is the filer:

Here is about such a technological cabinet installed at the customer. For understanding.
As a result, we can assemble the entire zoo into one solution due to the virtual delineation of networks. This is twice as good in cable and three times better in iron zoo on nodes in the number of units. IB decreases slightly, fault tolerance increases due to complete duplication of key nodes. Easier, faster and cheaper maintenance.
Expensive switches for automated process control systems are used, through them the traffic of automatic process control systems comes with the highest priority. Then the rest goes.
For objectively a small compromise in security, you can get a significant simplification of support, unification of the solution and savings in power and capital costs.
It’s as if we used physical network delimitation instead of firewalls in such a corporate (production) network. As a result, in many enterprises there are ten homogeneous solutions. Owners overpay money for duplicate functionality.

Here so the "uniform" local area network looks. It is much more effective to make one network, where it all comes together. And the second, to have a reserve. We did, and now tell you what it has done.
How to do better
For a number of mining companies we have done complex projects. There are dozens of vendors and hundreds of different solutions, all intertwined with each other. There are optics, radio relay, there is Wi-Fi, radio access using other technologies, there are industrial Ethernet networks, ordinary telephone exchanges, IoT sensors for process control systems, and much more.
No one has a stable solution for Feng Shui: a terrible zoo from the Legacy makes itself felt. Even in this area often occur mergers and acquisitions, and it turns out that two different zoos are combined. It turns out the zoo in the square.
Our task is to convince the customer that networking is safe. This is the main stop of progress, for example, in the oil sector: here, as nowhere else, the principle “works - do not touch” is used.
First, the ACS TP-part always uses other switches than the rest of the network. This is a serious appreciation, but it is historically correct. It is assumed that the automated process control system will work in any conditions, since at least it is formally untied from the Internet.
At the same time, physical isolation of networks does not guarantee isolation from malicious programs: engineers regularly connect to the internal segment equipment with infected computers from the external one. Protecting the process control system is critical, and you still need to take the same measures as if it was just sticking out.
Video surveillance: it is believed that there is no need to protect it as an ACS segment. Yes, either the network is built separately and on an analog (very expensive), or it is considered that it is conditionally protected. In my practice, you can turn off the camera and access the network. Or replace the picture, and no one in the next six months until the end of winter will not know. Checking the availability of cameras and the presence of images. Many feel so safe: the picture may not change 100 years. Tundra and tundra. We must go around and see what and where.
As a result, we answered all the security questions. Let's get to the details.
Example


The first option is when radio relay only. It is good, but if heavy precipitations (rain, snow) started or a strong wind began, then failures begin. A strong wind can turn the antenna around, rain and snow shielding and creating interference. If there are any ice rains or something else, then the ice can deactivate the antenna. Radio relay will work well in ideal weather conditions. In bad weather conditions (and in Russia, mining, as a rule, occurs in severe weather conditions) must be duplicated.
From our point of view, the best option is optics + radio relay. But optics can also break, it is torn more often than it might seem. Regardless of whether they bury it or hang it on supports. And during one repair, pipes can break in dozens of places.
Result
In our example there is an oil pipeline - about a hundred kilometers.
We have combined the network into a single complex, as in the diagram above. Fault tolerance is achieved through radio-relay bridges, there is a backup of telephony through a trunking network (integrated through walkie-talkies for calling telephone network subscribers).
The result is:
- Twice reduced the cable capacity of the fiber;
- Three times reduced active equipment;
- Each object (node) consumes three times less power.
Now about security. Here, for example, an IP camera, a frequent node of malware infiltration:

How is traffic delimited? Now I cut VLAN'Y. Conventionally, the automated process control system has the highest priority, then video and telephony, the rest of the traffic goes on.
Why is the VLAN set secure compared to the good old physical delineation?
When you share physically, you have your own piece of hardware for each task. It is absolutely safe. If malefactors got on one piece of iron, they will not get on the next. Need to get to the control segment. There is a common point of hacking - this is a management network. Accordingly, if there is a single point of failure, then what's the difference, on one piece of iron, the vilanas are cut or everything is spinning on different ones. Users are isolated, they do not see users from neighboring wilan. The probabilistic characteristic of some problems in virtual networks is not much higher than the same assessment in physical separated networks. Switches can be made isolated, switch clusters, optical links will be duplicated. Thus, the probability of failure is minimized.
Until recently, security insisted that video surveillance networks, automated process control systems, etc., be on physically dedicated networks, this is a definite point of view. And common sense is definitely there. But it's expensive. You can greatly reduce the price due to a very small reduction in fault tolerance.
The second reason is that if there are three different networks, they are extremely rarely duplicated by all three. We offered the option to combine fault-tolerant switches, fault-tolerant LANs - the key roles were duplicated here, but, accordingly, we divided all the networks virtually.
They made a calculation and showed that in fact such a solution is about a third cheaper. It is possible to minimize the amount of optics being laid, to minimize the recovery time. Because if you broke an optical fiber, for example 8-fiber, you have a conditional recovery time of half an hour, if it is 32-fiber, it is much longer. Also reduces maintenance costs.
Channels
There are guaranteed bands. 10G comes, it is divided into pieces under warranty and maximum utilization. All these calculations are individual.

Optics in any case lies on the field - for example, in the same leak detection system using fiber optic cable. When the temperature of the soil changes with the fiber lying there, it becomes clear that oil has flowed out. Therefore, there are simply no problems with switching and a narrow channel inside the local network. Yes, it can be built on copper or old technologies, but this is irrational. Therefore, fiber is a given.
Satellite channels are more likely to duplicate them, for critical telemetry and the same process control system. The sensor worked - immediately a reaction, even if there was war. Here is the filer:

Equipment

Here is about such a technological cabinet installed at the customer. For understanding.
Total
As a result, we can assemble the entire zoo into one solution due to the virtual delineation of networks. This is twice as good in cable and three times better in iron zoo on nodes in the number of units. IB decreases slightly, fault tolerance increases due to complete duplication of key nodes. Easier, faster and cheaper maintenance.
Expensive switches for automated process control systems are used, through them the traffic of automatic process control systems comes with the highest priority. Then the rest goes.
For objectively a small compromise in security, you can get a significant simplification of support, unification of the solution and savings in power and capital costs.
