Five stories about Cabir, the first virus for smartphones
Yesterday marks 10 years since the discovery of the first malware for smartphones. The Cabir worm nowadays looks harmless: it does not steal money from the account, it does not steal passwords, it does not delete user data. Unless the battery is planted for indecent by the standards of 2004, but it is quite acceptable in 2014 for 2-3 hours.
Today we will tell how we found this virus, why we named it exactly what happened next, and how the whole story ended. However, the end of the story came only for individual characters - for example, for the Symbian platform. For everyone else - in the sense, for smartphone manufacturers, users, and, alas, cybercriminals, everything is just beginning.
History is zero. Actually, the whole story of Cabir detection, told by the main antivirus expert of Kaspersky Lab Alexander Gostev, in this video :
The first story. Everything happens at the end of the day.
 I think, to most readers of Habr it is familiar. Servers have a habit of crashes, bugs in software become active, and new viruses are detected at exactly half past seven. As a rule - on Friday. In June 2004, everything happened not on Friday, but - just at the end of the shift for the team of viral analysts. The next shift was transferred to the recently dropped on a “viral” e-mail file with the comment “something strange”.
I think, to most readers of Habr it is familiar. Servers have a habit of crashes, bugs in software become active, and new viruses are detected at exactly half past seven. As a rule - on Friday. In June 2004, everything happened not on Friday, but - just at the end of the shift for the team of viral analysts. The next shift was transferred to the recently dropped on a “viral” e-mail file with the comment “something strange”.
Later it turned out that the mysterious file was sent to many antivirus vendors, but most apparently were satisfied that this is not an executable file for Windows and it does not pose a threat to ordinary PCs. The replacement Roman Kuzmenko quickly found out that this is a program for the ARM architecture and for the Symbian Series 60 platform, which at that time was only two years old.
The analysis of the file continued, while in the “Laboratory” a full-blown search operation unfolded. We were looking for Symbian phones, and since smartphones were still a novelty then, and were expensive (the first Nokia 7650 smartphone cost about 600 euros), no one immediately found such a phone.
While we were looking for phones (legend says that messengers were even sent to the nearest radio market), it became clear that you could not do with one smartphone, two were needed: to confirm in practice the fact of the worm spreading itself via Bluetooth. Here we must pay tribute to Roman: he conducted an analysis of a completely new program on an unfamiliar platform rather quickly, and he predicted the key features of the virus even before launching it on real devices. Six months earlier, in summing up 2003, Alexander Gostev predicted that mobile viruses would appear very soon. Actually, this is exactly what happened.
The second story. Why was Cabir called Cabir?
 In fact, almost all malicious programs are somehow named by their anonymous (often) author. In the case of Cabir, the name could simply be taken from the file name: caribe.sis. But by unspoken agreement, they never do that. Well, firstly, the same virus can spread under different names (in this case, the classification must be observed). Secondly, virus writers should not be encouraged by spreading their own names: some figures are engaged in breeding infections only to get their five minutes of fame with the help of anti-virus vendors.
In fact, almost all malicious programs are somehow named by their anonymous (often) author. In the case of Cabir, the name could simply be taken from the file name: caribe.sis. But by unspoken agreement, they never do that. Well, firstly, the same virus can spread under different names (in this case, the classification must be observed). Secondly, virus writers should not be encouraged by spreading their own names: some figures are engaged in breeding infections only to get their five minutes of fame with the help of anti-virus vendors.
Moreover, in most cases, the final name still has something in common with the creative impulses of virus writers. This happened in the case of Cabir, but the matter was not limited to a simple rearrangement of letters. In the midst of disputes over the name of the first smartphone worm, employee of the company Elena Kabirova entered the virlab. Evgeni Kaspersky, noticing it, immediately suggested that the malware be named after her, to which Elena responded favorably (but first clarified that the event was really important, it does not happen every day).
The third story. Iron room and device collection.
 So, the first worm for smartphones has been successfully found. The world learned that not all files sent to the phone are equally useful, and that viruses can now be sent not only via the Internet and flash drives, but almost like flu, by airborne
So, the first worm for smartphones has been successfully found. The world learned that not all files sent to the phone are equally useful, and that viruses can now be sent not only via the Internet and flash drives, but almost like flu, by airborne droplets . Despite the fact that Cabir was transmitted only via Bluetooth, and could infect another smartphone only within a radius of 10 meters, there are a couple of epidemics on its account. Most often this happened in crowded places, for example, in August 2005, a wave of infections went through a stadium in Helsinki during the World Athletics Championships.
What can I say, even in the Moscow metro it was possible to receive a message with a malicious attachment. The relative "popularity" of Cabir was also facilitated by the publication of source codes by the creators - a group known in narrow circles, code-named 29A. Due to this, in our database there are as many as 18 modifications of the worm created by followers. They practically do not differ from each other, except that Cabir.k, which appeared in April 2005, used MMS messages for distribution (remember these?), Causing already a real loss to the owner of the infected smartphone.
So where does the iron room? Investigation of new Cabir modifications, as well as similar malware, led to local incidents in the Lab. Imagine: a virus analyst launches another version of a worm on a test smartphone, and a floor below, developers of a mobile antivirus suddenly receive an invitation to accept a file. There was a need for an isolated zone for experiments. As a result, a room appeared in Kaspersky Lab where you couldn’t catch the cellular network and WiFi, and where you couldrelax in silence and experience a new virus without risking infecting your colleagues' phones.

Thanks to Cabir, we have a constantly replenished collection of mobile devices. One of the first was the Nokia 3650 smartphone:

The one! The truth is already inanimate. In addition to the dubious privilege of the second-ever Nokia smartphone, this phone is also remembered for its incredibly inconvenient keyboard.
And Nokia N-Gage:
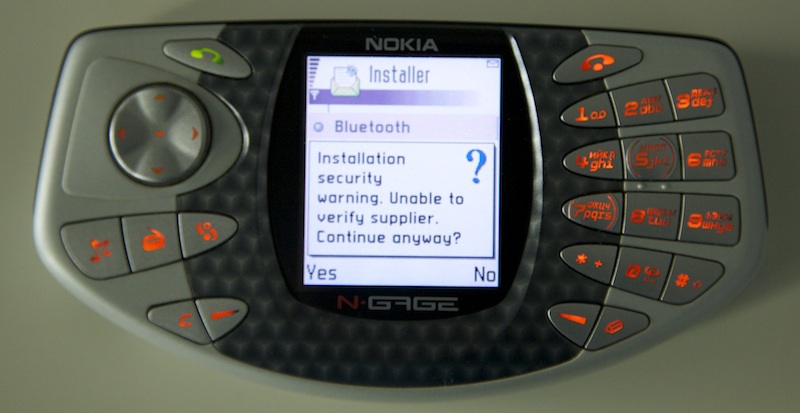
With a more modern version of the software, the phone nevertheless clarifies - you are sure that you want to install it is not clear what? However, many later Trojans for smartphones and ordinary mobile phones survived due to users who answered “yes” to any such question. The advantage of this phone was the opportunity to play mobile games that were good for that time. The downside is the need to put the phone to the ear end during a conversation, likening itself to a kind of Cheburashka-Van-Gogh.
The fourth story. Not a single bluetooth.
The method of distribution via Bluetooth, although it was original, did not live long. First, smartphone viruses appeared, spreading themselves through the address book via MMS, then there was a long epidemic of sending SMS to paid numbers (and this already brought income to the cybercriminal), and then all malicious activity finally went to the Internet - it’s faster, more reliable, and the radius of defeat is nothing is not limited. That very “iron room” was for a relatively short time the favorite meditation spot of our experts: they did not begin to transport it to the new office, there was no point.
True, there was one exception. This is Flame - the hardest cyber espionage tooldiscovered by us in 2012. The module that uses Bluetooth is not the main one, but the features are interesting. Firstly, it collects information about available devices (in approximately the same way you can find out the model of a smart TV and laptop / smartphone in a neighbor’s apartment). Secondly, Flame can turn a Bluetooth module into a kind of beacon, signaling to someone who knows about the presence of an infected computer nearby.
The fifth story. The rise and fall of Symbian malware and the advent of a bright (?!) Future.
Over the entire history of observations, Kaspersky Lab recorded 621 modifications of malware for Symbian. This is if we consider malware that is at least somewhat different from each other in functionality, and not just the name and icon. And this is actually a little. Until about mid-2008, almost all new products of cybercriminals (and various virus scripting enthusiasts) threatened only owners of Symbian smartphones. Then the situation changed. Firstly, Nokia, as the main manufacturer of devices on this platform, has begun to take action. For example, digital signatures for programs appeared (many remember how much headache they brought to users). Secondly, it suddenly turned out that it was much more profitable to write viruses for platform-independent Java ME. Potential victims of Java malware turned out to be much more people - owners of ordinary phones. But smartphones were also susceptible - at least those that supported Java. Double punch!
In August 2010, a record about the first malicious program for Android appears in our database . Actually now this is the main goal of cybercriminals: in total, we have information about more than 370 thousand modifications of malware for this platform. Compare with the miserable hundreds on Symbian.
The latest Symbian phone was released in 2012. The platform, fortunately, or unfortunately, is dead. If Cabir was the first malware for Nokia smartphones, then who will be the last? They appear occasionally now. The last more or less unique malware was discovered on May 6, 2014 - it was a rather ordinary trojan sending SMS to paid numbers and hiding reply messages from the user. Between finding the latter andpenultimate , by the way, it took about 8 months.
However, for mobile devices everything is just beginning. Despite the fact that in the first couple of years since the discovery of Cabir the number of new viruses was relatively small, they rapidly improved. In two years, the same stages of development (from the simplest viruses to the most complex) were completed, which took 20 years on personal computers. For 10 years, mobile malware “learned” to steal money from a user’s account and passwords, crack online banking and hijack SMS messages from one-time passwords, finally (recently) - encrypt user data and extort money. What will happen next - we'll see. But now, 10 years later, it is noticeable how “first-born” was harmless. Created by altruistic virus writers out of a love of art, encroaching only on the battery of a smartphone, but not on the money of the owner. A funny creation from the year before last - when smartphones were different and with real,warm and lamp buttons.
Have you come across Cabir?
Today we will tell how we found this virus, why we named it exactly what happened next, and how the whole story ended. However, the end of the story came only for individual characters - for example, for the Symbian platform. For everyone else - in the sense, for smartphone manufacturers, users, and, alas, cybercriminals, everything is just beginning.
History is zero. Actually, the whole story of Cabir detection, told by the main antivirus expert of Kaspersky Lab Alexander Gostev, in this video :
The first story. Everything happens at the end of the day.
 I think, to most readers of Habr it is familiar. Servers have a habit of crashes, bugs in software become active, and new viruses are detected at exactly half past seven. As a rule - on Friday. In June 2004, everything happened not on Friday, but - just at the end of the shift for the team of viral analysts. The next shift was transferred to the recently dropped on a “viral” e-mail file with the comment “something strange”.
I think, to most readers of Habr it is familiar. Servers have a habit of crashes, bugs in software become active, and new viruses are detected at exactly half past seven. As a rule - on Friday. In June 2004, everything happened not on Friday, but - just at the end of the shift for the team of viral analysts. The next shift was transferred to the recently dropped on a “viral” e-mail file with the comment “something strange”.Later it turned out that the mysterious file was sent to many antivirus vendors, but most apparently were satisfied that this is not an executable file for Windows and it does not pose a threat to ordinary PCs. The replacement Roman Kuzmenko quickly found out that this is a program for the ARM architecture and for the Symbian Series 60 platform, which at that time was only two years old.
The analysis of the file continued, while in the “Laboratory” a full-blown search operation unfolded. We were looking for Symbian phones, and since smartphones were still a novelty then, and were expensive (the first Nokia 7650 smartphone cost about 600 euros), no one immediately found such a phone.
While we were looking for phones (legend says that messengers were even sent to the nearest radio market), it became clear that you could not do with one smartphone, two were needed: to confirm in practice the fact of the worm spreading itself via Bluetooth. Here we must pay tribute to Roman: he conducted an analysis of a completely new program on an unfamiliar platform rather quickly, and he predicted the key features of the virus even before launching it on real devices. Six months earlier, in summing up 2003, Alexander Gostev predicted that mobile viruses would appear very soon. Actually, this is exactly what happened.
The second story. Why was Cabir called Cabir?
 In fact, almost all malicious programs are somehow named by their anonymous (often) author. In the case of Cabir, the name could simply be taken from the file name: caribe.sis. But by unspoken agreement, they never do that. Well, firstly, the same virus can spread under different names (in this case, the classification must be observed). Secondly, virus writers should not be encouraged by spreading their own names: some figures are engaged in breeding infections only to get their five minutes of fame with the help of anti-virus vendors.
In fact, almost all malicious programs are somehow named by their anonymous (often) author. In the case of Cabir, the name could simply be taken from the file name: caribe.sis. But by unspoken agreement, they never do that. Well, firstly, the same virus can spread under different names (in this case, the classification must be observed). Secondly, virus writers should not be encouraged by spreading their own names: some figures are engaged in breeding infections only to get their five minutes of fame with the help of anti-virus vendors.Moreover, in most cases, the final name still has something in common with the creative impulses of virus writers. This happened in the case of Cabir, but the matter was not limited to a simple rearrangement of letters. In the midst of disputes over the name of the first smartphone worm, employee of the company Elena Kabirova entered the virlab. Evgeni Kaspersky, noticing it, immediately suggested that the malware be named after her, to which Elena responded favorably (but first clarified that the event was really important, it does not happen every day).
The third story. Iron room and device collection.
 So, the first worm for smartphones has been successfully found. The world learned that not all files sent to the phone are equally useful, and that viruses can now be sent not only via the Internet and flash drives, but almost like flu, by airborne
So, the first worm for smartphones has been successfully found. The world learned that not all files sent to the phone are equally useful, and that viruses can now be sent not only via the Internet and flash drives, but almost like flu, by airborne What can I say, even in the Moscow metro it was possible to receive a message with a malicious attachment. The relative "popularity" of Cabir was also facilitated by the publication of source codes by the creators - a group known in narrow circles, code-named 29A. Due to this, in our database there are as many as 18 modifications of the worm created by followers. They practically do not differ from each other, except that Cabir.k, which appeared in April 2005, used MMS messages for distribution (remember these?), Causing already a real loss to the owner of the infected smartphone.
So where does the iron room? Investigation of new Cabir modifications, as well as similar malware, led to local incidents in the Lab. Imagine: a virus analyst launches another version of a worm on a test smartphone, and a floor below, developers of a mobile antivirus suddenly receive an invitation to accept a file. There was a need for an isolated zone for experiments. As a result, a room appeared in Kaspersky Lab where you couldn’t catch the cellular network and WiFi, and where you could

Thanks to Cabir, we have a constantly replenished collection of mobile devices. One of the first was the Nokia 3650 smartphone:

The one! The truth is already inanimate. In addition to the dubious privilege of the second-ever Nokia smartphone, this phone is also remembered for its incredibly inconvenient keyboard.
And Nokia N-Gage:

With a more modern version of the software, the phone nevertheless clarifies - you are sure that you want to install it is not clear what? However, many later Trojans for smartphones and ordinary mobile phones survived due to users who answered “yes” to any such question. The advantage of this phone was the opportunity to play mobile games that were good for that time. The downside is the need to put the phone to the ear end during a conversation, likening itself to a kind of Cheburashka-Van-Gogh.
The fourth story. Not a single bluetooth.
The method of distribution via Bluetooth, although it was original, did not live long. First, smartphone viruses appeared, spreading themselves through the address book via MMS, then there was a long epidemic of sending SMS to paid numbers (and this already brought income to the cybercriminal), and then all malicious activity finally went to the Internet - it’s faster, more reliable, and the radius of defeat is nothing is not limited. That very “iron room” was for a relatively short time the favorite meditation spot of our experts: they did not begin to transport it to the new office, there was no point.
True, there was one exception. This is Flame - the hardest cyber espionage tooldiscovered by us in 2012. The module that uses Bluetooth is not the main one, but the features are interesting. Firstly, it collects information about available devices (in approximately the same way you can find out the model of a smart TV and laptop / smartphone in a neighbor’s apartment). Secondly, Flame can turn a Bluetooth module into a kind of beacon, signaling to someone who knows about the presence of an infected computer nearby.
The fifth story. The rise and fall of Symbian malware and the advent of a bright (?!) Future.
Over the entire history of observations, Kaspersky Lab recorded 621 modifications of malware for Symbian. This is if we consider malware that is at least somewhat different from each other in functionality, and not just the name and icon. And this is actually a little. Until about mid-2008, almost all new products of cybercriminals (and various virus scripting enthusiasts) threatened only owners of Symbian smartphones. Then the situation changed. Firstly, Nokia, as the main manufacturer of devices on this platform, has begun to take action. For example, digital signatures for programs appeared (many remember how much headache they brought to users). Secondly, it suddenly turned out that it was much more profitable to write viruses for platform-independent Java ME. Potential victims of Java malware turned out to be much more people - owners of ordinary phones. But smartphones were also susceptible - at least those that supported Java. Double punch!
In August 2010, a record about the first malicious program for Android appears in our database . Actually now this is the main goal of cybercriminals: in total, we have information about more than 370 thousand modifications of malware for this platform. Compare with the miserable hundreds on Symbian.
The latest Symbian phone was released in 2012. The platform, fortunately, or unfortunately, is dead. If Cabir was the first malware for Nokia smartphones, then who will be the last? They appear occasionally now. The last more or less unique malware was discovered on May 6, 2014 - it was a rather ordinary trojan sending SMS to paid numbers and hiding reply messages from the user. Between finding the latter andpenultimate , by the way, it took about 8 months.
However, for mobile devices everything is just beginning. Despite the fact that in the first couple of years since the discovery of Cabir the number of new viruses was relatively small, they rapidly improved. In two years, the same stages of development (from the simplest viruses to the most complex) were completed, which took 20 years on personal computers. For 10 years, mobile malware “learned” to steal money from a user’s account and passwords, crack online banking and hijack SMS messages from one-time passwords, finally (recently) - encrypt user data and extort money. What will happen next - we'll see. But now, 10 years later, it is noticeable how “first-born” was harmless. Created by altruistic virus writers out of a love of art, encroaching only on the battery of a smartphone, but not on the money of the owner. A funny creation from the year before last - when smartphones were different and with real,
Have you come across Cabir?
