Safely Using Go in Web Programming
The article was written for developers who are beginning to learn the Go programming language in order to comply with the safe requirements for writing web applications in their code. The article describes the possible vulnerabilities that web programmers can leave, as well as ways to eliminate either using standard libraries or using third-party solutions that have already proved themselves.
The Go programming language is a fairly young programming language - developed by Google in 2007 and was officially introduced in 2009. Programmers really liked this language: compiled, multi-threaded, structured and imperative. It is used by such companies as Microsoft, GitHub, Cloudflare, Heroku, Vkontakte, Mail.Ru. Immediately after the release of the language, libraries and tools to help develop on Go appeared and continue to be created. Libraries for protecting web applications have also appeared among these tools. Many libraries written both by individual developers are built into the standard set of libraries.
Here are the most typical methods of attacks on sites and the main ways to avoid them or at least minimize these threats:
A review of tools to protect against these types of attacks, I would like to do.
Sessions are a clear target for a hacker, since they can be used to access a web server without the need for authentication. And it turns out that not competent implementation of sessions can jeopardize your entire service. If you decide to use sessions on your web service then the gorilla library will come in handy . Gorilla's session helps to cope with the storage of your cookies on the server, as well as simply transfer unique tokens. In addition, the SecureCookie library may be useful . These secure cookies cannot be faked because their values are verified using the HMAC.
Recently, JSON WebTokens technology has also been used very often . The jwt-go library will help you with this.. Read more about JWT in Go here .
Now consider the fight against cross-site request forgery or CSRF attacks on the site. A CSRF attack is carried out on an authorized user of a web application using a vulnerability in this application. For example, an attacker can force (by sending a letter with a link) a user to go to a specially prepared website that performs some malicious operation (for example, transferring money to an attacker's account or changing a password). To carry out this attack, the victim must be authenticated on the server where the request is sent. To prevent a CSRF attack, generate a special secret key and save it to the user's session, and based on this secret key, generate a token according to a specific rule. The token is made so that, on the one hand, it is different from the key (in particular, there can be many tokens for one key), on the other hand, to make it easy to check by the token whether it is generated based on this key or not. In 2015, researcher Mikhail Firstov came acrossa similar vulnerability on the Yota website. Recently, finding csrf vulnerabilities on many Microsoft services has brought $ 13,000 to one British researcher . This suggests that developers still poorly solve this problem and not always competently. NoSurf
library does a very good job at Go . For an example of the library, we give the program code. As you can see, based on the context of the request, a token is formed, which is subsequently inserted into the fields and headers we need. Source code of the html document: When trying to change the token in the request form, the server gives an error number 400 BadRequest. I also found a similar GojiCSRF library
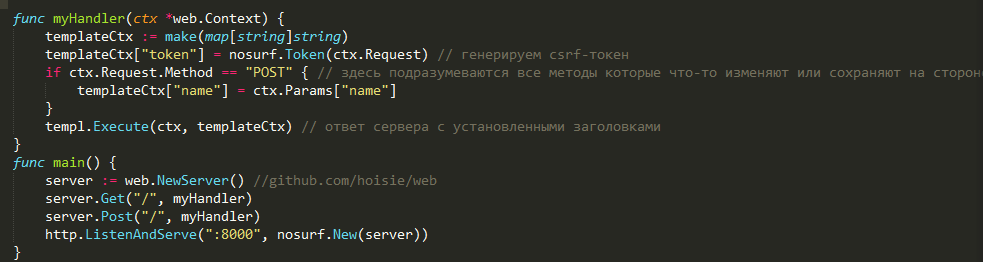
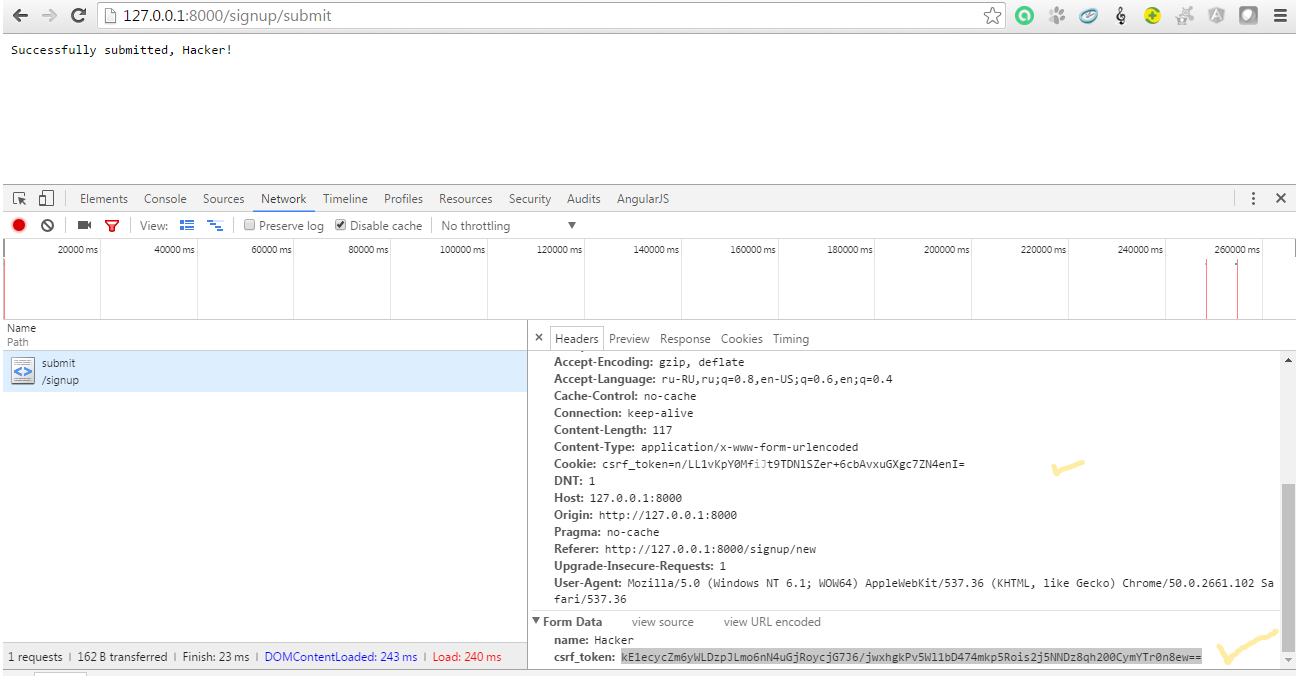
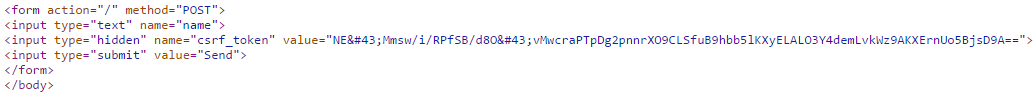
. It works out of the box right away with SecureCookie and generates tokens 32 bytes long. It works only with requests that can modify data and does not work with secure http methods (GET, HEAD, OPTIONS, TRACE).
Almost the same, but only in simplified mode, allows you to generate the standard Go XSRFtoken library . It has only two functions - it is funcGenerate and funcValid, as well as the ability to set the token lifetime.
An XSS attack or cross-site scripting is a type of attack on a web system consisting in introducing malicious code into a page issued by a web system. The most famous example is the hijacking of user cookies by an attacker.
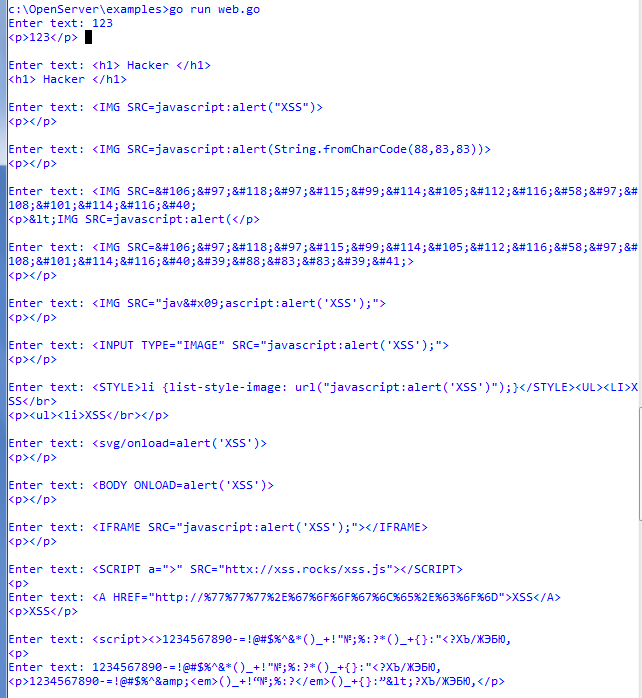
In my opinion, quite good libraries with consonant names were written for this case. This is blackfriday and bluemonday . Libraries are quick to set up and conveniently run. They can work both together and separately. He gave an example of code for a simple program that receives a line from the console, escapes certain characters, and some simply wipes it. I took some examples of JS scriptsthat can be used when implementing an attack. An example of the program is shown in the screenshot below, the filtered sequence is displayed between the tags
Program code:
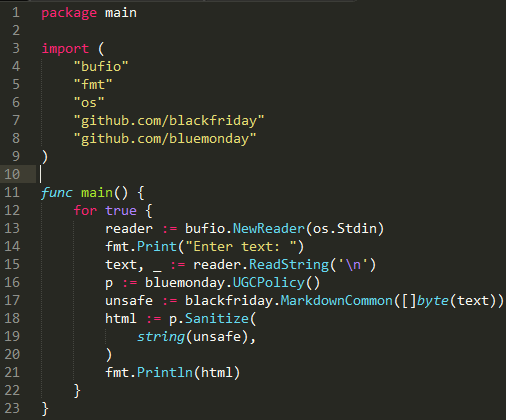
Displaying the result of two libraries working together:
And if you suddenly do not want to use third-party libraries for some reason, then Go out of the box has a couple of useful functions contained in the html / template
package : • funcHTMLEscape (w io.Writer, b [] byte) sends version b to w with the replacement of potentially dangerous characters with their escape sequences.
• funcHTMLEscapeString (s string) string returns the version of s with the replacement of potentially dangerous characters with their escape sequences.
• funcHTMLEscaper (args ... interface {}) string forms a string of many arguments replacing potentially dangerous characters with escape sequences.
Also, your input parameters can be easily "cleared" by Sanitizing. On the github of this library there is a fairly complete test with input from the same OWASP .
There is also an attack known as Clickjacking . The Clickjacking attack allows the hacker to click on the victim site “on behalf of the visitor,” also known as spoofing the user interface. Thus, a hacker can come up with various scenarios and, for example, transfer money from your mobile bank to your account in just a couple of clicks. Oddly enough, such vulnerabilities are still found even in DBO remote banking systems , although it would seem that banking systems should be protected much better than regular web applications.
It is also recommended that you attach an X-Frame-Options header to each response from your server for protection. Now all modern browsers support the X-Frame-Options header. It enables or disables the display of the page if it is open in a frame. The title can have three values:
• SAMEORIGIN - Rendering a document, when opened in a frame, is done only when the top document is from the same domain.
• DENY - Rendering a document inside a frame is prohibited.
• ALLOW-FROM domain - Allows rendering if an external document from this domain (not supported in Safari, Firefox).
An example implementation of adding a response header in Go.
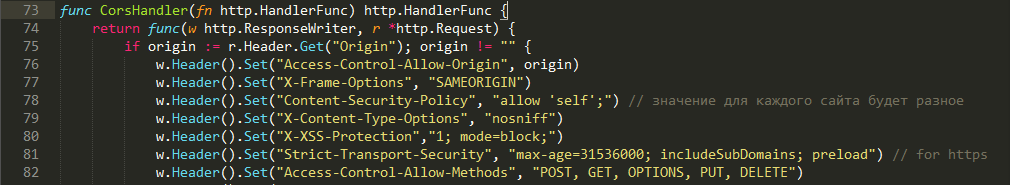
Secure- A small layer for conveniently setting the safe parameters of your service. Secure can work both with a large number of frameworks and with the standard net / http package.
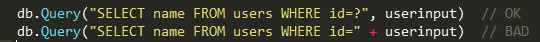
SQl-injection is one of the most common methods of hacking sites and programs that work with databases, based on the introduction of an arbitrary SQL code into the query .
In Go, you can use parameterized queries or what else are prepared statements. which help to avoid some problems with SQL-injection.
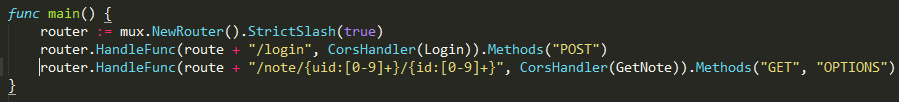
You can also use regular expression filtering. In this case, we use a working link containing only the digits in id and uid. An example of how in Go this can be done beautifully.
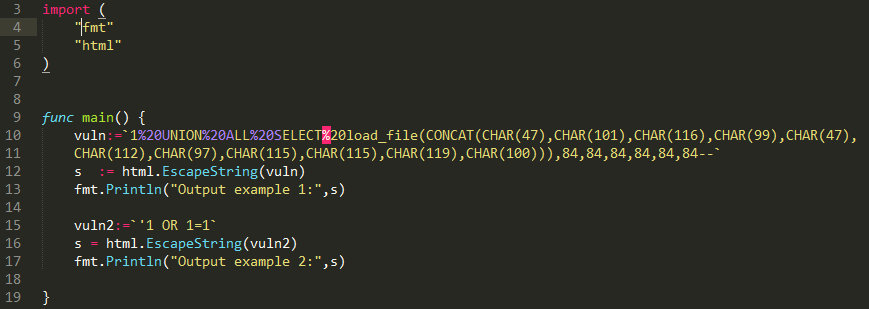
Use escaping certain characters. For example, a single quote.
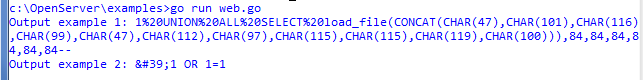
The conclusion of the program. It can be seen that the character “» ”is replaced by a sequence of characters“ »”.
But also do not forget that when implementing sql-injection, we do not have to have a quotation mark. The variable vuln1 just contains this line and, passing through the EscapeString function, does not change at all.
SafeSQL
SafeSQL is a static code analyzer for Go that allows you to find SQL injections.
Despite the fact that Go is a fairly new programming language, the community is growing rapidly and implements basic solutions that are found in almost every project. Including solutions based on web application security. The article examined ways to avoid SQL-injection, CSRF, XSS, Clickjacking. The above methods are not a panacea for the complete security of a web application. But they help to solve most of the fundamental problems related to information security.
https://learn.javascript.ru/csrf
https://nvisium.com/blog/2014/11/26/developing-secure-applications-with/
https://astaxie.gitbooks.io/build-web-application -with-golang / content / en / 09.1.html
https://learn.javascript.ru/clickjacking
http://0xdabbad00.com/2015/04/18/go_code_auditing/
http://dghubble.com/blog/posts / json-web-tokens-and-go /

The Go programming language is a fairly young programming language - developed by Google in 2007 and was officially introduced in 2009. Programmers really liked this language: compiled, multi-threaded, structured and imperative. It is used by such companies as Microsoft, GitHub, Cloudflare, Heroku, Vkontakte, Mail.Ru. Immediately after the release of the language, libraries and tools to help develop on Go appeared and continue to be created. Libraries for protecting web applications have also appeared among these tools. Many libraries written both by individual developers are built into the standard set of libraries.
Here are the most typical methods of attacks on sites and the main ways to avoid them or at least minimize these threats:
- The predicted value of the session identifier (Credential / Session Prediction).
- Cross site request forgery (CSRF).
- Cross-site scripting (XSS).
- Clickjacking.
- Injecting SQL statements (SQL Injection).
A review of tools to protect against these types of attacks, I would like to do.
Protecting session and cookie correctly
Sessions are a clear target for a hacker, since they can be used to access a web server without the need for authentication. And it turns out that not competent implementation of sessions can jeopardize your entire service. If you decide to use sessions on your web service then the gorilla library will come in handy . Gorilla's session helps to cope with the storage of your cookies on the server, as well as simply transfer unique tokens. In addition, the SecureCookie library may be useful . These secure cookies cannot be faked because their values are verified using the HMAC.
Recently, JSON WebTokens technology has also been used very often . The jwt-go library will help you with this.. Read more about JWT in Go here .
CSRF
Now consider the fight against cross-site request forgery or CSRF attacks on the site. A CSRF attack is carried out on an authorized user of a web application using a vulnerability in this application. For example, an attacker can force (by sending a letter with a link) a user to go to a specially prepared website that performs some malicious operation (for example, transferring money to an attacker's account or changing a password). To carry out this attack, the victim must be authenticated on the server where the request is sent. To prevent a CSRF attack, generate a special secret key and save it to the user's session, and based on this secret key, generate a token according to a specific rule. The token is made so that, on the one hand, it is different from the key (in particular, there can be many tokens for one key), on the other hand, to make it easy to check by the token whether it is generated based on this key or not. In 2015, researcher Mikhail Firstov came acrossa similar vulnerability on the Yota website. Recently, finding csrf vulnerabilities on many Microsoft services has brought $ 13,000 to one British researcher . This suggests that developers still poorly solve this problem and not always competently. NoSurf
library does a very good job at Go . For an example of the library, we give the program code. As you can see, based on the context of the request, a token is formed, which is subsequently inserted into the fields and headers we need. Source code of the html document: When trying to change the token in the request form, the server gives an error number 400 BadRequest. I also found a similar GojiCSRF library



. It works out of the box right away with SecureCookie and generates tokens 32 bytes long. It works only with requests that can modify data and does not work with secure http methods (GET, HEAD, OPTIONS, TRACE).
Almost the same, but only in simplified mode, allows you to generate the standard Go XSRFtoken library . It has only two functions - it is funcGenerate and funcValid, as well as the ability to set the token lifetime.
Xss
An XSS attack or cross-site scripting is a type of attack on a web system consisting in introducing malicious code into a page issued by a web system. The most famous example is the hijacking of user cookies by an attacker.
In my opinion, quite good libraries with consonant names were written for this case. This is blackfriday and bluemonday . Libraries are quick to set up and conveniently run. They can work both together and separately. He gave an example of code for a simple program that receives a line from the console, escapes certain characters, and some simply wipes it. I took some examples of JS scriptsthat can be used when implementing an attack. An example of the program is shown in the screenshot below, the filtered sequence is displayed between the tags
Program code:

Displaying the result of two libraries working together:

And if you suddenly do not want to use third-party libraries for some reason, then Go out of the box has a couple of useful functions contained in the html / template
package : • funcHTMLEscape (w io.Writer, b [] byte) sends version b to w with the replacement of potentially dangerous characters with their escape sequences.
• funcHTMLEscapeString (s string) string returns the version of s with the replacement of potentially dangerous characters with their escape sequences.
• funcHTMLEscaper (args ... interface {}) string forms a string of many arguments replacing potentially dangerous characters with escape sequences.
Also, your input parameters can be easily "cleared" by Sanitizing. On the github of this library there is a fairly complete test with input from the same OWASP .
Clickjacking
There is also an attack known as Clickjacking . The Clickjacking attack allows the hacker to click on the victim site “on behalf of the visitor,” also known as spoofing the user interface. Thus, a hacker can come up with various scenarios and, for example, transfer money from your mobile bank to your account in just a couple of clicks. Oddly enough, such vulnerabilities are still found even in DBO remote banking systems , although it would seem that banking systems should be protected much better than regular web applications.
It is also recommended that you attach an X-Frame-Options header to each response from your server for protection. Now all modern browsers support the X-Frame-Options header. It enables or disables the display of the page if it is open in a frame. The title can have three values:
• SAMEORIGIN - Rendering a document, when opened in a frame, is done only when the top document is from the same domain.
• DENY - Rendering a document inside a frame is prohibited.
• ALLOW-FROM domain - Allows rendering if an external document from this domain (not supported in Safari, Firefox).
An example implementation of adding a response header in Go.

Secure- A small layer for conveniently setting the safe parameters of your service. Secure can work both with a large number of frameworks and with the standard net / http package.
SQL injection
SQl-injection is one of the most common methods of hacking sites and programs that work with databases, based on the introduction of an arbitrary SQL code into the query .
In Go, you can use parameterized queries or what else are prepared statements. which help to avoid some problems with SQL-injection.

You can also use regular expression filtering. In this case, we use a working link containing only the digits in id and uid. An example of how in Go this can be done beautifully.

Use escaping certain characters. For example, a single quote.

The conclusion of the program. It can be seen that the character “» ”is replaced by a sequence of characters“ »”.
But also do not forget that when implementing sql-injection, we do not have to have a quotation mark. The variable vuln1 just contains this line and, passing through the EscapeString function, does not change at all.

SafeSQL
SafeSQL is a static code analyzer for Go that allows you to find SQL injections.
Conclusion
Despite the fact that Go is a fairly new programming language, the community is growing rapidly and implements basic solutions that are found in almost every project. Including solutions based on web application security. The article examined ways to avoid SQL-injection, CSRF, XSS, Clickjacking. The above methods are not a panacea for the complete security of a web application. But they help to solve most of the fundamental problems related to information security.
References
https://learn.javascript.ru/csrf
https://nvisium.com/blog/2014/11/26/developing-secure-applications-with/
https://astaxie.gitbooks.io/build-web-application -with-golang / content / en / 09.1.html
https://learn.javascript.ru/clickjacking
http://0xdabbad00.com/2015/04/18/go_code_auditing/
http://dghubble.com/blog/posts / json-web-tokens-and-go /
