7. Check Point for maximum. Sandboxing Conclusion
- Tutorial

Welcome to lesson 7. I would just like to warn you that this is the last lesson. Last for this course. The plans are already two new courses, so stay tuned. And the topic of today's lesson is Sandboxing (i.e. sandbox). And before you begin to tell what it is and how useful it is, I would like to summarize a little of the work we have already done. Let's go over the material covered again.
Access Control
At the very beginning, we advanced the thesis that one of the key elements of network security is the human factor . As always, everything depends on the frames. Competent tuning solves most security problems.
After that, we began to discuss the various blades that are designed to enhance protection. The main goal is to minimize the possible area of attack . In this process, each blade is important and complements the others. Unfortunately, I did not consider the features of setting up all the blades, and it is probably impossible to push everything into the framework of one course.
In fact, all Check Point blades can be divided into two categories: Access Control and Threat Prevention. Let's start with the first category. What kind of blades and features are included in Access Control and how can they reduce the attack surface?

- Firewall - I think everyone understands that the firewall should "hack" all the excess. Here it is necessary to use the approach "Forbidden everything that is not allowed." For example, for users, in most cases it is enough to allow only port 80 and 443, and nothing more!
- SSL inspection - I think I could convince you that this is a very important thing and that without it, we have a huge hole in our security system. A port can go through 443 a lot of interesting things, if you do not investigate this traffic as it should.
- URL Filtering - the name speaks for itself. With this feature, we must close all potentially dangerous Internet resources. Of course, it all depends on the company's security policy, but agree that there are some categories of sites that should definitely be closed. Many resources are widely known as malware distributors. Having closed access to them, we greatly reduce the area of attack.
- Identity Awareness - allows you to control access based on user accounts (not IP addresses). This makes our security policy more flexible and mobile. It becomes more personalized.
- Application Control - with the help of this blade we can block a huge number of potentially dangerous programs. TeamViewer, RDP, Tor, various VPN applications and more. Very often, the user himself does not realize how dangerous the application he installs.
- Content Awareness is another very useful feature with which you can prevent downloading (or upload) a certain category of files. As I said, your users should not download executable files and hope that the antivirus will save you. Moreover, sometimes the user may not even suspect that the background has started the jump of something. Content Awareness in this case will help.
- Geo Protection is another feature that I unfortunately did not discuss. This feature allows you to block any traffic for your network (both incoming and outgoing) of any country. For some reason I am sure that your users do not need to visit the resources of Bangladesh or the Congo. But the attackers love to use the servers of countries where the legislation in terms of cybercrime is rather poorly developed.
Threat prevention
We continue to reduce the area of attack. Let's look at the Threat Prevention category blades. These are already purely "securing" functions:

- You and I have already considered the importance of properly configuring Antivirus . I think the lab has convinced you.
- In two past lessons we covered IPS . As it turned out, this blade can not only scan network traffic, but it can also “catch” virus files.
- Anti-Bot . We unfortunately did not consider it. But the point is pretty simple. If in some way one of your computers has become infected and is trying to reach the command center (i.e., the classic botnet), Anti-Bot will be able to “see” this process, break the session and notify the administrator.
What unites these three blades? They only work with known threats . This is either a signature or a list of bad ip-addresses or URLs from the Checkpoint Global Threat Cloud database. How effective is it today?
According to the latest reports, such traditional, signature-based protection tools are able to cut off about 70% of the existing threats. And that, this indicator can be achieved only with proper configuration. I think it is obvious to all that this is catastrophically insufficient. What should I do if a previously unknown malware and signature protection were “screwed up”? Do you think this is fiction and marketing fiction? In the video below, I consider in detail an example of antivirus bypass with checking for VirusTotal. The first part is theoretical and duplicates the text above, so boldlyscroll to the 6th minute .
Sandbox
In the same video, we demonstrate the capabilities of the Check Point sandbox. The concept of a sandbox (Sandbox) appeared relatively recently. And many still are skeptical of this class of protection (Recall the story about IPS). What is the task of the sandbox?
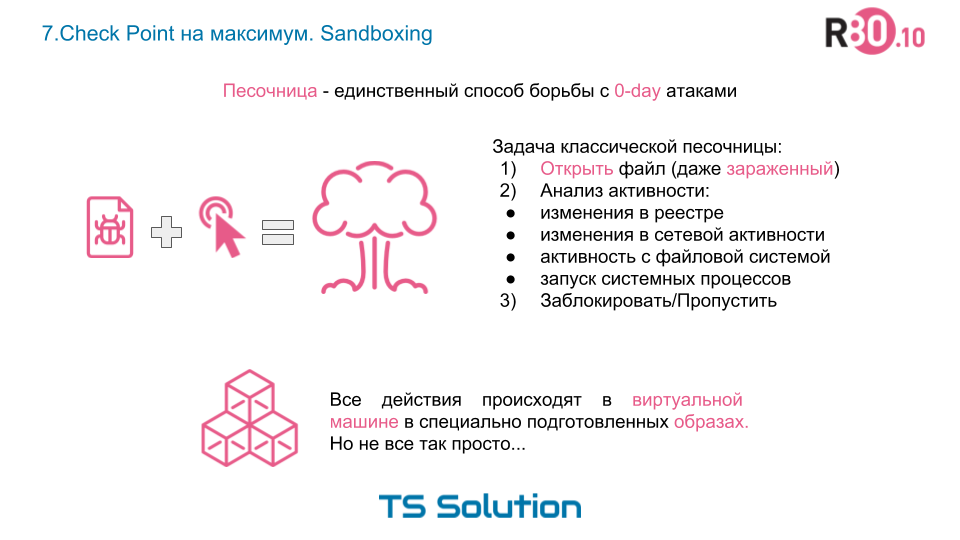
As you understand, this method of verification is fundamentally different from signature analysis. Of course, everything is not as simple as described in this slide. Modern sandboxes (especially Checkpoint sandboxes) use a variety of virus detection technologies. We will not focus on their description. The goal of this lesson is to show that the traditional signature-based approach has flaws and modern protection needs an additional level of protection.. Those. Sandbox can be considered as the last line of your protection when the virus has already passed the firewall, IPS and Anti-Virus.
What is so special about the Check Point sandbox? In fact, a lot of features. This technology is called Check Point SandBlast and includes several blades at once:

This is a very extensive topic, so with your permission, I will tell about it in more detail as part of the new course , which we will launch as soon as possible. As for this lesson, the main thesis:
The sandbox is a mandatory element of integrated network security.
With this you need to accept and accept the fact. Same thing happened with IPS.
Conclusion
On this, we probably finish our course. Many thanks to all who watched to the end, I sincerely tried to share something useful. I hope this information is useful to someone. Unfortunately, to tell absolutely everything in this mini course is simply impossible. Therefore, if you suddenly have questions, we will be happy to answer them. You can write to our shared box, or directly to me.

Also, taking this opportunity, I would like to express my gratitude to Alexei Beloglazov (Check Point company), who constantly helped me with consultations during the entire course. Alexey, thanks again :)
In addition, I would like to tell you that we are providing the Check Point security settings audit service for free.. As part of this audit, we will check all that was discussed in this course and additional things that are not included in the lessons. So do not hesitate to contact me or our engineers with pleasure “digging” in your settings and issue recommendations. You can contact through the website or via the same mailboxes.
Thank you for your attention and I am waiting for you in the new course!
Only registered users can participate in the survey. Sign in , please.
