What threatens Heartbleed to a simple user?
 Many have already heard about the vulnerability found in OpenSSL. It is safe to say that in terms of coverage in the Internet media it will take an honorable first place. They not only write about her, but also create special sites that check services and even draw comics . And not surprisingly - the scale of the defeat is really impressive, according to some estimatesmore than 17% of all ssl-enabled sites are vulnerable, given the ease of operation, this event can be compared to an epidemic. Unfortunately, even this is not a sufficient argument for many - a week later many sites remain at risk. This may not be critical for simple services, but not for financial ones. This can be especially painful for the payment gateways through which payments are made. I’ll talk about one of these.
Many have already heard about the vulnerability found in OpenSSL. It is safe to say that in terms of coverage in the Internet media it will take an honorable first place. They not only write about her, but also create special sites that check services and even draw comics . And not surprisingly - the scale of the defeat is really impressive, according to some estimatesmore than 17% of all ssl-enabled sites are vulnerable, given the ease of operation, this event can be compared to an epidemic. Unfortunately, even this is not a sufficient argument for many - a week later many sites remain at risk. This may not be critical for simple services, but not for financial ones. This can be especially painful for the payment gateways through which payments are made. I’ll talk about one of these. The other day I made an online purchase in a Russian Internet company. When I reached the time of payment, I was transferred to the payment gateway of a large bank with a form for entering data from a bank card. This was the only payment method and I started filling out the form.
Nothing foreshadowed trouble except the sixth sense. Before clicking the "Pay" button, I decided to check the payment gateway for vulnerability. All public services for verification gave a positive answer. Realizing that you should not continue the purchase, I decided to find out what could really threaten users who do not even suspect that they are making a payment through a vulnerable gateway and how easy is it to verify this?
It was not easy to verify this, but very simple. After modifying the code of one of the ready-made exploits on github, I ended up with a dump file of 64 kilobyte pieces. What was in it?
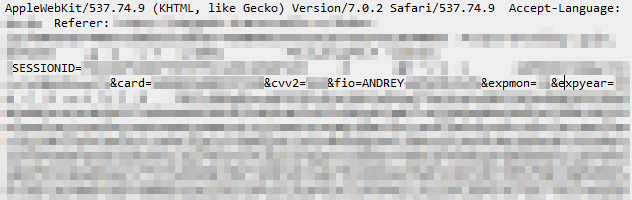
It was everything. Literally everything that passes through the payment gateway: order number, card number, CVV2, full name, year and month until which it is valid. For half an hour of the script in the dump, there were several hundred real bank cards and information about their owners.
Of course, all the necessary information was immediately sent to the contacts of the payment gateway and its largest customers, but at the moment the vulnerability has not been eliminated. I remind you that almost a week has passed since the moment when it became publicly known about Heartbleed. One can only be surprised at the carelessness of the security services of some large companies and imagine with horror how many cards and other critical personal information could leak into the hands of real attackers during this time.
Updated (04/15/2014):the vulnerability was fixed a week later, after the publication of information about Heartbleed, and three days after the date of my request.
Updated (04.16.2014): this vulnerability was discovered in the payment gateway of VTB24 Bank, which was used, in particular, on the Russian Railways website. I have nothing to do with sos-rzd.com and its authors. I recommend to everyone who made purchases through it from April 7 to April 14 to reissue cards.
