DEFCON 17. Hacking 400,000 passwords, or how to explain to a roommate why the electricity bill has increased. Part 2
- Transfer
DEFCON 17. Hacking 400,000 passwords, or how to explain to a roommate why the electricity bill has increased. Part 1
If you do not follow any rules for creating passwords, the password may look like a simple PHP list . People hate rules, hate phrases and do not want to use them. If you give them will, they will type in any minor password and they will assume that the work is done. In this case, it is safer if they do not use simple basic words, therefore it is better to use large input dictionaries.
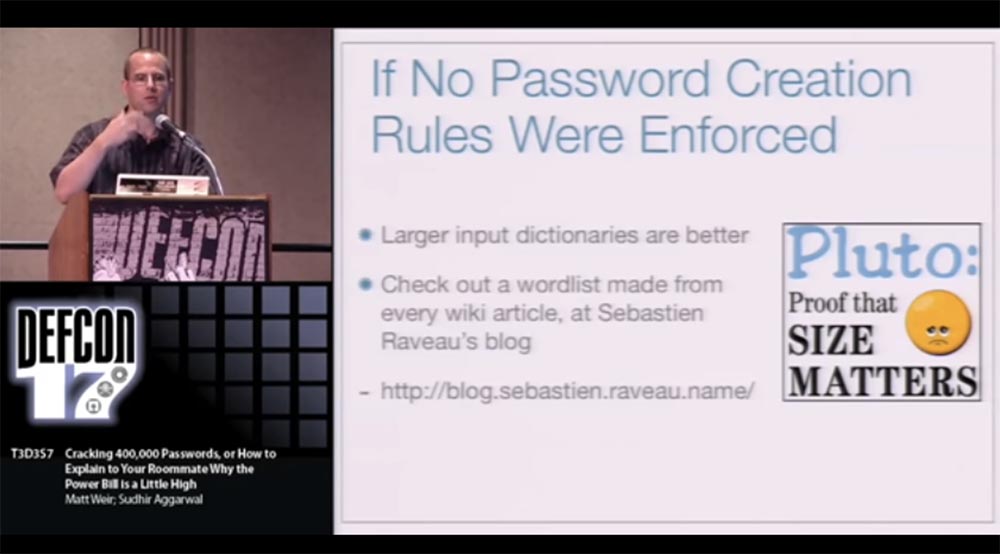
The greatest contribution to the creation of input dictionaries made Sebastian Ravo - he created huge lists of words from each article contained in Wikipedia, as well as from similar projects. If you know a word, then you create a Wikipedia article for it. But what's good for Wikipedia is not always good for creating secure passwords, so if the dictionary is really huge, you cannot apply many different rules to it. You can find a list of Wikipedia words on his blog at http://blog.sebastien.raveau.name/ .
If there is a policy for creating passwords, then you should follow these rules:
it is better to use small thematic, specialized word lists in dictionaries, the
best dictionaries are based on previously cracked passwords.
For privacy reasons, I cannot provide you with a list of cracked passwords, but believe me, just as the rich one gets richer, the hacked password becomes stronger if you see where a mistake was made when you created it and fix it.
There are lists of such passwords, and we can see that the same users are repeated in these lists, because they used the same password everywhere.
It will be useful if you can extract the basis of such passwords. For example, the password "TigerWoods1982" should not be too common, but people constantly use the password "TigerWoods" . Therefore, you can extract this basic phrase "TigerWoods"to create a strong password based on it. There are some tools on my CD that will help you make it much easier.
The rules for creating words for passwords are very simple:
However, you will need to develop your own rules if you want to crack really strong passwords. There is another tool on my CD that allows you to parse passwords into 2 different sets.
The first is the passwords about which we know how they were created, for example, password123 , and the second is passwords, the principle of creation of which is unknown to us. This is very good, because you do not need to go through 200 thousand passwords like password123 and then try to come up with new rules to use them. You will get a small list from which you will see, for example, that people use emoji to create passwords by inserting emoticons into words. You will learn new keyboard shortcuts, and it will help you create strong passwords much easier.
As I said before, I decided to move away from the built-in JtR rules and developed my own way of generating "clues". Good results are brought by the method of "probabilistic password cracking", probabilistic cracking . I have already said that our reactions are universal: we run through something with our eyes, we nod, we say that it looks great, but to ourselves we think: “what an academic bullshit”! But I want to say that we really wanted to learn how to create the most resistant to cracking passwords, so we tried to do everything in the best possible way.
It is known that people like some words more than others, for example, password , monkey , football. It is also known that people prefer certain rules of “mangling” passwords by adding 123, 007, $$$ or uppercase first letters of words. To increase resilience, we need to optimize password rules in an atypical way. This is a time consuming process. From the John the Ripper email list, I learned about a person who created 10 or 12,000 JtR rule configuration files , trying to get the most out of it.
I am much lazier than him, so I didn’t do it. I just tried to simplify the process of creating passwords and automate the process. We process all the information and determine the probability of using certain words and combinations, that is, we rank the passwords according to the probability of guessing. And then we use the least likely combination of words and “tinkering” to create a password. So, this is what we should try to make our passwords stronger:
With this way we have achieved success. If you can’t split passwords into two sets according to the features mentioned above, we have a trainer program that automatically analyzes the list of known passwords and generates what we call "grammar." This “grammar” contains all the necessary information, so we use two such “grammars” to explore the possibilities of password cracking.
Due to this, we determine the probability of using everything we have: words in dictionaries, rules for “mangling” words in passwords, algorithms for placing characters like “two digits at the end of password 12”, in contrast to which you can use the rule “two digits at the end of password 21 ", and the like.
I can continue to talk about it, but I'd better show you a vivid example of how this works. I don’t expect you to read everything on the slide, so I’ll tell you what I’m going to do. I'm going to launch our probabilistic password cracker and feed him two different input dictionaries. In fact, it supports up to 10 dictionaries, but it's better not to go crazy.
One input dictionary contains the most common passwords, so it has a high probability of guessing. The second dictionary contains the least common words, and the password cracker will switch between these two dictionaries. After that, I “salt” the result right in John the Ripper , because, as I said, I want to create my own password hashing algorithm.
Unfortunately, we cannot use the PHP list here , again because of confidentiality, because it is impossible to demonstrate password cracking in front of everyone, our institute does not recognize this as legitimate. Therefore, I will demonstrate the work of a cracker using the MySpace list as an example , which was disclosed 2 years ago. All passwords in it were presented in plain text, so that you can read them, and this operation does not present any additional danger.
We used MD5 hashing , this is exactly the same hash algorithm that is used for the phpbb list , so here the attack on phpbb is largely simulated. About 17,000 password hashes were loaded without “highlights”, and we actually divided their lists into several different parts for typical machine learning.
Right now on the screen you see how fast the password is cracked, so you should probably use a slower hashing algorithm. It also switches between different rules, so it’s not just “try 1 digit, try 2 digits” attempts and so on.
You see that passwords are of a different size, usually people use a length of 6 to 8 characters and sometimes there are exclamation marks at the end of the password.
There are several other types of optimization that we are trying to build into this algorithm, because our work is still ongoing. One of these things is the inclusion of targeted attacks in the process, when instead of cracking some big old password, the program tries to crack the password of a specific user.

All you need for a targeted attack is to use a different input dictionary, for example, children's names, birthdays, zip codes, and so on.
You see that the hacking process on the screen has slowed down a bit, these are design features, if hacking is simple enough, the process is accelerated. But since it is based on a probabilistic model, passwords are more likely to be guessed with the highest probability, and passwords are less likely to be cracked a little slower, as this is where a larger number of “clues” are used.
You also noticed that in this list there are mostly rather weak passwords. This is explained by the fact that we are just starting a password cracking session and do not want to use too complex or extended passwords.
If you have a hacking strategy in which you intend to attack only strong passwords, you need to create an appropriate list based on these passwords and start the session by hacking only strong passwords.
So, our program has finished its work. The hacking process took 2 minutes and 30 seconds, during which time 5,586 passwords were cracked, or guessed correctly, which is just over 30% of the total amount available.
There are a hundred reasons why I think that the password policy needs to be changed, not because the use of passwords is something backward and stupid. It's just that I actually believe that they are doing our security more harm than good. Especially if we are talking about offline attacks that cannot be resisted if you do not change your password every 2 minutes.
And now I want to talk about the technique of Brute Force attacks . These attacks can actually do a lot of damage if you don't take care of the defense.
They are quite powerful, but you can resist them, you just need to use your brains. To do this, you need to analyze the frequency of using letters and symbols to find out which letters or symbols are used relatively rarely in passwords.

Surely you have all heard about this, so try, for example, to use the letter Q more often, which is quite rare in passwords. Your hacking algorithm should not seek to crack all passwords; you need to focus on the most likely ones.
A more “advanced” version is the Markov model . It is based on the conditional probability of letters, for example, if you have two letters Q in a row, you are more protected than when you have U in your letter set, because U usually follows the letter Q in words. It also assumes that the password is created in “Human” manner, that is, if a certain letter is located in this place of the word, then it is followed by another letter, which is most often used in precisely this letter combination. The Markov model is used by the JtR hacking algorithm .which takes into account that the letter Q in “human words” is usually followed by U or W, but not S or Z. Do not think that I’m trying hard to get “John the Ripper” here, but this is a really good program.
We can further deepen the logic of Brute Force by applying targeted attacks. They are based on the use of such password creation principles:
The same principles can be used for “dictionary attacks”. There is a very good tool for testing the effectiveness of attacks called “Crunch” , it can be found on the programmers' forum remote-exploit.com .
I want to give you an example of hacking a “strong” password using the Brute Force attack . To do this, I first run JtR and it starts generating “guesses” based on lowercase letters using the Markov model.
You can see that there are a lot of real words in this list, such as dog, starless, marine, which are in the input dictionary. But thanks to the Markov model, he also generates words that are absent there, for example, stech. But since we solve a strong password, it is necessary to apply some additional logic. Therefore, I use scripts that provide a capital letter at the beginning of a word, and also add special characters and numbers at the end of a word.

As you can see, these "otgadki" look like a real strong password. Now that you know about the password policy, you should click on the “turn off laziness” button and spend 5 minutes to give these words a certain size, since they look too short.
We can also try to upload everything back to JtR.and try to crack the hashes.
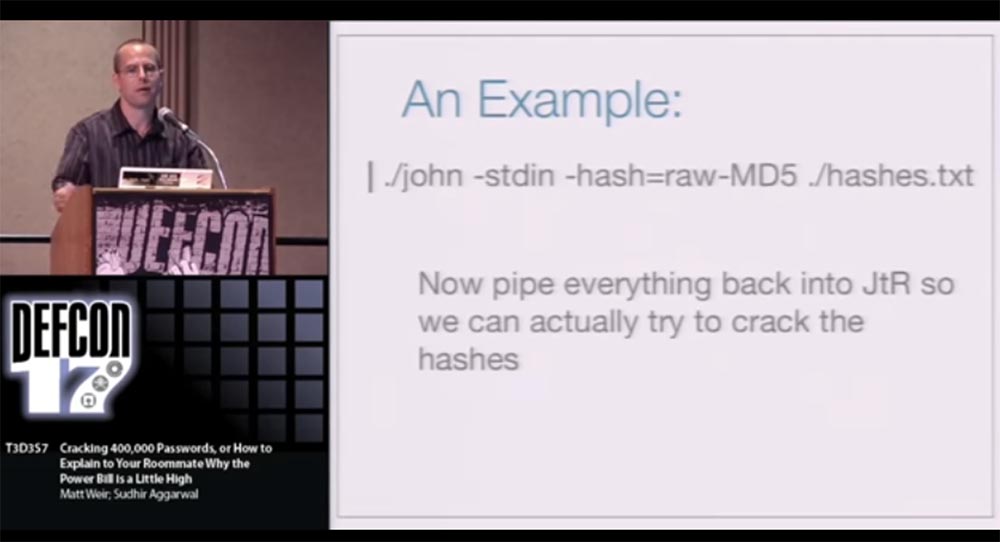
At the beginning of the presentation, I talked in detail about hacking the phpbb.com users' password list , and now I want to talk a little about hacking the Web Hosting Talk list .
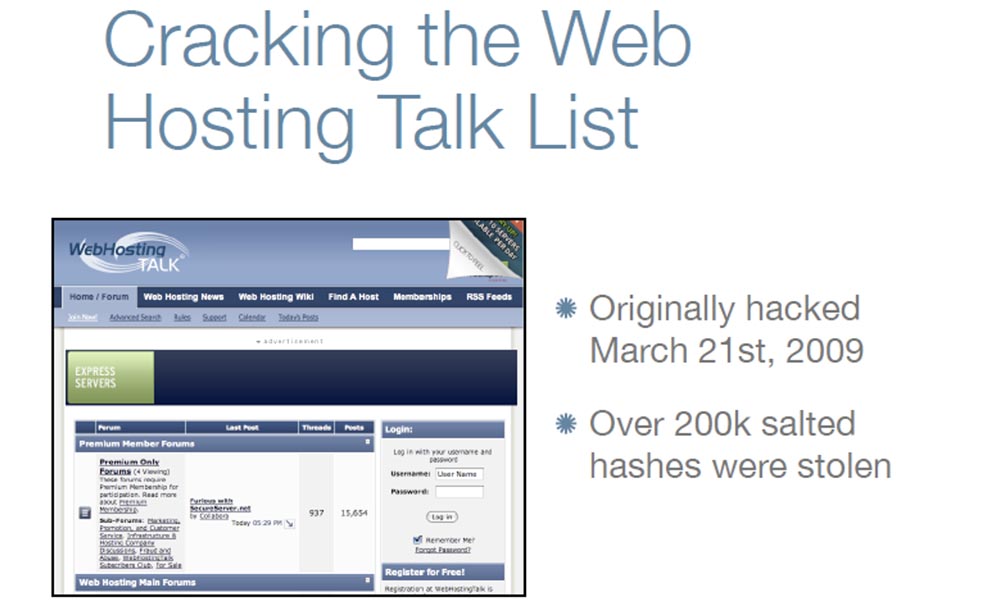
He was hacked on March 21, 2009, at least at that time the list was published on the network, and the attacker turned out to be a real scoundrel because he posted about 200 thousand logins and passwords and other confidential information of users in open access. He stole the hashes, and then deleted the site itself and all backups. This was a huge hit for the system administrator.
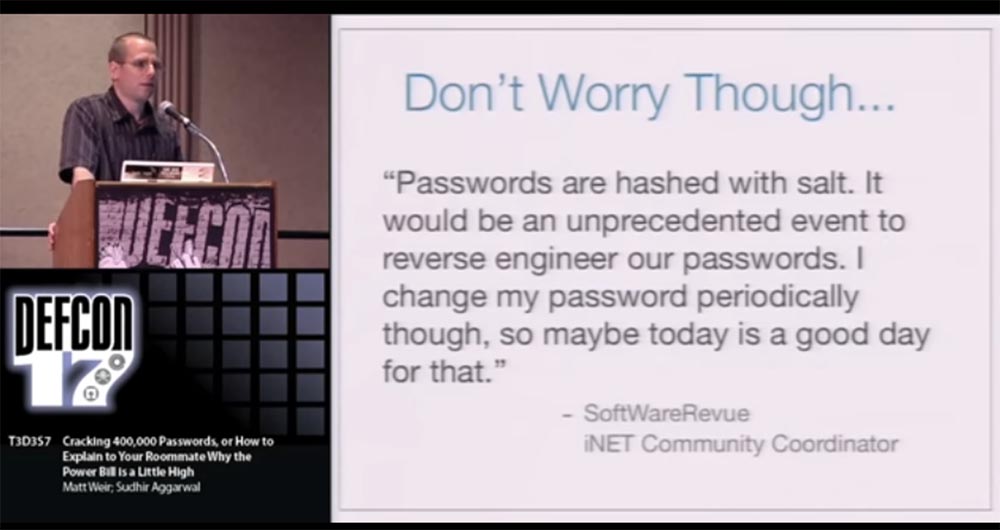
After that, the site owners reported that they were hacked, but users do not have to worry, because now they are safe. At the same time, they expressed one thought, which in reality was deceptive and dangerous, I quote the words of the iNET community coordinator : “Passwords have“ raisins ”, and it will be an unprecedented event if someone can redesign them. I periodically change my password, so maybe today is a good day for this. ”
It looks as if I say: “Hi guys, you know, the copy room is on fire, but don’t worry, there’s a fire extinguishing system there, so it’s absolutely impossible for this building to burn to ashes. But sometimes I like to go out at lunchtime, so you too can walk outside for now if you want. ” This is one of the reasons why I decided to hack this list here.
Further, the coordinator published the following statement: “Not a single credit card of users or PayPay account was hacked.” Probably only because the hacker didn't need it. And then there was a new failure - the same site was re-hacked by the same hacker on April 7, and this time he published about 202,000 password hashes and 2218 credit card numbers online.
I will never go to a site whose administration declares: “yes, two thousand credit card numbers have been stolen from us, but the rest are safe!”
I want to clarify the situation a little. People are being hacked, that's a fact, and I don't want to blame Web Hosting Talk for this . Trying to save and pull something out of your system right after it was hacked is a difficult problem, especially if users repeatedly called to you about the need to make backup copies of the system. Therefore, I think the main problem of Web Hosting Talk is that they downplay the risks faced by their users. And behaving on their part was very dangerous.
Because you, at least, should provide users with something like a ticking clock, which would indicate the need to log in and change your password, and not only for this site, but for all other sites, as quickly as possible. This is very important, because soon I discovered an interesting fact about this site: after the first attack, 1348 users changed their passwords, which accounted for only 0.6% of the total number registered on the site!
That is why the hacker had an excellent opportunity to return and re-hack the site using the same unchanged user credentials, or even use them to hack other sites where they were also registered.
I wanted to find out if the hash of this site was really so weak, and turned to Googleto find out which software this site uses. It turned out that this is the forum engine vBulletin , written in PHP and using the MySQL server to maintain its database . Google also answered the question which hashing algorithm this site uses is double-hashing MD5 (MD5 (Password) .salt) . That is, you take the user's password, hash it with MD5 and once again hash the received password hash with the same MD5. I didn’t know how “John the Ripper” would deal with such hashing, so I wrote my own “cracker”. But I did not try to crack the real passwords of this site, since it would take not a few weeks, but simply decided to test the presence of the password “password” in the list and immediately hacked 1109 people who used the word “password” as a password.
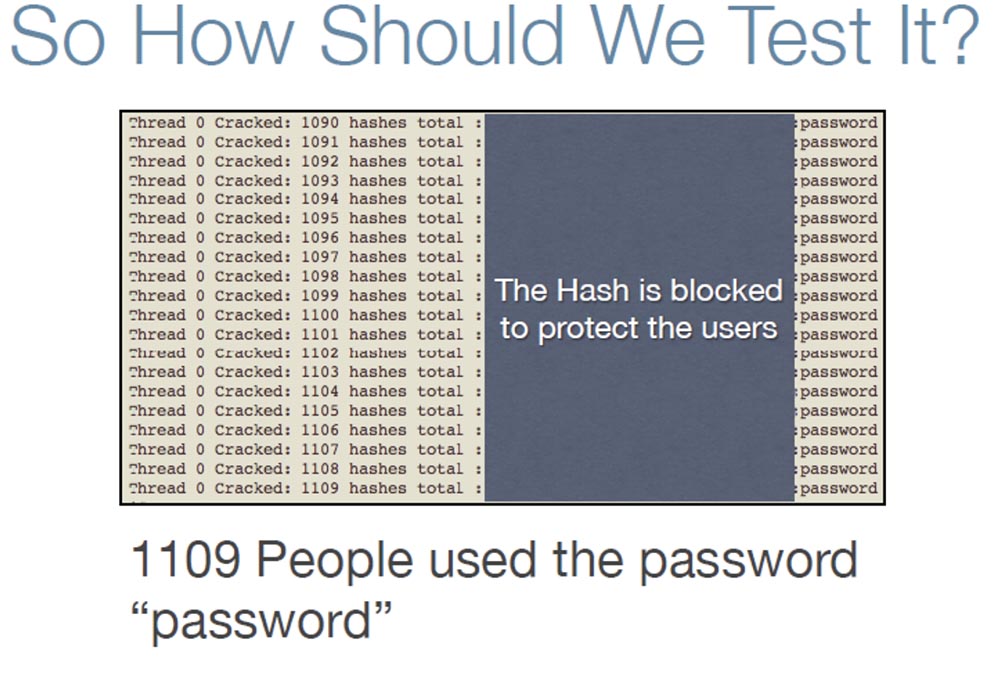
I want to say that the "highlight" in the password really becomes a problem for the attacker and therefore important to the user. I continue to "advertise" passwords with different "twists" because for a hacker, this would mean having to "guess" the hash of each password for each individual user. If we take for example the phpbb site , where one-step MD5 hashing was usedthen the hacker spent about 1 hour cracking the password list. For such an attack on the Web Hosting Talk password list , if they were protected by the “raisins”, it would take 200 thousand hours.
What else needs to be said? As you know, I spent almost a week hacking 34% of the hashes of 200 thousand phpbb users with my Dell computer . Moreover, most of these passwords were on the list of already cracked passwords from other sites, and no “mangling” was used for them. Tell me, do you know people who use the same password on more than one site? I think yes.
It is necessary to explain to people that the “raisins” will not protect individual users if some idiot from their colleagues publishes a hash of their password on the Internet, stating that it is impossible to crack it, because there is a “zest” in it. Because the hacker, having received this information, will not try to crack each of the 200 passwords, but will take on breaking this one hash. In this case, it will be possible to organize a targeted attack on specific users who have the words “admin” or “webmaster” in their email address.
The hacker will try to attack these users, because there is a good chance that these people use such a password for their site. So remember that, even creating a password with a "twist", you should not assume that you are completely secure against hacking.
Thank you for your attention, you can send your questions to me at weir@cs.fsu.edu.
Then follow a few slides from the speaker's CD, which were not included in the video presentation due to lack of time.
Hacking pass phrases: the problem is that usually we don’t have enough examples of pass phrases like “It's fun to try the impossible”! Therefore, it is recommended to use the input dictionary of pass phrases of the following type: "!! It's fun !!," or "!! ifttti!".
When creating pass phrases, use the approach that Mad Libs offers , that is, form unexpected phrases.
Hacking graphic passwords: users sometimes use ASCII encoding as passwords, for example:

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
If you do not follow any rules for creating passwords, the password may look like a simple PHP list . People hate rules, hate phrases and do not want to use them. If you give them will, they will type in any minor password and they will assume that the work is done. In this case, it is safer if they do not use simple basic words, therefore it is better to use large input dictionaries.

The greatest contribution to the creation of input dictionaries made Sebastian Ravo - he created huge lists of words from each article contained in Wikipedia, as well as from similar projects. If you know a word, then you create a Wikipedia article for it. But what's good for Wikipedia is not always good for creating secure passwords, so if the dictionary is really huge, you cannot apply many different rules to it. You can find a list of Wikipedia words on his blog at http://blog.sebastien.raveau.name/ .
If there is a policy for creating passwords, then you should follow these rules:
it is better to use small thematic, specialized word lists in dictionaries, the
best dictionaries are based on previously cracked passwords.
For privacy reasons, I cannot provide you with a list of cracked passwords, but believe me, just as the rich one gets richer, the hacked password becomes stronger if you see where a mistake was made when you created it and fix it.
There are lists of such passwords, and we can see that the same users are repeated in these lists, because they used the same password everywhere.
It will be useful if you can extract the basis of such passwords. For example, the password "TigerWoods1982" should not be too common, but people constantly use the password "TigerWoods" . Therefore, you can extract this basic phrase "TigerWoods"to create a strong password based on it. There are some tools on my CD that will help you make it much easier.
The rules for creating words for passwords are very simple:
- learn how to create new words based on previously cracked passwords;
- JtR only cracks weak passwords well, which is why it is designed, but it does worse with complex passwords. I made several JtR- based password rules available for download ;
- Minga also hosts a number of easy-to-use online password-creation tools: http://marc.info/?l=john-users&m=123820850908275&w=2 , http://marc.info/?l=john-users&m=124053430313891&w=2
However, you will need to develop your own rules if you want to crack really strong passwords. There is another tool on my CD that allows you to parse passwords into 2 different sets.
The first is the passwords about which we know how they were created, for example, password123 , and the second is passwords, the principle of creation of which is unknown to us. This is very good, because you do not need to go through 200 thousand passwords like password123 and then try to come up with new rules to use them. You will get a small list from which you will see, for example, that people use emoji to create passwords by inserting emoticons into words. You will learn new keyboard shortcuts, and it will help you create strong passwords much easier.
As I said before, I decided to move away from the built-in JtR rules and developed my own way of generating "clues". Good results are brought by the method of "probabilistic password cracking", probabilistic cracking . I have already said that our reactions are universal: we run through something with our eyes, we nod, we say that it looks great, but to ourselves we think: “what an academic bullshit”! But I want to say that we really wanted to learn how to create the most resistant to cracking passwords, so we tried to do everything in the best possible way.
It is known that people like some words more than others, for example, password , monkey , football. It is also known that people prefer certain rules of “mangling” passwords by adding 123, 007, $$$ or uppercase first letters of words. To increase resilience, we need to optimize password rules in an atypical way. This is a time consuming process. From the John the Ripper email list, I learned about a person who created 10 or 12,000 JtR rule configuration files , trying to get the most out of it.

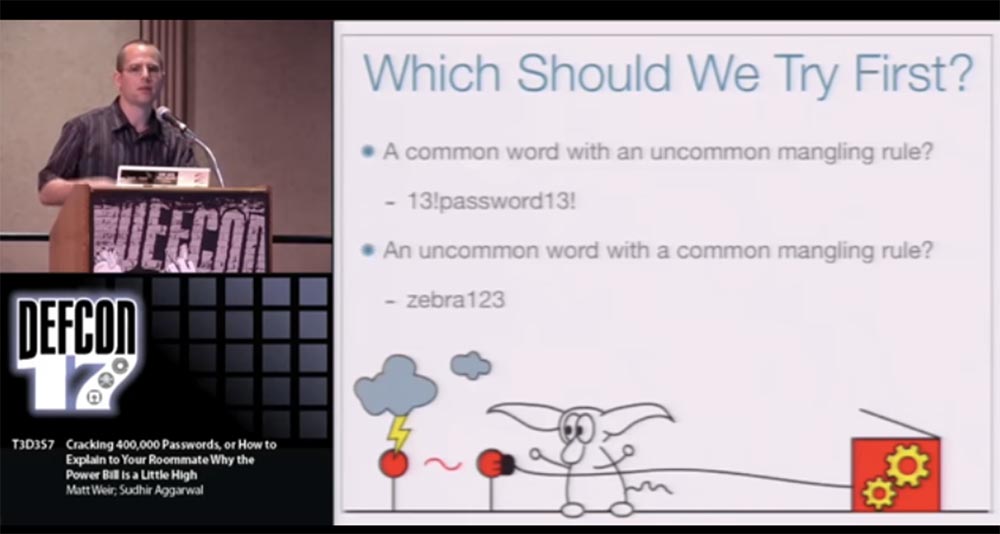
I am much lazier than him, so I didn’t do it. I just tried to simplify the process of creating passwords and automate the process. We process all the information and determine the probability of using certain words and combinations, that is, we rank the passwords according to the probability of guessing. And then we use the least likely combination of words and “tinkering” to create a password. So, this is what we should try to make our passwords stronger:
- use a common word with an unpredictable way to distort a password, for example 13! password13 !;
- use a rare word with a common "mangling", for example, zibra123.
With this way we have achieved success. If you can’t split passwords into two sets according to the features mentioned above, we have a trainer program that automatically analyzes the list of known passwords and generates what we call "grammar." This “grammar” contains all the necessary information, so we use two such “grammars” to explore the possibilities of password cracking.
Due to this, we determine the probability of using everything we have: words in dictionaries, rules for “mangling” words in passwords, algorithms for placing characters like “two digits at the end of password 12”, in contrast to which you can use the rule “two digits at the end of password 21 ", and the like.
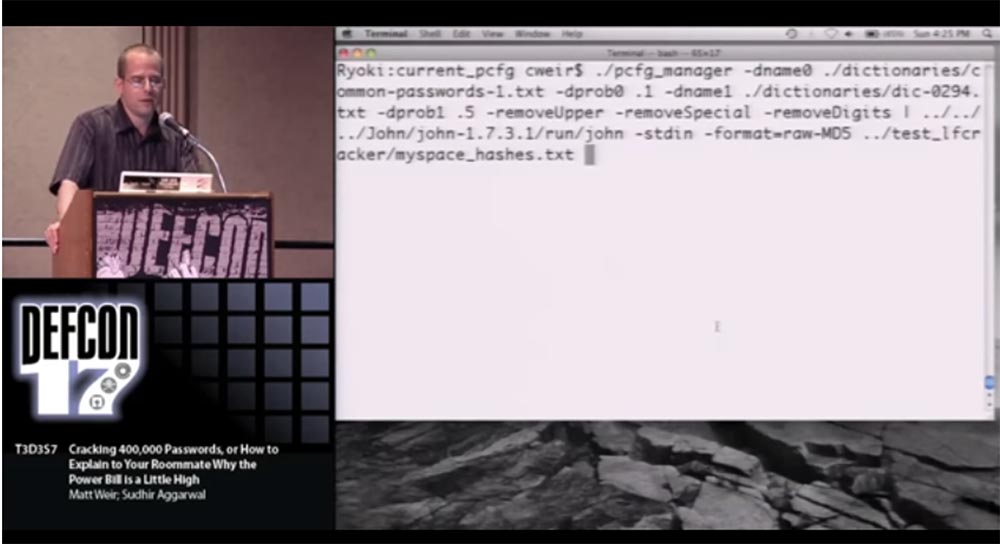
I can continue to talk about it, but I'd better show you a vivid example of how this works. I don’t expect you to read everything on the slide, so I’ll tell you what I’m going to do. I'm going to launch our probabilistic password cracker and feed him two different input dictionaries. In fact, it supports up to 10 dictionaries, but it's better not to go crazy.

One input dictionary contains the most common passwords, so it has a high probability of guessing. The second dictionary contains the least common words, and the password cracker will switch between these two dictionaries. After that, I “salt” the result right in John the Ripper , because, as I said, I want to create my own password hashing algorithm.
Unfortunately, we cannot use the PHP list here , again because of confidentiality, because it is impossible to demonstrate password cracking in front of everyone, our institute does not recognize this as legitimate. Therefore, I will demonstrate the work of a cracker using the MySpace list as an example , which was disclosed 2 years ago. All passwords in it were presented in plain text, so that you can read them, and this operation does not present any additional danger.
We used MD5 hashing , this is exactly the same hash algorithm that is used for the phpbb list , so here the attack on phpbb is largely simulated. About 17,000 password hashes were loaded without “highlights”, and we actually divided their lists into several different parts for typical machine learning.
Right now on the screen you see how fast the password is cracked, so you should probably use a slower hashing algorithm. It also switches between different rules, so it’s not just “try 1 digit, try 2 digits” attempts and so on.
You see that passwords are of a different size, usually people use a length of 6 to 8 characters and sometimes there are exclamation marks at the end of the password.
There are several other types of optimization that we are trying to build into this algorithm, because our work is still ongoing. One of these things is the inclusion of targeted attacks in the process, when instead of cracking some big old password, the program tries to crack the password of a specific user.

All you need for a targeted attack is to use a different input dictionary, for example, children's names, birthdays, zip codes, and so on.
You see that the hacking process on the screen has slowed down a bit, these are design features, if hacking is simple enough, the process is accelerated. But since it is based on a probabilistic model, passwords are more likely to be guessed with the highest probability, and passwords are less likely to be cracked a little slower, as this is where a larger number of “clues” are used.
You also noticed that in this list there are mostly rather weak passwords. This is explained by the fact that we are just starting a password cracking session and do not want to use too complex or extended passwords.
If you have a hacking strategy in which you intend to attack only strong passwords, you need to create an appropriate list based on these passwords and start the session by hacking only strong passwords.
So, our program has finished its work. The hacking process took 2 minutes and 30 seconds, during which time 5,586 passwords were cracked, or guessed correctly, which is just over 30% of the total amount available.
There are a hundred reasons why I think that the password policy needs to be changed, not because the use of passwords is something backward and stupid. It's just that I actually believe that they are doing our security more harm than good. Especially if we are talking about offline attacks that cannot be resisted if you do not change your password every 2 minutes.
And now I want to talk about the technique of Brute Force attacks . These attacks can actually do a lot of damage if you don't take care of the defense.
They are quite powerful, but you can resist them, you just need to use your brains. To do this, you need to analyze the frequency of using letters and symbols to find out which letters or symbols are used relatively rarely in passwords.

Surely you have all heard about this, so try, for example, to use the letter Q more often, which is quite rare in passwords. Your hacking algorithm should not seek to crack all passwords; you need to focus on the most likely ones.
A more “advanced” version is the Markov model . It is based on the conditional probability of letters, for example, if you have two letters Q in a row, you are more protected than when you have U in your letter set, because U usually follows the letter Q in words. It also assumes that the password is created in “Human” manner, that is, if a certain letter is located in this place of the word, then it is followed by another letter, which is most often used in precisely this letter combination. The Markov model is used by the JtR hacking algorithm .which takes into account that the letter Q in “human words” is usually followed by U or W, but not S or Z. Do not think that I’m trying hard to get “John the Ripper” here, but this is a really good program.
We can further deepen the logic of Brute Force by applying targeted attacks. They are based on the use of such password creation principles:
- people tend to start a password with a capital letter;
- they usually add numbers at the end of the password;
- for the same reason they like to use php or phpbb combinations in passwords.
The same principles can be used for “dictionary attacks”. There is a very good tool for testing the effectiveness of attacks called “Crunch” , it can be found on the programmers' forum remote-exploit.com .
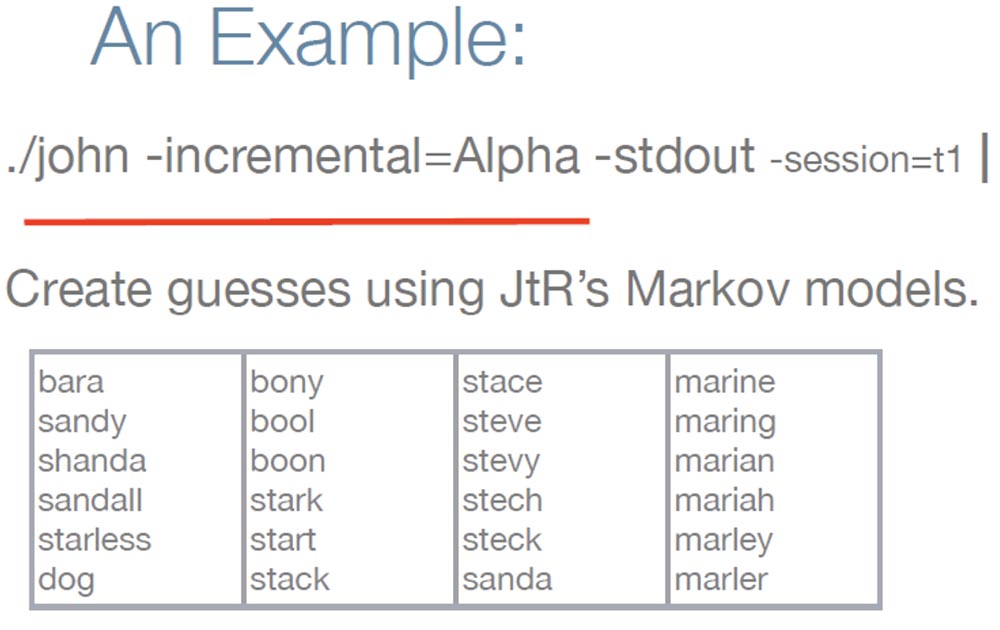
I want to give you an example of hacking a “strong” password using the Brute Force attack . To do this, I first run JtR and it starts generating “guesses” based on lowercase letters using the Markov model.

You can see that there are a lot of real words in this list, such as dog, starless, marine, which are in the input dictionary. But thanks to the Markov model, he also generates words that are absent there, for example, stech. But since we solve a strong password, it is necessary to apply some additional logic. Therefore, I use scripts that provide a capital letter at the beginning of a word, and also add special characters and numbers at the end of a word.

As you can see, these "otgadki" look like a real strong password. Now that you know about the password policy, you should click on the “turn off laziness” button and spend 5 minutes to give these words a certain size, since they look too short.
We can also try to upload everything back to JtR.and try to crack the hashes.

At the beginning of the presentation, I talked in detail about hacking the phpbb.com users' password list , and now I want to talk a little about hacking the Web Hosting Talk list .

He was hacked on March 21, 2009, at least at that time the list was published on the network, and the attacker turned out to be a real scoundrel because he posted about 200 thousand logins and passwords and other confidential information of users in open access. He stole the hashes, and then deleted the site itself and all backups. This was a huge hit for the system administrator.

After that, the site owners reported that they were hacked, but users do not have to worry, because now they are safe. At the same time, they expressed one thought, which in reality was deceptive and dangerous, I quote the words of the iNET community coordinator : “Passwords have“ raisins ”, and it will be an unprecedented event if someone can redesign them. I periodically change my password, so maybe today is a good day for this. ”
It looks as if I say: “Hi guys, you know, the copy room is on fire, but don’t worry, there’s a fire extinguishing system there, so it’s absolutely impossible for this building to burn to ashes. But sometimes I like to go out at lunchtime, so you too can walk outside for now if you want. ” This is one of the reasons why I decided to hack this list here.
Further, the coordinator published the following statement: “Not a single credit card of users or PayPay account was hacked.” Probably only because the hacker didn't need it. And then there was a new failure - the same site was re-hacked by the same hacker on April 7, and this time he published about 202,000 password hashes and 2218 credit card numbers online.
I will never go to a site whose administration declares: “yes, two thousand credit card numbers have been stolen from us, but the rest are safe!”
I want to clarify the situation a little. People are being hacked, that's a fact, and I don't want to blame Web Hosting Talk for this . Trying to save and pull something out of your system right after it was hacked is a difficult problem, especially if users repeatedly called to you about the need to make backup copies of the system. Therefore, I think the main problem of Web Hosting Talk is that they downplay the risks faced by their users. And behaving on their part was very dangerous.
Because you, at least, should provide users with something like a ticking clock, which would indicate the need to log in and change your password, and not only for this site, but for all other sites, as quickly as possible. This is very important, because soon I discovered an interesting fact about this site: after the first attack, 1348 users changed their passwords, which accounted for only 0.6% of the total number registered on the site!
That is why the hacker had an excellent opportunity to return and re-hack the site using the same unchanged user credentials, or even use them to hack other sites where they were also registered.
I wanted to find out if the hash of this site was really so weak, and turned to Googleto find out which software this site uses. It turned out that this is the forum engine vBulletin , written in PHP and using the MySQL server to maintain its database . Google also answered the question which hashing algorithm this site uses is double-hashing MD5 (MD5 (Password) .salt) . That is, you take the user's password, hash it with MD5 and once again hash the received password hash with the same MD5. I didn’t know how “John the Ripper” would deal with such hashing, so I wrote my own “cracker”. But I did not try to crack the real passwords of this site, since it would take not a few weeks, but simply decided to test the presence of the password “password” in the list and immediately hacked 1109 people who used the word “password” as a password.

I want to say that the "highlight" in the password really becomes a problem for the attacker and therefore important to the user. I continue to "advertise" passwords with different "twists" because for a hacker, this would mean having to "guess" the hash of each password for each individual user. If we take for example the phpbb site , where one-step MD5 hashing was usedthen the hacker spent about 1 hour cracking the password list. For such an attack on the Web Hosting Talk password list , if they were protected by the “raisins”, it would take 200 thousand hours.
What else needs to be said? As you know, I spent almost a week hacking 34% of the hashes of 200 thousand phpbb users with my Dell computer . Moreover, most of these passwords were on the list of already cracked passwords from other sites, and no “mangling” was used for them. Tell me, do you know people who use the same password on more than one site? I think yes.
It is necessary to explain to people that the “raisins” will not protect individual users if some idiot from their colleagues publishes a hash of their password on the Internet, stating that it is impossible to crack it, because there is a “zest” in it. Because the hacker, having received this information, will not try to crack each of the 200 passwords, but will take on breaking this one hash. In this case, it will be possible to organize a targeted attack on specific users who have the words “admin” or “webmaster” in their email address.
The hacker will try to attack these users, because there is a good chance that these people use such a password for their site. So remember that, even creating a password with a "twist", you should not assume that you are completely secure against hacking.
Thank you for your attention, you can send your questions to me at weir@cs.fsu.edu.
Then follow a few slides from the speaker's CD, which were not included in the video presentation due to lack of time.
Hacking pass phrases: the problem is that usually we don’t have enough examples of pass phrases like “It's fun to try the impossible”! Therefore, it is recommended to use the input dictionary of pass phrases of the following type: "!! It's fun !!," or "!! ifttti!".
When creating pass phrases, use the approach that Mad Libs offers , that is, form unexpected phrases.
Hacking graphic passwords: users sometimes use ASCII encoding as passwords, for example:

Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
