Vulnerability Scanner Interaction with Metasploit. Part 1
- Tutorial
We are starting a series of training articles on the interaction of vulnerability scanners with Metasploit.
Software Required: Kali Linux .
Required knowledge: experience with the console of Linux-systems (in particular, the Kali Linux distribution) and the Metasloit console .
Most attacks are based on software vulnerabilities or configuration errors. In this regard, the recommended measures to ensure the information security of the organization are regular scanning of the system for vulnerabilities and penetration testing.
Scanning for vulnerabilities allows you to check the range of specified IP addresses for possible problems in the security system, providing Pentesters with information about likely attack vectors. When working with vulnerability scanners, you need to remember that they can be wrong and provide false or incorrect information.
As you know, the Metasploit Framework is a tool for creating, testing and using exploits. But, thanks to the support of modules and plugins, it may well be suitable for searching for vulnerabilities.
In the first part, we will consider the modules built into Metasploit, which allow you to identify the most common security holes.
The SMB Login Check module connects via the SMB protocol to a specified range of ip addresses and determines whether a username / password can be used to access the target.
We load the module,
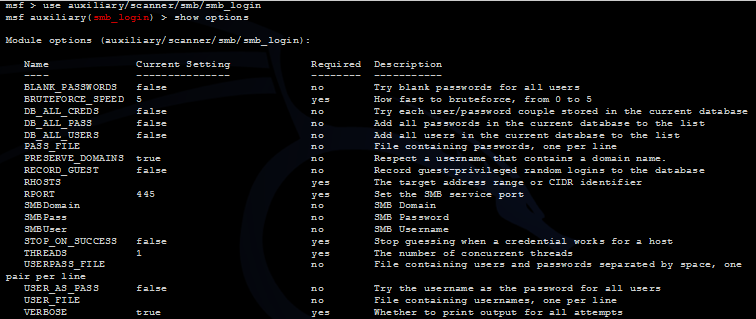
set the necessary settings and start it.
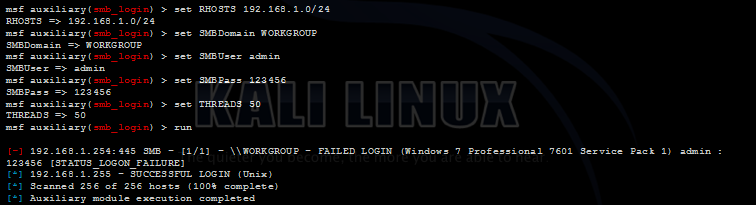
It should be borne in mind that such a scan will not go unnoticed, because every failed authentication attempt creates a corresponding entry in the Windows log. Further, successful scan results can be used in the windows / smb / psexec exploit module to create a Meterpreter session.
The VNC scanner will search for the VNC server without password authentication. Some system administrators neglect information security requirements and do not set passwords for establishing a connection, which is detected during the scanning process. To use the VNC scanner, you first need to select the auxiliary / scanner / vnc / vnc_none_auth module,
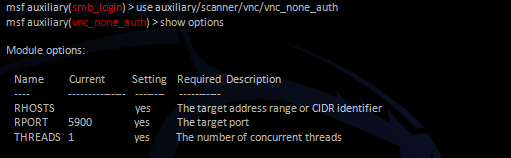
set the settings, and then run it.
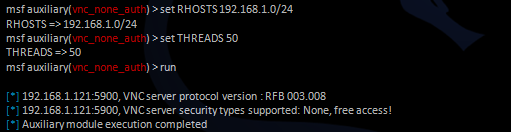
At the end of the scan, a result with a list of vulnerable VNC servers will be displayed.
WMAP is a multi-functional vulnerability scanner based on SQLMap. Thanks to the interaction with Metasploit, we can scan web applications directly from the framework.
First, we’ll use the built-in Metasploit Web Crawler module - a search robot that allows you to determine the structure of the site and works in conjunction with wmap.
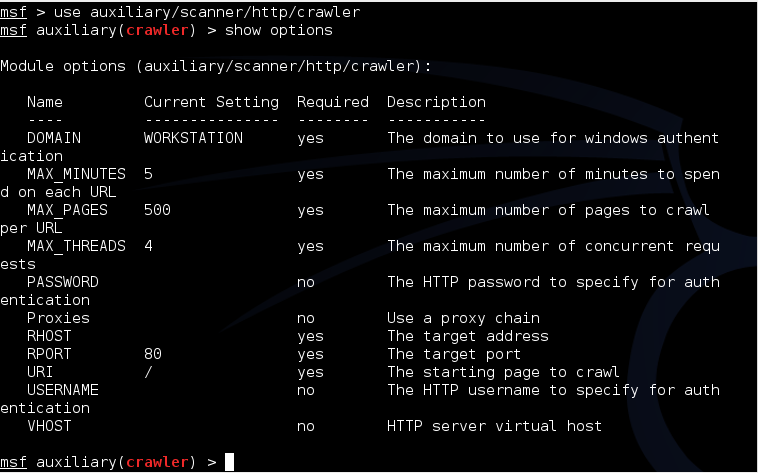
specify the address of the site and its start page (left the default value). Now the module is ready to work.
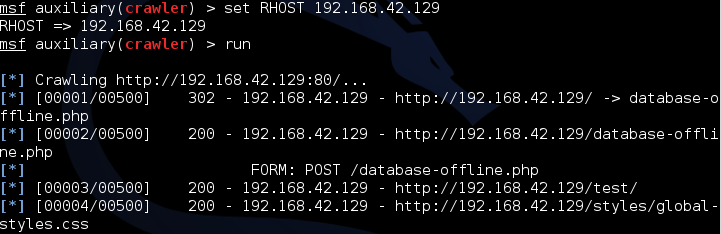
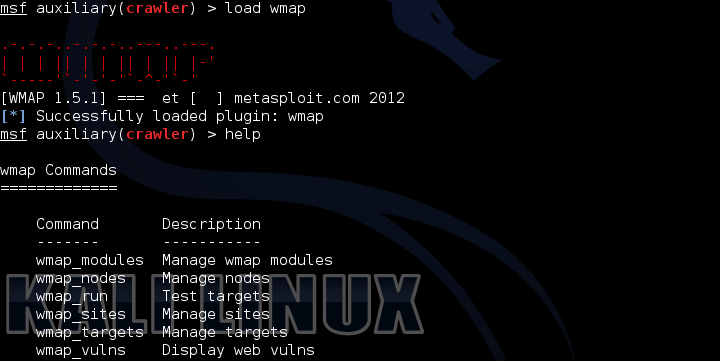
Next, download the wmap plugin.
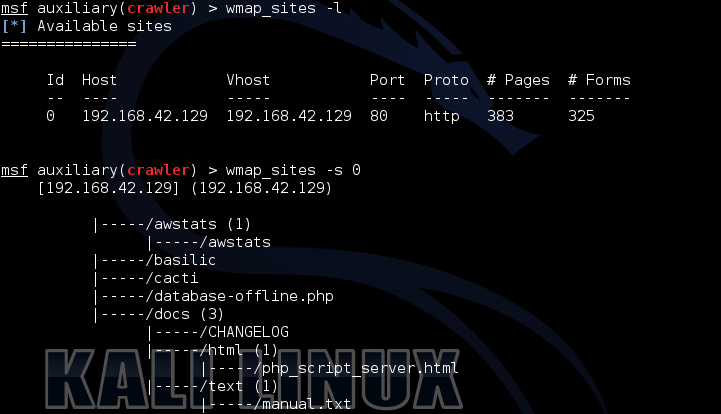
At this stage of the scan, we already have information about the structure of the site, which is stored in our database. You can view it using the wmap_site –s [id] command, where id is the target number in the wmap_sites –l list.
Now we ’ll determine the purpose
Here you can specify both the range of ip-addresses and specify the url leading to a specific section of the site.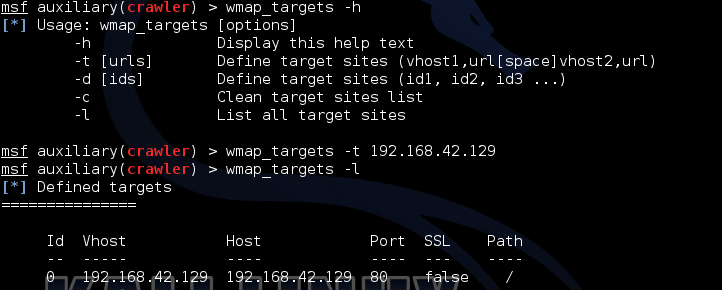
The automatic vulnerability search is launched with the wmap_run command. We will
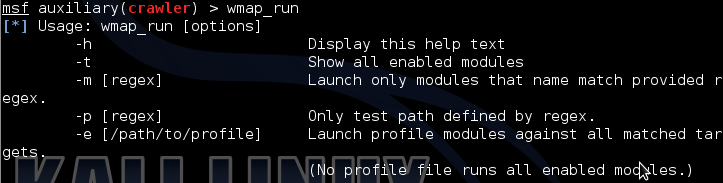
look at the list of modules that are available for scanning our target.
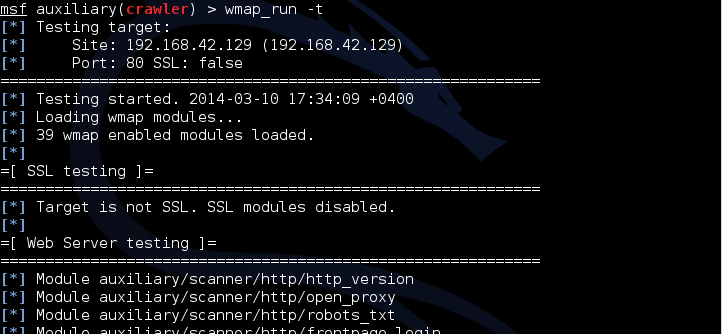
You can run as a specific module, indicating the path to it, for example, wmap_run -e auxiliary / scanner / http / robots_txt, and start all of the listed modules at once (which we and we’ll do it)
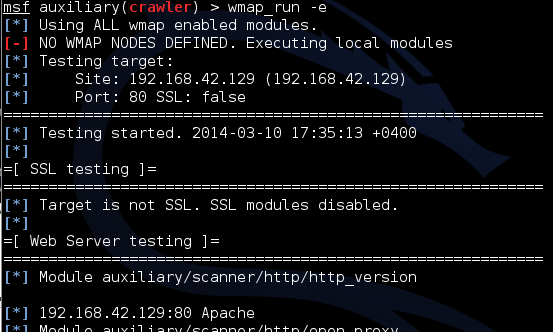
After the scan is completed, information about the detected vulnerabilities will be stored in the WMAP database. Let's see what he found there.

To be continued ....
References:
Metasploit Unleashed. Vulnerability Scanning
Metasploit Unleashed. Scanner VNC Auxiliary Modules
Rapid7. VNC Authentication None Detection
Rapid7. CVE-1999-0506 SMB Login Check Scanner
Metasploit Web Crawler
Metasploit Redmine Interface. Metasploit Framework. WMAP
Software Required: Kali Linux .
Required knowledge: experience with the console of Linux-systems (in particular, the Kali Linux distribution) and the Metasloit console .
Most attacks are based on software vulnerabilities or configuration errors. In this regard, the recommended measures to ensure the information security of the organization are regular scanning of the system for vulnerabilities and penetration testing.
Scanning for vulnerabilities allows you to check the range of specified IP addresses for possible problems in the security system, providing Pentesters with information about likely attack vectors. When working with vulnerability scanners, you need to remember that they can be wrong and provide false or incorrect information.
As you know, the Metasploit Framework is a tool for creating, testing and using exploits. But, thanks to the support of modules and plugins, it may well be suitable for searching for vulnerabilities.
In the first part, we will consider the modules built into Metasploit, which allow you to identify the most common security holes.
SMB Login Check
The SMB Login Check module connects via the SMB protocol to a specified range of ip addresses and determines whether a username / password can be used to access the target.
We load the module,
use auxiliary/scanner/smb/smb_login
set the necessary settings and start it.

It should be borne in mind that such a scan will not go unnoticed, because every failed authentication attempt creates a corresponding entry in the Windows log. Further, successful scan results can be used in the windows / smb / psexec exploit module to create a Meterpreter session.
VNC authentication
The VNC scanner will search for the VNC server without password authentication. Some system administrators neglect information security requirements and do not set passwords for establishing a connection, which is detected during the scanning process. To use the VNC scanner, you first need to select the auxiliary / scanner / vnc / vnc_none_auth module,

set the settings, and then run it.

At the end of the scan, a result with a list of vulnerable VNC servers will be displayed.
WMAP Web Scanner
WMAP is a multi-functional vulnerability scanner based on SQLMap. Thanks to the interaction with Metasploit, we can scan web applications directly from the framework.
First, we’ll use the built-in Metasploit Web Crawler module - a search robot that allows you to determine the structure of the site and works in conjunction with wmap.
use auxiliary/scanner/http/crawler
specify the address of the site and its start page (left the default value). Now the module is ready to work.

Next, download the wmap plugin.
load wmap
At this stage of the scan, we already have information about the structure of the site, which is stored in our database. You can view it using the wmap_site –s [id] command, where id is the target number in the wmap_sites –l list.
wmap_site –s 0
Now we ’ll determine the purpose
wmap_targets -t 192.168.42.129Here you can specify both the range of ip-addresses and specify the url leading to a specific section of the site.

The automatic vulnerability search is launched with the wmap_run command. We will

look at the list of modules that are available for scanning our target.
wmap_run –t
You can run as a specific module, indicating the path to it, for example, wmap_run -e auxiliary / scanner / http / robots_txt, and start all of the listed modules at once (which we and we’ll do it)
wmap_run -e
After the scan is completed, information about the detected vulnerabilities will be stored in the WMAP database. Let's see what he found there.
wmap_vulns –l
To be continued ....
References:
Metasploit Unleashed. Vulnerability Scanning
Metasploit Unleashed. Scanner VNC Auxiliary Modules
Rapid7. VNC Authentication None Detection
Rapid7. CVE-1999-0506 SMB Login Check Scanner
Metasploit Web Crawler
Metasploit Redmine Interface. Metasploit Framework. WMAP
