Summ3r 0f h4ck: the results of a summer internship at Digital Security

For the third year in a row, we successfully continue the tradition of summer internships. As in previous years, we took interns in two technical areas: the research department and the security analysis department. The results of previous internships can be found here:
And today we will tell you how our Summer of h4ck 2018 went .
As practice shows, the main stream of internship summaries comes to the security analysis department; There were many people who wanted to spend the summer in Digital Security again, and therefore we created a special form for candidates, which was available on our website. Applicants had to work hard and demonstrate not only their knowledge and skills, but also the desire to develop professionally. Thanks to this, we were able to assess the level of training of future interns and select the most worthy of them. In addition, this time, Digital Security focused exclusively on office internship - we did not consider the remote internship option.
The
staff of the security analysis department
The employees of the research department solve problems related to reverse engineering, search and exploitation of vulnerabilities, system development and auditing of C / C ++ code; conduct research in the field of machine learning, blockchain and other interesting areas. The team is actively developing plug-ins, scripts, tools for automating the search for vulnerabilities in both static and dynamic (fuzzing).
Who are we waiting for? Lovers of interesting tasks, not succumbing to difficulties and in love with what they do!
Introduction
We were glad to see again familiar names and surnames in the lists of candidates for internship - some people already visited us last year, and they all very, very much enjoyed :) The company only supports this initiative. In addition, if you come again, you get more branded DSec merchandise!

These are the gifts we have prepared this year.
A little more detail about the selection process. Electronic questionnaires were posted on our website: a questionnaire from the research department allowed us to get an initial idea of the skills of a potential trainee in reverse, and in the questionnaire from the security analysis department there were ten small tasks that could / should be solved. We did not demand the solution of all the tasks, but the more correct the answers were given by the candidate and the better he explained the course of his reasoning, the more attention he received in the evaluation. However, this does not mean that it was easier to get into the research department :) Instead of a detailed questionnaire, the staff preferred to conduct an internal interview stage, where they found out the details of the level of training in a personal conversation.
As before, the interns were offered a list of topics that they could deal with during the internship. In addition, the guys could offer their own theme, we were always ready to listen to them.
We gave lecturers to trainees in different subject areas; Of course, I wanted these lectures to be interesting and useful to everyone, regardless of the level of training of the trainee.
Lectures included:
- Active Directory Security Audit
- Device networking and network protocols
- Web vulnerabilities
- Linux and Windows privilege escalation
- The exposure of Intel 64 architecture
- Research large C ++ projects using the example of Chromium
- Recovery of function names in the absence of symbolic information
- Code Instrumentation
- SMT, Z3, SSE, DSE, ...
- Other...
At the end of Summ3r 0f h4ck, the participants gave lectures already for us - they told whether they were able to achieve their goals, what difficulties they encountered during the research and what results they received from the internship. All successfully reaching the final were issued Summ3r 0f h4ck participant certificate 2018 . Some of the interns preferred to team up and work together, and we, of course, only welcomed this desire.
By a good tradition, we conducted a small survey of participants who successfully reached the end, and now we are sharing with you their feedback on the summer in Digital Security.
Questions for the mini-interview were as follows:
- Why did you decide to train in Digital Security? What attracted you to the company?
- Did you like the internship? What is especially remembered? How much reality coincided with your expectations?
- Tell us about your task / tasks.
- Did the tasks you worked on during the internship seem interesting? Was there something you wanted to do, but failed?
- Are you ready to return to the company for an internship or a job?
And some answers were given by some trainees:
Pavel Knyazev, the topic “Taint-analysis of ARM architecture”:
- After the end of the second course, I realized that I lacked skills in information security. I wanted not just to listen to the courses, but to work with my hands. The first thing I came across was the article about the Summer of H3ck from Digital security on Habré. Having almost zero experience, I decided to go.
- Internship liked. A spacious room, a large table and silence - I was provided with a workplace in the interns room. Nearby sits another pair of interns - workaholic. From time to time, mentors come to us to discuss plans, further actions. They are always ready to explain something, to throw the necessary link. I especially remember the ease of communicating with them - just Anton, Sasha, Dima. You can forget for a while that the big boss is sitting in front of you, and just talk.
- I had, I think, a very exotic topic: “Taint-analysis of ARM architecture”. Considering that neither about taint - analysis, nor about ARM architecture really knew anything, I was "overwhelmingly happy" that I had such a topic. To begin with, it was necessary to understand the differences between ARM and x86 (it was only familiar with it), to study the assembler of this architecture, the addressing modes. Then it was necessary to deal with existing means, which ... did not appear. Rather, they were, but one tool did not fit for the tasks of information security, the second did not have sufficient flexibility, and the third, DrTaint library- only recently began its existence. My task was to refine this library. A pleasant surprise was waiting for me here: the DrTaint library is based on DynamoRIO, and I knew it a little, but I knew. Despite the fact that DrTaint was quite small, it took almost two weeks to study the source code and understand the principles of its work. Only after these two weeks, I felt that I was not going to the bottom. Another week passed, and everything began to get better. I stopped being afraid and started changing the source code. If something went wrong, then DynamoRIO immediately reported it to me with its fall. As a result of the internship, I was able to find and correct several errors in the library, add new features, and demonstrate its efficiency. In the end, I was surprised to realize that I understand DBI and assembler for ARM.
- After I learned that taint-analysis facilitates the work of revolvers and even helps to detect software vulnerabilities, the development of DrTaint really interested me. I had enough of what I was doing.
- Collect things.

Running one of the tests
Evgeny Lukin, topic “Golang Social Bot”:
- The fact that DSQ is normal for students and allows them to work with real work projects. Besides, I’ve heard a lot about the company and I know that great people work in it.
- It was probably even better than I thought. I liked that everyone from the department can prompt almost on any topic and if there is a problem, then solve it. Expected more formalities, so to speak
- I had the theme of Golang Social Bot. This bot is used during penetration testing. The main goal was to write modules that collect the necessary data, such as passwords, configuration files and files in principle, allow you to interact with the file system. It was also necessary to think of fixing in the system and network work within the corporate network.
- Yes, as I said, I wrote modules. And although a lot of work was done, a lot of things remained
- Yes, there are cool people who can learn a lot.
Part of the work can be found here .
Dmitry Frolov, topic “Finalization of the UEFITool New Engine”:
- After reading reviews from interns of previous years, I realized that interesting projects related to revolvers are waiting for me here. And I did not lose.
- I really liked the internship, and the reality exceeded all my expectations. A very friendly atmosphere in the team created favorable conditions for working on the project, and the solution of the tasks set for me brought one pleasure.
- I’ve been interested in reverse engineering various low-level pieces for a long time, in particular the BIOS, so I chose the appropriate task. It consisted in the finalization of the program UEFITool NEwhich is designed to work with UEFI BIOS images. The NE addition means the New Engine: it was decided to rewrite the once original UEFITool, and so its new NE came into being. But UEFITool New Engine did not yet support the possibility of modifying the firmware with its subsequent reassembly, as it was in the original branch, and I had the task to return this function, and also add the ability to modify the NVRAM partitions (which were not supported in the old tool). ). I coped with the task and performed a couple more extras (for example, it was necessary to add the possibility of parsing some intricate structures). My curator and I contacted the developer of the tool, and we will soon have to send a pull request.
- The tasks are very interesting. In the process of solving them, I received a very good knowledge base in the field of BIOS, and I want to continue developing it.
- I would be happy to return both for internship and for work.

Generalized architecture of the modified UEFITool New Engine
The process of making a pull request to the main UEFItool repository can be viewed here .
The topic “Cisco Config Analysis Tool”
The following interns worked in a group on the general topic “Cisco Config Analysis Tool”. The result of their work can be found here .
Natalia Khodukina :
- I have long heard of the company as one of the leaders in the field of information security in Russia.
- I liked it, and reality completely coincided with expectations. It so happened that we worked together on the topic, so apart from practical and theoretical skills, I learned how to work in a team. In the discussions, new ideas and solutions were born, in addition, we helped each other to find and correct mistakes and shortcomings, share their (small) experience and get a new one. It was also pleasant to communicate with the staff, they all tried to convey information in the most understandable way, they were ready to answer all the questions and explain what remained unclear.
- We were faced with the task of developing a utility for analyzing network equipment configuration files for the presence of weak points and unsafe settings. To do this, it was necessary to get acquainted with the network equipment, learn about the various settings, try to configure the switch and test its performance and attack resistance.
- The tasks were really interesting, because I studied network technologies before the internship. Everything that was planned turned out to be done. However, in the process of research and development there was a mass of new ideas, which, I hope, we will realize.
- Of course yes.
Mikhail Dryagunov:
- Known company engaged in information security. Among the others, it is distinguished by various studies and publications.
- Yes, everything is super! Interesting reports and themes of projects. Of the most memorable - team development, and everything connected with it.
- I had a group project. First, we decided on the basic functionality, then divided the topics (it was necessary to understand what and how it works before writing for all these checks), we made a kind of wiki for possible weaknesses and security features in the switches. When everything was ready, we started writing the program itself. By the end of the internship, we wrote the functionality that was originally planned, but there were even more ideas and desired features. We plan to finish them and make a presentation at ZN.
- At first I wanted to deal with the topic of working with PayPass / PayWave, but she was already busy. The topic of the study of dynamic routing protocols was also interesting, but it seemed to me too open.
- Of course!
Ekaterina Fedoschenko, topic “Recovery of data structures by dynamic paths”:
- DSec's reputation is almost legendary. Heard about the research activities of the company, it was extremely interesting to touch all this. It seemed to me that this is a great chance to learn how to work in the practical information security, what skills are needed.
- Say what you liked - do not say anything. I remember a lot of things: wonderful lectures, many thanks to the guys who prepared the speeches; and communication with mentors and fellow trainees - what are enthusiastic, purposeful people, how much can you learn from them. Reality and expectations - neither idealistic nor pessimistic - did not coincide completely, and this was just the coolest experience. I also managed to experience an incredible feeling when the knowledge gained was useful not only as part of an internship.
- The topic of my internship was the restoration of data structures by dynamic tracks. There is a fair amount of academic work in public access, but the tools that solve this problem can be counted on the fingers. In the course of work, it turned out to consider two such tools - Recoverer and dynStruct ; It turned out that only one can cope (dynStruct), but it needs some work. It was also necessary to combine the results with static HexRaysPyTools - a cool plugin for IDA Prowritten by my mentor. Despite the fact that some successes have been achieved, there are still a lot of unsolved problems. Also, on Dmitry's advice, work was started on a test application that should cover as many ways of working with structures and classes as possible in order to check the effectiveness of existing tools, because this is also a rather urgent task.
- Everything was very interesting. It was desirable, but it was not possible to devote more time to the tasks of the internship: it is quite possible to combine work, although at times there was not enough strength and psychological discipline. An excellent, however, reason to know yourself and understand what to work on.
- With great pleasure. Thank you very much to the organizers and trainees!
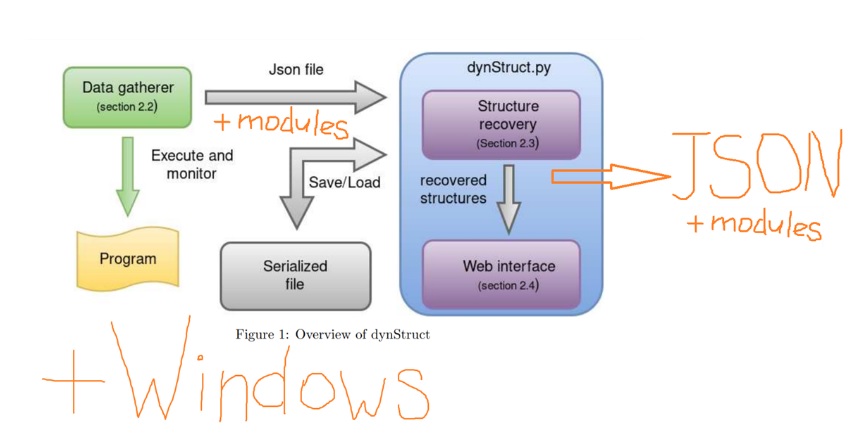
New modules for dynStruct
Vitaly S., topic “We are looking for bugs in hypervisor web interfaces (proxmox / kimchi / oVirt)”:
- This is the only company in the city that holds such events. Perhaps there are other companies, but they are unknown to me. I think that some of the universities can somehow directly interact with information security companies, without making the internship accessible, like with Digital Security. I know about these practices. I believe that other companies should learn from Digital Security. If not in the organization, then at least in the very idea and accessibility. The company is professionally engaged in practical information security.
- Internship liked. She can not not like it. I remember the fact that I talked with the guys studying at the university, which I once graduated from. On familiar to me specialties with famous faculty :). Labs are cool. I did not expect that there will be such a number of virtual machines. Waiting / reality. I realized that my skills leave much to be desired. I realized what directions I should pull up. What to read and where to look.
- My task was to find flaws and vulnerabilities in virtualization (web) management systems (open source). In this case, these are projects where developers keep track of the safety of their developments, but not everywhere. The topic was quite voluminous, and the work continues beyond the scope of the internship.
- The tasks are mostly interesting. Light, I would not call them. When choosing a topic it is difficult to decide something, without rushing to extremes. Nice to see familiar words in the names of topics. There are a couple lifehacks. Do not take more than one topic. It will be difficult for you to combine both the topics themselves and the work, unless of course the topic does not coincide with your main work. Take the topic, in which there are directions that you may have encountered or are currently engaged. There are a number of personal trends, but they are very small. Basically, what you encounter in practical work, and what thoughts are, but there is no time to check.
- Ready to return for internship. Work - maybe in the future.
The hypervisors covered in the study:
Nikita Knyzhov, “Feedback-driven fuzzing open source projects” topic:
- Because I know only a couple of companies other than Digital Security, which do the same interesting things as in the research department.
- I liked it very much. It was especially interesting to talk with those who work professionally in the field, some very useful lectures with life examples.
- My task was to conduct a study of fuzzers (forks and related ones in afl), to understand the principles of operation, to structure and compare on a test application, which fuzzer I found how many vulnerabilities.
- A very interesting task, the area is relevant in science and industry. I did not know that fuzzers could be so tricky and complicated. I even naphazzil dos-vulnerability in ffmpeg during the internship.
- Of course, ready!
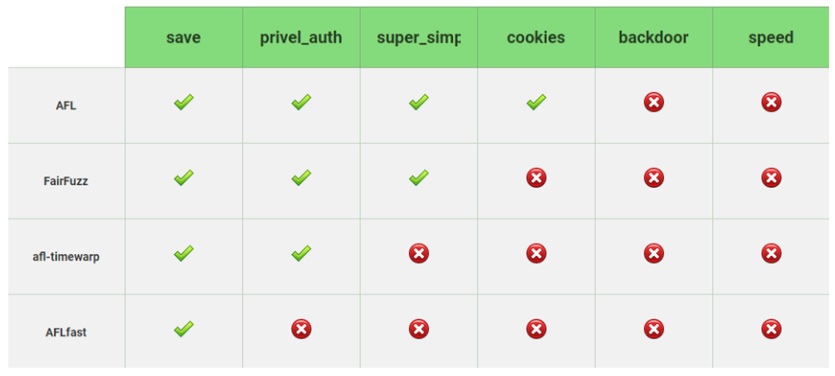
Summary table of opportunities for fuzzing open source projects by
Stepan Besklubov, topic “Tracing based on ARM processor hardware capabilities”:
- I know about DSec a long time ago, mainly from friends and acquaintances in the field of information security, and I am also very attracted to the company's active participation in the life of Russian and international information security.
- The internship is definitely liked. Especially memorable lectures and friendly staff, ready to help on any issue. My expectations were fully met.
- The topic of my internship was “Tracing based on the hardware capabilities of the ARM processor”. I was studying the ARM CoreSight technology, tracing programs using it, and writing a plug-in to display the resulting trace in IDA Pro. He also studied the principle of the ARM TrustZone, and how these two technologies interact with each other.
- The tasks were quite interesting and fascinating. It was especially interesting to work with boards based on ARM processors. I managed to do all that I wanted.
- I am glad to be ready to return to the company as an employee.
Plugin for IDA Pro for parsing shot trails
The plug-in's code and how to use it can be found here (instructions for setting up CoreSight are attached).
Vladislav Lunin, topic “Reverse engineering based on string information”:
- I saw a post on Habré about the results of last year's internship, read about the projects of interns, as well as their reviews, and decided to try.
- I really liked the internship, the reality turned out to be predictable: everything that you don’t know, google, if you don’t find the right one, you turn to the mentor (s), he (and) is ready to help you at any time.
- The name of my task was “Reverse engineering based on string information”. Engaged in writing a plugin for IDA PRO. The plugin allows you to view all the lines in a binary file, shows them by function belonging, allows you to go directly to the data segment and to the place where the lines are called in functions, rename functions, search for strings (and) by keywords. It also searches in real time for lines (and) in the current function, or for a given depth, which can be negative or positive, while adding depth, the display of lines takes a tree structure that demonstrates the arrangement of lines relative to the current function. And restore rows.
- Yes. I wanted to add to the plugin the ability to restore function names based on string information, but I didn’t have time, I think I’ll finish it in my free time.
- Of course!

Plugin for IDA PRO
Conclusion
Based on the results of previous years, we continue to improve the internship program to make it both convenient and useful, both for ourselves and for the participants. Our team was very pleased to work with the guys, and we very much hope that it was mutual :)
See you next summer!
