LG smart TVs spy on users
- Transfer
It all started with the fact that I paid attention to the ads that my new SmartTV from LG shows. After a little investigation, I stumbled upon a video for corporate customers telling about LG's advertising opportunities. The video is quite long, the essence is that LG Smart Ad collects information about the user's favorite programs, his behavior on the network, including the collection of keywords used in the search, and other information about personal addictions. All this is used to display targeted advertising.
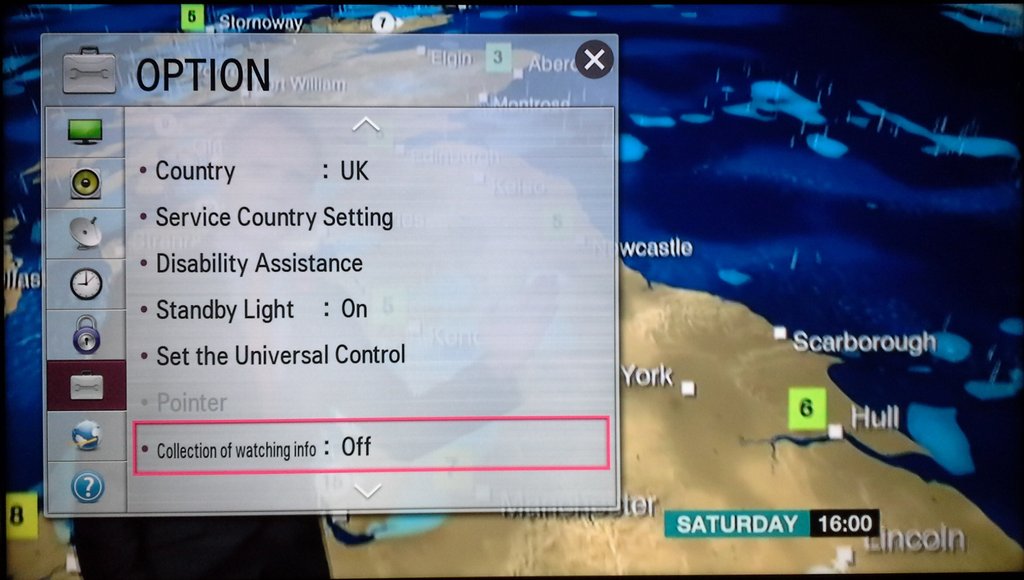
In fact, in the system settings there is an option “Collection of watching info”, which is enabled by default. To see this setting, the user must scroll to the bottom of the menu. In addition, this item does not have a context help with a detailed description of the option, unlike all other items.
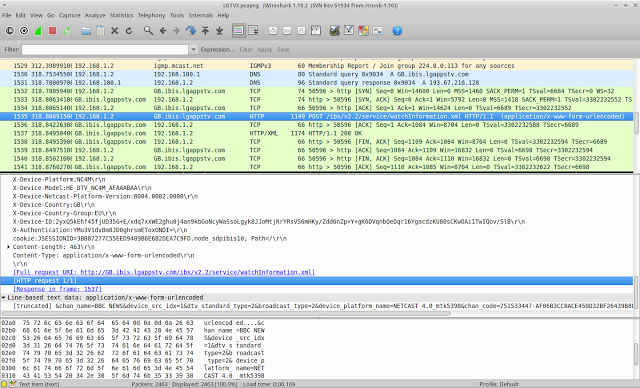
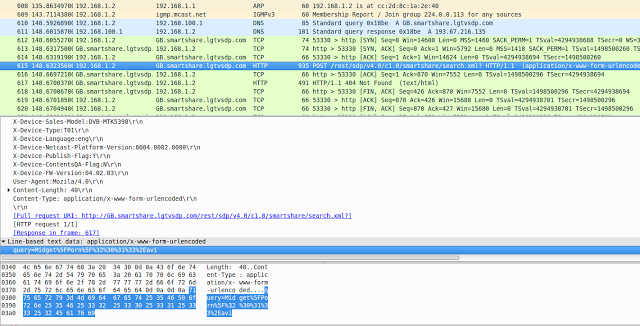
I decided to conduct a small analysis of the traffic that the TV sends. It turned out that traffic is sent regardless of whether the flag is set that allows the collection of information or not. The transmitted information contains a unique device number, the name of the current channel (in my case - “BBC NEWS”), its parameters and other information. Here is an example of an intercepted packet:
As you can see, the information is sent without any encryption. Sending is done every time you switch the channel, regardless of the tracking option. I did not stop there and continued to intercept packets, I noticed strange file names that were also sent to LG servers, these were lists of files from my external hard drive connected via USB to the TV.
To demonstrate this, I took the first video in AVI and copied it to a USB drive:
Actually, the name of the file does not reflect its contents, I just renamed it to make it easier to find it in traffic :) Packages containing the file name are detected several times, in some of them only the file name is sent, in others - the whole path. I could not determine by what principle sending works.
Interestingly, some of the addresses on the server side of LG where the information is sent are no longer available - the answer with the 404th error is visible in the screenshot.
In any case, even if this information is not stored “on the other side” now, no one will guarantee that LG will not restore the server and continue collecting. (It is also possible that the script intentionally returns the 404th error in order to hide from the charges. - Translator's comment. )
I contacted LG representatives and asked to comment on the unofficial collection of information by their TVs, their answer is below:
I didn’t ask them about transferring file names from USB-carriers (obviously, a question was sent about transferring data about channels when the setting was disabled - translator's comment) because of their “accept this” response policy for any questions, actually, I don’t expecting some other answer.
How can information leakage be prevented? The easiest option is to prohibit the transfer of traffic to LG servers on the router, here is a list of them:
This ban will allow you to block all leaks and, possibly, even disable all ads. At the same time, the software update is downloaded from another server and should work fine.

In fact, in the system settings there is an option “Collection of watching info”, which is enabled by default. To see this setting, the user must scroll to the bottom of the menu. In addition, this item does not have a context help with a detailed description of the option, unlike all other items.

I decided to conduct a small analysis of the traffic that the TV sends. It turned out that traffic is sent regardless of whether the flag is set that allows the collection of information or not. The transmitted information contains a unique device number, the name of the current channel (in my case - “BBC NEWS”), its parameters and other information. Here is an example of an intercepted packet:

GB.smartshare.lgtvsdp.com POST /ibs/v2.2/service/watchInformation.xml HTTP / 1.1
Host: GB.ibis.lgappstv.com
Accept: * / *
X-Device-Product: NETCAST 4.0
X-Device-Platform : NC4M
X-Device-Model: HE_DTV_NC4M_AFAAABAA
X-Device-Netcast-Platform-Version: 0004.0002.0000
X-Device-Country: GB
X-Device-Country-Group: EU
X-Device-ID: 2yxQ5kEhf45fjUD35G + E / xdq7xxWE2ghu0j4qyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqyqykyjycy Zdd6nZp + Y + gK6DVqnbQeDqr16YgacdzKU80sCKwOAi1TwIQov / SlB
X-Authentication: YMu3V1dv8m8JD0ghrsmEToxONDI = cookie: JSESSIONID = 3BB87277C55EED9B9dbdebde Path = /
Content-Length: 460
Content-Type: application / x-www-form-urlencoded
& chan_name = BBC TWO & device_src_idx = 1 & dtv_standard_type = 2
& broadcast_type = 2 & device_platform_name = NETCAST 4.0_mtk5398 & chan_code = 251533454-72E0D0FB0A8A4C70E4E2D829523CA235 & external_input_name = Antenna & chan_phy_no = & atsc_chan_maj_no = & atsc_chan_min_no = & chan_src_idx = 1 & chan_phy_no = & atsc_chan_maj_no = & atsc_chan_min_no = & chan_phy_no = 47 & atsc_chan_maj_no = 2 & atsc_chan_min_no = 2 & chan_src_idx = 1 & dvb_chan_nw_id = 9018 & dvb_chan_transf_id = 4170 & dvb_chan_svc_id = 4287 & watch_dvc_logging = 0
As you can see, the information is sent without any encryption. Sending is done every time you switch the channel, regardless of the tracking option. I did not stop there and continued to intercept packets, I noticed strange file names that were also sent to LG servers, these were lists of files from my external hard drive connected via USB to the TV.
To demonstrate this, I took the first video in AVI and copied it to a USB drive:

Actually, the name of the file does not reflect its contents, I just renamed it to make it easier to find it in traffic :) Packages containing the file name are detected several times, in some of them only the file name is sent, in others - the whole path. I could not determine by what principle sending works.

Interestingly, some of the addresses on the server side of LG where the information is sent are no longer available - the answer with the 404th error is visible in the screenshot.
In any case, even if this information is not stored “on the other side” now, no one will guarantee that LG will not restore the server and continue collecting. (It is also possible that the script intentionally returns the 404th error in order to hide from the charges. - Translator's comment. )
I contacted LG representatives and asked to comment on the unofficial collection of information by their TVs, their answer is below:
Good morning.
Thank you for your letter.
As we wrote in the previous letter, your request was redirected to LG headquarters in the United Kingdom.
Since you, unfortunately, have accepted the Terms and Conditions of use of the LG TV, your complaints should be directed to the seller of the device. You should have read the Terms and Conditions at the place of sale of the TV, for obvious reasons, LG can not provide comments on its actions.
We apologize for any inconvenience this may have caused you. If you have any other questions, feel free to contact us in the future.
Sincerely,
Tom
LG Electronics Support Service
Tel: 0844 847 5454
Fax: 01480 274 000
Email: cic.uk@lge.com
UK: [premium rate number removed] Ireland: 0818 27 6954
Mon-Fri 9am to 8pm Sat 9 am - 6pm
Sunday 11am - 5pm
I didn’t ask them about transferring file names from USB-carriers (obviously, a question was sent about transferring data about channels when the setting was disabled - translator's comment) because of their “accept this” response policy for any questions, actually, I don’t expecting some other answer.
How can information leakage be prevented? The easiest option is to prohibit the transfer of traffic to LG servers on the router, here is a list of them:
ad.lgappstv.com
yumenetworks.com
smartclip.net
smartclip.com
smartshare.lgtvsdp.com
ibis.lgappstv.com
This ban will allow you to block all leaks and, possibly, even disable all ads. At the same time, the software update is downloaded from another server and should work fine.
