Mikrotik and OSPF. What we had to face and how we overcame it
Good day. Today I would like to talk about what did not allow us to live, it blew our brains for a long time - Mikrotik and OSPF.
Mikrotik itself is a good piece of hardware, with a low cost, a lot of features, but unfortunately, not without flaws.
We have the following network diagram:
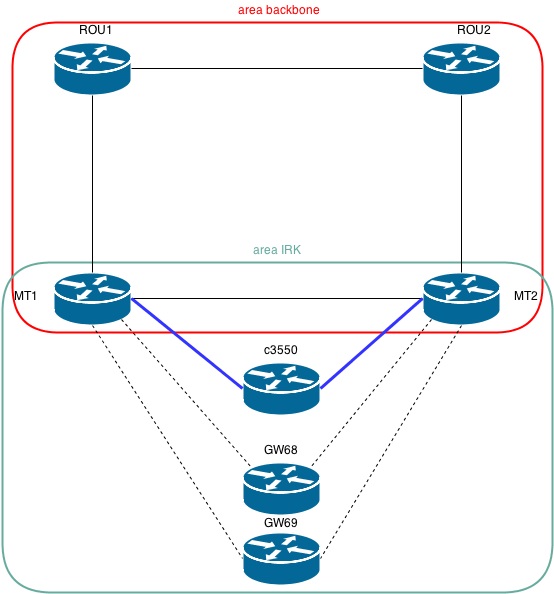
ROU1 - Cisco c3845
ROU2 - Cisco c3845
MT1 - Mikrotik 1100Ahx2
MT2 - Mikrotik 1100Ahx2
c3550 - Cisco c3550
GW68 - MikroTik RB751U-2HnD
GW69 - MikroTik RB751U-2HnD MT
to RO1 and MT1 to RO1 MT1 and RO1 MT1 ROU1 (I will skip IPSec), the OSPF process for backbone has been started. Suggested subnet 10.0.0.0/19:
On MT1 and MT2, the tunnel addresses are 172.20.64.2 and 172.20.64.6, respectively. Area backbone is already there by default.
But we must still have a connection between MT1 and MT2 directly.
To do this, we use the new area IRK. We do not only have a Cisco c3550 switch, it has a root device, all vlans are installed on it, providers are forwarded through it, vrf is created on it, etc. (If it is interesting, then I will describe the entire network organization)
Create a c3550 area IRK and two vlan to connect to MT1 and MT2. Area IRK is the main area of RU - a regional node in which all routers connected to RU operate.
Now we will accept these vlan on MT1 and MT2, and we will create a new ospf instance and area, add a link between MT1 and MT2 and attach the address.
It seems that I didn’t forget anything that we got:
1. We have two tunnels to the central routers, one from each Mikrotik.
2. Cost 10 and 40 respectively. That is, with MT1, the main router (provider) is alive, we will get the route from backbone 10.0.0.0/19 through the tunnel to ROU1, while dead through the tunnel to ROU2
3. We have a direct link between MT1 and MT2, so as not to drive traffic always through c3550.
Set up, set. Everything works:
# MT1
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.1 gateway-status = 172.20.64.1 reachable via ipip_yyy_vl03_rou1 distance = 110 scope = 20 target-scope = 10 ospf-metric = 40 ospf-type = external-type-1
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.105 gateway-status = 172.20.64.105 reachable via ether2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 50 ospf-type = external-type-1
On MT2, the route is up to 10k via ether2, as in principle it should be.
Problem No. 1:
Once, on MT1, a provider dies. The subnet 10.0.0.0/19 becomes accessible through the tunnel to ROU2, everything is as it should be:
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.5 gateway-status = 172.20.64.5 reachable via ipip_yyy_vl03_rou2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 70 ospf-type = external-type-1
BUT! As soon as the provider comes to life on MT1, we see the following:
# MT1
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.1 gateway-status = 172.20.64.1 reachable via ipip_yyy_vl03_rou1 distance = 110 scope = 20 target-scope = 10 ospf-metric = 40 ospf-type = external-type-1
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.5 gateway-status = 172.20.64.5 reachable via ipip_yyy_vl03_rou2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 70 ospf-type = external-type -1
We see that each router looks into its own tunnel. Which does not suit us at all. Reboot MT2. He begins to receive a route via ether2 from MT1. The mess.
As a temporary solution, we added all area from regional nodes to ROU1 and ROU2. Everything worked very nicely until one day our tsiska said: too many routing processes
And again we returned to the problem with the backbone. Long battles with support do not lead to anything, but at one point we get the answer that Mikrotik, when redistributing routes between Erias (in this case, the route from the backbone is redistributed via IRK),
starts to incorrectly install the routes. And we get the picture that each router looks into its own tunnel.
Then the solution comes by itself:
Add IP to ether2, add a new subnet to the backbone.
# MT1
/ ip address add address = 172.20.64.121 / 30 comment = "MT-MT BB" interface = ether2
/ routing ospf network add area = backbone network = 172.20.64.120 / 30
# We prohibit redistributing the route via IRK
/ routing filter add action = discard chain = ospf-in prefix = 10.0.0.0 / 19
# MT2
/ ip address add address = 172.20.64.122 / 30 comment = "MT-MT BB" interface = ether2
/ routing ospf network add area = backbone network = 172.20.64.120 / 30
# Forbid re-distributing the route via IRK
/ routing filter add action = discard chain = ospf-in prefix = 10.0.0.0 / 19
And we get that route 10.0.0.0/19 is not redistributed through someone else’s eria, but is accepted within one. Fuf, one problem was won.
Now to consider the second problem, we will give the GW config, I will omit the config for MT1 and MT2, there is nothing complicated there.
In the figure we have GW68 and GW69, I will give the settings for only one and in abbreviation:
On Mikrotik 751:
ether2 - backup
ether3 provider - main
ether5 provider - LAN
The question will be, why is not ether2 the main provider. First we made ether1 - the main provider, but it turned out that the port was half-software and there was absolutely no IPSec performance, we just transferred it to ether3 so as not to edit the config much.
How it works:
GW68 installs two tunnels to MT1 and to MT2, each through its own provider. There is no default on Mikrotik, the addresses of MT1 and MT2 are registered in statics.
On the tunnel to MT1 costs cost 10, on the tunnel to MT2 cost 40. As soon as the tunnel comes to life, we get a default and all routes from MT1 through OSPF. All traffic is wrapped on MT1. As soon as the main provider falls off,
after the OSPF timer expires, routes through the tunnel to MT2 become active.
Problem 2:
With the live main channel, we see in the GW68 log 20:12:26
route, ospf, info Database Description packet has different master status flag
20:12:26 route, ospf, info new master flag = false
At this point, our traffic by itself begins to run through the tunnel to MT2. The tunnel to MT1 is live, and traffic runs through the tunnel to MT2. And since stores usually have megabyte reserves,
we get money exhausted for no reason.
To return everything to the tunnel to MT1, it was necessary to turn off and on again the tunnel to MT1 on MT1. Moreover, this problem arose only in some cities, and not on all routers.
At the microtica forum, in those. nobody helped us with support. Once my colleague, trying to raise the MT1-Juniper SRX-650 tunnel, was armed with a bunch of alcohol, a sniffer and a debugger :)
And while debugging IPSec, I came across OSPF Mikrotik authorization errors. We disabled authorization on OSPF and voila interfaces, the problem disappeared by itself.
How authorization is going on, where is the failure, now neither he nor I remember. But the issue is resolved. Why somewhere it worked perfectly and with authorization, I can’t say.
With Mikrotik one can only guess on the coffee grounds, since each support response is a new question, each new firmware presents a new problem :)
Mikrotik itself is a good piece of hardware, with a low cost, a lot of features, but unfortunately, not without flaws.
We have the following network diagram:

ROU1 - Cisco c3845
ROU2 - Cisco c3845
MT1 - Mikrotik 1100Ahx2
MT2 - Mikrotik 1100Ahx2
c3550 - Cisco c3550
GW68 - MikroTik RB751U-2HnD
GW69 - MikroTik RB751U-2HnD MT
to RO1 and MT1 to RO1 MT1 and RO1 MT1 ROU1 (I will skip IPSec), the OSPF process for backbone has been started. Suggested subnet 10.0.0.0/19:
Configuration of ROU1 and ROU2
# ROU1
interface Tunnel100641
description # XXX_IRK64_YYY #
ip address 172.20.64.1 255.255.255.252
ip access-group DMZ_IN in
ip access-group DMZ_OUT out
ip mtu 1450
ip ospf network point-to-point
ip ospf cost 10
ip ospf mtu-ignore
ip ospf 1 area 0.0.0.0
tunnel source 194.xxx
tunnel mode ipip
tunnel destination 195.xxx
router ospf 1
router-id 255.255.255.255
redistribute ospf 100 metric-type 1 subnets route-map OSPF_100_to_BB
network 172.20.64.0 0.0.0.3 area 0.0.0.0
# ROU2
interface Tunnel100642
description # XXX_IRK64_YYY #
ip address 172.20.64.5 255.255.255.252
ip access-group DMZ_IN in
ip access-group DMZ_OUT out
ip mtu 1450
ip ospf network point-to-point
ip ospf cost 40
ip ospf mtu-ignore
ip ospf 1 area 0.0.0.0
tunnel source 109 .xxx
tunnel mode ipip
tunnel destination 85.xxx
router ospf 1
router-id 255.255.255.254
redistribute ospf 100 metric-type 1 subnets route-map OSPF_100_to_BB
network 172.20.64.4 0.0.0.3 area 0.0.0.0
interface Tunnel100641
description # XXX_IRK64_YYY #
ip address 172.20.64.1 255.255.255.252
ip access-group DMZ_IN in
ip access-group DMZ_OUT out
ip mtu 1450
ip ospf network point-to-point
ip ospf cost 10
ip ospf mtu-ignore
ip ospf 1 area 0.0.0.0
tunnel source 194.xxx
tunnel mode ipip
tunnel destination 195.xxx
router ospf 1
router-id 255.255.255.255
redistribute ospf 100 metric-type 1 subnets route-map OSPF_100_to_BB
network 172.20.64.0 0.0.0.3 area 0.0.0.0
# ROU2
interface Tunnel100642
description # XXX_IRK64_YYY #
ip address 172.20.64.5 255.255.255.252
ip access-group DMZ_IN in
ip access-group DMZ_OUT out
ip mtu 1450
ip ospf network point-to-point
ip ospf cost 40
ip ospf mtu-ignore
ip ospf 1 area 0.0.0.0
tunnel source 109 .xxx
tunnel mode ipip
tunnel destination 85.xxx
router ospf 1
router-id 255.255.255.254
redistribute ospf 100 metric-type 1 subnets route-map OSPF_100_to_BB
network 172.20.64.4 0.0.0.3 area 0.0.0.0
On MT1 and MT2, the tunnel addresses are 172.20.64.2 and 172.20.64.6, respectively. Area backbone is already there by default.
MT1 and MT2 Configuration
# MT1
# Create a tunnel
/ interface ipip add comment = YYY_VL03_ROU1 disabled = no local-address = 195.xxx mtu = 1450 name = ipip_yyy_vl03_rou1 remote-address = 194.xxx
# Put the address
/ ip address add address = 172.20.64.2 / on it 30 comment = YYY_VL03_XXX interface = ipip_yyy_vl03_rou1
# Let's fix instance by adding filters and id
/ routing ospf instance set [find default = yes] in-filter = ospf-default-in out-filter = ospf-default-out redistribute-other-ospf = as-type-1 router-id = 30.0.64.1
# Add a subnet to area backbone
/ routing ospf network add area = backbone comment = “Backbone Network VL” network = 172.20.64.0 / 30
# Make filters
/ routing filter add action = accept chain = ospf-default-out prefix = 10.0.64.0 / 19
/ routing filter add action = accept chain = ospf-default-out prefix = 172.20.64.0 / 19
/ routing filter add action = discard chain = ospf-default-out
/ routing filter add action = accept chain = ospf-default-in prefix = 10.0.0.0 / 19
/ routing filter add action = accept chain = ospf-default-in prefix = 172.20.0.0 / 19
/ routing filter add action = discard chain = ospf-default-in
# Create the OSPF
/ routing ospf interface add interface authentication-key = 0 interface = ipip_yyy_vl03_rou1 network-type = point-to-point priority = 255
# MT2
# Create a tunnel
/ interface ipip add comment = YYY_VL03_ROU2 disabled = no local-address = 85.xxx mtu = 1450 name = ipip_yyy_vl03_rou2 remote- address = 109.xxx
# Let's hang an address on it
/ ip address add address = 172.20.64.6 / 30 comment = YYY_VL03_ROU2 interface = ipip_yyy_vl03_rou2
# Let's fix instance by adding filters and id
/ routing ospf instance set [find default = yes] in-filter = ospf-default-in out-filter = ospf -default-out redistribute-other-ospf = as-type-1 router-id = 30.0.64.2
# Add a subnet to area backbone
/ routing ospf network add area = backbone comment = "Backbone Network VL" network = 172.20.64.4 / 30
# Make filters
/ routing filter add action = accept chain = ospf-default-out prefix = 10.0.64.0 / 19
/ routing filter add action = accept chain = ospf-default-out prefix = 172.20.64.0 / 19
/ routing filter add action = discard chain = ospf-default-out
/ routing filter add action = accept chain = ospf-default-in prefix = 10.0.0.0 / 19
/ routing filter add action = accept chain = ospf-default-in prefix = 172.20.0.0 / 19
/ routing filter add action = discard chain = ospf-default-in
# Create the OSPF
interface / routing ospf interface add authentication-key = 0 cost = 40 interface = ipip_yyy_vl03_rou2 network-type = point-to-point priority = 200
# Create a tunnel
/ interface ipip add comment = YYY_VL03_ROU1 disabled = no local-address = 195.xxx mtu = 1450 name = ipip_yyy_vl03_rou1 remote-address = 194.xxx
# Put the address
/ ip address add address = 172.20.64.2 / on it 30 comment = YYY_VL03_XXX interface = ipip_yyy_vl03_rou1
# Let's fix instance by adding filters and id
/ routing ospf instance set [find default = yes] in-filter = ospf-default-in out-filter = ospf-default-out redistribute-other-ospf = as-type-1 router-id = 30.0.64.1
# Add a subnet to area backbone
/ routing ospf network add area = backbone comment = “Backbone Network VL” network = 172.20.64.0 / 30
# Make filters
/ routing filter add action = accept chain = ospf-default-out prefix = 10.0.64.0 / 19
/ routing filter add action = accept chain = ospf-default-out prefix = 172.20.64.0 / 19
/ routing filter add action = discard chain = ospf-default-out
/ routing filter add action = accept chain = ospf-default-in prefix = 10.0.0.0 / 19
/ routing filter add action = accept chain = ospf-default-in prefix = 172.20.0.0 / 19
/ routing filter add action = discard chain = ospf-default-in
# Create the OSPF
/ routing ospf interface add interface authentication-key = 0 interface = ipip_yyy_vl03_rou1 network-type = point-to-point priority = 255
# MT2
# Create a tunnel
/ interface ipip add comment = YYY_VL03_ROU2 disabled = no local-address = 85.xxx mtu = 1450 name = ipip_yyy_vl03_rou2 remote- address = 109.xxx
# Let's hang an address on it
/ ip address add address = 172.20.64.6 / 30 comment = YYY_VL03_ROU2 interface = ipip_yyy_vl03_rou2
# Let's fix instance by adding filters and id
/ routing ospf instance set [find default = yes] in-filter = ospf-default-in out-filter = ospf -default-out redistribute-other-ospf = as-type-1 router-id = 30.0.64.2
# Add a subnet to area backbone
/ routing ospf network add area = backbone comment = "Backbone Network VL" network = 172.20.64.4 / 30
# Make filters
/ routing filter add action = accept chain = ospf-default-out prefix = 10.0.64.0 / 19
/ routing filter add action = accept chain = ospf-default-out prefix = 172.20.64.0 / 19
/ routing filter add action = discard chain = ospf-default-out
/ routing filter add action = accept chain = ospf-default-in prefix = 10.0.0.0 / 19
/ routing filter add action = accept chain = ospf-default-in prefix = 172.20.0.0 / 19
/ routing filter add action = discard chain = ospf-default-in
# Create the OSPF
interface / routing ospf interface add authentication-key = 0 cost = 40 interface = ipip_yyy_vl03_rou2 network-type = point-to-point priority = 200
But we must still have a connection between MT1 and MT2 directly.
To do this, we use the new area IRK. We do not only have a Cisco c3550 switch, it has a root device, all vlans are installed on it, providers are forwarded through it, vrf is created on it, etc. (If it is interesting, then I will describe the entire network organization)
Create a c3550 area IRK and two vlan to connect to MT1 and MT2. Area IRK is the main area of RU - a regional node in which all routers connected to RU operate.
C3550 configuration
interface Vlan66
description # MGM 1 VLAN #
ip address 172.20.64.98 255.255.255.252
ip policy route-map test
ip ospf cost 10
ip ospf hello-interval 5
ip ospf dead-interval 10
ip ospf priority 100
!
interface Vlan67
description # MGM 2 VLAN #
ip address 172.20.64.102 255.255.255.252
ip ospf cost 10
ip ospf hello-interval 5
ip ospf dead-interval 10
ip ospf priority 50
router ospf 100
router-id 10.0.64.0
log-adjacency-changes
redistribute connected metric-type 1 subnets
redistribute static metric-type 1 subnets
network 172.20.64.96 0.0.0.3 area 10.0.64.0
network 172.20.64.100 0.0.0.3 area 10.0.64.0
# Two zero routes
ip route 10.0.64.0 255.255.224.0 Null0 250
ip route 172.20.64.0 255.255.224.0 Null0 250
description # MGM 1 VLAN #
ip address 172.20.64.98 255.255.255.252
ip policy route-map test
ip ospf cost 10
ip ospf hello-interval 5
ip ospf dead-interval 10
ip ospf priority 100
!
interface Vlan67
description # MGM 2 VLAN #
ip address 172.20.64.102 255.255.255.252
ip ospf cost 10
ip ospf hello-interval 5
ip ospf dead-interval 10
ip ospf priority 50
router ospf 100
router-id 10.0.64.0
log-adjacency-changes
redistribute connected metric-type 1 subnets
redistribute static metric-type 1 subnets
network 172.20.64.96 0.0.0.3 area 10.0.64.0
network 172.20.64.100 0.0.0.3 area 10.0.64.0
# Two zero routes
ip route 10.0.64.0 255.255.224.0 Null0 250
ip route 172.20.64.0 255.255.224.0 Null0 250
Now we will accept these vlan on MT1 and MT2, and we will create a new ospf instance and area, add a link between MT1 and MT2 and attach the address.
MT1 and MT2 Configuration
# MT1
# Accept vlan
/ interface vlan add interface = ether1 l2mtu = 1594 name = vlan_66_mgm vlan-id = 66
# Create area
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
# Create instance
/ routing ospf instance add distribute-default = if-installed-as-type-1 name = IRK redistribute-other-ospf = as-type-1 redistribute-static = as-type-1 router-id = 10.0.64.1
# Hang up IP
/ ip address add address = 172.20.64.97 / 30 comment = MGM_Interface interface = vlan_66_mgm
/ ip address add address = 172.20.64.105 / 30 comment = MT-MT_Interface interface = ether2
# Add subnets to area IRK
/ routing ospf network add area = IRK network = 172.20.64.96/30
/ routing ospf network add area = IRK network = 172.20.64.104 / 30
#Create ospf interface
/ routing ospf interface add dead-interval = 10s hello-interval = 5s interface = vlan_66_mgm network-type = broadcast priority = 255
# MT2
# Accept vlan
/ interface vlan add interface = ether1 l2mtu = 1594 name = vlan_67_mgm vlan- id = 67
# Create area
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
# Create instance
/ routing ospf instance add distribute-default = if-installed-as-type-1 name = IRK redistribute- other-ospf = as-type-1 redistribute-static = as-type-1 router-id = 10.0.64.2
# Hang up IP
/ ip address add address = 172.20.64.101 / 30 comment = MGM_Interface interface = vlan_67_mgm
/ ip address add address = 172.20.64.106 / 30 comment = MT-MT_Interface interface = ether2
# Add subnets to area IRK
/ routing ospf network add area = IRK network = 172.20.64.100 / 30
/ routing ospf network add area = IRK network = 172.20.64.104 / 30
# Create ospf interface
/ routing ospf interface add dead-interval = 10s hello-interval = 5s interface = vlan_67_mgm network-type = broadcast priority = 200
# Accept vlan
/ interface vlan add interface = ether1 l2mtu = 1594 name = vlan_66_mgm vlan-id = 66
# Create area
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
# Create instance
/ routing ospf instance add distribute-default = if-installed-as-type-1 name = IRK redistribute-other-ospf = as-type-1 redistribute-static = as-type-1 router-id = 10.0.64.1
# Hang up IP
/ ip address add address = 172.20.64.97 / 30 comment = MGM_Interface interface = vlan_66_mgm
/ ip address add address = 172.20.64.105 / 30 comment = MT-MT_Interface interface = ether2
# Add subnets to area IRK
/ routing ospf network add area = IRK network = 172.20.64.96/30
/ routing ospf network add area = IRK network = 172.20.64.104 / 30
#Create ospf interface
/ routing ospf interface add dead-interval = 10s hello-interval = 5s interface = vlan_66_mgm network-type = broadcast priority = 255
# MT2
# Accept vlan
/ interface vlan add interface = ether1 l2mtu = 1594 name = vlan_67_mgm vlan- id = 67
# Create area
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
# Create instance
/ routing ospf instance add distribute-default = if-installed-as-type-1 name = IRK redistribute- other-ospf = as-type-1 redistribute-static = as-type-1 router-id = 10.0.64.2
# Hang up IP
/ ip address add address = 172.20.64.101 / 30 comment = MGM_Interface interface = vlan_67_mgm
/ ip address add address = 172.20.64.106 / 30 comment = MT-MT_Interface interface = ether2
# Add subnets to area IRK
/ routing ospf network add area = IRK network = 172.20.64.100 / 30
/ routing ospf network add area = IRK network = 172.20.64.104 / 30
# Create ospf interface
/ routing ospf interface add dead-interval = 10s hello-interval = 5s interface = vlan_67_mgm network-type = broadcast priority = 200
It seems that I didn’t forget anything that we got:
1. We have two tunnels to the central routers, one from each Mikrotik.
2. Cost 10 and 40 respectively. That is, with MT1, the main router (provider) is alive, we will get the route from backbone 10.0.0.0/19 through the tunnel to ROU1, while dead through the tunnel to ROU2
3. We have a direct link between MT1 and MT2, so as not to drive traffic always through c3550.
Set up, set. Everything works:
# MT1
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.1 gateway-status = 172.20.64.1 reachable via ipip_yyy_vl03_rou1 distance = 110 scope = 20 target-scope = 10 ospf-metric = 40 ospf-type = external-type-1
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.105 gateway-status = 172.20.64.105 reachable via ether2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 50 ospf-type = external-type-1
On MT2, the route is up to 10k via ether2, as in principle it should be.
Problem No. 1:
Once, on MT1, a provider dies. The subnet 10.0.0.0/19 becomes accessible through the tunnel to ROU2, everything is as it should be:
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.5 gateway-status = 172.20.64.5 reachable via ipip_yyy_vl03_rou2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 70 ospf-type = external-type-1
BUT! As soon as the provider comes to life on MT1, we see the following:
# MT1
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.1 gateway-status = 172.20.64.1 reachable via ipip_yyy_vl03_rou1 distance = 110 scope = 20 target-scope = 10 ospf-metric = 40 ospf-type = external-type-1
# MT2
ADo dst-address = 10.0.0.0 / 19 gateway = 172.20.64.5 gateway-status = 172.20.64.5 reachable via ipip_yyy_vl03_rou2 distance = 110 scope = 20 target-scope = 10 ospf-metric = 70 ospf-type = external-type -1
We see that each router looks into its own tunnel. Which does not suit us at all. Reboot MT2. He begins to receive a route via ether2 from MT1. The mess.
As a temporary solution, we added all area from regional nodes to ROU1 and ROU2. Everything worked very nicely until one day our tsiska said: too many routing processes
And again we returned to the problem with the backbone. Long battles with support do not lead to anything, but at one point we get the answer that Mikrotik, when redistributing routes between Erias (in this case, the route from the backbone is redistributed via IRK),
starts to incorrectly install the routes. And we get the picture that each router looks into its own tunnel.
Then the solution comes by itself:
Add IP to ether2, add a new subnet to the backbone.
# MT1
/ ip address add address = 172.20.64.121 / 30 comment = "MT-MT BB" interface = ether2
/ routing ospf network add area = backbone network = 172.20.64.120 / 30
# We prohibit redistributing the route via IRK
/ routing filter add action = discard chain = ospf-in prefix = 10.0.0.0 / 19
# MT2
/ ip address add address = 172.20.64.122 / 30 comment = "MT-MT BB" interface = ether2
/ routing ospf network add area = backbone network = 172.20.64.120 / 30
# Forbid re-distributing the route via IRK
/ routing filter add action = discard chain = ospf-in prefix = 10.0.0.0 / 19
And we get that route 10.0.0.0/19 is not redistributed through someone else’s eria, but is accepted within one. Fuf, one problem was won.
Now to consider the second problem, we will give the GW config, I will omit the config for MT1 and MT2, there is nothing complicated there.
In the figure we have GW68 and GW69, I will give the settings for only one and in abbreviation:
On Mikrotik 751:
ether2 - backup
ether3 provider - main
ether5 provider - LAN
The question will be, why is not ether2 the main provider. First we made ether1 - the main provider, but it turned out that the port was half-software and there was absolutely no IPSec performance, we just transferred it to ether3 so as not to edit the config much.
GW68 Configuration
# Create tunnels
/ interface ipip add comment = X_GW64_X disabled = no local-address = 195.xxx mtu = 1440 name = ipip_x_gw64_x remote-address = 195.xxx
/ interface ipip add comment = Y_GW64_Y disabled = no local-address = 87.xxx mtu = 1440 name = ipip_y_gw64_y remote-address = 85.xxx
# Create a bridge, combine wifi ap and ether5
/ interface bridge add l2mtu = 1594 name = bridge_private
/ interface bridge port add bridge = bridge_private interface = ether5
/ interface bridge port add bridge = bridge_private interface = wlan_private
# Create DHCP
/ ip pool add name = 10.0.68.0 ranges = 10.0.68.64-10.0.68.160
/ ip dhcp-server add address-pool = 10.0.68.0 disabled = no interface = bridge_private name = 10.0.68.0
/ ip dhcp-server network add address = 10.0.68.0 / 24 dns-server = 10.0.64.14,10.0.3.6 domain = partner.ru gateway = 10.0.68.1
# Hang up IP
/ ip address add address = 10.0.68.1 / 24 comment = LAN interface = bridge_private
/ ip address add address = 172.20.68.2 / 30 comment = X_GW64_X interface = ipip_x_gw64_x
/ ip address add address = 172.20.68.6 / 30 comment = Y_GW64_Y interface = ipip_y_gw64_y
/ ip address add address = 195.xxx / 30 comment = X interface = ether3
/ ip address add address = 87.xxx / 30 comment = Y interface = ether2
# Add routes to the addresses MT1 and MT2 through the provider gateways
/ ip route add check-gateway = ping comment = Route_over_Y_to_Y distance = 1 dst -address = 85.xxx / 32 gateway = 1.1.1.1
/ ip route add check-gateway = ping comment = Route_over_X_to_X distance = 1 dst-address = 195.xxx / 32 gateway = 2.2.2.2
# Add area and instance, network and ospf interface
/ routing ospf instance set [find default = yes] disabled = yes
/ routing ospf instance add name = IRK router-id = 10.0.68.1
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
/ routing ospf network add area = IRK network = 172.20.68.0 / 30
/ routing ospf network add area = IRK network = 172.20.68.4 / 30
/ routing ospf network add area = IRK network = 10.0.68.0 / 24
/ routing ospf interface add authentication = md5 authentication-key = 0 interface = ipip_x_gw64_x network-type = point-to-point priority = 0
/ routing ospf interface add authentication = md5 authentication-key = 0 cost = 40 interface = ipip_y_gw64_y network-type = point -to-point priority = 0
/ routing ospf interface add authentication = md5 authentication-key = 0 interface = bridge_private network-type = broadcast passive = yes
/ interface ipip add comment = X_GW64_X disabled = no local-address = 195.xxx mtu = 1440 name = ipip_x_gw64_x remote-address = 195.xxx
/ interface ipip add comment = Y_GW64_Y disabled = no local-address = 87.xxx mtu = 1440 name = ipip_y_gw64_y remote-address = 85.xxx
# Create a bridge, combine wifi ap and ether5
/ interface bridge add l2mtu = 1594 name = bridge_private
/ interface bridge port add bridge = bridge_private interface = ether5
/ interface bridge port add bridge = bridge_private interface = wlan_private
# Create DHCP
/ ip pool add name = 10.0.68.0 ranges = 10.0.68.64-10.0.68.160
/ ip dhcp-server add address-pool = 10.0.68.0 disabled = no interface = bridge_private name = 10.0.68.0
/ ip dhcp-server network add address = 10.0.68.0 / 24 dns-server = 10.0.64.14,10.0.3.6 domain = partner.ru gateway = 10.0.68.1
# Hang up IP
/ ip address add address = 10.0.68.1 / 24 comment = LAN interface = bridge_private
/ ip address add address = 172.20.68.2 / 30 comment = X_GW64_X interface = ipip_x_gw64_x
/ ip address add address = 172.20.68.6 / 30 comment = Y_GW64_Y interface = ipip_y_gw64_y
/ ip address add address = 195.xxx / 30 comment = X interface = ether3
/ ip address add address = 87.xxx / 30 comment = Y interface = ether2
# Add routes to the addresses MT1 and MT2 through the provider gateways
/ ip route add check-gateway = ping comment = Route_over_Y_to_Y distance = 1 dst -address = 85.xxx / 32 gateway = 1.1.1.1
/ ip route add check-gateway = ping comment = Route_over_X_to_X distance = 1 dst-address = 195.xxx / 32 gateway = 2.2.2.2
# Add area and instance, network and ospf interface
/ routing ospf instance set [find default = yes] disabled = yes
/ routing ospf instance add name = IRK router-id = 10.0.68.1
/ routing ospf area add area-id = 10.0.64.0 instance = IRK name = IRK
/ routing ospf network add area = IRK network = 172.20.68.0 / 30
/ routing ospf network add area = IRK network = 172.20.68.4 / 30
/ routing ospf network add area = IRK network = 10.0.68.0 / 24
/ routing ospf interface add authentication = md5 authentication-key = 0 interface = ipip_x_gw64_x network-type = point-to-point priority = 0
/ routing ospf interface add authentication = md5 authentication-key = 0 cost = 40 interface = ipip_y_gw64_y network-type = point -to-point priority = 0
/ routing ospf interface add authentication = md5 authentication-key = 0 interface = bridge_private network-type = broadcast passive = yes
How it works:
GW68 installs two tunnels to MT1 and to MT2, each through its own provider. There is no default on Mikrotik, the addresses of MT1 and MT2 are registered in statics.
On the tunnel to MT1 costs cost 10, on the tunnel to MT2 cost 40. As soon as the tunnel comes to life, we get a default and all routes from MT1 through OSPF. All traffic is wrapped on MT1. As soon as the main provider falls off,
after the OSPF timer expires, routes through the tunnel to MT2 become active.
Problem 2:
With the live main channel, we see in the GW68 log 20:12:26
route, ospf, info Database Description packet has different master status flag
20:12:26 route, ospf, info new master flag = false
At this point, our traffic by itself begins to run through the tunnel to MT2. The tunnel to MT1 is live, and traffic runs through the tunnel to MT2. And since stores usually have megabyte reserves,
we get money exhausted for no reason.
To return everything to the tunnel to MT1, it was necessary to turn off and on again the tunnel to MT1 on MT1. Moreover, this problem arose only in some cities, and not on all routers.
At the microtica forum, in those. nobody helped us with support. Once my colleague, trying to raise the MT1-Juniper SRX-650 tunnel, was armed with a bunch of alcohol, a sniffer and a debugger :)
And while debugging IPSec, I came across OSPF Mikrotik authorization errors. We disabled authorization on OSPF and voila interfaces, the problem disappeared by itself.
How authorization is going on, where is the failure, now neither he nor I remember. But the issue is resolved. Why somewhere it worked perfectly and with authorization, I can’t say.
With Mikrotik one can only guess on the coffee grounds, since each support response is a new question, each new firmware presents a new problem :)
